With so much happening on our mobile devices and laptops nowadays, cybercriminals do everything to get hold of our digital accounts — especially our login credentials. As we live in a digital age, we have multiple login details for our emails, online subscriptions, online banking and many more. But how can you track them and ensure they are secure and protected?
First, every account should have a unique password and follow these rules:
- More than ten characters.
- Be complex.
- Use a combination of letters, numbers, symbols and cases.
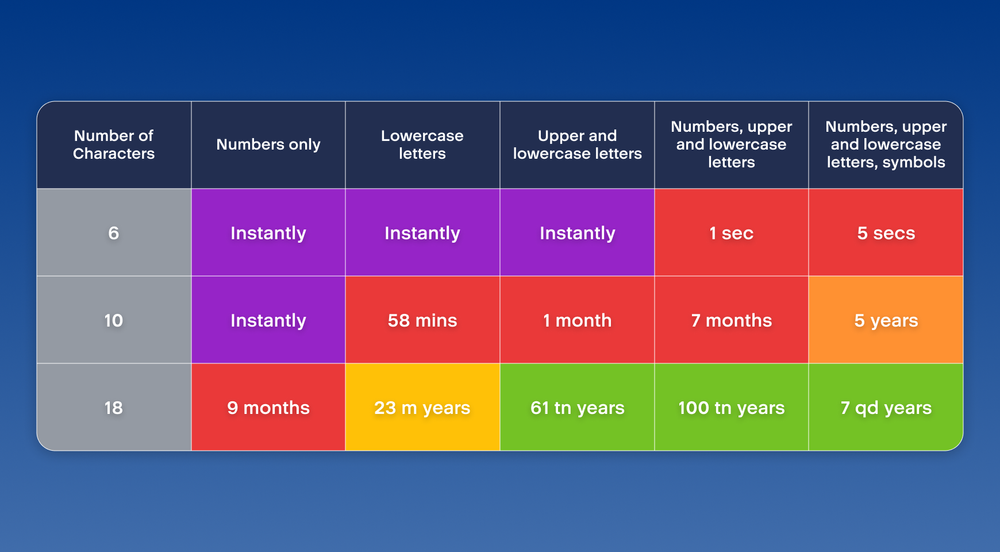
Below is an example of how long it takes for cybercriminals to brute-force your password. A brute force attack on your login details is when cybercriminals use trial-and-error to guess your details.
The importance of 2FA
How can I make my password even stronger? Well, it’s pretty simple — use two-factor authentication, also known as 2FA, for all your digital accounts.
In short, it confirms that users are who they say they are. It is an extra layer of security. The way it works, you enter your username and password and before you can gain access, you will be required to provide another piece of information to validate it’s you. Therefore, 2FA consists of two authentication elements.
The first authentication element is:
- Something you know: a pin number, a password, answers to specific questions.
The second authentication element, which is the additional security layer ― is something that cannot be easily replicated:
- Something you have: a credit card, a smartphone or a hardware token.
- Something you are: a fingerprint, an iris scan or a voice print.
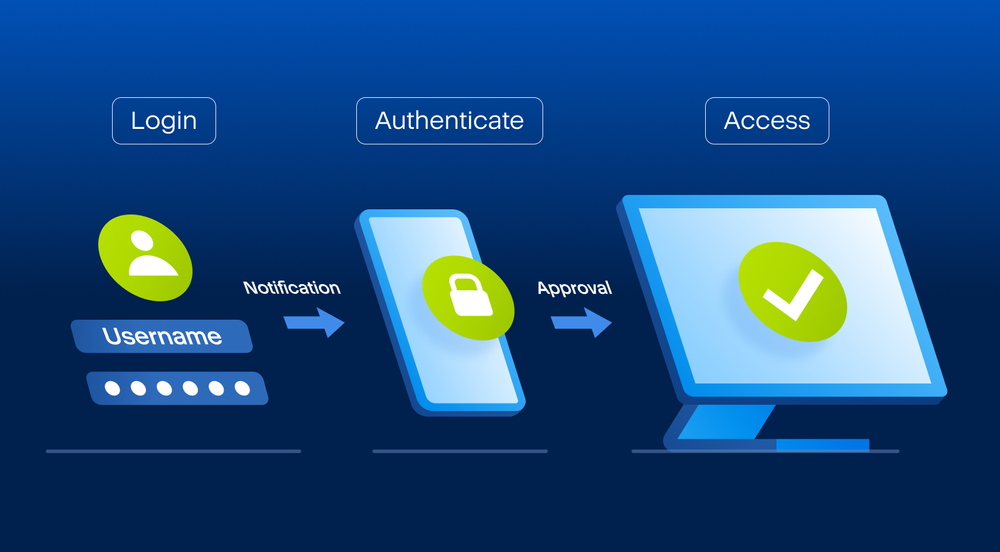
How does 2FA work
When you sign into your account, typically, you’re asked to enter your username and password. This is the first authentication element. After that comes the second element (2FA), a one-time password, a text message with a verification code or a USB or key fob.
Types of authenticator apps
There are a few apps available to help you with 2FA.
• YubiKey ― a physical key that provides the ultimate security, using your fingerprint to authorize.
• Google or Microsoft Authenticator — an app on your mobile phone (Android or iOS) that generates real-time authentication codes that change every 30 seconds.
• 2FAs ― an app on your mobile phone (Android and iOS) that generates real-time authentication codes that change every 30 seconds.
Advantages and disadvantages of the different types of 2FA
As explained earlier, there are different kinds of 2FA elements.
1. A device such as a physical key
Advantages:
- High security. Physical devices like security tokens or smart cards are less susceptible to remote attacks like phishing or keylogging.
- Offline access. These devices generate codes locally to work without an internet connection.
- No need for a mobile device. Unlike OTPs sent via SMS or apps, physical devices do not rely on a specific smartphone or app.
Disadvantages:
- Inconvenience. Carrying an extra device can be inconvenient and if you lose the device, you might lose access to your accounts.
- Cost. Some physical devices might incur initial costs, especially for organizations implementing them on a large scale.
2. Mobile app
Advantages:
- Convenience. Most people carry their smartphones everywhere, making this method convenient.
- Multiple account support. A single app can generate codes for multiple accounts.
- No network dependency. Many authenticator apps can work offline, generating codes even when the phone is not connected to the internet.
Disadvantages:
- Dependence on a device. An attacker can gain access if you lose your phone or it's compromised.
- Backup challenges. You must carefully back up the app's recovery codes or transfer the app when getting a new phone.
- Potential SIM hijacking. If an attacker can hijack your SIM card, they might intercept SMS-based authentication codes.
3. Biometrics
Advantages:
- Easy to use. Biometric authentication is often seamless and user friendly.
- Difficult to replicate. Biometric traits are unique and challenging to replicate.
- No need to remember codes. Since you're using your biological traits, you don't need to remember passwords or codes.
Disadvantages:
- Privacy concerns. Storing biometric data could raise privacy concerns, as compromised biometric data cannot be changed like a password.
- False positives or negatives. Biometric systems can sometimes produce false positives (mistakenly recognizing someone else as you) or false negatives (failing to recognize you).
- Lack of universality. Not all devices or systems support the same biometric methods, limiting cross-platform applicability.
2FA best practices
There are several best practices when it comes to using 2FA, including:
• Use long passwords — minimum ten characters, with numbers, upper and lowercase letters and symbols — otherwise, they are too easy to crack by cybercriminals.
• Never use a password twice.
• Use 2FA to ensure you are the one accessing your online account.
• Always keep all software up to date with the latest version.
• Make secure backups of your data and never wait for the unexpected to happen.
A solution with 2FA and identity protection
Acronis True Image is the #1 personal cyber protection solution with secure backup with built-in 2FA and identity protection.* Now you can secure your data and protect your identity — as our lives are more digital and attracting cybercriminals. Stolen security numbers or other information allows thieves to open credit cards and take loans, including selling this personal information on the dark web. Get the protection you need with Acronis True Image.
In conclusion, 2FA helps you and your family safeguard your life in this modern digital landscape. When you are using it, it’s a proactive step towards protecting one's digital identity, sensitive information and valuable resources. Stay safe and secure and make use of two-factor authentication.
*Only available in the U.S. for Advanced and Premium subscriptions.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



