- Maximize productivity and collaborationIncrease your clients’ operational efficiency by enabling them to easily share data and files with colleagues, customers, and partners. Support their digital transformation with simple file and link sharing, controlled access with custom permissions, eSigning, and file notarization.
- Mitigate security risksHelp your clients reduce fraud, interference, or data loss. Leverage a HIPAA-compliant file sync and share service with encryption at rest and in transit, full control over data location, and data authenticity powered by Ethereum blockchain to record and verify notarizations.
- Boost revenue growthExpand your offering with an File sync and share service that supports Apple and Android smartphones and tablets, Windows PCs, Macs, and all popular web browsers. Increase client retention and generate new revenue streams by easily upselling to your existing customer base.
Create and securely share content from anywhere, at any time and on any device with Acronis Cyber Protect Cloud — a single solution that integrates best-of-breed backup and recovery, next-generation anti-malware, endpoint protection management and simple file sharing. Add the File Sync and Share pack to the pay-as-you-go file sync and share service to electronically sign any document with user identification and document integrity, in conformity with eIDAS regulation.
| Sync and share from any device: Support for Apple and Android smartphones and tablets, Windows PCs, Macs, and all popular web browsers | | |
| Folder sharing | | |
| PDF editing and annotation tools | | |
| Unlimited file versioning | | |
| Audit trail section: Shows the history of all activities | | |
| Encryption at rest and in transit | | |
| Two-factor authentication | | |
| Control over files and folders, and policy controls for users, applications and data | | |
| Remote file notarization: Accelerate the pace of your clients' business by digitizing their notarial processes | | |
| Embedded eIDAS AdES B-LTA eSignature | | |
| Notarization and signature certificates: Give an irrefutable proof that a file was notarized or signed at a specific time | | |
| Trusted, independent verification | | |
On-demand trainings

Upcoming events
Capabilities designed for secure collaboration
Rely on an easy, efficient, and secure file sync and share service that is specifically designed to help you provide the data protection, authenticity, and privacy your clients need to stay ahead of today’s threats and regulations.
Secure file sync and share
Complete end-to-end encryption, enterprise-class audit trails, control over files and folders, and sophisticated policy controls for users, applications, and data.Access from any device
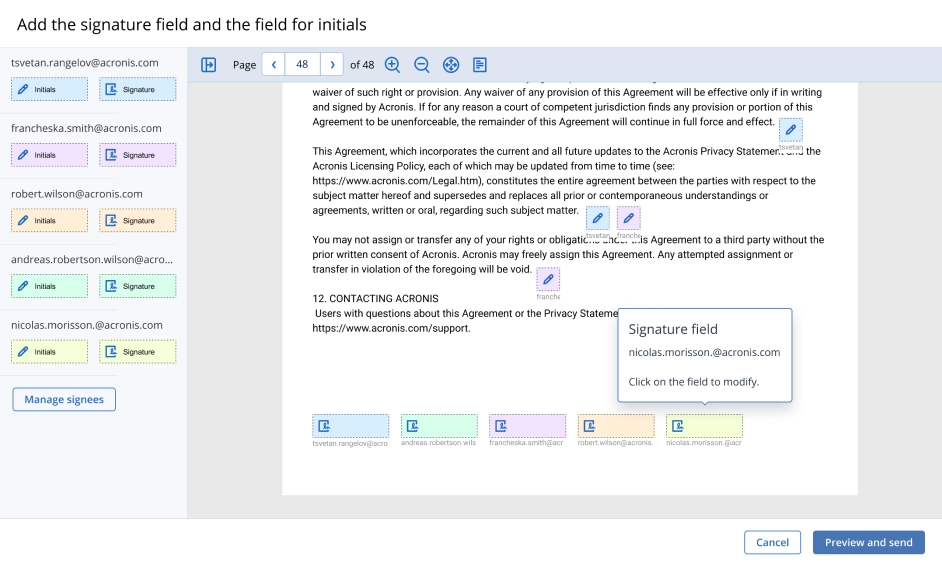
Empower clients with the ability to securely create, edit, sign, notarize, verify, and share data using their own smartphones, tablets, PCs, Macs, or web-enabled devices.File notarization
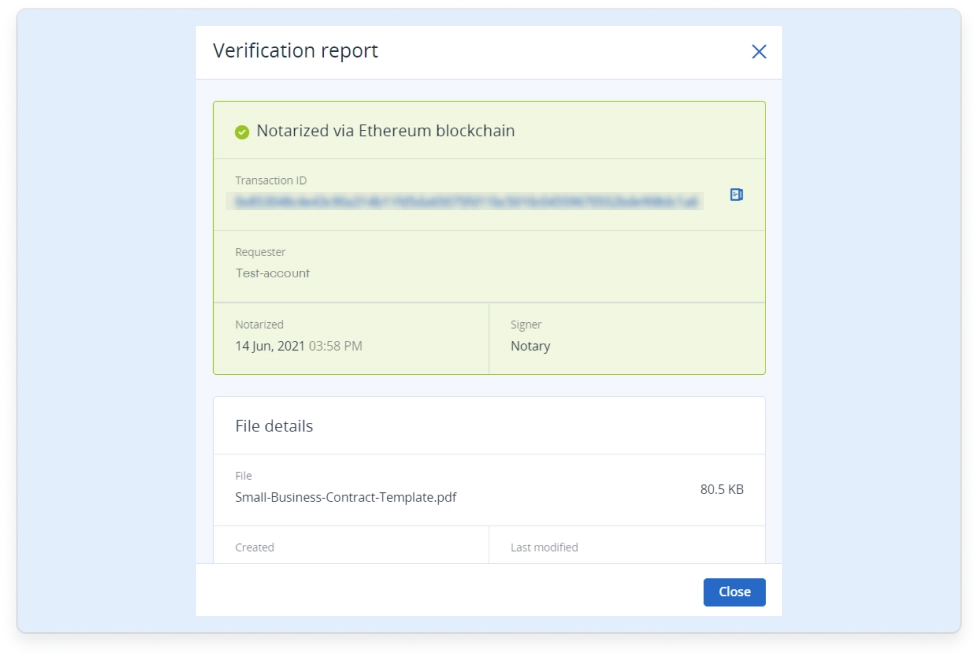
Notarize files of any format and type, generating a time-stamped, blockchain-based certificate that provides irrefutable proof the file is original and unaltered.Embedded eSignatures
Easily execute every step of the document workflow – from creation, to sending the document to multiple signees – with an easy drag, drop, and sign feature.
Acronis Professional Services
If your organization has a complex IT infrastructure or limited IT resources, Acronis Professional Services can assist you with the design, integration, implementation and on-going operation of your Acronis solution.
Consulting services
Leverage Acronis’ experience and shorten the time it takes to gain value from your Acronis investment.- Exclusive
Deployment services
With Acronis Deployment Services, you can be the first to market with data protection, infrastructure migration, and disaster recovery services. Audit services
Decrease maintenance costs and enjoy peace of mind knowing your customers’ data is protected in accordance with industry and Acronis best practices.Educational services
Enable your personnel to drive data protection, migration, and disaster recovery services enablement, effectively support your customers.
Expand your services with advanced protection
Add other powerful components to strengthen your services even further with advanced protection and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
- Security + XDRInstead of counting on a costly and complex stack of point solutions, Acronis XDR introduces natively integrated, highly efficient protection built for MSPs:
- Natively integrated cybersecurity, data protection and endpoint management
- Highly efficient security designed to protect the most vulnerable attack surfaces with AI-guided incident analysis and single-click response
- Built for MSPs, including a single agent and console for all services
- Security + EDRInstead of counting on a costly & complex stack of point solutions, Acronis enables MSPs via integration of EDR, endpoint management, and backup & recovery to:
- Easily launch a complete security solution, including rapid recovery
- Protect against modern threats and readily comply with cyber insurance requirements
- Maximize efficiency through a single security platform
- Acronis RMMAchieve peak MSP performance with a natively integrated, secure, AI-powered RMM. Enhance client satisfaction by delivering superior IT administration and monitoring services while improving security posture for both endpoints and Microsoft 365. Boost technician performance with seamless automation of IT management.
- Automated patch management
- System and hardware monitoring
- AI-assisted scripting and more
- Acronis PSASimplify success with an easy-to-deploy, adopt and use PSA tailored for modern recurring and cloud MSP business models. With Acronis PSA, you take the shortest path to increased profits and streamlined business operations.
- Service desk
- Billing and invoicing
- KPI reports and more
- Advanced BackupDefend clients’ data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You can also gain visibility into data-protection statuses across your clients’ infrastructure.
- Continuous data protection
- Data protection map
- Off-host data processing
- Disaster RecoveryGet clients back to business in mere minutes when disaster strikes by spinning up their systems in the Acronis Cloud and restoring them anywhere, ensuring immediate data availability. Make disaster recovery painless and increase efficiency with orchestration, runbooks, and automatic failover.
- Disaster recovery orchestration
- Production failover
- Site-to-site VPN
- Email SecurityBlock any email threat, including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero days in seconds before it reaches end users. Leverage Perception Point’s next-generation technology for lightning-fast detection and easy deployment, configuration, and management.
- Anti-phishing and anti-spoofing engines
- Anti-evasion and account takeover protection
- Next-generation dynamic detection against zero-days
- Data Loss Prevention (DLP)Prevent leakage of sensitive data from endpoints via more than 70 local and network channels and strengthen compliance with minimal effort and speed to value.
- Content-aware data loss prevention
- Automatic client-specific DLP policy creation and extension
- Pre-build data classifiers for common regulatory frameworks
- File Sync and ShareGet a full control over data location, management and privacy with a file sync and share service, including a transaction ledger to enable notarization and eSignature capabilities, across all platforms.
- File notarization
- Embedded eSignatures
- Independent file verification
Global data center presence
Help your clients meet their unique needs by storing their data where they choose. With multiple data centers worldwide, Acronis enables you to meet the compliance, data sovereignty, and performance requirements of all your clients.
Learn More, Earn More with Acronis Academy
Whether you and your team are seeking professional certifications or starting an MSP business, we're here to support you at every stage.

Start learning for Free
New! MSP Academy offers budding and seasoned MSP professionals vendor-neutral training covering the A-Z of managing a successful MSP business.
Train on-demand
Access our most popular sales and technical training courses designed for existing MSPs looking to enhance their cybersecurity skills and knowledge.
Login to Partner Portal
Available exclusively to Acronis Partners. Access our complete Acronis Academy training catalogue and earn your required certifications.
Looking for help?
Frequently Asked Questions
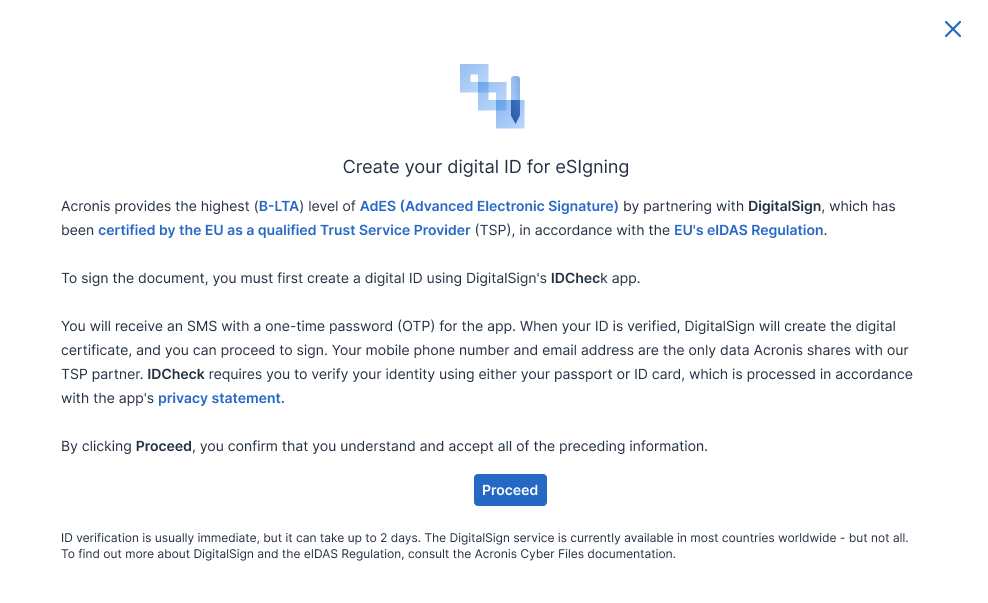
Why is it important to respect the eIDAS regulation
eIDAS is an E.U. regulation, also known as the Electronic Identification and Trust Services Regulation, or eIDAS Regulation 910/2014/EC.
While contracts were previously expected to be signed in person or in wet ink, the eIDAS regulation empowers businesses and customers to sign contracts digitally and securely, paving the way for easier cross-border transactions.
What is AdES B-LTA signature
An advanced electronic signature is an electronic signature which is:
- Uniquely linked to and capable of identifying the signatory;
- Created in a way that allows the signatory to retain control;
- Linked to the document in a way that any subsequent change of the data is detectable.
B-LTA level provides requirements for the incorporation of timestamp tokens that allow validation of the signature long after its generation. This level aims to tackle the long-term availability and integrity of the validation document.
How can eSignature validity can be checked?
All electronic signatures of the document can be analyzed and reports produced with the validation results on https://dss.nowina.lu/validation or https://ec.europa.eu/digital-building-blocks/DSS/webapp-demo/validationHow do you choose a file sharing service for a business?
There are a lot of file sync and share solutions on the market, so it is important to evaluate the solution that’s right for specific business environments.Key criteria include:
- Security — Does it provide the industry’s strongest security? Does it support multifactor authentication (MFA)? Does it enable encryption at rest and in transit, access control for files or policy controls for users, apps and data?
- Efficiency — Does it enable users to work on files using popular mobile devices, Macs and PCs? Does it enable users to annotate and edit documents on the go?
- Simplicity — Can you start using it quickly? Does it provide end users with an intuitive interface, eliminating the need for training?
- Upgrade — Does it support options to enable more functionalities “on the spot”; e.g., eSignature and blockchain-based data notarization?
- Embedded eSignature — Does it respect regulations that prove signature validity in front of a legal court?
- Embedded notarization — Does it provide the possibility to guarantee document integrity?
- Verification — Does it provide tools to prove signee identity and document integrity?
How to protect files?
To avoid financial and reputation damage that could result from a data breach, it is critical to handle a business client’s sensitive information carefully (e.g. customer or client data). Corporate files and data that are shared across different devices and locations should be protected with a secure cloud-based file sync and share service. A truly secure cloud FSS service is possible thanks to advanced methods for sharing and storing files, flexible policy controls, and highly secure data centers. These methods ensure you have full control over the data location, management and privacy.
Is online file-sharing secure?
It can be. Truly secure cloud EFSS services are possible thanks to advanced methods for sharing and storing files, flexible policy controls and highly secure data centers. These methods ensure you have full control over the data’s location, management and privacy.
FSS solutions that do not include such capabilities, however, should not be considered secure.
What is blockchain?
Blockchain is a technology based on the principle of a continuously growing list of data records, or blocks, which are linked and secured using cryptography. Each block contains a cryptographic hash of the previous block, including a timestamp and transaction data.
Most people know the term “blockchain” because it is used as the basis for cryptocurrencies like Bitcoin or Ethereum. But the underlying concept allows blockchain technology to have a variety of use-cases, such as file notarization, digital voting, creating smart contracts, and more.
The key advantages of the technology includes:
- Security: Blockchain uses strong cryptography to create transactions that are impervious to fraud.
- Distributed architecture: Blockchain leger is not owned by anyone as it can be distributed across multiple organizations and becomes more secure as replicas are added.
- Impossible to backdate changes: Every transaction is written into the ledger once and cannot be changed thereafter.
What is blockchain-based data notarization?
Blockchain-based services for data notarization allows users to notarize business critical data of any type by creating a digital fingerprint for files and automatically storing it in a public blockchain ledger. It empowers companies with independent validation of data authenticity and proof it existed at a specified date and time.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.