Summary
- Ransomware-as-a-service
- Written in C\C++
- Brings vulnerable drivers for privilege escalation
- Uses syscalls instead of direct calls to WinAPI
- Injects to the ‘svchost.exe’ process
Introduction
The analyzed BlackByteNT (also known as BlackByte 3.0) sample was spotted in February 2023, and had been already distributed for two weeks by that time.
Being an example of ‘ransomware-as-a-service‘ (RaaS), the threat actors constantly upgrade this malware to keep their customers satisfied. BlackByte ransomware has already seen three major changes. The first version was written in C#, the second in Go, and the third (BlackByteNT) is written in C\C++. Such changes in programming languages have a certain progression in increasing the complexity of the analysis for cybersecurity analytics, also bringing new anti-analysis and anti-debugging techniques.
Technical details
Overview
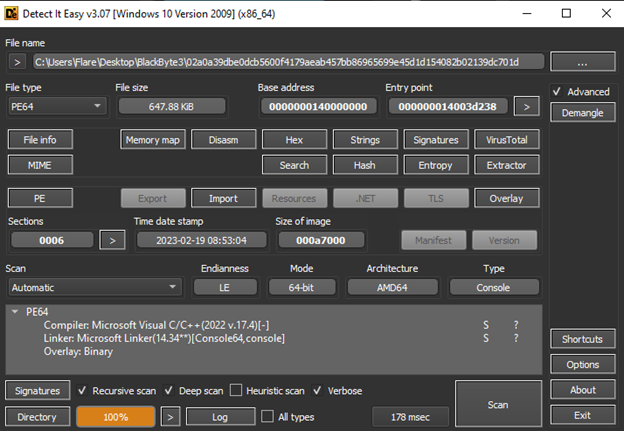
The sample that was loaded to VirusTotal is an unpacked version of the original BlackByteNT sample, which was packed with the UPX utility. This sample is a PE64 file, written in C\C++ and designed as a console application.
Execution
The first thing that BlackByte does is check what arguments are passed to the command line. If none of the checked-for arguments are passed, it terminates the execution.
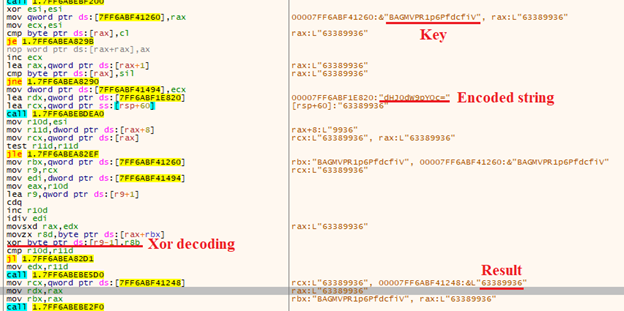
Assuming that one of these parameters is passed, BlackByte loads an encoded string and decodes it using XOR operation and a hardcoded key. The result will be a value, which must be passed to the command line after the given parameter. BlackByte then compares this with the value from the command line. If it differs from this value, execution is terminated.
If it matches, execution proceeds. During analysis, we observed the following behavior with different parameters:
-a – inject to ‘svchost.exe’, do not encrypt files
-w – inject ‘svchost.exe’, encrypt files
-s – inject ‘svchost.exe’, encrypt files
-q – do not inject to ‘svchost.exe’, do not encrypt files
One additional argument can be passed after the main parameter – ‘svc’.
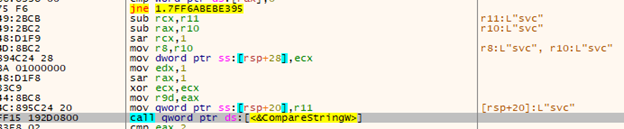
This will cause BlackByte to create a new thread and use the ‘StartServiceCtrlDispatcherW’ function to register a new service with a random name.
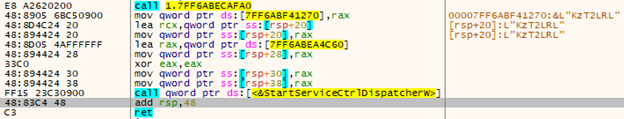
This sample doesn’t have a lot of imports, but it decodes their names during execution.
Then it stores them in local variables.
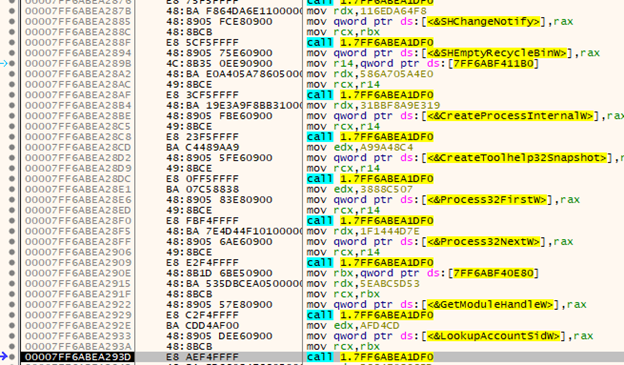
BlackByte creates four new files in the ‘C:\SystemData’ folder.
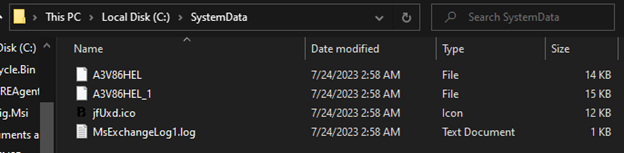
These files are:
A3V86HEL – RTCore64.sys, a Micro-Star MSI AfterBurner kernel mode driver (CVE-2019-16098).
A3V86HEL_1 – DBUtil_2_3.Sys, a Dell Client firmware update utility driver (CVE-2021-21551).
jxUxd.ico – an icon.
MsExchangeLog1.log – a log file.
The first two files are drivers with vulnerabilities, which can be exploited for escalation of privileges. One of these files, ‘RTCore64.sys,’ has already been used in the BlackByte v2 ransomware.
During execution, BlackByte writes data to the log file, which is probably used to log the execution process.
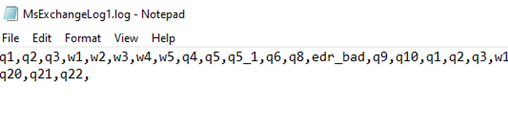
Then it executes ‘svchost.exe’ with the same argument as the sample.
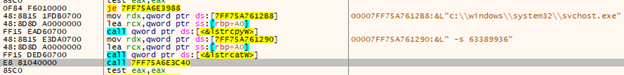
After the process is created, BlackByte searches for it with the ‘CreateToolHelp32Snapshot,’ ‘Process32First,’ and ‘Process32Next’ functions for further injection.
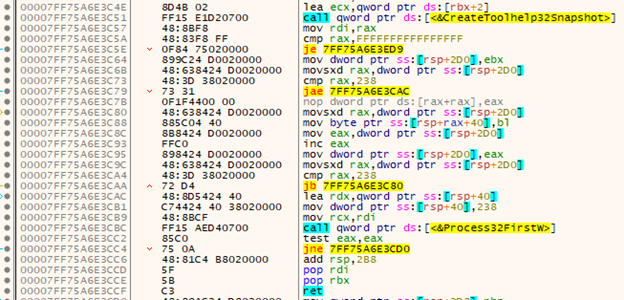
The initial ransomware process deletes its original file by creating a ‘cmd.exe’ process with the ‘CreateProcessInternalW’ function, using the following command:
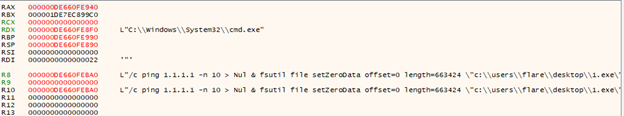
Then the original process is terminated; further work will be done in the ‘svchost.exe’ process.
File encryption
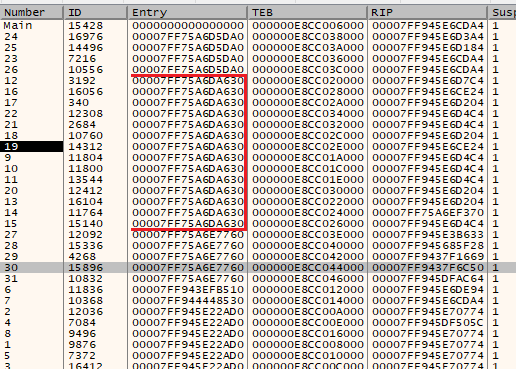
After the ‘svchost.exe’ process loads its imports, it proceeds to create new threads. It created 14 encryption threads in total, with a start address of ‘00007FF75A6DA630.’
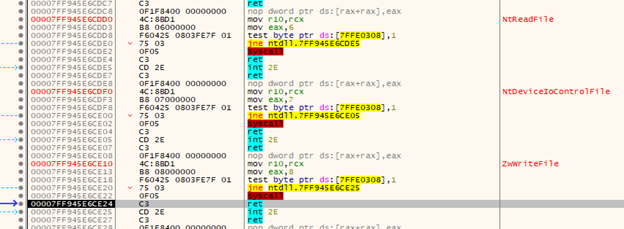
Throughout the execution process, BlackByteNT doesn’t call WinAPI functions directly. Instead, it uses syscalls to additionally evade endpoint detection and response (EDR) and antivirus (AV) systems, which monitor user-mode hooks.
To encrypt users’ files, BlackByteNT uses an asymmetric Curve25519 elliptic curve cryptography algorithm and symmetric ChaCha20. Both of these algorithms are hardcoded in the sample. To generate a random 32-bytes key for each file it uses the 'CryptGenRandom()’ function.
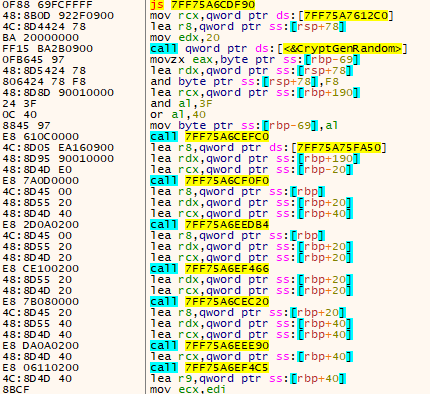
For each file, there will be at least two writing procedures. The first one is to encrypt data. The second one (always 41 bytes in size) adds the BlackByte data, where the first 9 bytes is ‘BLACKBYTE’ string and the other 32 bytes are a key, which is unique for each file.
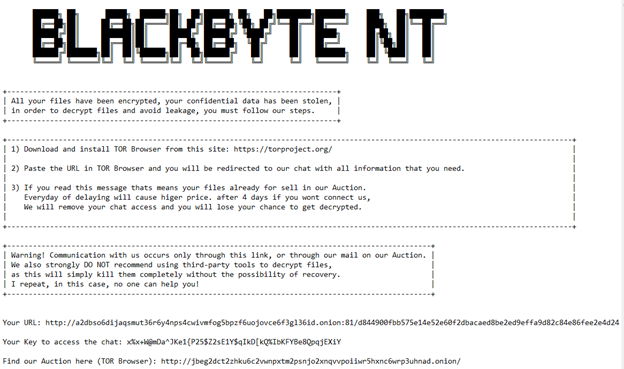
Ransom note
The ransom note ‘BB_Readme_CDXNB8WC.txt’ is dropped in each encrypted folder and opened automatically at the end of encryption. The note contains a personal URL and key to access chat with threat actors, and a link to the data auction.
Data leak site
The auction link points to the leak site, where victims’ data is sold.
Choosing one of the victims' tabs, we can see some screenshots of victims' files and four different buttons: pay for data, delete data (unavailable), download proof data, and buy data (unavailable).
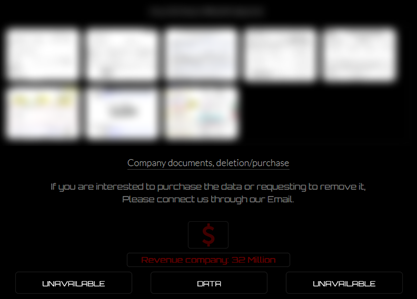
The proof data archive is hosted on the Anonfiles service and has 2.4 GB of stolen data, which anyone with this link can download.

Conclusion
As the third version of BlackByte ransomware, the ‘NT’ version continues to use vulnerable drivers to escalate privileges on the victims' machines. Aside from the programming languages, there is a difference in the encryption algorithms between these versions. The first and second versions use AES and RSA to encrypt files, and the ‘NT’ version uses Curve25519 elliptic curve cryptography algorithm and ChaCha20. As this malware operates as ransomware-as-a-service, it is possible that in the future there will be new versions of BlackByte.
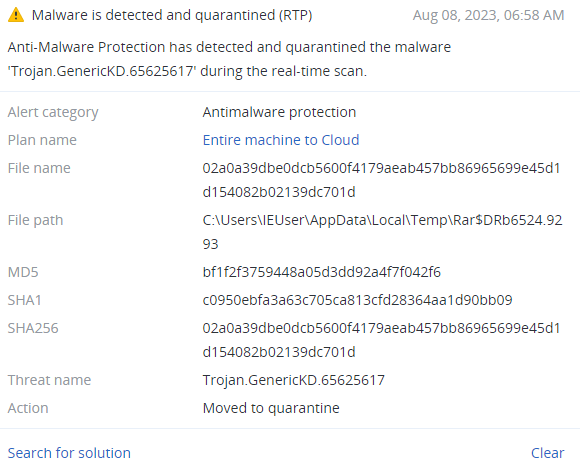
Detected by Acronis