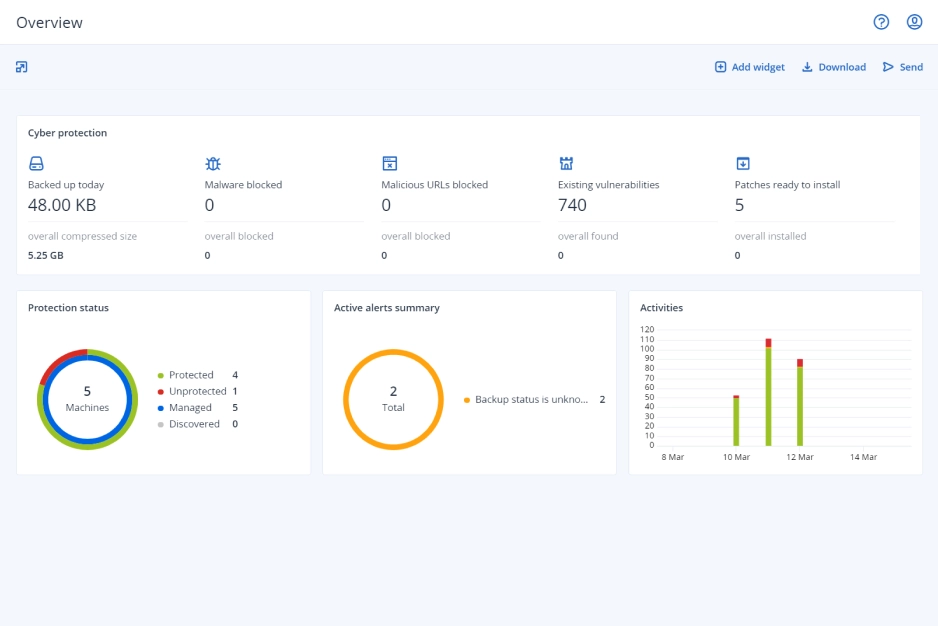
- The world’s best backup and recoveryFull-image and file-level backup and recovery to safeguard workloads on more than 25 platforms – with near-zero RPOs and RTOs.
- Enhanced with essential cyber protection at no costAdvanced AI-based behavioral detection engine stops malware, ransomware, and zero-day attacks on client workloads.
- With protection management built for MSPsIntegrates data protection, cybersecurity, and endpoint management into a single solution with centralized management. Seamless integration with RMM and PSA systems.
Strengthen your security services and increase profitability
Expand your services with advanced protection
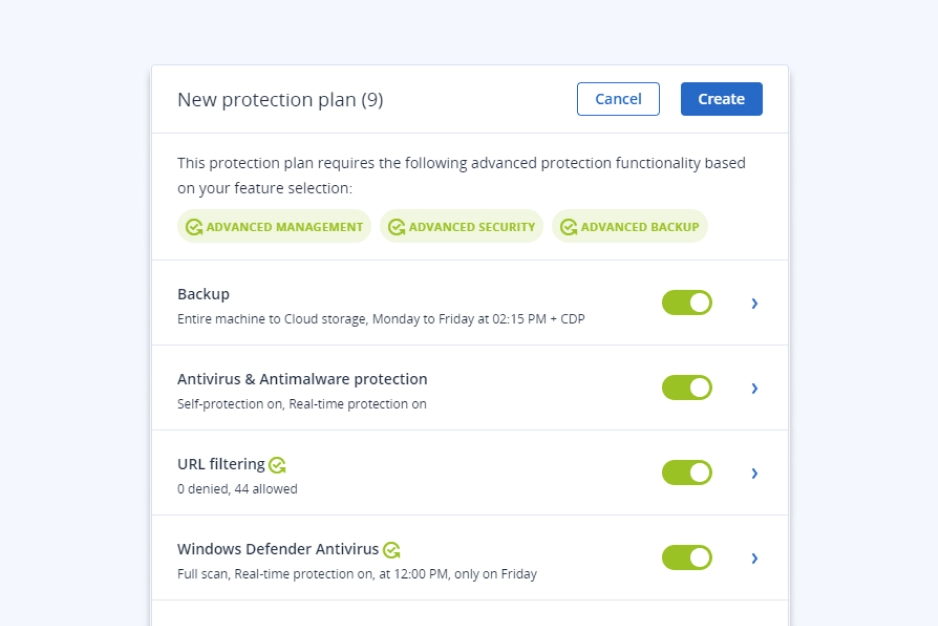
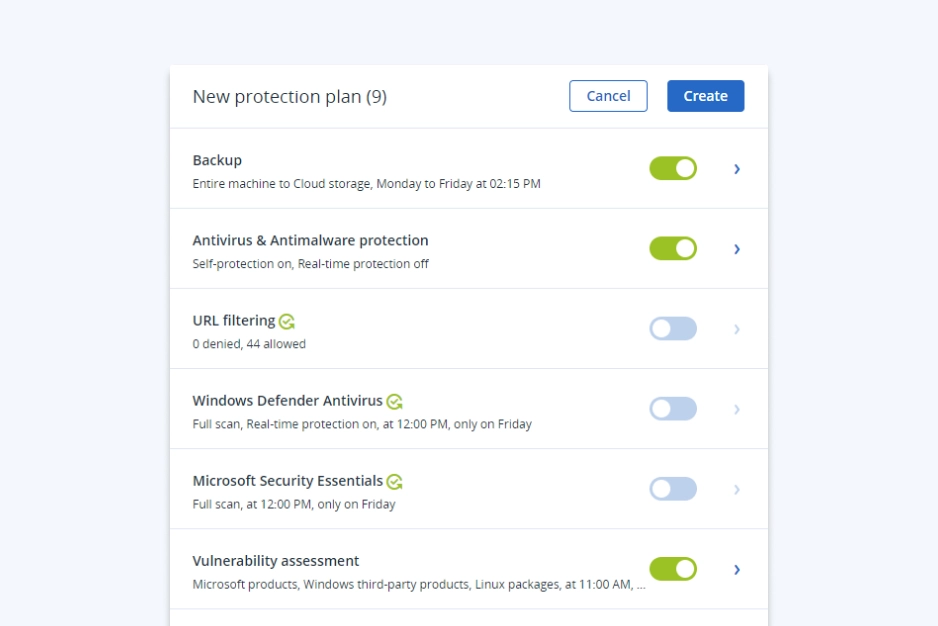
Add other powerful components to strengthen your services even further with advanced protection and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
- Security + XDRInstead of counting on a costly and complex stack of point solutions, Acronis XDR introduces natively integrated, highly efficient protection built for MSPs:
- Natively integrated cybersecurity, data protection and endpoint management
- Highly efficient security designed to protect the most vulnerable attack surfaces with AI-guided incident analysis and single-click response
- Built for MSPs, including a single agent and console for all services
- Security + EDRInstead of counting on a costly & complex stack of point solutions, Acronis enables MSPs via integration of EDR, endpoint management, and backup & recovery to:
- Easily launch a complete security solution, including rapid recovery
- Protect against modern threats and readily comply with cyber insurance requirements
- Maximize efficiency through a single security platform
- Acronis RMMAchieve peak MSP performance with a natively integrated, secure, AI-powered RMM. Enhance client satisfaction by delivering superior IT administration and monitoring services while improving security posture for both endpoints and Microsoft 365. Boost technician performance with seamless automation of IT management.
- Automated patch management
- System and hardware monitoring
- AI-assisted scripting and more
- Acronis PSASimplify success with an easy-to-deploy, adopt and use PSA tailored for modern recurring and cloud MSP business models. With Acronis PSA, you take the shortest path to increased profits and streamlined business operations.
- Service desk
- Billing and invoicing
- KPI reports and more
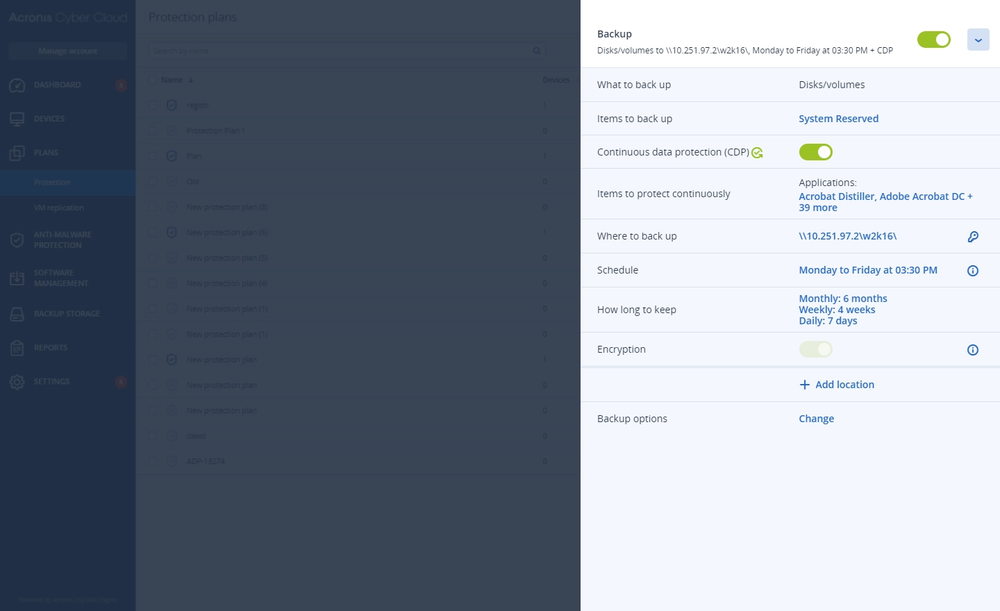
- Advanced BackupDefend clients’ data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You can also gain visibility into data-protection statuses across your clients’ infrastructure.
- Continuous data protection
- Data protection map
- Off-host data processing
- Disaster RecoveryGet clients back to business in mere minutes when disaster strikes by spinning up their systems in the Acronis Cloud and restoring them anywhere, ensuring immediate data availability. Make disaster recovery painless and increase efficiency with orchestration, runbooks, and automatic failover.
- Disaster recovery orchestration
- Production failover
- Site-to-site VPN
- Email SecurityBlock any email threat, including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero days in seconds before it reaches end users. Leverage Perception Point’s next-generation technology for lightning-fast detection and easy deployment, configuration, and management.
- Anti-phishing and anti-spoofing engines
- Anti-evasion and account takeover protection
- Next-generation dynamic detection against zero-days
- Data Loss Prevention (DLP)Prevent leakage of sensitive data from endpoints via more than 70 local and network channels and strengthen compliance with minimal effort and speed to value.
- Content-aware data loss prevention
- Automatic client-specific DLP policy creation and extension
- Pre-build data classifiers for common regulatory frameworks
- File Sync and ShareGet a full control over data location, management and privacy with a file sync and share service, including a transaction ledger to enable notarization and eSignature capabilities, across all platforms.
- File notarization
- Embedded eSignatures
- Independent file verification
Upcoming events
Recognized member of the cybersecurity industry









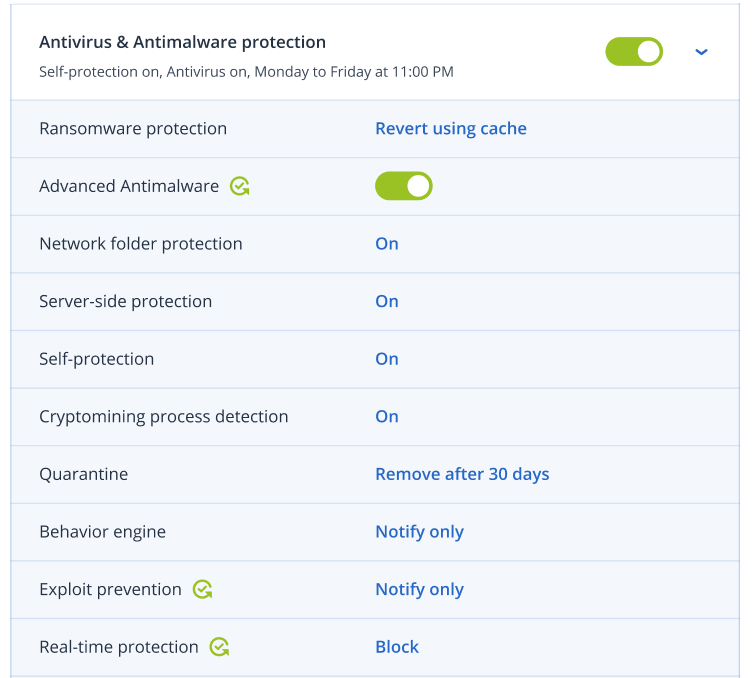
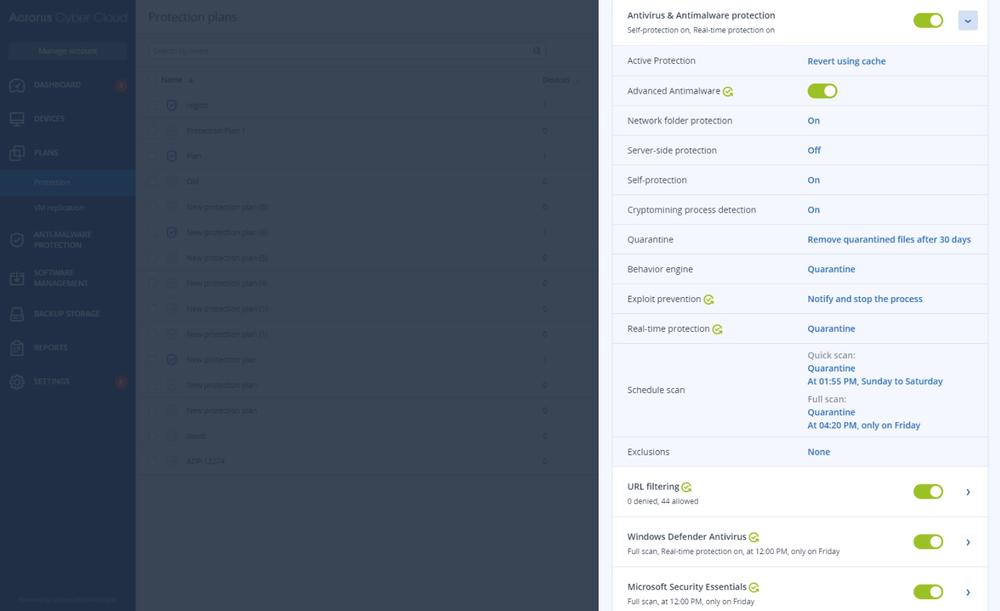
- CybersecurityStay ahead of modern cyberthreats with award-winning anti-ransomware enhanced with anti-malware capabilities that complement your clients’ antivirus. Prevent data leaks via local channels.
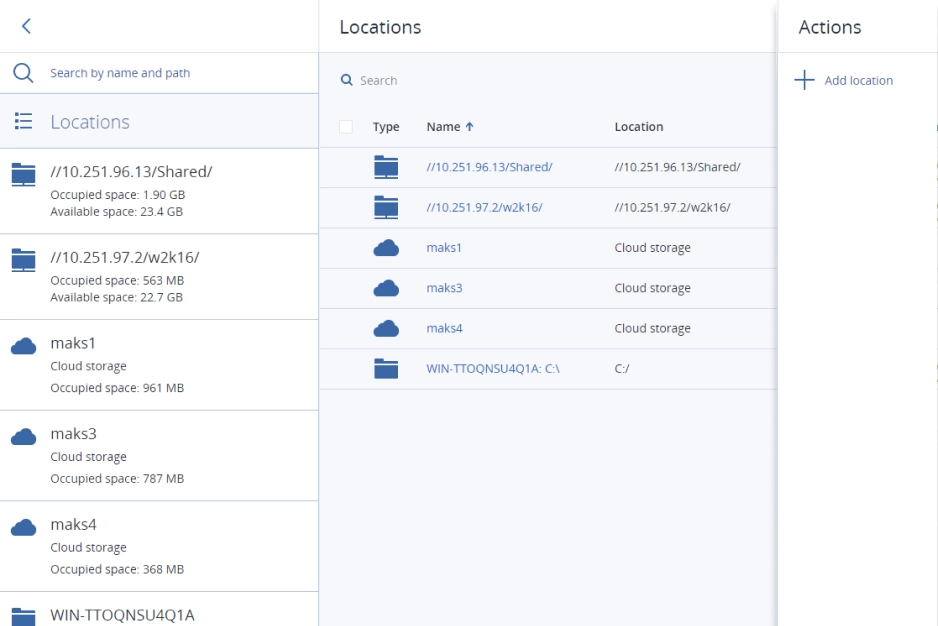
- Backup and recoveryMinimize data loss across your clients’ infrastructure and workloads with the best backup and recovery technology, available in consumption-based or per-workload licensing models.
- Acronis RMMCentralize your protection management and provision endpoints in minutes. Remotely assist clients and assess system vulnerabilities and security gaps. Increase visibility with built-in monitoring and reporting.
- Disaster recovery (DR)Allow clients on DR-enabled tenants to establish secure connection to the corporate network with their personal devices, or test failover in an isolated network environment.
- File sync and shareIncrease productivity by enabling your clients to create and securely share corporate content from anywhere, at any time, and on any device. Only get charged for the storage you use.
- NotaryEnsure the integrity of data, while achieving regulatory transparency and decreasing security risks with a blockchain-based service for file notarization, eSigning, and file verification.
Acronis Cyber Protect Cloud
Modernize your cybersecurity and backup with integrated cyber protection
Acronis Professional Services
If your organization has a complex IT infrastructure or limited IT resources, Acronis Professional Services can assist you with the design, integration, implementation and on-going operation of your Acronis solution.
Consulting services
Leverage Acronis’ experience and shorten the time it takes to gain value from your Acronis investment.- Exclusive
Deployment services
With Acronis Deployment Services, you can be the first to market with data protection, infrastructure migration, and disaster recovery services. Audit services
Decrease maintenance costs and enjoy peace of mind knowing your customers’ data is protected in accordance with industry and Acronis best practices.Educational services
Enable your personnel to drive data protection, migration, and disaster recovery services enablement, effectively support your customers.
Why do MSPs choose Acronis Cyber Protect Cloud over other solutions? It’s an all-in-one data protection and cybersecurity platform that enables MSPs to offer more client services at less cost.
Business Resilience System (BRS) appliance for MSPs by Scale Computing
Purpose-built for Acronis Cyber Protect Cloud, MSPs can skyrocket how they deliver client operations resiliency and end-to-end data protection with the BRS.
Leverage a flexible, hybrid cloud approach
Allow data and applications to interoperate across boundaries (for example, cloud versus on‐premises) with a hybrid cloud approach.Gain unparalleled data protection and cybersecurity
Minimize data loss across clients’ infrastructure and workloads with active ransomware protection, granular-file level backups, long-term archiving and the ability to instantly spin up workloads on-premises.Convert to a VM – any VM
Back up physical workloads, VMware and Hyper-V and instantly power them on as VMs on the local BRS appliance at a moment’s notice.Boost your efficiency and bottom line
Eliminate confusion and time-consuming management tasks during the recovery process, when time is of the essence. Increase revenue with a higher level of service, plus new cyber protection services.
Acronis Cyber Protect Cloud
Modernize your cybersecurity and backup with integrated cyber protection
Supported systems
Operating systems and environments
Windows
- Windows 7 and later
- Windows 2008 R2 and later
Linux
- Linux with kernel from 2.6.9 to 5.1 and glibc 2.3.4 or later
MacOS
- OS X Mavericks 10.9, OS X Yosemite 10.10, OS X El Capitan 10.1, macOS Sierra 10.12, macOS High Sierra 10.13, macOS Mojave 10.14, macOS Catalina 10.15
Mobile
- Android 4.1 or later
- iOS 8 or later
Infrastructure-as-a-Service
Microsoft applications
- Microsoft SQL Server 2019, 2017, 2016, 2014, 2012, 2008 R2, 2008, 2005
- Microsoft Exchange Server 2019, 2016, 2013, 2010, 2007 Microsoft SharePoint 2013
- Microsoft SharePoint Server 2010 SP1, Microsoft SharePoint Foundation 2010 SP1, Microsoft Office SharePoint Server 2007 SP2, Microsoft Windows SharePoint Services 3.0 SP2
Hypervisors
- VMware vSphere 7.0, 6.7, 6.5, 6.0, 5.5, 5.1, 5.0, 4.1
- Microsoft Hyper-V Server 2019, 2016, 2012/2012 R2, 2008/2008 R2
- Microsoft Windows Server 2022, 2019, 2016, 2012/2012 R2,2008/2008 R2 with Hyper-V
- Microsoft Windows 10, 8/8.1 (x64) with Hyper-V
- Citrix XenServer 7.6-4.1.5
- RHEV 3.6-2.2, RHV 4.1, 4.0
- Oracle VM Server 3.4, 3.3, 3.0, Oracle VM VirtualBox 4.x
- Nutanix AHV 20180425.x-20160925.x
- Linux KVM 5.3 - 8
- Proxmox virtual environment 5.3 - 8
- Virtuozzo 6.0.10, 6.0.11, 6.0.12, 7.0.13, 7.0.14
- Virtuozzo Infrastructure Platform 3.5
Resources
- DatasheetAcronis Cyber Protect Cloud Overview
- DatasheetAcronis Cyber Protect Cloud with Security Overview
- DatasheetAcronis Cyber Protect Cloud with Backup Overview
- DatasheetAcronis Cyber Protect Cloud with Disaster Recovery Overview
- DatasheetAcronis Cyber Protect Cloud with Email Security Overview
- DatasheetAcronis Cyber Protect Cloud with Data Loss Prevention (DLP)
- DatasheetAcronis Cyber Protect Cloud with File Sync and Share Overview
- DatasheetAcronis Cyber Protect Cloud with Management Overview
Stages of modern cyber protection
To deliver thorough protection for our partners’ clients, Acronis’ vision and products are based on a multi-stage process rather than simply detecting and blocking threats, leaving other risks uncovered.
Prevention
Don’t wait for threats to hit, proactively protect your clients and limit their attack surface.Detection
Detect issues and threats in real-time before they pose risk to the IT environment.Response
Enable quick actions that immediately mitigate the risk.Recovery
Restore client data quickly and safely so no data is lost, with near-instant availability, in case of compromise.Forensics
Mitigate future risks and enable easy investigations by collecting forensics information.
Global data center presence
Help your clients meet their unique needs by storing their data where they choose. With multiple data centers worldwide, Acronis enables you to meet the compliance, data sovereignty, and performance requirements of all your clients.
Looking for help?
Frequently Asked Questions
Does Acronis Cyber Protect Cloud provide all-in-one solution for MSPs?
Acronis Cyber Protect Cloud is the industry-first solution that unites cybersecurity, data protection, and endpoint management in one integrated solution – with one agent and a single management console. In addition to greatly reducing the resources needed to operate because it consolidates multiple solutions, it creates easy upsell and cross-sell opportunities for increased profitability.
Acronis Cyber Protect Cloud is easy to deploy with automatic machine discovery and remote agent installation. It reduces the administrative burden with centralized, group, and multi-tenant management and built-in secure remote connections for assistance.
Service providers can track and plan their work much more efficiently with hardware inventory collection, change tracking, vulnerability assessments, and centralized monitoring and reporting via a single pane-of-glass.
It greatly eases daily service providers tasks thanks to integrations with most common RMM and PSA tools, hosting control panels and billing systems, and marketplace providers such as Autotask, ConnectWise (Automate, Manage, Control), Kaseya, Atera, Plesk, cPanel, CloudBlue, and AppDirect.
Moreover, service providers can turn themselves into value-added resellers and sell beyond the end-customer market with reseller management.
Is cloud storage better than local storage for backup as a service (BaaS)?
Depending on your client, they may have a preference on whether they want to store their data locally or in the cloud. Acronis offers service providers the option to back up to cloud storage hosted by Acronis, Google or Microsoft, their own cloud storage, or local networked storage. Supports more than 25 platforms, including Microsoft SQL clusters, Microsoft Exchange clusters, Oracle DB, and SAP HANA, which are supported in the Backup add-on for Acronis Cyber Protect Cloud.
What is a cloud-based disaster recovery solution?
A cloud-based disaster recovery solution is an offsite recovery option that ensures high-availability of business-critical data by quickly restoring workloads after natural disasters, human error, cyberattacks, or hardware or server failures. Disaster Recovery for Acronis Cyber Protect Cloud provides an all-in-one backup and disaster recovery solution to help service providers minimize complexity while growing their margins.
Does Acronis Cyber Protect Cloud include endpoint protection?
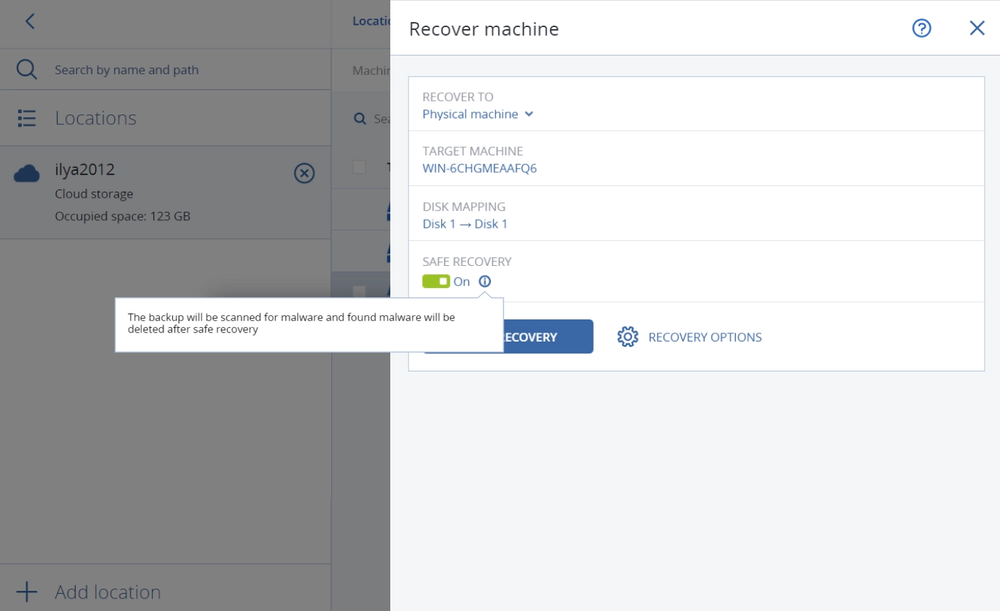
Acronis Cyber Protect Cloud includes best-of-breed anti-ransomware technology, strengthened with AI- and behavior-based detection focused on zero-day attacks. It also provides essential data loss prevention through device control.
Both the Acronis Cyber Protect Cloud agent and backups are protected by our comprehensive self-defense technology that prevents tampering.
The Security add-on extends endpoint protection with full-stack anti-malware to prevent a wider scope of threats, including web-based attacks and exploitation techniques. It increases the speed and accuracy of detection while ensuring zero-false positives. All collaborative applications benefit from prioritized protection, preventing exploitation of their processes. For more aggressive scanning, the anti-malware scans in the Acronis Cloud reduce the load on endpoints while ensuring no threat can reoccur.
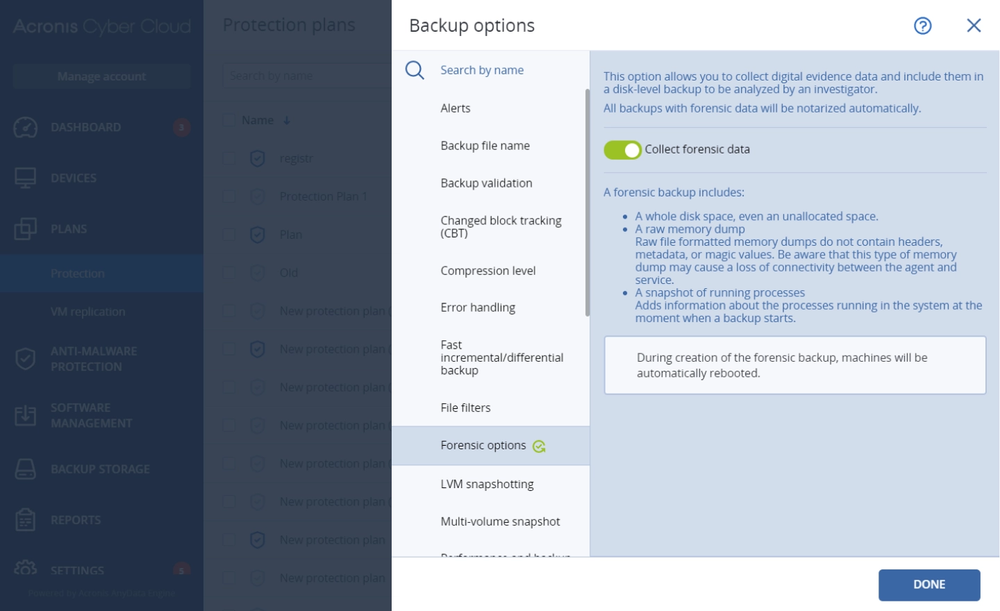
Acronis Cyber Protect Cloud with Security also eases remediation and makes security investigations less costly by collecting digital forensic evidence and storing them in backups.
Does Acronis Cyber Protect Cloud contain a patch management solution?
Acronis Cyber Protect Cloud provides vulnerability assessment technology to properly identify security gaps before they pose a serious threat to the IT environment.
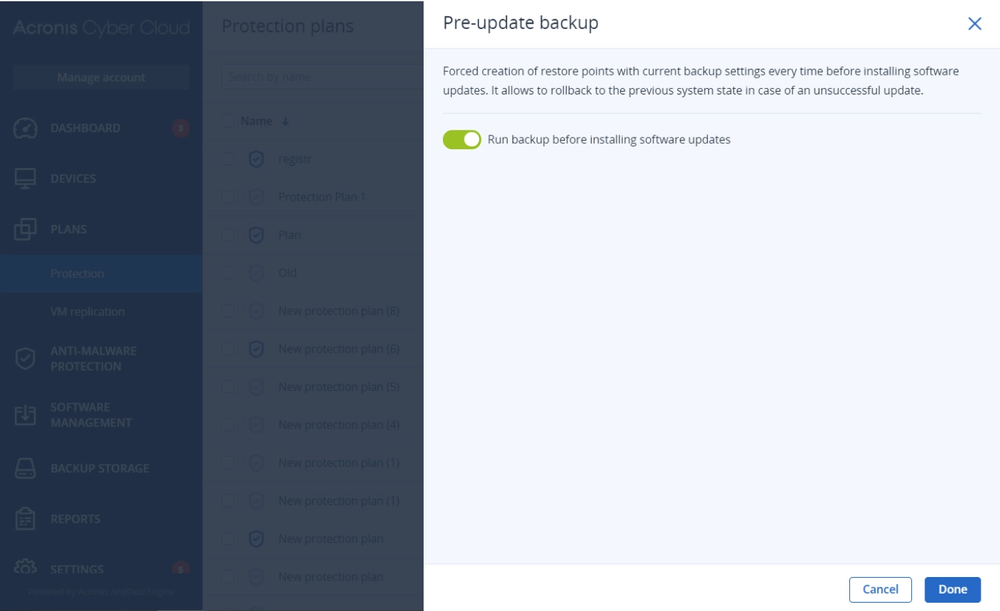
The Management add-on helps map the vulnerability assessment process to patch management for prioritized patching based on criticality. It also reduces the service provider’s management burden with patch management automation and fail-safe patching technology, which automatically backs up the system before a patch is applied to enable easy rollback in case the update renders the system unstable.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.