When it comes to checking if a network port is opened or closed on a remote computer, there's no easier way than to use Telnet. Ports left open for no reason are a security risk that malicious programs and viruses can exploit. At the same time, if legitimate software communicates through a specific port, having that port closed will make the program throw errors and malfunction.
Many people find the challenge of checking if a port is opened to be too complex. However, one of the most efficient ways is to use the network protocol Telnet. Telnet allows the user to test individual ports and see whether they are open. In this article, we'll break down how Telnet can be used to check ports on Windows 10, Windows Server 2022, 2016, 2012, and 2008.
What is Telnet?
The name "Telnet" is short for "Teletype Network Protocol".
In a nutshell, Telnet is a computer protocol that was built for interacting with remote computers. It enables terminal-to-terminal communication and can be used for a variety of purposes.
The word "Telnet" also refers to the command-line utility "telnet", available under Windows OS and Unix-like systems, including Mac, Linux, and others. We will use the term "Telnet" mainly in the context of the telnet client software.
Telnet utility allows remote user access to test connectivity to remote machines and issue commands through a keyboard. Though most users opt to work with graphical interfaces, Telnet is one of the simplest ways to check connectivity on certain ports.
What is Telnet used for?
The Telnet protocol is as old-school as it gets in the tech world. It was developed in 1969, so it doesn't pack the robust security features of today's network protocols.
As we've mentioned, via Telnet, users can connect to software that utilizes text-based unencrypted protocols from web servers to ports. You can open the command line interface on a remote computer, type "telnet", the remote machine's name or IP address, and wait for the Telnet connection to ping the port to check if it's open.
However, you can use Telnet to execute various other tasks. When properly connected, you can edit files, run programs, or check your email with it.
In addition, some servers enable remote Telnet connections to access public data. For starters, you can check the weather forecast via the Weather Underground service, active since 1995 and still running. (because, let's face it, TV forecasts can get boring)
Moreover, Telnet lets you play chess at the Free Internet Chess Server and really merge with the spirit of old digital masters.
To play chess there, use the command:
o freechess.org
Now, for the hardcore Star Wars fans - you can watch Star Wars Episode 4 in the default ASCII mode. Or at least the part of the movie that's finished and available for "streaming".
To do so, use the following command in Telnet:
o towel.blinkenlights.nl 23
Via Telnet, a nostalgic network user can also talk to the AI psychotherapist Eliza. Even if she rarely understands you, her lines are bound to brighten your day and give you a laugh.
To get in touch with Eliza, type the following command:
o telehack.com, followed by eliza
Some users still use Telnet to administer and join text-based bulletin board systems. As forums are plain text, you won't need fancy pictures or animations to spice up the threads.
To sum up, aside from its ability to check port status, Telnet is primarily used for nostalgic fun or to equip an older user system that doesn't support access to specific data otherwise.
What are the 3 modes of Telnet protocol?
The Telnet protocol generally has three modes of operation. In all of them, your keyboard produces outgoing data via the Telnet command structure, travels via a Telnet TCP connection, and arrives at a virtual or physical terminal to satisfy a terminal-computer connection.
Default mode
- If no other modes are invoked, Telnet will default to this mode.
- Echoing is performed in this mode by the user.
- Here, the user can type a character, and the client echoes said character on the screen. However, it won't send it until the whole line is completed.
This mode is also referred to as "half-duplex device operating mode" or "half-duplex mode". It requires the Telnet GA command (GO AHEAD) from the server before accepting any user input data. The motivation for this is the high potential cost of processing network input interrupts along with the NVT specification that "echoes" do not traverse the network.
Character mode
- In Telnet Character mode, only one character is transmitted at a time. (user-to-server direction)
- The server's telnet interpreter will acknowledge the receipt of the character by echoing it back to the client.
- Then, the Telnet client software will send back a TCP ACK packet to the server to inform of the receipt of the echo from it.
- Telnet generates an IP datagram packet for each character, which may cause connectivity delays due to the high volume of network traffic. (in older systems)
Line mode
- The line mode (aka "Line-at-a-time mode") derives from the Telnet Character mode.
- In this mode, characters are echoed by a locally defined explicit signal and sent to the Telnet server once completed.
- In Line mode, either the ECHO or the SUPPRESS GO AHEAD commands are disabled.
Telnet command section
Telnet commands are distinguished by various characters use with the most significant bit set. The data stream portion of Telnet ensures the incorporation of commands invoked by network users. Commands are always introduced via the decimal 255, also known as the Interpret as command (IAC) character.
Defined Telnet commands consist of:
WILL - 251 - Offer or accept to enable
WON'T - 252 - Accept of Offer to disable
DO - 253 - Request or Approve to enable operation
DON'T - 254 - Disapprove enable or Request to disable
SE - 240 - End of subnegotiation parameters
NOP - 241 - No operation
DM - 242- The Telnet command "data mark" indicates and locates a Telnet Synch sequence within the data stream. (critical to be accompanied by a Transmission Control Protocol (TCP) urgent notification)
BRK - 243 - Break command. It indicates that the "attention" or "break" key was hit
IP - 244 - Suspends, interrupts, or aborts the Network Virtual Terminal connection corresponding to the specific process
AO - 245 - Aborts output - allows for the process to complete but doesn't send data
AYT - 246 - This stands for "Are you there?" - it requests to send back visible evidence that the AYT was received from the Network Virtual Terminal (NVT)
EC - 247 - Erase character command - the receiver of the command should delete the last undeleted preceding
EL - 248 - Erase line command - delete characters from the stream back to - but not including - the previous Carriage Return Line Feed (CRLF)
GA - 249 - The Telnet Go Ahead command - used primarily to inform the other end that it can start to transmit data
SB - 250 - Indicates subnegotiation of the included options to follow
IAC - 255 - The "Interpret-as-command" character
Telnet protocol command options
Several Telnet option specifications are available to negotiate between the Telnet client and server. This can be done by using commands at any stage as long as the connection persists. Below is a list of the most important command options.
Actual code assignments
1 echo
3 suppress go ahead
5 status
6 timing mark
24 terminal type
31 window size
32 terminal speed
33 remote flow control
34 linemode
36 environment variables
Options undergo a negotiation process to present the client and server with a common view of the potential extra capabilities affecting the interchange and the operation of applications.
Both ends of a Telnet dialogue can either enable or disable options locally or remotely.
How to enable a Telnet connection on a server?
The Telnet client is built into Windows 11, but to use it on Windows Server 2022, you'd need to enable it as it's disabled by default.
To do so, you'd need to go through the Graphical User Interface (GUI).
- Log into Windows Server 2022 with administrative privileges
- Open "Server Manager" from the Start menu
- Select the "Manage" menu (in the top right corner) -> select "Add Roles and Features"
- In the "Add Roles and Features Wizard", select "Next" on the "Before you begin" line
- Click "Next" -> click "Select installation type"
- On the "Select destination server" screen, select your local server in the server list -> click "Next"
- Click "Next" on the "Select server roles" line
- On the "Select features" screen, scroll through the available features -> check "Telnet Client" -> click "Next"
- Select "Install" on the "Confirmation installation selections" line
- Close the "Add Roles and Features Wizard"
The Telnet protocol can be enabled in several ways. Below, we will explore all available options so that you can choose the most efficient one for you.
Enabling Telnet client in Microsoft Windows operating systems
As we've mentioned, Telnet is disabled by default in Windows settings, so you need to turn it on before you can do anything. Enabling it will help you run the required diagnostics and check if a port is open. If you try to use Telnet without turning it on first, you'll receive a message like this:
In order to turn Telnet on, you need to use the command line or the graphical interface of your computer.
Enabling Telnet client through Command Prompt:
If you want to enable Telnet via the command line, open the Command Prompt with elevated privileges ("as Administrator") and run the following command:
Dism /Online /Enable-feature /FeatureName:TelnetClient
After you've put this in, Telnet will be ready to use to check your ports.
Alternatively to Command Prompt, you can use the following PowerShell command to achieve the same result:
Install-WindowsFeature -name Telnet-Client
If you want to use the graphical user interface, you need to:
How to enable Telnet client on Windows 7, 8. 10:
Open Windows Start menu > Type "Control Panel" > Press Enter > “Programs” > "Programs and Features" > Turn Windows features on or off > Select "Telnet Client" > Press “OK"
How to enable Telnet client on Windows Server 2008:
Open "Server Manager"> Features > click "Add Features"> enable "Telnet Client" checkbox > click "Next"> click "Install"> when the feature installation finishes, click "Close"
How to enable Telnet client on Windows Server 2012, 2016:
Open "Server Manager"> "Add roles and features"> click "Next" until reaching the "Features" step > tick "Telnet Client"> click "Install"> when the feature installation finishes, click "Close".
How to use Telnet command to Test Open Ports
One of Telnet's biggest perks is that you can test whether a port is open with a simple command. Issuing the Telnet line telnet [domainname or ip] [port] will allow you to test connectivity to a remote host on the given port.
Issue the following command in the Command Prompt:
telnet [domain name or ip] [port]
Put the IP address or domain name of the server you're trying to connect to in place of [domain name or ip], and replace the second brackets with the port number on the remote machine, the connection to which you want to test.
For example, to verify connection to 192.168.0.10 on port 25, issue the command:
telnet 192.168.0.10 25
If the connection succeeds, a blank screen will appear, meaning that the computer port is open.
A failed connection will be accompanied by an error message. Such a signal can indicate either a closed port or that the indicated remote server is not listening on the provided port.
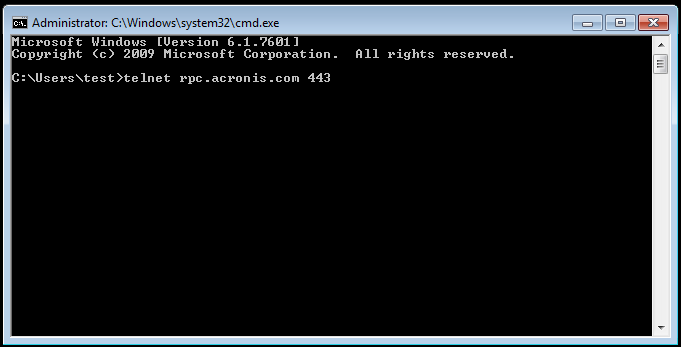
Example
telnet rpc.acronis.com 443
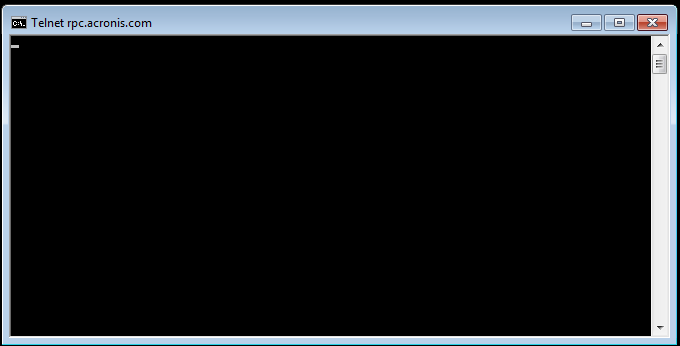
How to Check if a Port is Open on Mac
High Sierra users: Apple removed the telnet client from macOS 10.13 High Sierra. There is no official way to return it, but you can still copy it from an older OS or compile it from sources and use it on High Sierra.
Just like on Windows, Telnet can be accessed through Terminal, the command prompt on macOS. To open telnet, click "Go"> "Utilities"> "Terminal", then run the following command (the numbers are example IP address and port): telnet [domainname or ip] [port], e.g.>telnet 192.168.1.1 443
When a computer port is open, a blank screen will show up, meaning that the connection has been successful. An unsuccessful connection will be accompanied by an error message.
An alternative to Telnet in checking user ports is Network Utility. To check ports on a Mac, follow the plan below:
Open "Network Utility"> Click "Port Scan"> Indicate the hostname and ports to scan the remote host e.g. myserver.com from 995 to 995 > Check the output
Acting on the results obtained from the Telnet test
Many times when you try to use Telnet, you may find that your own network is blocking your connection. It's common for users to run a firewall, which blocks the connection to outbound ports. A basic way to test whether your firewall is interrupting your Telnet is to disable your firewall and run a Telnet test.
If you want to check for closed ports on your router, enter your router management console. Open a web browser and enter the IP address or name of the router, for example, "192.168.0.10". If the page does not open, try replacing "http" with "https" at the beginning of the address.
Next, enter your username and password, and click "Enter" or "Log in". Head to the Security section to open or close ports and access other firewall settings of the router.
If you need to make resources in the internal network accessible from the outside, enter "External access"/" Port forwarding" section. Consult the router manufacturer's documentation for detailed instructions.
What is SSH? What is its port?
SSH stands for "Secure Shell" or "Secure Socket Shell". It's a secure protocol that enables encrypted communication between two computers.
Secure Shell uses hypertext transfer protocol (HTTP) to transfer hypertext (web pages) and share data.
As SSH enables encrypted communication between the two machines, it is suitable for unsecured networks.
SSH is primarily used to establish a virtual terminal connection and log onto a remote machine to perform operations or transfer data. The default port for the SSH client connection is 22. You can change the default by entering a port number between 1024 and 32,767.
Keep in mind, in a virtual system (VSYS), the root and VSYS share the same SSH port number. This means that if you change the SSH port from the default (22), the port will also change for all virtual terminals.
How does SSH work?
To establish remote terminal access via Secure Shell, you'd need an SSH client on your computer to connect to the SSH server.
The SSH client, once enabled, invokes the connection setup process to process communication secured by strong symmetric encryption.
The client relies on public key cryptography to verify the SSH server's identity, followed by hashing algorithms to ensure the privacy and integrity of exchanged data between the client and the server.
What is the difference between Telnet and SSH?
Telnet and SSH are both network protocols used to manage a remote computer system.
But what makes them different? Let's explore that below step-by-step.
- Difference in Definition
Telnet is an application network protocol that enables user communication with a remote computer via a text-based interface. Telnet creates a virtual terminal connection, allowing users to access applications on a remote machine.
SSH serves the same primary functions as Telnet but adds security to the process. It allows secure access even when the connected network is unsecured, making it safer than the Telnet protocol. Additionally, network admins can log into a remote machine via SSH, execute commands, transfer files, and more.
- Difference in Operation
Telnet requires a server app installed on the remote computer (the one you want to manage) and a client app installed on the local machine.
Telnet uses the TCP port protocol and port 23 to establish a connection with remote computers. The created system acts as a Telnet server and is available to receive commands. Said commands are sent via the Network Virtual Terminal (NVT) format. Then, they are received and interpreted by the Telnet server and sent to the corresponding application.
SSH ensures a secure connection to the server via port 22. It generates a session after the client verifies the server via key-based authentication. The generated session is sent to both the client and the server, and all traffic is encrypted for the current session.
Lastly, the server verifies the client via a generated SSH key pair. After successful client authentication, it establishes an encrypted connection, and the two systems can exchange data securely.
- Difference in Security
Telnet doesn't provide any security features or protocols when transmitting data. The network protocol is highly vulnerable to cyber threats unless used on private, trusted, preferably offline, networks.
Thanks to the key pairs used for authentication, SSH is extremely difficult to penetrate and read the transferred data. This makes it a way more secure protocol than Telnet, even for unsecured networks.
- Difference in Data formats
Telnet sends data as plain text via the NVT format.
SSH sends data via an encrypted format through a secure channel.
- Difference in Authentication
Telnet employs no authentication mechanism.
SSH relies on public key encryption.
- Difference in Supported operating systems
Both Telnet and SSH are available on Windows, Mac OS, and Linux. (with some exceptions for Telnet in newer Mac OS versions)
- Difference in Bandwidth usage
Telnet connection bandwidth usage is low.
SSH connection bandwidth usage is high.
When to use Telnet or SSH?
There are two primary cases when using a Telnet connection over SSH is recommended.
- When operating on trusted networks (e.g., LANs) that are disconnected from the internet.
- When operating with a remote host that doesn't support SSH.
In all other cases, it's best to use SSH since it provides high security for internet-connected devices.
In addition, SSH enables more functionality options than Telnet. (e.g., secure file transfer, port forwarding)
Is Telnet still used?
Telnet is a primordial being in the tech universe. And as such, it is still being used in specific scenarios. Telnet is easy to operate, requires no high-tech knowledge, and doesn't overload your network. (in most cases)
As we've discussed, network admins rely on Telnet (at times) to access and manage remote network devices. In addition, individual users can establish a Telnet connection to check port status on private, trusted networks.
Related Acronis resources
Read further on what ports are used in Acronis software and how to open them:
https://kb.acronis.com/brandmauer - A summary page about the network ports used in Acronis software
https://www.acronis.com/blog/posts/open-ports-on-microsoft-azure/ - Instructions for using Acronis software with Microsoft Azure (the required ports part).
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



