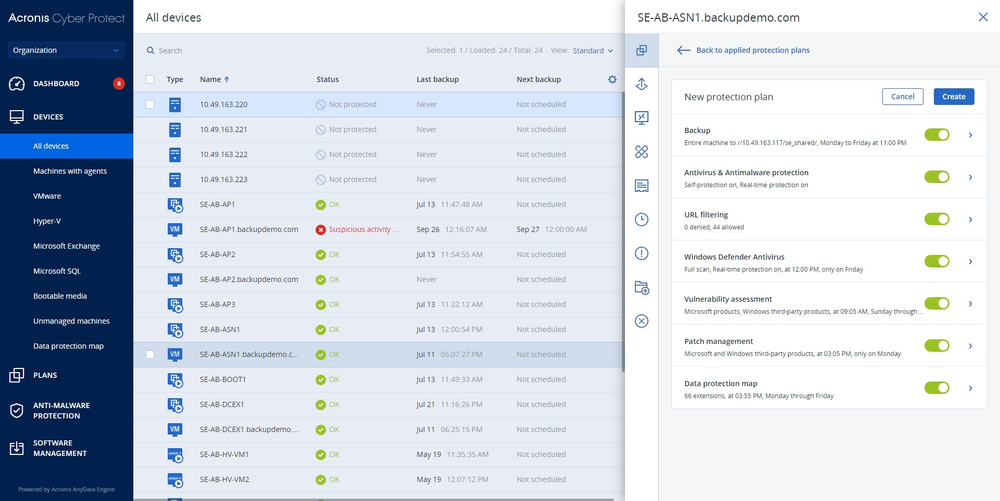
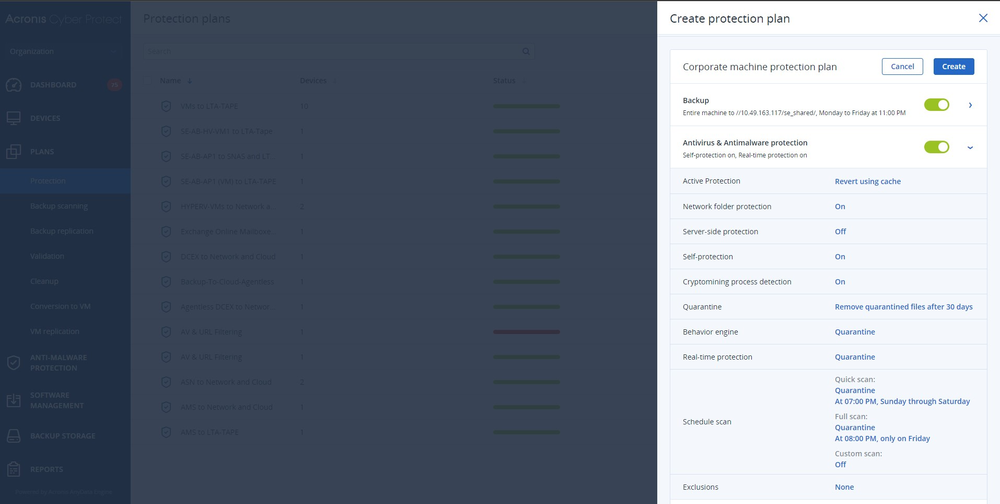
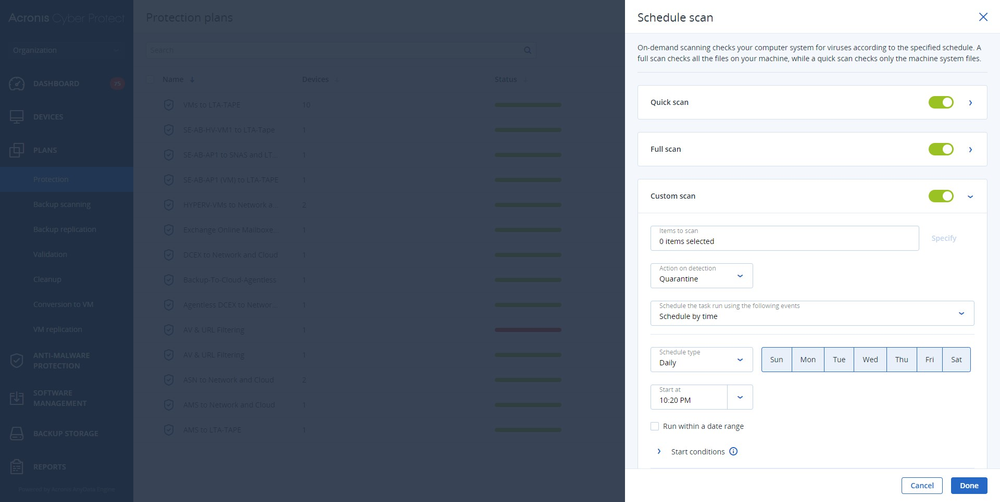
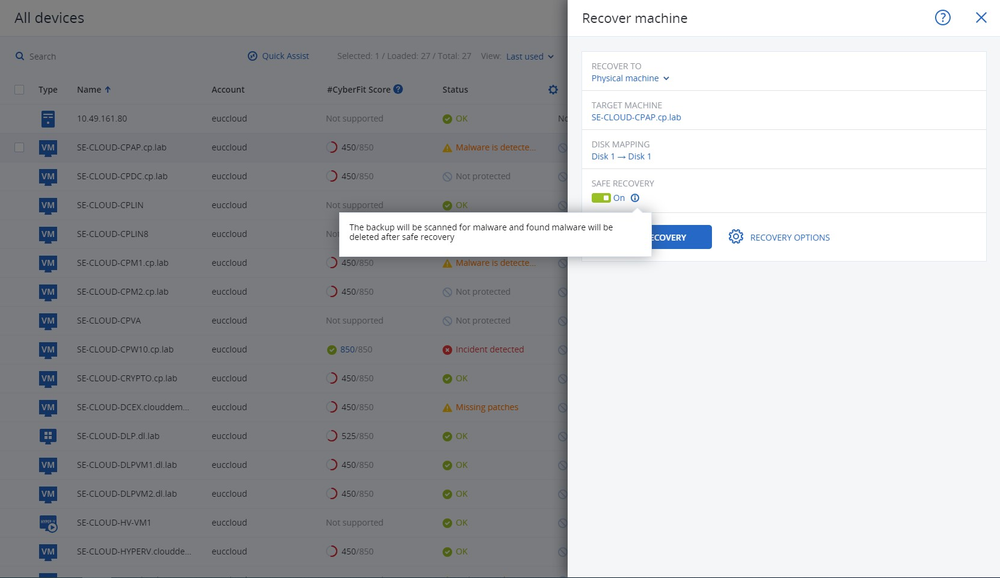
Build cyber resilience
Advanced threat detection and prevention
Multi-layered security to address threats, with AI-assist to detect and mitigate ransomware attacks.Automatic backups
Robust file and image backups with automatic rollbacks and efficient cloud storage.Integrated data protection
Consolidates data protection (backup and recovery) with endpoint security, providing comprehensive cyber defense and recovery.
Unify ransomware defense and recovery
Acronis detects and neutralize new and advanced ransomware, providing powerful defense to safeguard valuable data and ensure business continuity.
- IDENTIFY
- Auto-discovery of new devices
- Vulnerability assessments
- Data protection map
- PROTECT
- Remote agent installation
- Backup and data protection
- Unified protection policies management
- DETECT
- Behavior-centric approach to detect unknown & advanced threats
- Defenses against malware and exploits
- Hard drive health control
- RESPOND
- Rapid incident prioritization & EDR telemetry for rich analysis
- Workload remediation with isolation
- Additional investigation via forensic backups and remote connections
- RECOVER
- Pre-integrated backup and disaster recovery
- Rapid rollback of attacks
- Self-recovery & one-click mass recovery
Ransomware threatens every business sector
- $80Mwas a recent ransom demand given to Royal Mail, UK.
- 300,000policy holders' data stolen from Bitmarck's internal systems in Germany.
- 3,500staff were affected by an attack at CHSF, a hospital in Paris.
- 1.6Mof unique records of personal information from PharMerica leaked.
The ransomware threat is still growing

Lockbit
Details:
In June 2023, the Lockbit ransomware gang disclosed it breached the data of Managed Care of North America (MCNA) Dental, one of the largest dental care and oral health insurance providers in the U.S. The incident affected nearly 9 million individuals, including patients, parents, guardians and guarantors. Acronis secures your business against cybersecurity risks.

Clop
Details:
The Clop ransomware group claimed credit for data theft attacks on MOVEit Transfer, leveraging a zero-day vulnerability to breach hundreds of companies’ servers and exfiltrate sensitive data. Clop revealed it had initiated the exploit on May 27th, 2023, coinciding with US Memorial Day, when staffing levels are typically reduced. Anti-ransomware tools from Acronis can safeguard from such attacks.

BlackCat/ALPHV
Details:
A cyberattack carried out by the ALPHV/BlackCat ransomware group targeted Constellation Software, a Canadian company with a revenue of USD 3.96 billion. The group claimed to have stolen over 1 TB of data from the company's network and demanded a ransom. They threatened to release the data if the company did not pay the ransom. Anti-malware features from Acronis block ransomware like BlackCat.

Royal
Details:
The Royal ransomware gang claimed responsibility for an attack against telecommunications company Intrado. The group demanded $60 million in ransom and shared an over 50 MB archive with stolen files (including passports and other documents) as proof of breach. Made up of experienced threat actors, the gang threatened to publish it on their data leak site unless the ransom was paid. Acronis offers malware protection to prevent such attacks.

Play
Details:
Financial institution Globalcaja, located in Castilla-La Mancha, Spain, with over 300 offices and revenues of USD 248.3 million, was recently targeted by the Play ransomware gang. The gang claims to have stolen private and confidential data and threatened to release it if the ransom was not paid. Acronis' anti-ransomware software can detect and block new and existing threats.
Stay updated on the latest ransomware trends

What your peers are saying
Protect more workloads on more platforms
Physical
Applications
- Microsoft Exchange
- Microsoft SQL Server
- Microsoft SharePoint
- Oracle Database
- Microsoft Active Directory
Virtual
- VMware vSphere
- Microsoft Hyper-V
- Citrix XenServer
- Red Hat Virtualization
- Nutanix AHV
- Linux KVM
- Oracle VM Server
Endpoints
- Windows PC
- Mac

Get answers to your questions
Frequently Asked Questions
What is Ransomware?
Ransomware is malicious software designed to infiltrate and compromise a victim's endpoints and servers, encrypting critical files and preventing access to those systems until a ransom is paid. The consequences of a successful ransomware attack can be severe. It can result in losing sensitive and valuable data, financial damage from operational disruptions, reputational harm, regulatory penalties and potential legal implications.
Acronis Cyber Protect offers robust protection against ransomware through its advanced security features, including real-time threat detection, AI-based behavioral analysis and proactive vulnerability assessments.
With Acronis, you can ensure data integrity and prevent potential damage caused by ransomware attacks. Additionally, it provides secure backup and recovery capabilities, allowing you to restore your systems and files in case of a successful attack.Can I recover from Ransomware?
To effectively prevent ransomware attacks, it is crucial to implement a multi-layered security approach that encompasses various proactive measures. Relying on a single security solution is no longer sufficient, given the evolving and sophisticated nature of ransomware threats.
Acronis Cyber Protect offers comprehensive protection measures. It combines AI-driven anti-malware, secure backup solutions, vulnerability assessments and patch management to identify and mitigate ransomware risks proactively.
Moreover, Acronis safeguards your systems, detects suspicious activities and provides secure backups that allow you to restore data without paying a ransom. By leveraging Acronis Cyber Protect, you can secure your defenses and minimize the chances of falling victim to ransomware attacks.Can ransomware steal data?
Yes, ransomware can steal data in addition to encrypting files. Some advanced ransomware strains have data exfiltration capabilities, enabling cybercriminals to steal sensitive information before encrypting it.
Acronis Cyber Protect not only prevents ransomware attacks but also provides comprehensive data protection. Its secure backup solutions create multiple copies of your data, which can be restored in the event of a ransomware attack, ensuring that your valuable information remains protected and inaccessible to unauthorized parties.How should companies handle ransomware?
Companies should proactively protect against ransomware by implementing a robust cybersecurity strategy. This includes using comprehensive security solutions like Acronis Cyber Protect, which offers real-time threat detection, continuous data backup and AI-based malware protection.
Companies should also conduct regular employee training on recognizing and avoiding phishing attempts and suspicious attachments. In case of a ransomware incident, companies should follow incident response protocols, isolate infected systems, notify law enforcement and leverage Acronis Cyber Protect's recovery capabilities to restore operations swiftly and securely.How to detect ransomware?
Detecting ransomware requires a combination of advanced security measures. Acronis Cyber Protect employs AI-driven behavioral analysis, heuristic detection and signature-based scanning to identify ransomware threats in real time. It continuously monitors system activities, network traffic, and file behavior to detect any anomalies or malicious patterns commonly associated with ransomware attacks.
By leveraging Acronis Cyber Protect's powerful detection capabilities, companies can quickly identify and respond to ransomware incidents, minimizing potential damage and ensuring data and system integrity.Why is cyber insurance important for businesses?
Cyber insurance has become a useful hedge for businesses against the financial and reputational damage caused by modern cyberthreats. With the increasing frequency and sophistication of cyberattacks, organizations face significant risks such as data breaches, ransomware attacks and business interruption. Cyber insurance provides financial protection by covering expenses related to incident response, legal fees, data recovery and even potential extortion payments. It helps businesses recover from financial losses and manage the costs of incident investigation, notification and customer remediation.
Moreover, cyber insurance offers coverage for third-party liability, safeguarding businesses from lawsuits arising from data breaches or privacy violations. By transferring the risk to an insurance provider, organizations can gain peace of mind, enhance their cyber risk management strategies and ensure business resilience in the face of cyberthreats.
Acronis provides protection against a broad range of such cyber threats, making it easier for businesses to qualify for cyber insurance in the face of newly strict standards imposed by issuers.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.