Reduce client risk with a comprehensive security approach
The risks of data loss, data leakage, and downtime can be prevented only with a security program that encompasses not just technology, but also people and processes. Acronis empowers MSPs to improve their threat prevention services to provide proactive protection and resilient processes, while increasing end-users’ security-awareness.

Cyber protection that encompasses people, process, and technologies
In addition to improving your team’s skills and productivity, certifications enable your company to advance to higher levels within the Acronis #CyberFit Partner Program, which unlocks exclusive benefits.
Prevent attacks that target people
People are the top targets of cyber criminals. No matter which cyber protection services you provide, human error is still the cause of 88% of breaches, according to Stanford University. Address your weakest link and enhance end-user preparedness with 700+ security-awareness training modules.Improve your processes to prevent zero-day threats
Improve your team’s cyberattack prevention processes with integrated and automated hardware and software detection, vulnerability assessments and failsafe patching.Prevent tomorrow’s attacks with modern technology
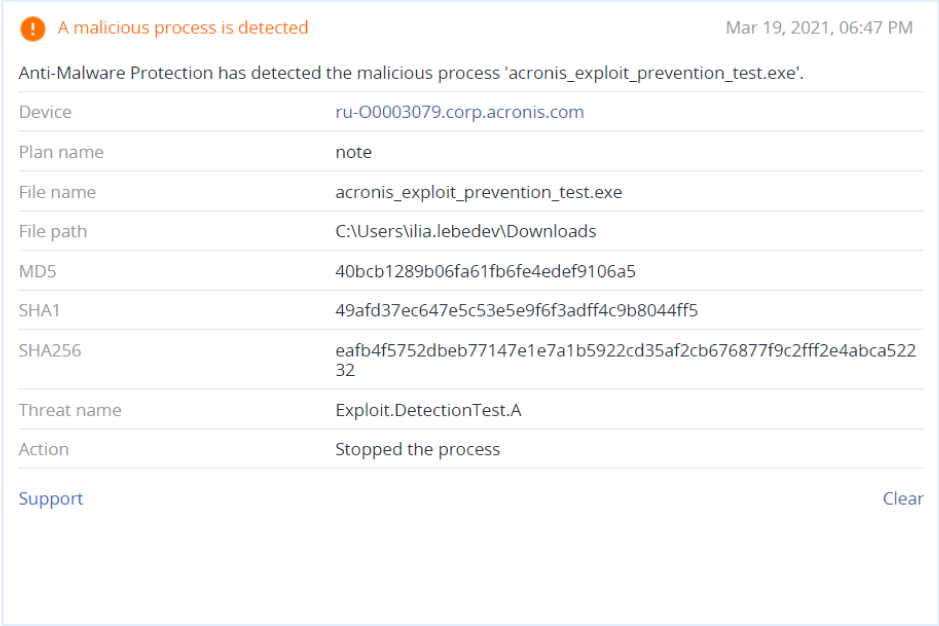
Modernizing your cybersecurity technology stack to be more proactive is critical. With just one agent, you can have a next-generation anti-malware service that enhances your cyber protection services to prevent loss or leakage of clients’ data, malware infections, and vulnerability exploitation.
A successful attack on a client can leak or completely destroy their data or result in long costly downtime before you’re able to react. Be a step ahead of cyberthreats and reduce client exposure to them with an integrated approach to cyber protection.
Request a demoUpcoming online events
Address vulnerabilities across 230+ applications with automated patch management
A proven MSP partner
Build your services on top of industry-proven protection








- 100% detection rateIn AV-Test certification under macOS, Acronis detected 100% of malware and had zero false positives.
- 0% false positivesIn the AV-Comparatives test, Acronis was one of only four solutions with zero false-positives.
- 100% high performanceIn all eight performance categories for AV-TEST, Acronis demonstrated either a Very Fast or Fast performance rating.
Acronis Cyber Protect Cloud
The only solution that integrates data protection, cybersecurity, and endpoint protection management
- Protect data on 30+ workload typesFrom a single console you can protect client’s data across physical, virtual, cloud, and mobile environments to prevent data loss.
- Deliver the most secure backup servicesCombine cloud backup with cyber protection capabilities. Offload client endpoints and employ more aggressive anti-malware scans of backed up data in the Acronis Cloud to increase detection rates and prevent reinfection.
- Store in the most convenient way for youAcronis provides multiple storage options, including Acronis Cloud, private and public clouds, and local network storage.
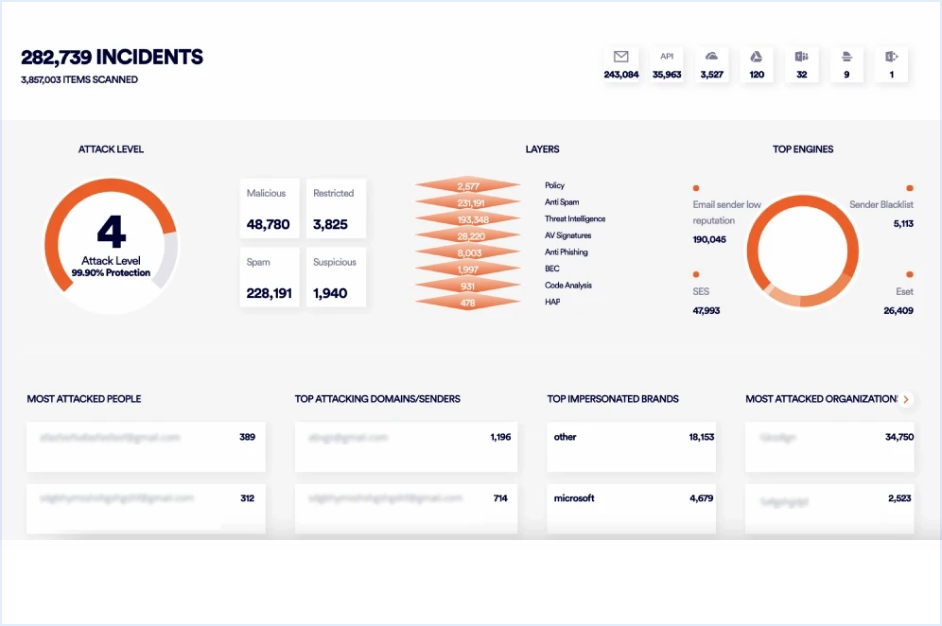
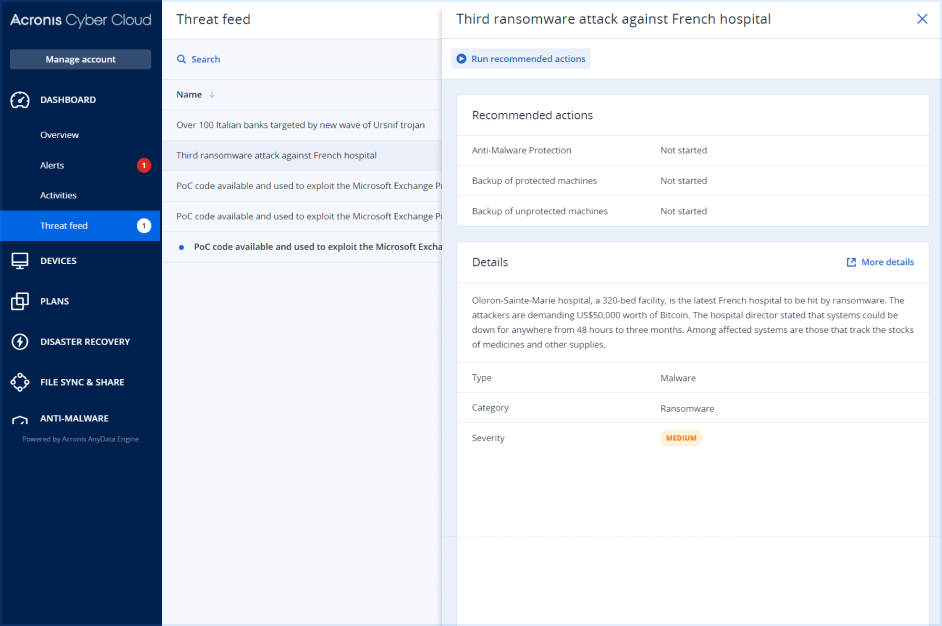
Every change to your clients’ IT environment or processes inadvertently introduces new risks and potential security gaps. Acronis Security Assessment Services enable you to apply a proactive approach to review a client’s security program and enhance your services with MSSP-level services.
Learn morePrevention is just one stage of modern cyber protection
To enable partners to deliver thorough protection for their clients, Acronis’ vision and products are based on a multi-stage process rather than simply detecting and blocking threats, leaving other risks unaddressed.
Prevention
Don’t wait for threats to hit, proactively protect your clients and limit their attack surface.Detection
Detect issues and threats in real-time before they pose risk to the IT environment.Response
Enable quick actions that immediately mitigate the risks before damage occurs.Recovery
Restore client data quickly and safely so no data is lost, with near-instant availability, in case of compromise.Forensics
Mitigate future risks and enable easy investigations by collecting forensics information.
Acronis Cyber Protect Cloud
The only solution that integrates data protection, cybersecurity, and endpoint protection management
Looking for help?
Frequently Asked Questions
How can I protect my clients from online threats?
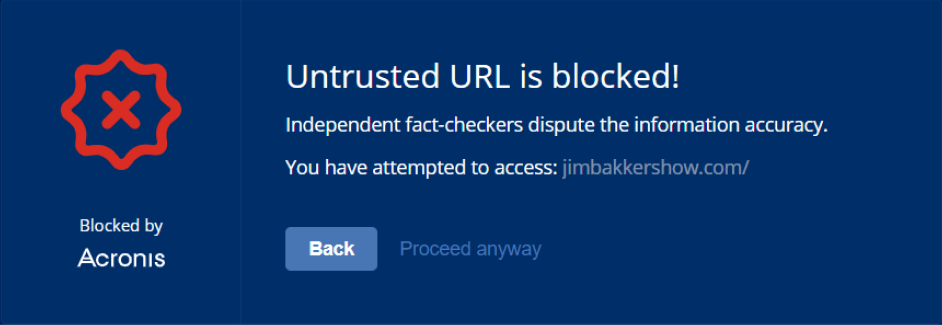
Acronis Cyber Protect Cloud enables you to deliver thorough cyber protection for your clients. The Advanced Security pack enables you to protect your clients from online threats via web filtering. The Advanced Email Security pack prevents all email-borne threats before they can reach clients’ mailboxes. The other anti-malware and protection layers of Acronis Cyber Protect Cloud, including the behavioral analysis enhanced with machine intelligence, ensure that online threats are prevented, even if they’re able to reach clients’ workloads.
Do clients need backup and disaster recovery if they already have prevention solutions?
The backup and recovery functionalities of Acronis Cyber Protect Cloud guarantee that even if clients are breaches with advanced attack techniques, or if they experience downtime due to system failure, you would be able to quick recover their systems and data to a good, known state.
The Advanced Disaster Recovery pack enables you to create disaster recovery plans to ensure faster recoveries and less downtime for your clients. While Advanced Backup extends the data protection capabilities of Acronis Cyber Protect Cloud with continuous data protection and ability to backup more workloads, including Microsoft Exchange, Microsoft SQL Server, Oracle DBMS Real Application clusters, and SAP HANA.
As some malware variants target backups, Advanced Security adds anti-malware protection for your clients’ backups, offloading their endpoints and applying more aggressive scans in Acronis Cloud, to prevent reinfection during recovery.
Do clients need backup and disaster recovery if they already have prevention solutions?
The backup and recovery functionalities of Acronis Cyber Protect Cloud guarantee that even if clients are breaches with advanced attack techniques, or if they experience downtime due to system failure, you would be able to quick recover their systems and data to a good, known state.
The Advanced Disaster Recovery pack enables you to create disaster recovery plans to ensure faster recoveries and less downtime for your clients. While Advanced Backup extends the data protection capabilities of Acronis Cyber Protect Cloud with continuous data protection and ability to backup more workloads, including Microsoft Exchange, Microsoft SQL Server, Oracle DBMS Real Application clusters, and SAP HANA.
As some malware variants target backups, Advanced Security adds anti-malware protection for your clients’ backups, offloading their endpoints and applying more aggressive scans in Acronis Cloud, to prevent reinfection during recovery.
How can we identify and close security gaps in across clients’ organizations?
Acronis Cyber Protect Cloud enables you to monitor clients’ applications for vulnerabilities across Windows, Mac, and Linux environments. The Advanced Management packs extends these capabilities, allowing you to close vulnerabilities across more than 230 Windows and third-party Windows applications with automated patch management.
Every change to client’s IT environment introduces new security gaps. Malicious attackers are able to bypass standard security solutions with newly introduced techniques and advanced threats. The Acronis Security Assessment service lets you deliver a thorough review of your client’s security program and align the cybersecurity strategy with their business goals through risk assessment, penetration testing, vulnerability scanning, and social engineering along with an actionable remediation report. Having a proactive approach is paramount to meet today’s complex cyberattacks.
Learn More, Earn More with Acronis Academy
Whether you and your team are seeking professional certifications or starting an MSP business, we're here to support you at every stage.

Start learning for Free
New! MSP Academy offers budding and seasoned MSP professionals vendor-neutral training covering the A-Z of managing a successful MSP business.
Train on-demand
Access our most popular sales and technical training courses designed for existing MSPs looking to enhance their cybersecurity skills and knowledge.
Login to Partner Portal
Available exclusively to Acronis Partners. Access our complete Acronis Academy training catalogue and earn your required certifications.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.