Stop data leaks at the source with complete endpoint data loss prevention (DLP)
Centralized management and deployment
Ease the labor-intensive and resource-consuming processes of DLP deployment and managment by choosing from a flexible set of central management consoles with the same UI. Depending on the organization’s IT environment, SMBs or large enterprises can choose the console that best fit their needs.
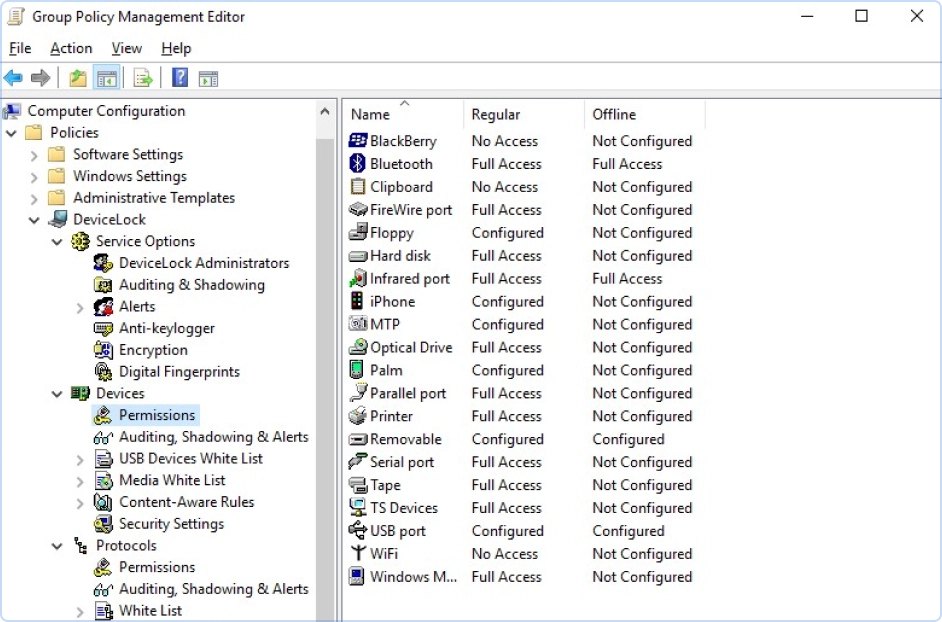
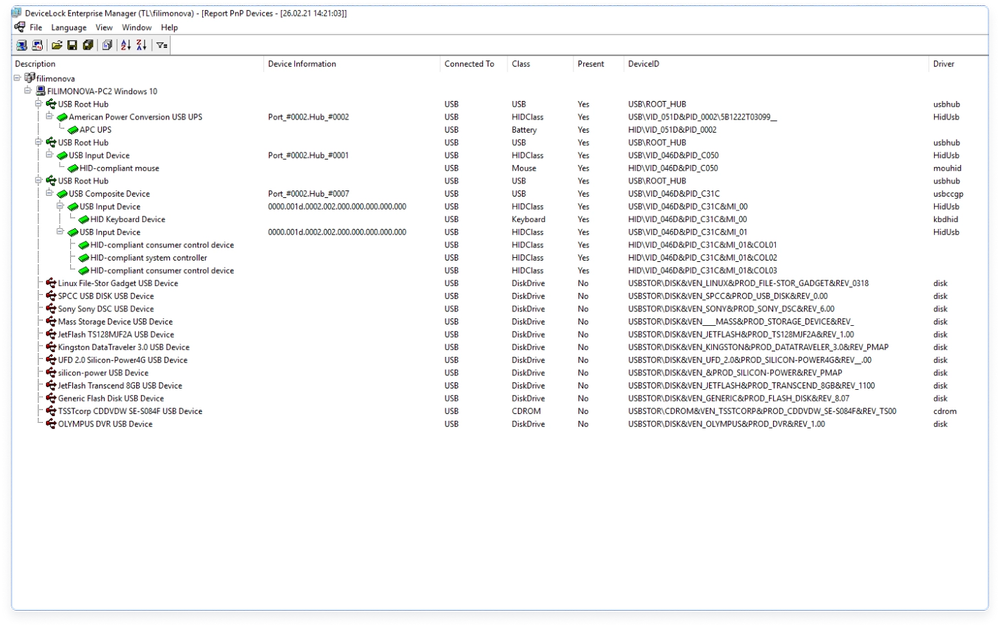
- Active Directory integrationCut learning times and administrative efforts with a console based on the custom Acronis DeviceLock MMC snap-in to the Microsoft Group Policy Management Console used as the Active Directory Group Policy interface. This native integration enables Acronis DeviceLock DLP agents to be deployed and fully managed via Group Policies.
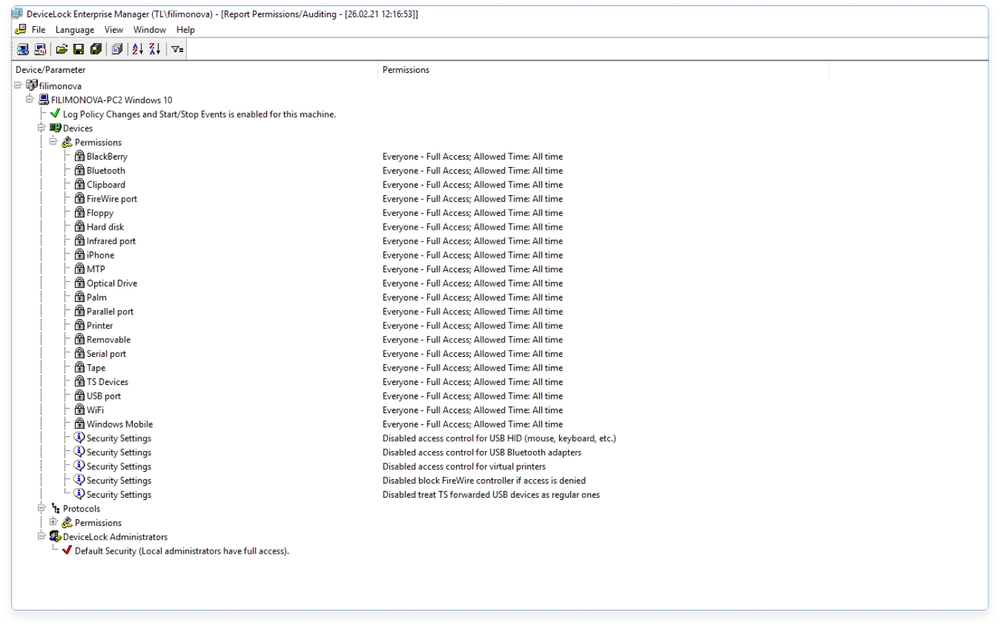
- Non Active Directory environmentsIn non-AD environments, administration is done through Acronis DeviceLock Enterprise Manager, a native Windows app that runs on a separate computer. DLP policies are delivered to all agents (pushed or pulled) via Acronis DeviceLock Enterprise Server (DLES).
- Directory-less installationsIn such IT environments, e.g. in a Windows for Workgroups network, as well as for managing Acronis DeviceLock Discovery, the custom Acronis DeviceLock MMC snap-in can be used to remotely manage agents on per-endpoint basis.
Proactive protection
- Universal
Tamper protection
Enforce process compliance by preventing tampering with DLP policy settings locally on protected endpoints, even by users with local system administrator privileges. Only designated Acronis DeviceLock DLP administrators can uninstall or upgrade the agent, or modify DLP policies. - Universal
Printing security
Control network and local printing from Windows endpoints by enforcing DLP policies over user access and content of printed documents for network, local, and virtual printers. Ensure higher data security by intercepting and inspecting print spooling operations, allowlisting of USB-connected printers, and print data shadowing. - Universal
Network-awareness
Administrators can define different online vs. offline DLP policies for the same user or user group. A reasonable and often necessary setting on a mobile user’s laptop, for example, is to disable Wi-Fi when docked to the corporate network and enable it when undocked.
Allowlisting
Allow granular controls over data access and transfer operations with the ability to manage exclusions to general DLP rules through wide allowlisting capabilities.
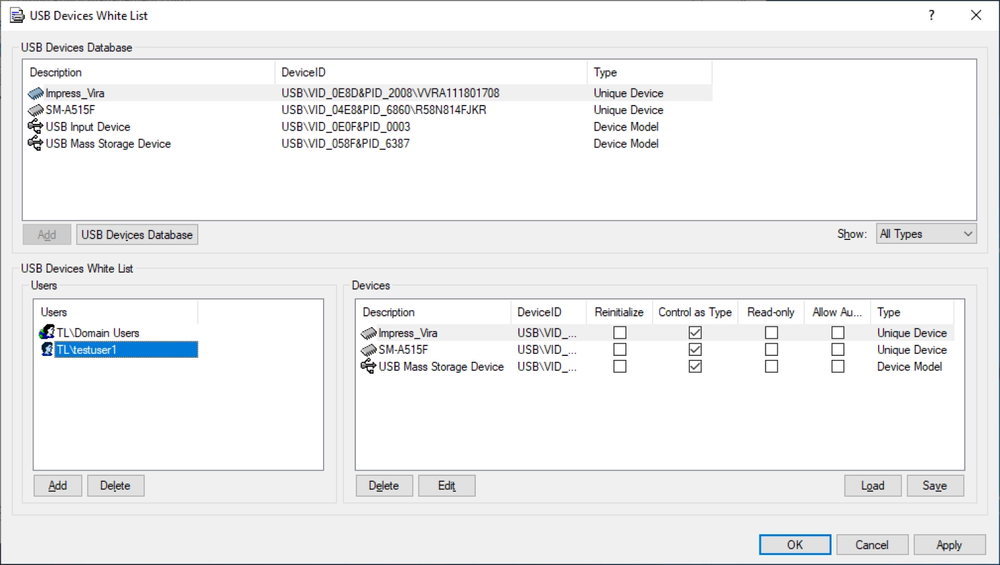
- CoreUSB allowlistAllows administrators to authorize a specific model of devices or particular device, distinguished by a unique identifier such as a serial number, to access the USB port, while locking out all other devices.
- CoreMedia allowlistEase the distribution of authorized software by authorizing the use of specific DVD, BD, and CD-ROM disks, uniquely identified by data signature. Granularly control authorized users and groups that can access them.
- CoreTemporary USB allowlistFor using USB devices on endpoints working out of the corporate network, a temporary access to a USB-connected device can be provided by issuing an access code delivered to the user out of-band, rather than through regular Acronis DeviceLock DLP permissions procedures.
Increase process compliance
- Universal
Virtual DLP
Prevent data leaks via BYOD devices when using leading remote virtualization solutions. Running on a VDI host or terminal server, Acronis DeviceLock DLP enforces context- and content-aware controls over data exchanges between the virtual workspace and the personal part of the BYOD device, its local peripherals, and the network. - Core
Removable media encryption integration
Increase data security when copying information to removable media by allowing data to only upload to removable storage encrypted by a set of best-of-breed, integrated encryption solutions. Selectively allowlist encrypted USB media to strengthen internal compliance. - Universal
Alerting
Shorten reaction times with real-time notifications on DLP-sensitive user activities on protected endpoints within and outside the corporate network. Acronis DeviceLock DLP provides SNMP, SYSLOG, and SMTP based alerting capabilities to SIEM systems and administrators.
Comprehensive log collection for increased visibility
- Universal
Auditing
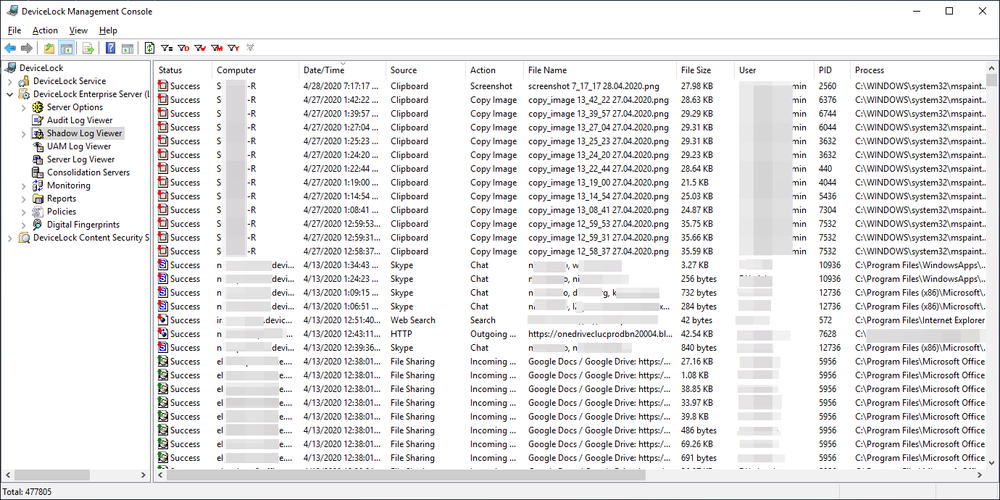
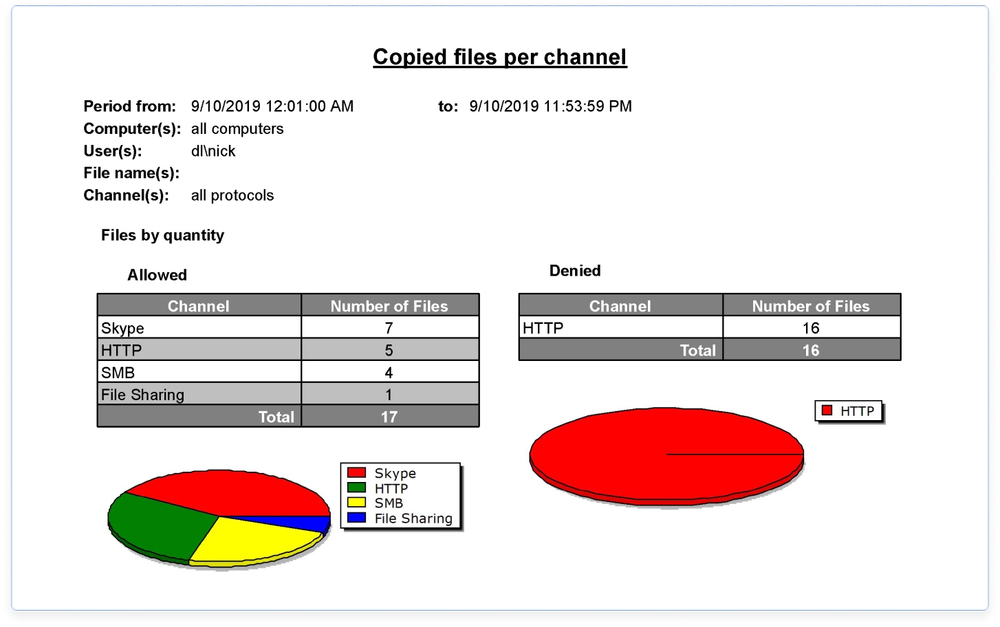
Track user and file activities for specified device types, ports, and network resources on a computer and collect logs with GMT timestamps centrally in a Microsoft SQL or Postgres database. Pre-filter audit activities by event and context. Audit logs can be exported to many standard file formats for use in other reporting tools. - Core
Data shadowing
Enable security compliance auditing, incident investigations, and cyber forensics by mirroring data transferred without authorization via local and network channels. Leverage data shadowing that’s triggered based on operations context and content. Pre-filter shadow activities for network load balancing. - Universal
Monitoring
Monitor remote computers in real-time with Acronis DLES, checking agents’ status, policy consistency, and policy integrity and writing information to the monitoring log. Define a master policy to be applied across selected remote computers in the event that their current DLP policies are out-of-date or damaged.
Acronis DeviceLock DLP
72% of employees share sensitive information. Prevent any data leaks headed your way.
Looking for help?
Frequently asked questions
Can Acronis DeviceLock DLP function without internet connection?
There are two different sets of DLP policies, Regular and Offline, which are automatically applied to a controlled endpoint by Acronis DeviceLock DLP agents depending on its network status. The Offline policy can be triggered by the laptop using either cached or confirmed Windows credential authentication, whether it can connect to any of its known Acronis DeviceLock Enterprise Servers, or if in a wired vs. unwired state.
Is Acronis DeviceLock DLP capable of “passive mode” functioning, i.e. not restricting data transfer, but logging and shadow copying?
Yes, Acronis DeviceLock DLP is capable of functioning in any administrator set mode. We also call this “observation mode”.
In cases where access to ports, devices, or network protocols is not blocked or content-filtered by policy, logging and data shadowing policy can be actively logging and keeping records in audit and shadow logs in “passive mode”.
If there is a restrictive access policy active, Acronis’ DLP solution blocks the transfer and prevents data leakage on a controlled endpoint in real time.
Is there an option to configure various access control policies for laptops in- and out of the corporate network?
Yes, there is. Acronis DeviceLock DLP supports various on- and off-corporate-line security policies. This way you can have one policy when the laptop is behind the firewall or DMZ and a totally different policy when the laptop is out in the wild, strengthening DLP security.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.