Acronis is trusted by
Overcoming increasing IT infrastructure complexity and cyberattack sophistication requires a comprehensive backup solution to keep every bit of data safe.
Acronis Cyber Protect integrates backup with advanced anti-ransomware technologies to keep your data safe from any threat.
- 30+ workloads protectedSafeguard data across physical, virtual, cloud and mobile environments.
- Quick, reliable recoveryGet fast and reliable recovery of your apps, systems and data on any device, from any incident.
- Secure ransomware protectionDefend your data with built-in ML-based ransomware protection and blockchain notarization.
- Flexible storageBalance the value of data, infrastructure and any regulatory requirements with flexible storage options. Grow with ease using the storage that fits your needs: NAS, SAN, disks, Acronis Cloud or any private or public cloud, such as Azure, AWS or Google.
- Any-to-any migrationAcronis stores data in a unified backup format so that you can easily recover to any platform, regardless of the source system. Reduce risk and IT overload by migrating between different hypervisors and to/from physical machines (P2V, V2V, V2P and P2P) or the cloud (P2C, V2C, C2C, C2V and C2P).
- Acronis Universal RestoreMinimize expensive downtime by restoring Windows and Linux systems to dissimilar hardware, including bare-metal physical, virtual or cloud environments. By overcoming compatibility issues, Acronis Universal Restore technology ensures quick and easy system migration with a few clicks.
- Acronis Instant RestoreReduce recovery times with best-in-industry RTOs by immediately starting your backup as a Windows or Linux virtual machine directly from storage. Have your VM up and running in mere seconds, while Acronis Instant Restore technology invisibly moves your data to the host in the background.
- Variable block-size deduplicationProtect more systems while reducing the impact on disk-storage and network capacity by capturing only the blocks with data that has changed since the previous backup. Acronis Cyber Backup deduplication minimizes storage space by detecting data repetition and storing the identical data only once.
- Data protection across 30+ workloadsAcronis Cyber Protect simplifies data protection for 30+ workloads and multi-generational IT, centralizing the protection of servers, virtual machines, computers, cloud environments and even mobile devices. Any new application or device is automatically protected, delivering continuous and comprehensive data protection.
- Drive health monitoringAvoid unpredictable data loss and proactively improve uptime by monitoring drive health. By using machine learning on S.M.A.R.T. reports, and various operating system parameters, Acronis Cyber Protect can alert you about a disk issue before it happens. This enables you to take the precautionary measures needed to protect your data.
- UniqueAnti-malware scanning of backupsAcronis Cyber Protect ensures that you can always recover malware-free. By centrally scanning your backups for malware, Acronis Cyber Protect helps detect and remove threats, ensuring you restore a clean, safe backup every time.
- UniqueSafe RecoveryAn OS image or application in a backup that is infected with malware can cause continuous reinfection if it is used for recovery without removing the malware. Removing the detected malware and applying the latest anti-malware definitions during the recovery allows users to restore the OS image safely, reducing the chance of reinfection.
- UniqueData Protection MapEnsure that critical data is protected for compliance reporting with a data protection map. Get detailed information about stored data and use the automatic data classification to track the protection status of important files. You will be alerted if files are backed up or not, helping you to further protect your data.
- UniqueApp allowlisting based on backups contentsTraditional, global allowlisting is often ineffective when handling custom applications. Acronis Cyber Protect scans backups with anti-malware technologies, including ML and behavioral heuristics, allowing for precise allowlisting of your unique business applications, minimizing false positives.
- UniqueForensic data collectionMaintaining compliance and running internal investigations can be an expensive process. With the Forensic Mode built into Acronis Cyber Protect, you can simplify future analysis by collecting digital evidence – like memory dumps and process information – from disk- level backups.
- UniqueOne-click RecoveryEnable fast and reliable recovery for entire systems with one-click, including bare-metal recovery to dissimilar hardware. It's so simple and intuitive, users can initiate recovery without IT dependency, significantly reducing downtime and IT team workload.
- Immutable storageEnsure the integrity of backup data and backup accounts themselves with immutable storage, preventing alterations or deletions by any unauthorized entity, including malware, for a customizable period. This solidifies your defense against ransomware, ensuring reliable recovery points are always available.
- Agentless Azure VM backupEasily protect Azure VMs without installing agents. Streamline backup management and reduce resource consumption while maintaining robust data protection for your virtual machines.
Acronis Cyber Protect Cloud
Get cyber protection as a managed service from an Acronis partner
Upcoming events
Expand your protection
- Acronis Cyber Disaster RecoveryEnsure business continuity with an on-demand solution that quickly restores data anywhere - no matter what
- Acronis Cloud StorageSecure offsite cloud backup for reliable data protection and disaster recovery
Award-winning business backup and recovery






Acronis Cyber Protect
Protect your business data from any threat
From $85.00 per year
Looking for help?
Frequently Asked Questions
Can I recover a backup of a physical machine as a virtual one?
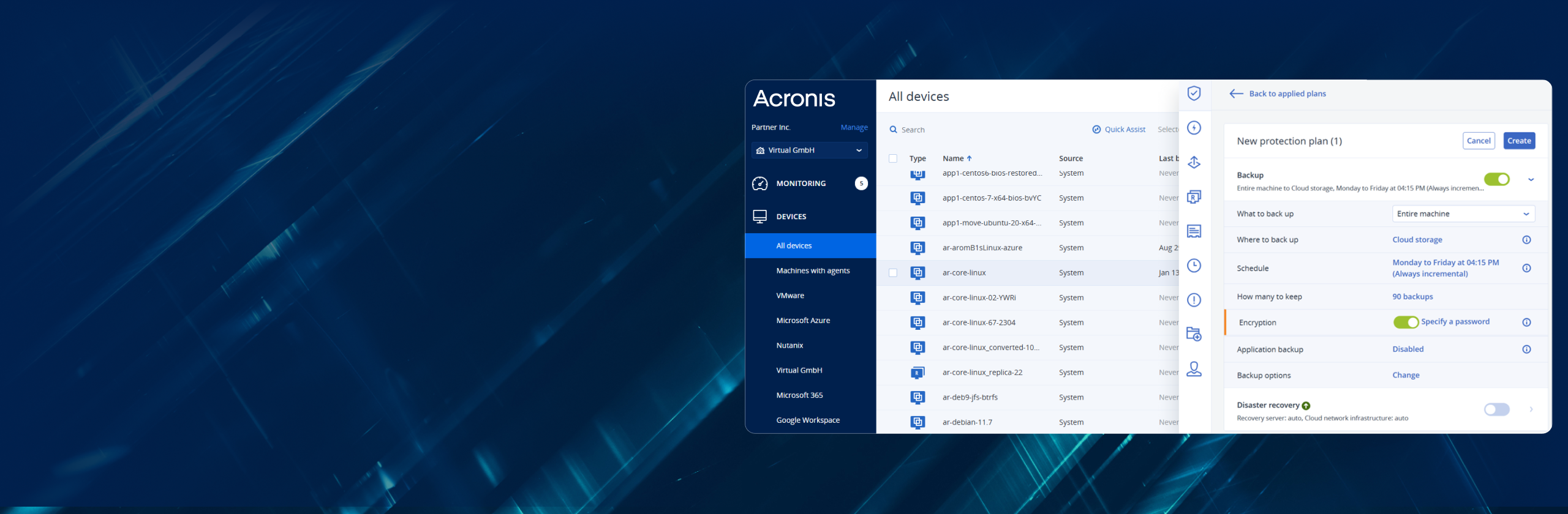
Yes, physical-to-virtual migration is available in Acronis Cyber Protect. This operation can be performed if at least one Agent for VMware or Agent for Hyper-V is installed and registered.How do I configure backup to the cloud?
For a backup to Cloud, an active Acronis Cloud Storage subscription is required.
Create a new backup plan and choose "Cloud Storage" as a destination in the field "Where to back up".
Why is data backup important for businesses?
Sophisticated ransomware attacks and high-profile data breaches have become a constant part of the cybersecurity landscape, reinforcing the importance of sensible data backup.
Although large enterprises are an ever-tempting target, hackers often target small and medium-sized businesses (SMBs). As businesses become more data-dependent each year, they must implement robust, reliable methodologies to keep data secure to ensure unhindered business processes and a steady revenue stream.
Even if cyberattacks are a primary threat to company data, data protection isn't just about safeguarding data from malicious third parties. Sometimes, even the most comprehensive data protection strategy can be breached. As you can't predict when data loss will occur, it's imperative to ensure your business has adequate solutions to restore critical data as quickly as possible. This is why data backup and disaster recovery are as essential as data protection.
Below are the primary reasons businesses of all sizes need a reliable data backup and recovery strategy.
- Constantly evolving cyberattacks
Cyberattacks disrupt business operations and can damage critical IT assets and infrastructure. While large enterprises may have the resources and budget to recover from a severe data breach, SMBs often struggle in such scenarios. According to the Ponemon Institute's State of Cybersecurity Report, SMBs globally have reported alarming statistics in recent years.
– 45% of SMBs say that they lack sufficient security measures to mitigate incoming attacks.
– 66% of SMBs have experienced at least a single cyberattack in the past 12 months.
– 69% of SMBs state that cyberattacks are becoming more targeted.
The most common attack types targeting SMBs are phishing/Social Engineering (57%), compromised or stolen devices (33%), and credential theft (30%).
- Threat prevention doesn't always work
Proactive threat prevention requires network security solutions, automated patch management tools, and specific firewall configurations. Additionally, businesses must also employ robust data loss mitigation tools. As no organization is immune to data theft or ransomware encryption, companies must go the extra mile to fortify their data centers and keep attackers at bay.
However, a Nationwide Insurance report shows that 68% of SMBs don't rely on a disaster recovery plan. Without a DR strategy, businesses are liable to natural disasters, hindered business processes, server downtime, and other data-loss scenarios.
- Data loss can hurt your brand's reputation
In addition to data loss and halted business processes, data breaches can lead to customer distrust. If your customers are aware that your company has lost data, especially their data, your reputation will likely take a severe hit. A poor reputation can lead customers away from your services and impact productivity since new employees may hesitate (or refuse) to join your ranks.
- You can't control natural disasters
Data loss comes in many forms. While you can implement proactive threat prevention, ransomware protection, and stellar cybersecurity hygiene amongst employees, natural disasters can decimate your on-premises data center. SMBs and enterprises must prepare for fires, floods, earthquakes, and other natural disasters that could shut down business processes and data centers.
What are the three most common methods for business data backup?
There are three primary data backup methods – full, incremental, and differential backup. Before you choose the most optimal data backup strategy for your company's needs and preferences, it's important to know the advantages and disadvantages of every backup approach.
- Full data backup
A full data backup creates a complete copy of all the data on a device or system, including files, documents, folders, operating system configurations, applications, calendars, and more, regardless of any previously created backups or circumstances.
The entire data copy is backed up and transferred to secure storage – on-site (local storage), off-site (remote storage), or the cloud. Full backups take longer to complete but are most convenient for disaster recovery as they contain the entire data set of the target environment.
Full backups usually provide the most comprehensive critical data loss protection but must be conducted regularly on a carefully defined schedule to optimize time and resource expenditure. Nonetheless, every backup strategy relies on at least one initially created full backup. Afterward, you can combine weekly or monthly full backups with incremental or differential backups.
While full backups are typically easiest to perform, there are several disadvantages to them to keep in mind.
First, full backups use the most storage space compared to the other two methods; if you rely on physical storage, you may need additional hardware to store entire data sets in secure backup. Secondly, full backups require significant network bandwidth and considerable implementation time, depending on the scale and preferences of your business.
The other two approaches – incremental and differential backups – are partial data backups reliant on at least one full backup in storage. They are similar but have one considerable difference.
- Incremental data backup
Incremental backups require users to create at least one full backup beforehand. Then, subsequent incremental backups will store only changed data since the last full or incremental backup.
Since incremental backups only store alterations (changes) to already backed-up data, they require the least storage space. This enables increased backup speeds and requires fewer resources to complete the backup. Nonetheless, incremental backups take the longest to restore. If an organization needs to restore its entire system backup, responsible teams must first recover the target full backup, followed by all incremental backups in order.
If one or more incremental backups are damaged, corrupted, or lost, the disaster recovery process becomes significantly more complicated (or even impossible).
- Differential data backup
Similar to incremental, differential backup also requires at least one full backup created beforehand. Then, a company can initiate differential backups to include all changed data (files, folders, apps) since the last full backup. As differential backups are cumulative, a combination of full and differential backups includes all files in the company data set (both changed and unchanged data).
Differential backups require more network bandwidth and storage space than incremental backups as they comprise more significant data volumes. However, they enable faster restoration times. A company would only need the initial full backup and the last differential backup to recover its entire system.
What are some critical types of data that every business should back up?
Companies handle different types of critical data. Said data must be kept confidential and readily available for access and recovery. To protect the integrity of business data, companies must consider backing up all of the data types below.
- Patents and intellectual property (IP)
Companies must keep multiple copies of all intellectual property they own to access during or following a security breach, computer compromise, human error, or natural disaster. You can rely on IP documents to demonstrate the rights to various designs, creative works, or products. Having all of them in secure backup ensures you can access IP data whenever needed.
- Company personal records
Personal records are a critical data type for all companies. Confidential employee data – full names, birth dates, social security numbers, addresses, etc. – are liable to cyberattacks and human error, so companies must ensure they are always securely backed up. It's best to store the backups in multiple locations, following the 3-2-1 Rule of Backup, to protect all sensitive data and access in a data-loss scenario.
- Administration data
A wide range of administration files requires sensible data management and security. Such documents may include business plans, contracts, employment agreements, bylaws, and other confidential information.
Every company, regardless of its size, needs administration documents to meet regulatory compliance effectively, so you must ensure all administration data is copied regularly and stored in secure backup. Moreover, you must ensure that sensitive data is private, can't be shared, corrupted, or exploited online, and can be accessed even if you encounter a data breach or another data loss event.
- Financial data (including payment and transaction information)
Financial data can include banking accounts, sensitive business transaction information, customer payment methods, etc. You must safeguard financial data to prevent malicious actors from stealing it, which can lead to increased costs, halted business processes, and customer distrust.
Transaction information regarding sales, equipment or infrastructure purchases, money exchanges, and more must always be secured and readily available for access or recovery. Keeping a record of all previous purchases, business activities, and client transactions is critical to supporting your business project's success, addressing any disputes, and mitigating potential production issues. Using a sensible backup solution to keep transaction data in secure storage is essential to ensure its integrity and availability.
Payment data may include sensitive client financial information, so you must protect it accordingly. As you may need to access that data in the future, it's essential to keep it confidential, protected, and accessible in secure storage.
Every company must design and implement a unique data backup and protection strategy to keep financial information away from prying eyes and pesky malware. If your on-premises hard drives are somehow compromised, you need to be able to quickly restore and access sensitive data via a secure backup solution.
What are the four types of business data recovery?
There are numerous ways you can lose sensitive data. Instead of stressing over a data loss event, you can be proactive and implement proper disaster recovery policies before a data breach occurs. This way, you can restore critical information in every scenario.
There are four primary data recovery process types to restore data following a cyberattack, accidental deletion, or natural disaster. Let's explore them below.
- Physical
Sometimes, you can lose data due to physical damage to your hard drive (HDD). Restoring data from a physically faulty hard drive is called "physical data recovery". When your HDD is corrupted, damaged, or dead, you will often hear a constant clicking noise from the hard drive.
Physical hard drive damage can result from overheating, moisture penetration, humidity, physical hits, or high-temperature exposure. In case of a compromised hard drive, it's best to seek professional help to aid in the physical data recovery.
- Logical
If there's nothing physically wrong with your hard drive, but you still can't access particular files or folders, your HDD is likely affected by software issues. In such cases, you can turn to logical data recovery.
Logical errors affecting the HDD are often due to a damaged file system. If that's the case, you can recover a portion (or all) of the lost data by repairing the file system or a corrupted partition via native Windows commands or specialized data recovery software. Most often, you can retrieve the lost data on your own. However, it's best first to back up all accessible data to avoid compromising it if the recovery process goes wrong. If the logical errors persist after you've tried all reliable fixes, it's best to seek expert help.
- Instant
Instant data recovery can restore essential data via direct backups. If your hard drive is not physically damaged and operates correctly, you can recover secure backups and proceed with your day-to-day tasks.
Either manually or with the help of a professional, it's best to back up the entire data set on your HDD to secure storage. Then, you can troubleshoot your device (computer, laptop, tablet) until it functions as intended. Once that's done, you can transfer all backup data to your device.
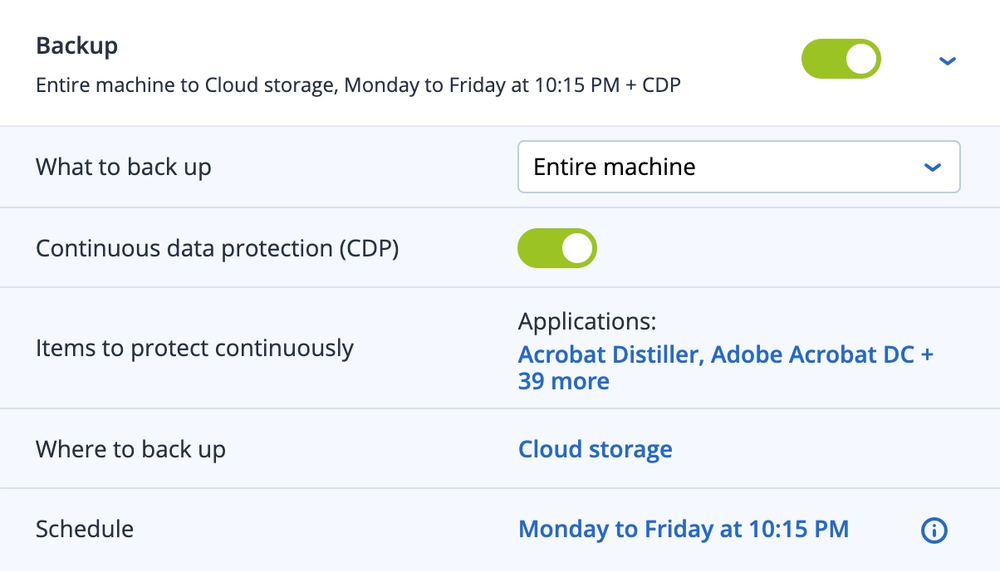
- Continuous data protection
It's better to prevent data loss than to recover your data after a breach.
Data protection and recovery solutions focus on threat prevention features to detect lurking threats on your network and block them before they can infiltrate your computer. Be it malware, ransomware, or nasty viruses, a robust cybersecurity solution can safeguard your data against ill-intended third parties.
However, even the most thorough cybersecurity measures can fall victim to a sophisticated cyberattack. In such cases, having a reliable data backup is crucial to ensure quick recovery and zero data loss. The good thing about modern cybersecurity tools is that they offer automated backup features. Even a non-tech-savvy user can pilot and manage data protection, backup, and recovery options from a centralized agent powered by a user-friendly interface.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.