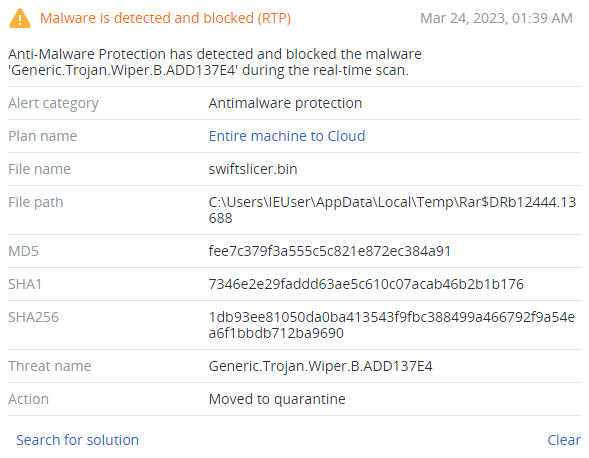
On January 25, 2023, ESET Research found a new data wiper in the network of Ukrinform, Ukraine’s national news agency. Later, the Computer Emergency Response Team of Ukraine (CERT-UA) added that as of January 27, five additional, different malware samples were spotted in the network.
These attacks were attributed to the Sandworm APT group, which was active from 2014. Sandworm is responsible for Industroyer, NotPetya, WhisperGate, CaddyWiper, IsaacWiper and other disruptive malware.
Technical details
Overview
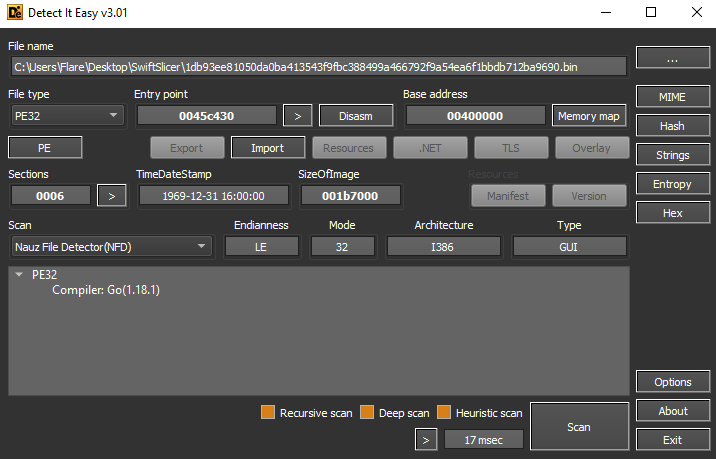
The analyzed SwiftSlicer sample (SHA256:1db93ee81050da0ba413543f9fbc388499a466792f9a54ea6f1bbdb712ba9690) was written in the Go programming language, and has a fake compilation timestamp. This sample is not packed or obfuscated.
Execution
Although the SwiftSlicer sample has over 1,800 functions, the wiping preparation and routine are easily located within functions with the ‘main_’ prefix.
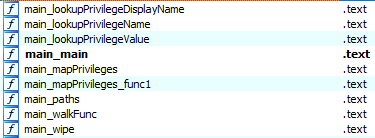
SwiftSlicer probably took its name from the ‘slice’ data type in Go. It has a bunch of functions to work with slices, which are used during execution to store data.
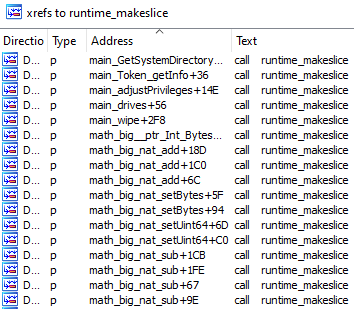
Execution starts from the ‘main_main’ function. First, SwiftSlicer calls ‘main_paths()’ to obtain the System folder path.
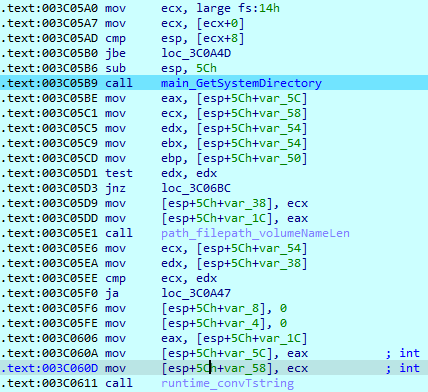
Besides the System folder, it also obtains some information about the system, user and other system paths.
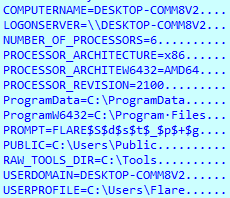
SwiftSlicer then obtains all available volumes’ path names. The System volume will be marked as ‘HOMEDRIVE’.
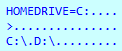
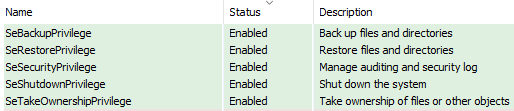
Before starting the wiping routine, SwiftSlicer obtains some privileges. This particular operation requires administrative privileges and uses the ‘AdjustTokenPrivileges’ system call.
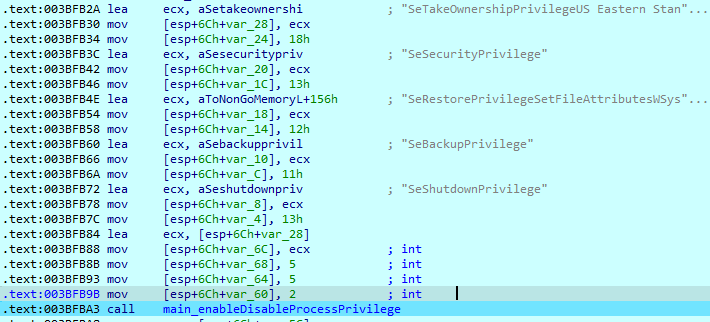
After this operation has completed, SwiftSlicer’s process has the following privileges:
It then deletes all shadow copies using the ‘wmic.exe’ process.
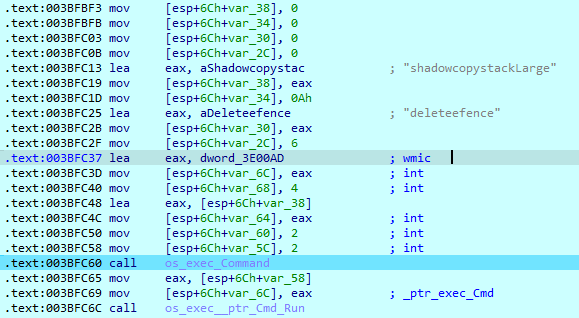
Executed command:
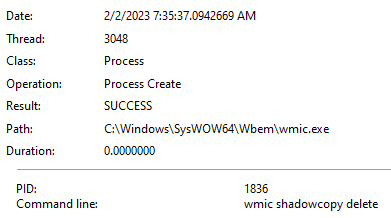
SwiftSlicer then starts searching for files to wipe. After reading the file on the logical drive, it checks whether it is a folder. If so, it reads its’ subfolders names.
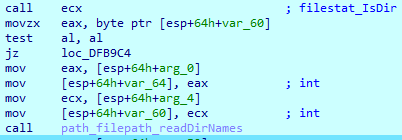
After that, it generates its’ full path and saves it in the memory.
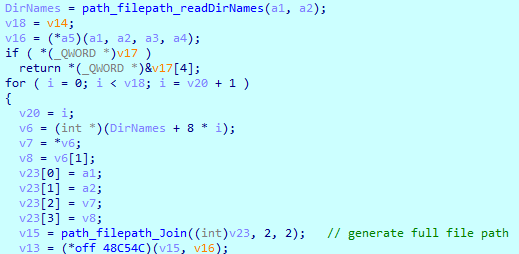
If the current folder doesn’t contain any folders, SwiftSlicer loads the 'main_walkFunk()’ function to the register and calls it.
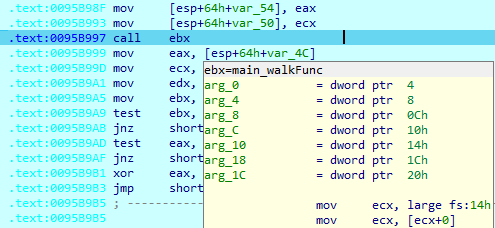
SwiftSlicer corrupts every file on the computer. The first-opened drive is not the System drive, allowing the malware to corrupts users’ files before it breaks the system’s workability. On the System drive, the first folder read is ‘C:\Windows\SysWOW64\drivers’. After listing all directories in this folder, SwiftSlicer loads the first driver file and calls the wipe function.
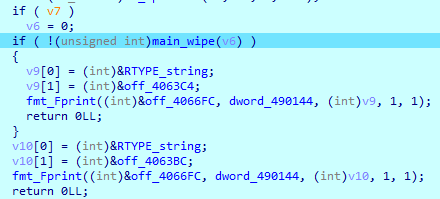
After obtaining access to the file, SwiftSlicer checks its size.
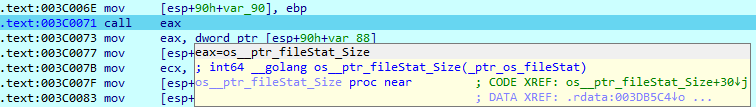
Then, it randomly generates a 128-byte buffer.
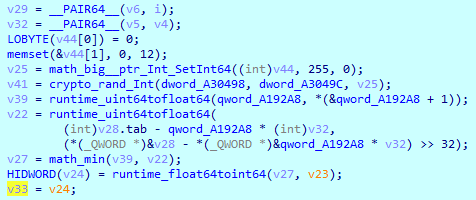
This buffer is given as an argument to the ‘os__ptr_File_WriteAt()’ function, where it can be expanded up to 4096 bytes or to the file size.
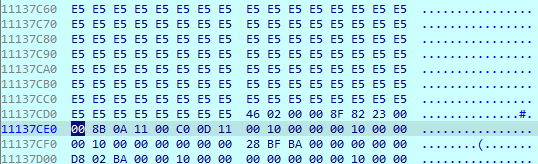
Depending on the file’s size, SwiftSlicer starts overwriting it. If the file is smaller than 4096 bytes, the wiper makes one iteration, writing a buffer equal to the file size. If the file is larger than 4096 bytes, it is divided into chunks and then overwritten. Each buffer has different content.
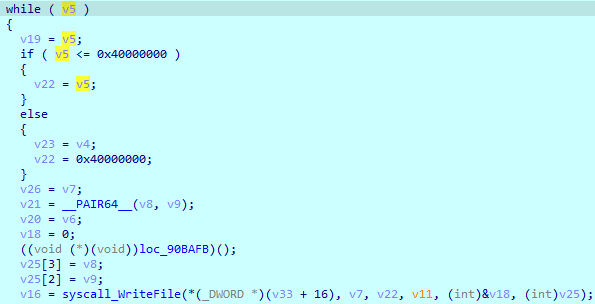
Here is an example of how it overwrites a large file, making the offset for 4096 bytes after writing the previous buffer. The size of the last buffer depends on the file’s remaining size.
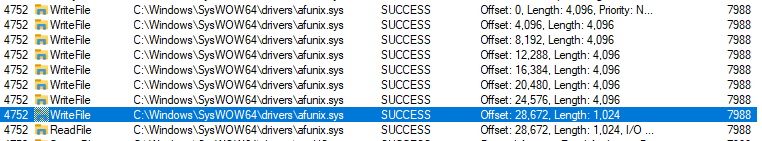
The result is shown below:
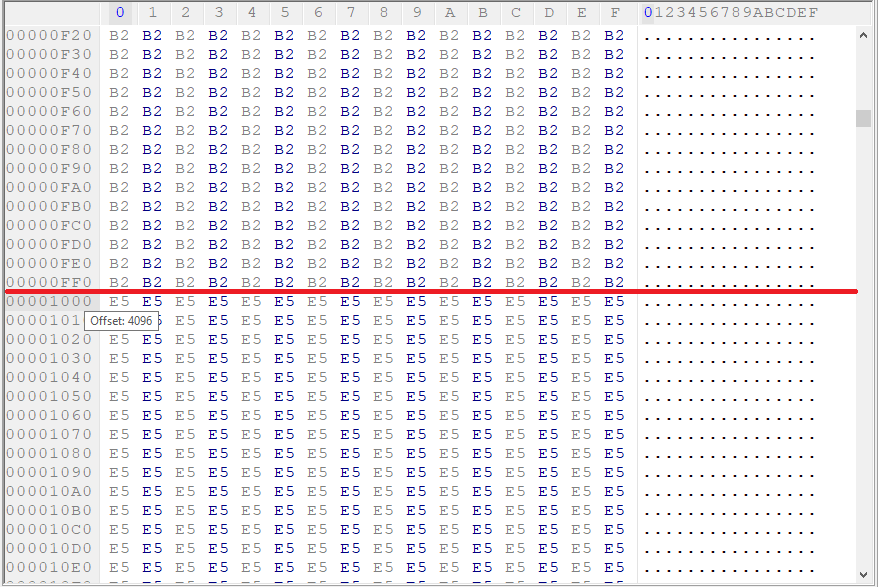
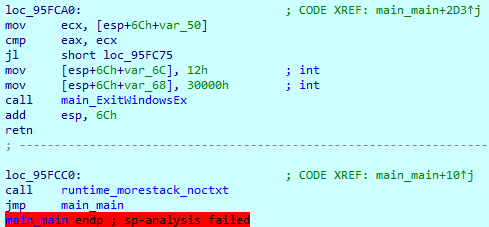
At the end of execution, it reboots the system using the ExitWindowsEx() call.
Conclusion
The Sandworm APT group continues to develop disruptive malware and deploy it on different networks. Their new SwiftSlicer malware wipes all users’ files on the system, as well as system files such as drivers.
The whole corruption process was not particularly fast, because SwiftSlicer has only one thread, which enumerates files, loads and overwrites them. As a result, the process can be spotted early, before it corrupts the System drive.
Still, without good cybersecurity tools, some files could be corrupted and lost even if the malware was spotted and its execution terminated, as SwiftSlicer deletes all shadow copies at the start of execution.
Detected by Acronis