While 2016 and the early part of 2017 were a peak period for devastating ransomware attacks, the end of 2017 saw another threat become the number one headache for home users and businesses – illicit cryptomining.
Like ransomware, cryptominers are not a new phenomenon; the ability to use computer resources to mine bitcoin without the help of specialized or powerful hardware have been around since at least 2011. Cybercriminals only began developing malware to perform this function in the wake of the boom in cryptocurrencies in mid-to-late 2017.
At that time, thousands of different blockchain-based digital currencies appeared, many of them rocketing upward in volume and capitalization, with some of them able to be mined with ordinary computer resources. Cryptomining is one of the foundations of any cryptocurrency: it provides the processing horsepower necessary to verify previous transactions in the cryptocurrency, a process that ensures the digital currency’s integrity. Cryptominers use their computers’ resources to solve complex mathematical problems: the first miner to solve the problem gets paid for their efforts in the same cryptocurrency.
That can be a lucrative enterprise if you are the one getting paid for the resources (in computing power and electricity) you have expended to verify a cryptocurrency transaction. What cybercriminals figured out is that if they infect your computer with cryptomining malware, they can get your computer to do the work, but they collect the profits. Multiply that by 1000 or a million infected computers, and it is easy to see why crooks jumped on the cryptomining malware bandwagon: it is highly profitable and victims often have no idea their pocket is being picked.
Smart cybercriminals decided that they could potentially multiply their success rate and profits by bundling multiple malware types. If an unwary user clicked on a link or opened an attachment to a malicious email, they’d get two infections: cryptomining malware and ransomware. The attacker would not activate both types at once -- a computer whose files are encrypted by ransomware cannot function as a cryptomining engine – but choose based on factors like the machine’s hardware and software configuration, its anti-malware defenses, and which attack would prove more lucrative. Cryptomining malware suddenly became very popular with cybercriminals.
Cryptojackers skyrocketed in 2018
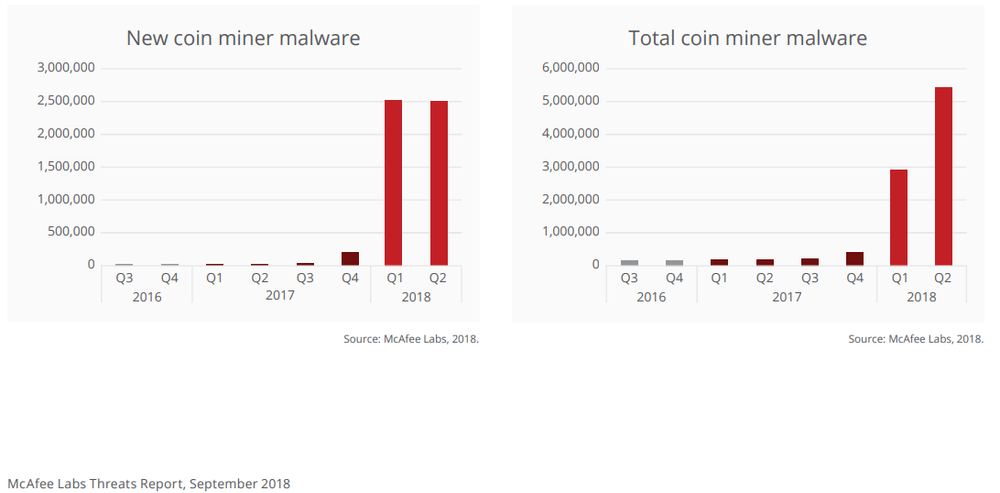
Anti-malware vendor McAfee detected roughly 400,000 samples of cryptomining malware in the fourth quarter of 2017, which exploded by a shocking 629 percent to more than 2.9 million samples in Q1 2018. Q2 saw an increase of 86 percent, representing more than 2.5 million new samples. Anti-malware vendor TrendMicro published very similar reports over the same period: they noted a 956 percent jump in such attacks from the start of 2017.
Worse, cryptomining malware has been developed not just as apps that quietly run on victims’ Windows or Linux machines, but also as cryptocurrency mining services. These criminal enterprises surreptitiously install a small piece of JavaScript on Web sites. The code uses some or all of the computing power of any browser that visits the site in question, enlisting the machine to mine cryptocurrency, unbeknownst to – and without benefiting – the visitor whose system resources are being consumed.
This approach caught on quickly. In November 2017, AdGuard, maker of a popular ad-blocking browser plugin, reported a 31 percent growth rate for in-browser cryptojacking. Its research found more than 30,000 websites running cryptomining scripts like Coinhive, which according to various reports has affected one in five organizations worldwide. In February, Bad Packets Report found 34,474 sites running Coinhive, the most popular JavaScript miner that is also used for legitimate cryptomining activity. In July 2018, Check Point Software Technologies reported that four of the top 10 malware instances it had found were cryptominers. Having affected nearly half of the world’s businesses, cryptomining malware has overtaken ransomware as the biggest, most prevalent cyber threat out there today.
How illicit cryptomining works
To infect their targets with cryptojacking malware, cybercriminals use a variety of techniques, from compromising individual user PCs and mobile devices to infiltrating popular websites and spreading the malware to anyone that visits them. Phishing and spearphishing emails designed to lull users into clicking on malicious links or opening malicious attachments remain an extremely popular and effective attack vector. Some variants have worm components that allow the malware to jump from one compromised machine to many other machines to which it is connected over the network. The EternalBlue exploit, which was used to multiply WannaCry ransomware infections into a global epidemic in 2017, is still in use by cryptomining malware distributors today. But unlike ransomware targets, most cryptomining victims have no idea they’re being stolen from, other than a vague sense that their system isn’t performing as efficiently as it used to.
Fake software updates are another popular infiltration technique, e.g., a malware download that disguises itself as a legitimate update to Adobe Flash Player, and covers its tracks by actually updating Flash while it delivers its malicious cryptomining payload. Another widespread method is to inject a malicious mining script into a legitimate website or block of online ads that run on many websites. Once a victim visits the website or its browser loads the online ad, the cryptomining process is initiated, stealing the resources and profits without the user’s knowledge.
Cryptomining malware developers have learned from their early mistakes. It is far less common today to find malware that consumes 100 percent of the victim’s CPU capacity, yielding a noticeable slowdown that is likelier to prompt the user to notice and take remedial action. Newer editions of cryptomining malware take smarter steps to conceal their presence: only loading the victim’s CPU to around 20 percent, seeking user idle times to perform the most resource-intensive calculations, etc. These cryptominers can thus steal resources from the victim without detection for a very long time.
Worse, one does not have to be a highly skilled software engineer to get into the business of illicit mining. As with other malware kits, cryptojacking as a service can be purchased on the dark web for as little as half a US dollar. The high level of privacy and anonymity inherent in certain cryptocurrencies like Monero and Zcash makes it much harder to trace and catch the thieves, too.
For instance, Monero uses a public ledger to create and track the exchange of digital tokens, but transactions are obfuscated to hide the source, destination and actual amounts of cryptocurrency transferred. A recent academic study revealed that embedded cryptocurrency miner Coinhive is generating $250,000 worth of Monero every month. This same research, released by RWTH Aachen University in Germany, concludes that Monero accounts for 75 percent of all browser-based cryptocurrency mining.
Notable cryptojackers
Smominru
Smominru is probably most notorious cryptojacking botnet, consisting of over 520,000 machines that by January 2018 had earned its owners over $3 million in Monero, abetted by a smart perpetually self-regenerating botnet design. Smominru was powered by EternalBlue, the stolen NSA exploit that was also used in the WannaCry global ransomware epidemic of 2017.
BadShell
Clever cryptojackers like BadShell hide themselves within legitimate processes like Windows PowerShell through which they execute hidden malicious mining scripts. Few traditional antivirus programs will detect the threat, as they typically trust Windows signed executables like PowerShell by default.
Coinhive
Originally intended and still used as a legitimate website monetization tool, Coinhive’s mining code is currently the world’s largest cryptojacking threat. One interesting fact is that the company responsible for Coinhive nets 30 percent of all mining operations, even hacked instances.
MassMiner
MassMiner is an interesting example because it uses many exploits for various vulnerabilities in one payload. Exploiting unpatched flaws in Oracle WebLogic, Windows SMB, and Apache Struts has earned close to $200,000 worth of Monero cryptocurrency for MassMiner’s creators.
Prowli
Prowli is a massive and prominent botnet of over 40,000 infected web servers, modems, and other Internet of Things (IoT) devices that it used for cryptocurrency mining and for redirecting users to malicious sites. Part of Prowli is a brute-force password worm to facilitate the spread of its Monero miner. In some cases, the botnet also installs backdoors on infected systems.
WinstarNssMiner
WinstarNssMiner infected more than half million systems over the course of three days in May 2018. When this cryptojacker detects effective anti-virus software on its target machine, it stays dormant, activating itself only on systems with weaker defenses. Worse, if you try to remove WinstarNssMiner, it crashes the infected system.
Acronis True Image now fights cryptojackers
As part of its ongoing cyber protection efforts, Acronis been tracking the cryptomining phenomenon as it has grown into a pervasive worldwide threat. In the interest of protecting our business and consumer customers against cryptomining malware, we extended the anti-ransomware capabilities of Acronis Active Protection with technology to combat cryptomining malware as well.
This enhanced version of Acronis Active Protection uses advanced machine learning to identify and terminate all known cryptojacking processes running on Windows. When it detects a cryptominer, Acronis Active Protection notifies the machine’s admin user of the potentially illicit activity. (This capability is initially available in our home product Acronis True Image, we plan to add it to our business-oriented Acronis Backup products in the near future.)
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



