- ProductsFor service providersEmpowering service providers with backup, DR, cybersecurity, and endpoint management in one integrated solution.For businessesComplete cyber resilience for small business, including backup and DR, anti-malware and remote endpoint monitoring.The most secure backup and fastest recovery for Enterprise, designed specifically for multi-site, multi-generational and industrial IT.Acronis Cyber Protect Connect is a remote access solution to remotely manage workloads — quickly and easily.For homeAcronis True Image-40%Formerly Acronis Home Office, it's the only personal cyber protection solution that delivers easy-to-use, integrated backup and anti-malware in one.Looking to update or renew your product or contact us for help?
- SolutionsSolutionsFor service providersFor businessEnvironmentsMobile |
- PartnersOne partner program. Total cyber protection.Benefits designed for youSupport for your business
- Find an IT provider
- Find a distributor
- Partner Certification Partners now have access to all sales and technical training — a $999 annual value per partner
- MSP Academy Vendor-neutral training, covering the A-Z of managing an MSP business
Go further with cyber protection- Acronis #CyberFit Technology Partner Program One tiered program to build and promote your custom solution
- Acronis Developer Network Developer community and resources in our Technology Partner Program
- SupportResourcesSupport by categoryNeed more help?Logins
- Cyber Protection Console Access and administer your client cloud solutions
- Partner Certification Partners now have access to all sales and technical training — a $999 annual value per partner
- Cyber Protection Console
- ResourcesBrowse through a full list of the latest product documentation, case studies, white papers, eBooks, upcoming and on-demand webinars of AcronisProduct resourcesAcronis Academy
- Partner Certification Partners now have access to all sales and technical training — a $999 annual value per partner
- MSP Academy Vendor-neutral training, covering the A-Z of managing an MSP business
Events, webinars and trainings - Partner Certification
- CompanyCompanyCompany policiesSpecial projects
- Acronis #CyberFit Sports See how the world’s leading sports teams use cyber protection to gain a competitive advantage.
- Acronis Cyber Foundation Discover how we can work together to create, spread, and protect knowledge to build a better future.
- Acronis #CyberFit Sports

Stop data leaks at the source with complete endpoint data loss prevention (DLP)
Function-based modular DLP solution architecture with incremental licensing
Acronis DeviceLock DLP is designed as a modular architecture of standalone products and built-in, add-on functional components whose capabilities complement each other. The management of all modules is unified and licensing for functional components other than Acronis DeviceLock Core is optional.
This architecture allows customers to purchase only those DLP functions they need and incrementally upgrade them over time as their data protection requirements evolve.

Modules
The fundamental component of Acronis DeviceLock Endpoint DLP is DeviceLock Core, which can be used alone as the basic configuration of this product.
It granularly controls data access and transfer operations locally on protected endpoints, based on the operation’s context such as involved users, used channels, accessed/transferred data type, flow direction, date and time, etc. These context-aware controls govern user access to peripheral devices and ports, document printing, clipboard copy/paste operations, screenshot capturing, media format and eject operations, file type detection access controls, and synchronizations with locally connected mobile devices.
- Integrated central management framework - Includes all central management and administration components of Acronis DeviceLock DLP.
- Granular controls – Granularly controls local data flows, based on device class, user group, or unique device identifiers.
- Connection-interface-independent – Detects the true device type and enforces context-aware controls based on it, regardless of the connection interface used.
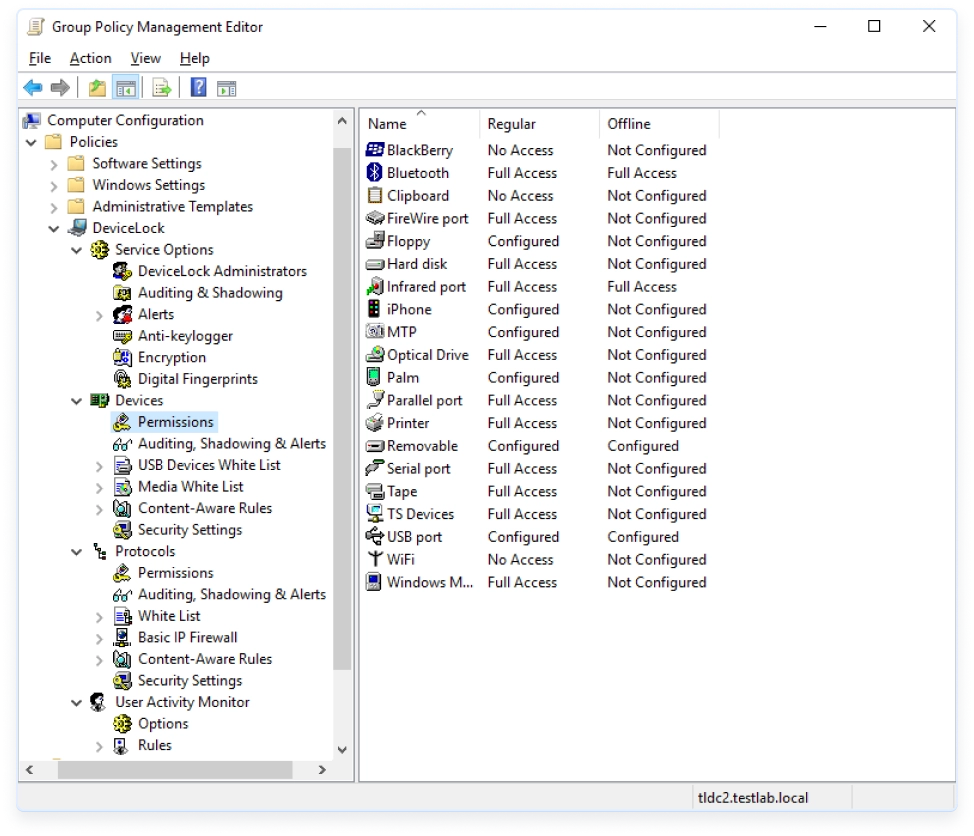
This optional add-on module to Acronis DeviceLock Core expands context-aware controls to network communications of protected endpoints.
Acronis DeviceLock NetworkLock controls network data flows through most risky applications and protocols. These include popular email platforms, webmails, instant messengers (IMs), cloud-based file storage, social media, web access, web search engines, local network shares, and torrent P2P file sharing, as well as FTP and Telnet protocols.
- Deep packet inspection (DPI) – Application- and browser-independent controls over network communications via SMTP, HTTP/HTTPS, WebDAV, FTP, Telnet, and P2P file sharing to detect the protocol and application type regardless of the network ports they use.
- Inspect encrypted traffic – The ability to inspect both plain and SSL-protected traffic allows you to enforce context-aware controls over a wider range of network data flows, as well as extract data transmitted in SSL-tunnels for further content inspection.
- Stateful IP Firewall – Selectively filter network communications uncontrolled by Acronis DeviceLock NetworkLock’s DPI.
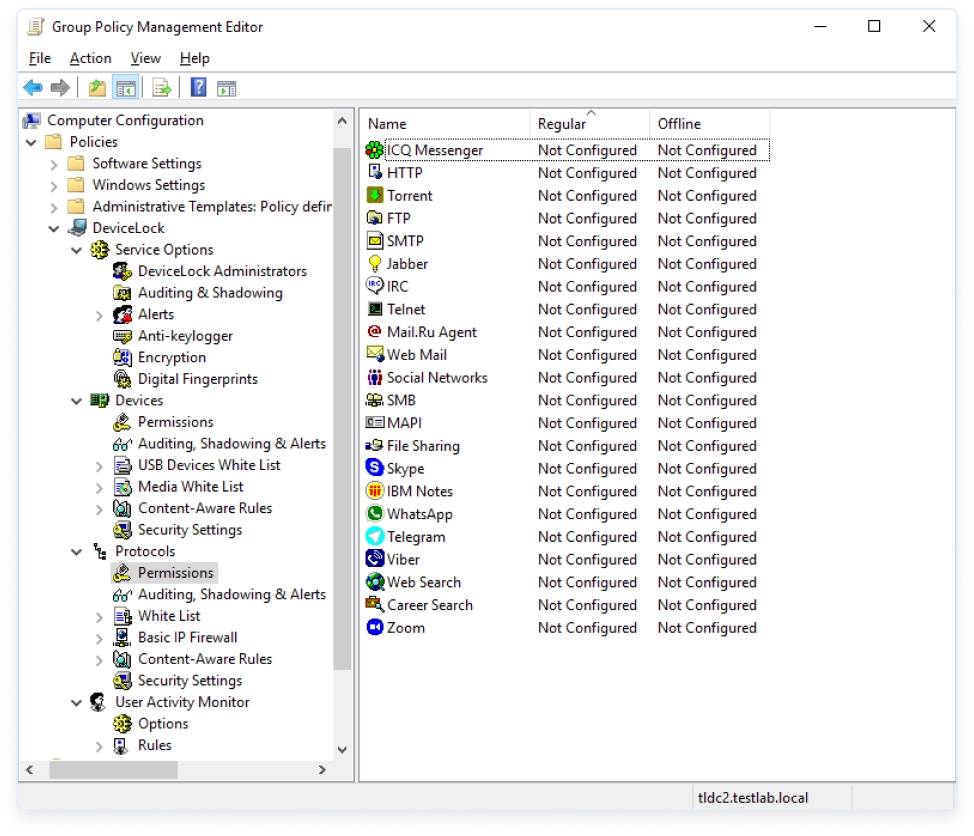
This add-on component expands the functions of Acronis DeviceLock Core and Acronis DeviceLock NetworkLock with content-aware controls over local and network channels.
Acronis DeviceLock ContentLock performs content inspection and filtering of files and other data objects used on or transferred from the protected computer to enforce controls based on the sensitivity of detected content. Acronis DeviceLock ContentLock can identify and inspect three general categories of content: textual data, binaries, and various data and metadata types.
- Verified file type – Inspect a file’s binary content to reliably detect the actual file type regardless of its extension or file name, and enforce controls based on this information.
- Universal content detection – Detect both structured textual data based on industry and contry-specific keyword dictionaries and regular expression patterns, as well as unstructured binary and textual content by using data fingerprinting.
- Data classification support – Identify classification labels assigned to documents and files by Boldon James Classifier products. Automatically classify corporate data into pre-built or user-defined classification levels.
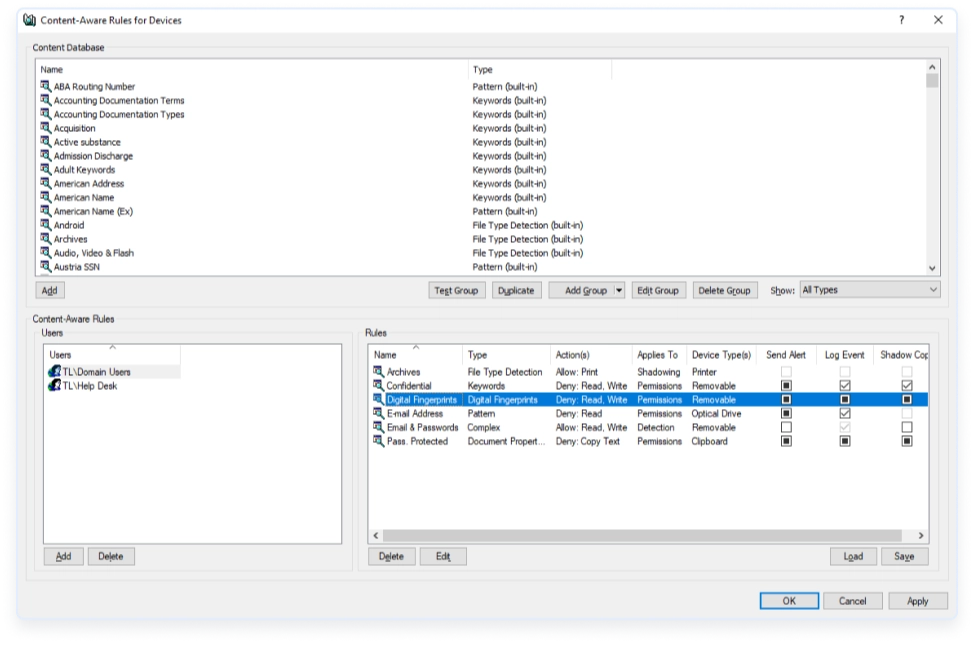
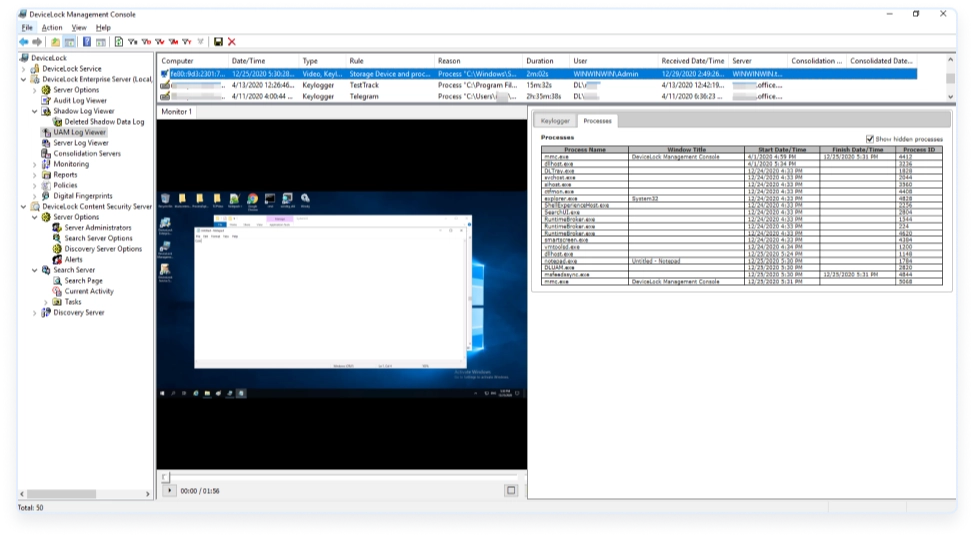
This optional add-on module to Acronis DeviceLock Core enables monitoring of end-users activities based on DLP-related events. UAM expands the evidence base for security incident investigations and simplifies the detection of suspicious user behavior and misuse of access privileges.
Acronis DeviceLock User Activity Monitor records the user’s computer screen together with on-screen actions, keystrokes, and information about applications that were used on the computer during recording. UAM logs are automatically collected to the central DLP log database. Security administrators can use built-in tools for viewing and analyzing UAM logs both locally at the endpoint and in the central log database.
- Configurable recording rules – Recording of end-user activity can be triggered or stopped based on system state parameters or DLP events. Independent UAM policies can be configured for endpoints on the corporate network and ones that are offline or off-site.
- Centralized log collection – UAM logs are automatically collected in the central storage database. A maximal log size can be defined with various override options and a configurable storage duration.
- Built-in UAM log viewers – View and analyze recorded UAM sessions both locally at the endpoint and centrally on the log server by using integrated log viewers with a video player for screen recordings, keystroke viewer, and process viewer.
A standalone product that scans corporate endpoints, network attached storage systems, file shares, and Elasticsearch databases to locate exposed sensitive content stored at the wrong places and protect it with automatic, configurable remediation actions and alerts to IT security administrators and SIEM systems. Acronis DeviceLock Discovery enables organizations to gain visibility and control over confidential “data-at-rest” stored across their IT environment to proactively prevent data breaches and help achieve compliance with regulatory and corporate data security requirements.
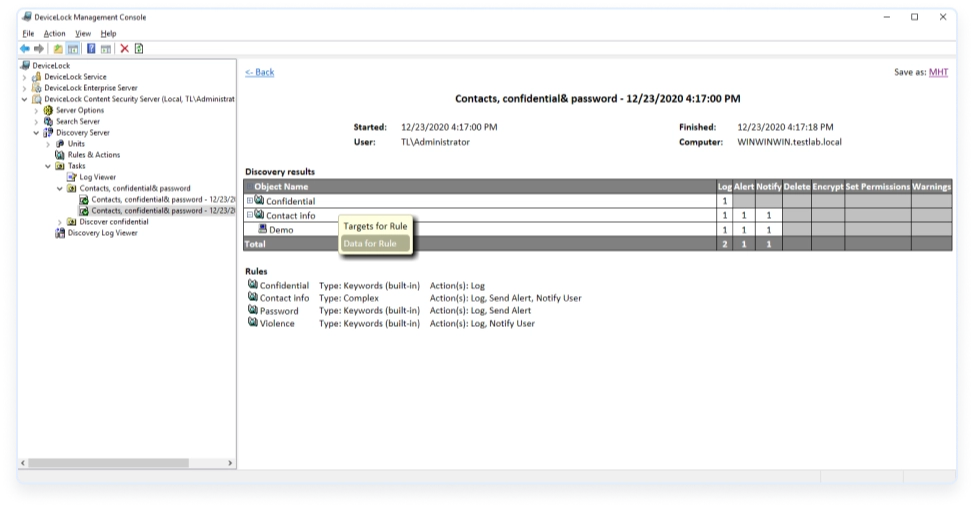
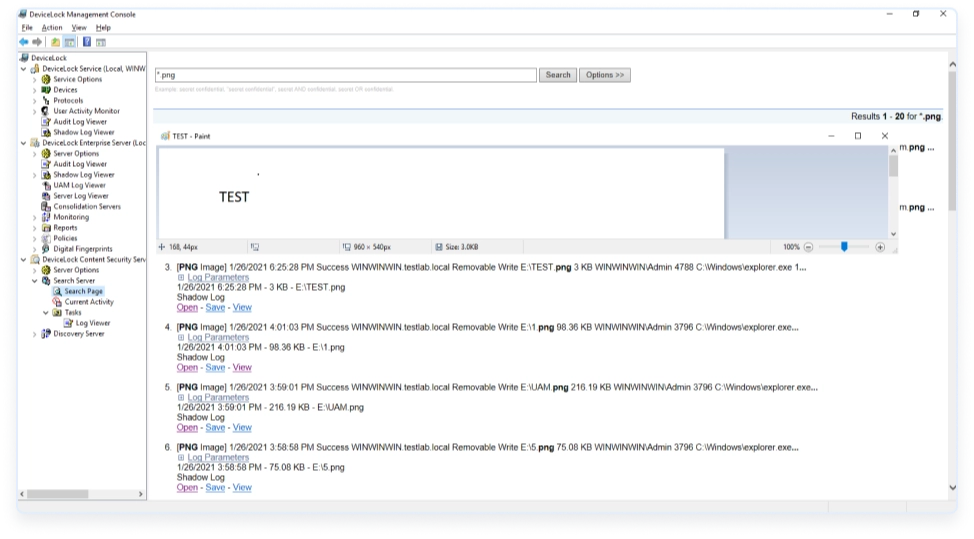
An optional, standalone post-analysis component – Acronis DeviceLock Search Server (DLSS) can be used to perform full-text searches in the central audit log database, shadow log, and file repository populated with data by Acronis DeviceLock agents. Acronis DLSS is aimed at making the labor-intensive processes of log analysis during information security audits and incident investigations much faster and more accurate.
Acronis DeviceLock DLP
72% of employees share sensitive information. Prevent any data leaks headed your way.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.