Cyberattacks occur daily and you need to have information on them to be able to defend yourself, both by preventing the attack from happening and by knowing how to solve the damage they may have caused, because they cannot always be avoided. With this method, cybercriminals obtain very valuable data and personal information with which they can steal the identity of the victim. But they can be avoided, do you want to know how?
What is phishing and what data does it look for
This type of malware attack is executed to trick the user into accessing a fake website or providing private and confidential information. What interests them most are the passwords and access codes to sites where there may be interesting information, such as the codes to access the bank's website, PayPal, eBay, social media, the business network, etc.
Not only are they interested in bank details, but also, in many cases, the confidential information of a company or a professional can be the target of this type of attack, where the victim inadvertently reveals relevant information about their company, business, or important projects.

It is common for companies to share important files on the network, both on the local network and on the Internet, which employees access through a username and password. Can you imagine if any of them suffer a phishing attack? Confidential company information could be exposed. The problem is aggravated if you do not have a business backup that, at least, allows you to recover the data.
Since today we store information in many places, the cloud and the data access codes stored there are also the target of these hackers. The technology of smartphones and tablets increasingly allow us to access important sites such as banks, social media, payment platforms, and more, so attacks on these devices are multiplying. Laptops, servers, and desktops (PCs or Macs) are not the only ones susceptible to attacks.
Professionals increasingly share important files on platforms that can be the target of phishing. Imagine a freelancer who writes a book and uploads it to the web, and before it can be published, someone steals it and impersonates it. How could I have prevented it?

How it all starts
The most normal thing is that the user receives an email with a link to access a website that, although similar to the original, turns out to be fake. On this website, the user is asked to identify himself/herself and, in this way, they obtain the victim's data. If the attack reaches a company's Exchange server, it will quickly spread to many employees, and who knows if someone will fall for the fraud.
Not only do they contact victims through an email, but sometimes, they put fake links on other websites. In this way, we access a website to read information about something that interests us and, there, we find a link as part of the content, and that link can lead us to a fake website. Once again, here they can request confidential data and that is how easily they get the information they want. Attachments in emails are usually another hook to find victims.
How it is usually recognized
There are some clues by which we can detect that something is not going well, and it is important to always keep them in mind, whether it is done from a mobile phone, or if it is done from a computer or tablet. The operating system is not a problem, no matter which one is used. Remember to protect your iPhone, iPad or Android devices.
- Language is not a limit for these fraudulent emails, but many times they have been translated automatically, so the way of expressing themselves is not correct. There are spelling or grammatical errors that, obviously, a bank or important company does not usually make. This can help us detect that it may be fraud.
- They offer gifts, discounts, or amazing surprises to get the user's attention. If it seems too much for you and you also have nothing to do with that website, why would they give you a car, a prize, or money? If you receive a prize from a website where you have not participated, you almost certainly do not have any prize. Run away!
- The website you are redirected to when you click on the link is not exactly what you were used to seeing when you accessed your social media, your bank, or that platform where you have a user. What has changed? Check the URL because it is usually similar, but not the same as the original. It is a fraudulent copy.
- You receive an email from a bank of which you are not a customer, alerting you to a problem and asking you to log in to identify yourself. Obviously this attack is going nowhere, but what if you are a customer of the bank? If it turns out that you are, then you could click and access, giving the confidential data to hackers.
- The "To" field of the mail does not have any recipient, it appears blank. Really, any respectable company will send you a personalized email, with your name and surname, addressed exclusively to you. If this does not happen, you become suspicious.
- One technique used in these phishing emails is to alert you to something and ask you to act urgently. For example, "if you do not access in the next 24 hours, we will cancel your account", or "someone has tried to access your account, access here to protect it." In this way, they capture attention and get victims by diverting them to a website that is a fraud and a hoax.
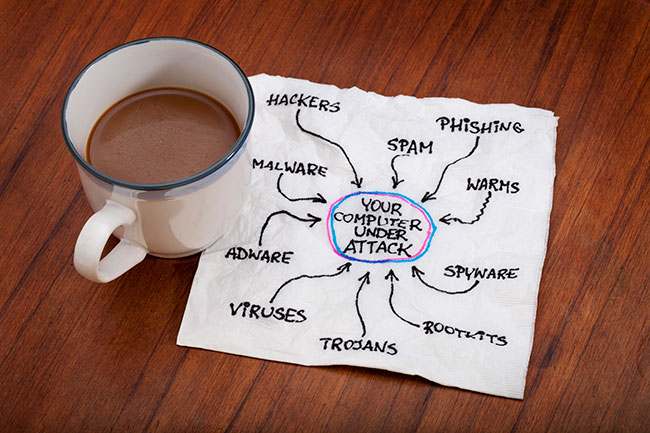
Avoiding phishing
Now you may be wondering what you can do to avoid it. Well, one of the ways to do it is to always be attentive, be cautious and, if you detect any of the ways that we mentioned above in any of the emails you receive, then be careful and take a good look at the links and where you enter your confidential data before doing it, and you better… don't do it.
An antivirus or a good firewall is another way to protect yourself, but keep in mind that hackers know this, and try to find new ways to mislead these programs and go unnoticed, without any security filter detecting them. Everything is in constant advance, both protections and crime, so it all depends on who is more advanced to get to your data. Don't forget to keep your browser and its add-ons updated, as well as your antivirus and firewall.
Having an outdated protection system or introducing a new way of accessing the web may be enough for the attack to occur. Now what? What about my data and my personal information? If you didn't have backup, then you may have lost it.
Never enter confidential data on unsecured websites that do not begin with https:// and if you have questions, do not enter them. And of course, never give confidential data over the phone or in response to any email that requires it. This is not the right way to solve
Data backup
Having a backup is an advantage in case of suffering a malware attack, because in that case, even if they access your data in the cloud and delete it, you will always have all that information available again.
Automatic backups are very convenient and do not involve any inconvenience for the user, who can perform them on a scheduled basis, and in the background, without reducing the performance of their work.
Having the backup of a backup has already helped many people, professionals, and companies to be able to recover from a hacker attack and to be able to restore the information or system quickly and effectively. This avoids many annoyances, and above all, that the business stops due to a phishing attack that may have stolen the identity of the company, for example.
Acronis Backup guarantees the restoration of data and backups of servers, PCs, mobile phones, tablets and, ultimately, of all the devices that we use today. Its experience and awards are well worth your trust, and it offers you the best features and capabilities to protect yourself.
Common sense
Always remember to update the access passwords from time to time, and do not make them all the same, since a single attack can expose you in several accounts.
Always take a good look at the emails you receive, and do not act hastily. Check first that everything is correct and legal.
Make regular backups of all your data, so that, in case of disaster, you always have it available.
Check the origin of incoming emails and the URLs you visit. Strengthen the protection of your device and your data.
And above all, use common sense, that is what probably best prevents you from suffering a phishing attack. You cannot avoid receiving the email, but you can ignore it. It is in your hands!
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



