Conti ransomware shuts down backup services and unlock files with Windows Restart Manager before encryption
Summary
- First seen in December 2019.
- The average demand for this ransomware is under $100,000.
- Uses Windows Restart Manager to close open and unsaved files before encryption.
- Contains more than 250 strings decryption routines and about 150 services to be terminated.
- Performs fast file encryption in 32 simultaneous threads using Windows I/O Completion Ports.
- The ransomware follows the trend and recently has launched the 'Conti.News' data leak site.
Conti is a ransomware that supposedly inherits its code from Ryuk family and used in targeted attacks against enterprises since December 2019. Recently, Conti operators started the data leak site called ‘Conti.News’ to publish stolen data in case the ransom is not paid. Being a successor of Ryuk ransomware, Conti can be delivered by Trickbot trojans. Conti also implements the Ransomware-as-a-Service model
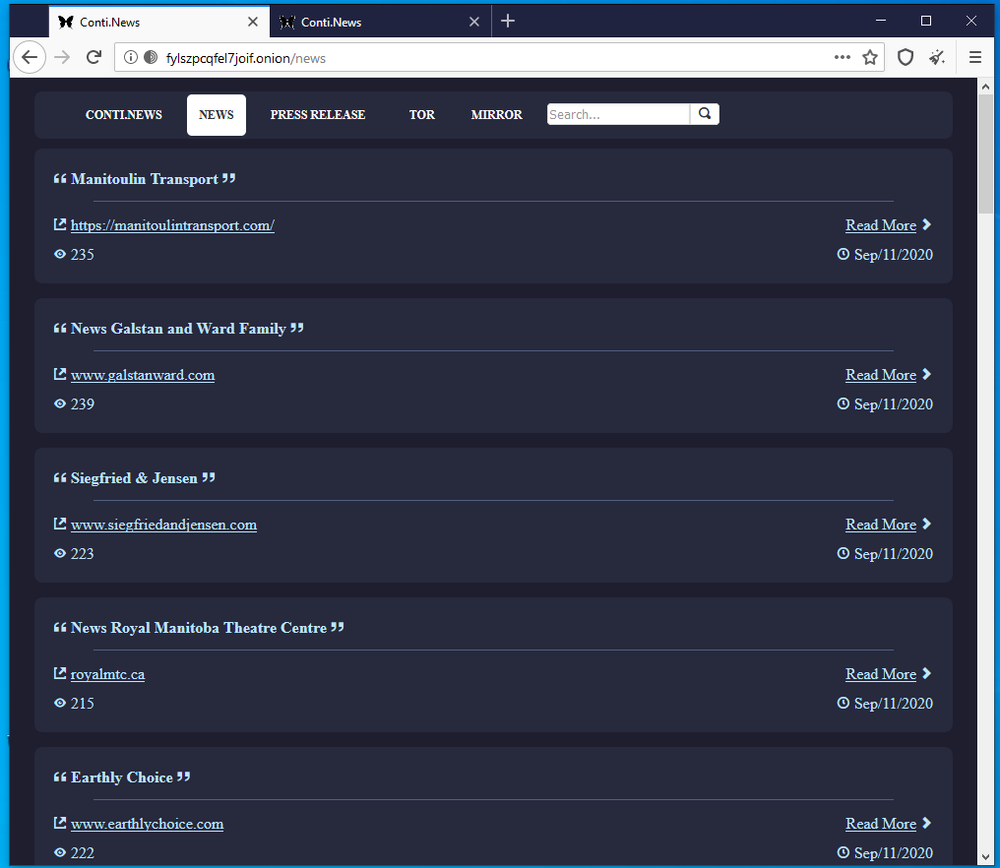
fylszpcqfel7joif.onion site is created for publishing stolen company’s data.
Operation modes
The Conti ransomware can be launched with one of the two parameters: ‘-h’ and ‘--encrypt-mode’.
- ‘--encrypt-mode’ indicates which files are being encrypted, there are 3 possible values: ‘all’, ‘local’, ‘network’. ‘all’ supposes both types of encryption, local and network. Network encryption means to encrypt shared resources inside the local network. By default, ransomware is run with ‘all’ parameters.
- ‘-h’ parameter should be run with corresponding filename, where the list of DNS or NetBIOS names of the remote servers is written on which the function NetShareNum() is to execute. By default ‘-h’ is assigned to null, to retrieve information about each shared resource on a current computer.
ProliferationThe ransomware is looking shared resources inside the local network by the local following IP address patterns:
● “172.”
● “192.168”
● “10.”
Killing services
The ransomware deletes shadow copies of the files and resizes shadowstorages for disks from C: to H: that may also result in shadow copies disappearing.
cmd.exe /c vssadmin Delete Shadows /all /quiet cmd.exe /c vssadmin resize shadowstorage /for=c: /on=c: /maxsize=401MB cmd.exe /c vssadmin resize shadowstorage /for=c: /on=c: /maxsize=unbounded cmd.exe /c vssadmin resize shadowstorage /for=d: /on=d: /maxsize=401MB cmd.exe /c vssadmin resize shadowstorage /for=d: /on=d: /maxsize=unbounded cmd.exe /c vssadmin resize shadowstorage /for=e: /on=e: /maxsize=401MB cmd.exe /c vssadmin resize shadowstorage /for=e: /on=e: /maxsize=unbounded cmd.exe /c vssadmin resize shadowstorage /for=f: /on=f: /maxsize=401MB cmd.exe /c vssadmin resize shadowstorage /for=f: /on=f: /maxsize=unbounded cmd.exe /c vssadmin resize shadowstorage /for=g: /on=g: /maxsize=401MB cmd.exe /c vssadmin resize shadowstorage /for=g: /on=g: /maxsize=unbounded cmd.exe /c vssadmin resize shadowstorage /for=h: /on=h: /maxsize=401MB cmd.exe /c vssadmin resize shadowstorage /for=h: /on=h: /maxsize=unbounded cmd.exe /c vssadmin Delete Shadows /all /quiet
The next step is stopping services that belong to SQL, antivirus, and backup and cyber security solutions such as BackupExec and Veeam. It also tries to terminate the Acronis Cyber Protection solution, but fails due to our self protection feature. List contains about 146 services, most of them are SQL databases. The Acronis self-protection technology successfully prevents the backup services from being terminated by the ransomware.
The last step before encryption is terminating SQL-related processes. The predefined “sql” string is matched with the list of the running processes.
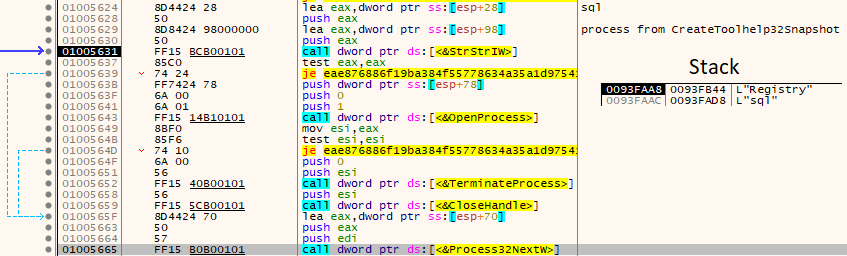
Unlocking files
To unlock the currently opened files for encryption, Conti calls Windows Restart Manager to force the files closing. To do that, Conti loads an unusual for malware dynamic linking library rstrtmgr.dll for operating with the Restart Manager service. In short, Restart Manager is responsible for saving and not damaging open and unsaved files before system reboot. It prompts the user to save his data before the system will be shut down. The main feature which is abused by Conti is files unlocking. Before a file will be encrypted, it is checked by the piece of code below, to ensure that file is unlocked and can be closed immediately to prevent the file from being damaged as much as possible.
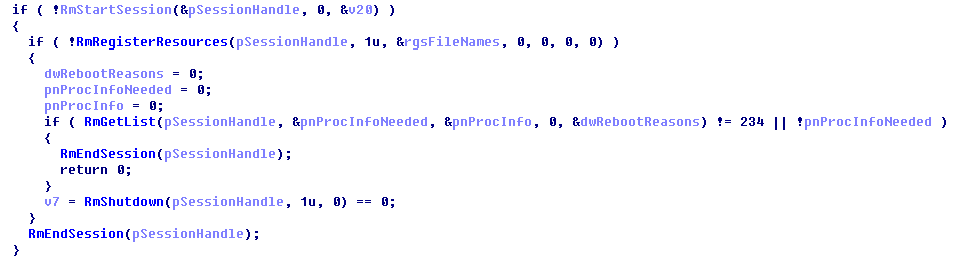
Encryption
Conti ransomware uses RSA-4096 and AES-256-CBC encryption algorithms. The embedded public master RSA-4096 key is used for encrypting AES keys generated per file and appending them in the footer of every file.
Conti`s encryption is implemented using Windows I/O Completion Ports to speed up the encryption process by running 32 concurrent threads.
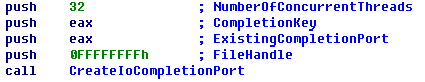
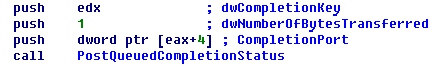
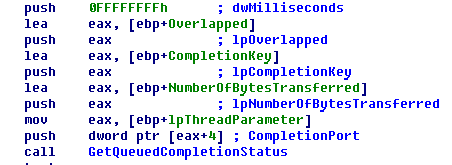
Lastly, Conti retrieves the result of file encryption using GetQueuedCompletionStatus() and adds the encrypted AES-256-CBC file key to the footer.
The hardcoded master RSA-4096 key is imported from the ‘.data’ section to the Microsoft Cryptographic Provider.
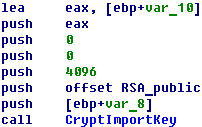
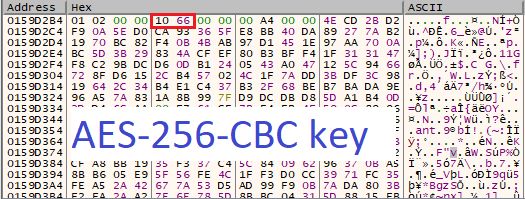
The folders that are ignored during encryption:
tmp
winnt
Application Data
AppData
temp
thumb
$Recycle.Bin
$RECYCLE.BIN
System Volume Information
Program Files
Program Files (x86)
Windows
Boot
The file extensions that are skipped by ransomware:
.exe
.dll
.lnk
.sys
.CONTI
The encrypted files are appended with ‘.CONTI’ extension and look as follows.
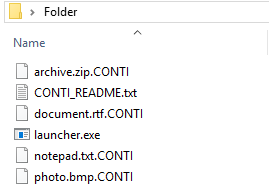
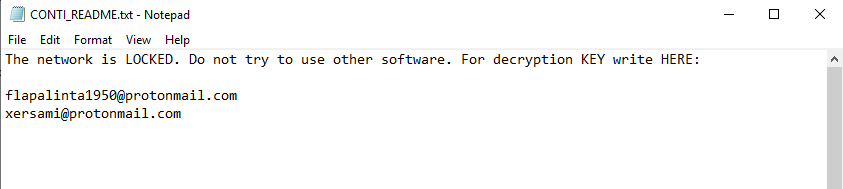
Ransom note
CONTI leaves a ransom note in every folder to notify a user about infection. It does not generate a user ID and asks to write to one of the email addresses mentioned in the note.
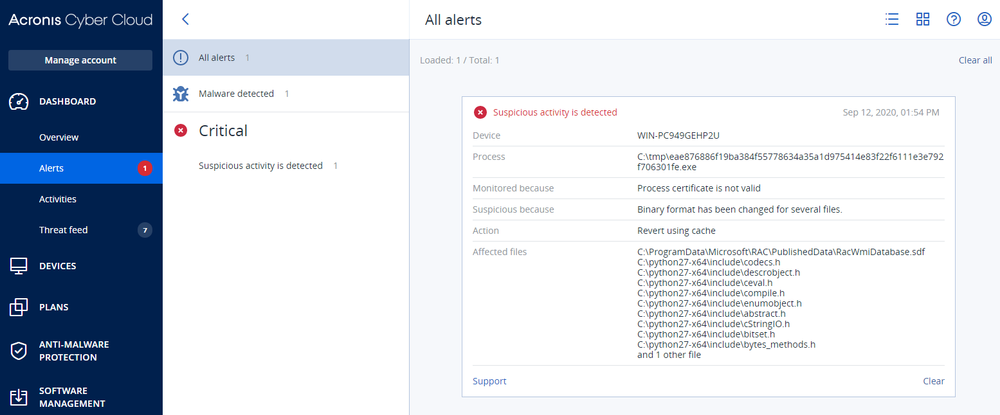
Detection by Acronis
Acronis Cyber Protection successfully blocks Conti ransomware with the help of anti-ransomware protection engine and restores encrypted files.
IoCs
MD5: c3c8007af12c9bd0c3c53d67b51155b7 SHA256: 8c243545a991a9fae37757f987d7c9d45b34d8a0e7183782742131394fc8922d Mutex =_CONTI_ .CONTI extension CONTI_README.txt flapalinta1950@protonmail.com xersami@protonmail.com
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



