The only security suite specifically designed and optimized for Azure
Acronis Cloud Security protects Azure virtual machines, networks and disks. Organizations can take advantage of a simple GUI console, which includes a virtual firewall, agentless antivirus with optimized scanning, deep packet inspection, intrusion detection (IDS), and network analytics with granular user and tenant access control. Today, businesses of any size can meet their industry’s compliance and regulatory needs without deploying multiple Microsoft Azure cloud security solutions.
Technical Differentiators
- Unified Security Suite A single solution for virtual firewall, agentless antivirus with optimized scanning, deep packet inspection, intrusion detection (IDS), and network analytics.
- Easy Network Logging Automatically configure resource providers and Azure resource groups on every security network without having to access the Azure Portal.
- Simple and Intuitive Interface Built-in firewall rule templates, quick configurability, intuitive management and same GUI console as on-premises version simplifies management.
- Prevents Antivirus Storms Patented technology only analyzes files that have been created, accessed or changed since the last scan resulting in 70X faster scans, less disruption and almost no performance impact.
- Automatic, Immediate Protection Ensures agile VM deployment and security by automatically and immediately protecting newly created VMs in an Azure Resource Group.
- Agentless Introspection The virtual appliance runs outside of the VMs it is protecting and does not require additional software or agents and supports all guest operating systems, including Windows and Linux.
- Granular Tenant Isolation Users are assigned specific networking resources which only they can access which improves Quality of Service (QoS) and prevents infected VMs from attacking others.
- No Hardware Required Virtualized security components which can be created on-demand and changed at scale eliminate the need for hardware components like routers and firewalls.
- Supports Any Guest OS The virtual appliance runs outside of the VMs it is protecting and does not require additional software or agents and supports all guest operating systems, including Windows and Linux.
Acronis Cloud Security Features
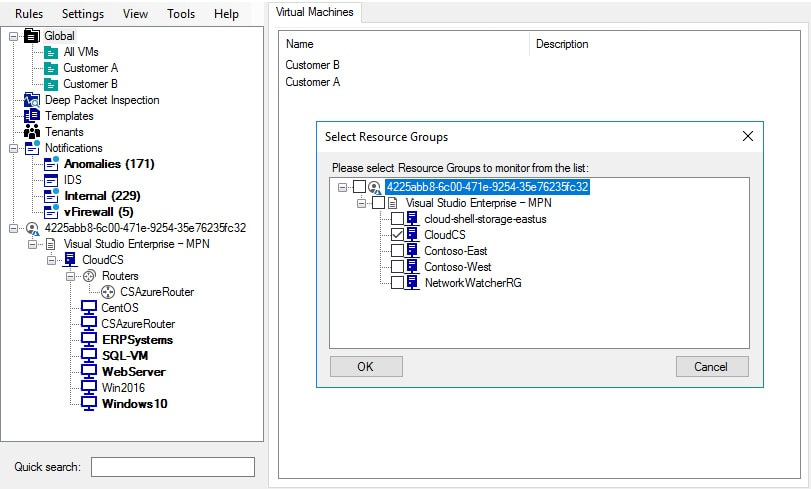
Azure Subscription Management
Protect Azure VMs without having to enable network logging through the Azure Portal. With Acronis Cloud Security you do not have to continually configure resource providers, register new providers, create Azure Resource Groups, configure logging, enable diagnostics or configure log settings.
- Easily populate Microsoft Azure credentials directly into the Acronis Cloud Security console
- Select the resource groups to monitor and Acronis Cloud Security takes care of the rest
- The system automatically retains settings for each administrator
- An intuitive interface eliminates the pain of continually accessing the Azure Portal
Virtual Firewall
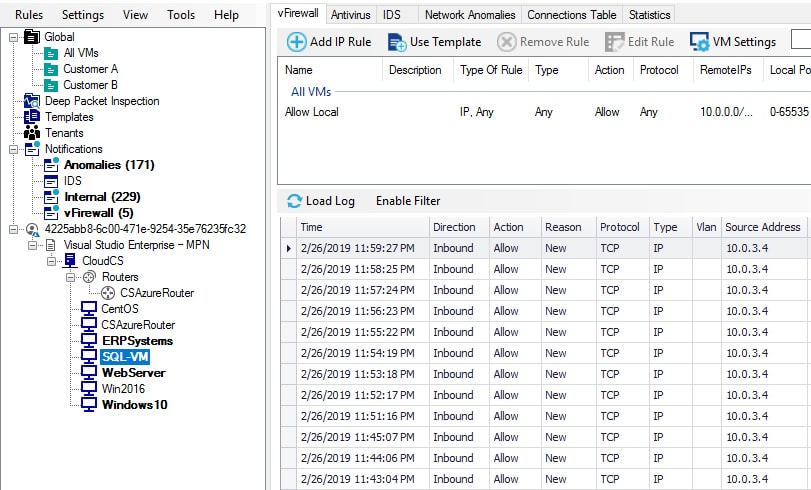
The Acronis Cloud Security virtual firewall allows organizations to control all inbound, outbound, and VM-to-VM traffic by intercepting and inspecting network packets in the virtual appliance before they reach their virtual machines and virtual networks.
- Configure firewall rules to allow or block inbound or outbound traffic
- Apply rules to specific VMs, IP addresses, MAC addresses, or VLAN IDs
- Monitor broadcast, unicast, or multicast transfers across a variety of protocols, including ICMP, IGMP, TCP, UDP, GRE, or ICMPv6
- Protocols can be defined manually
- The system supports both IPv4 and IPv6
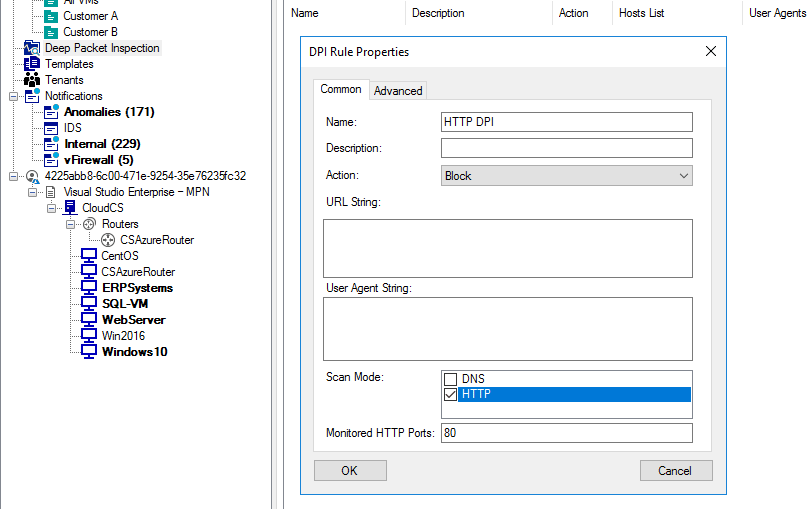
Deep Packet Inspection (DPI)
The Acronis Cloud Security virtual firewall offers DPI on HTTP and DNS packets.
- The system allows the data portion of the network packet to be inspected for specific strings or URLs even if the traffic passed through the firewall
- Block specific sites which could disrupt network traffic or distract end users, like social media or file-sharing websites
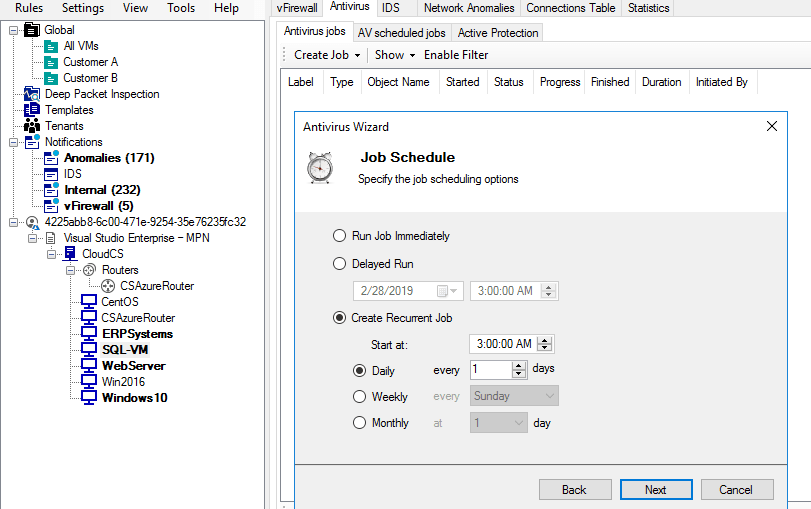
Agentless Antivirus
Acronis Cloud Security has built-in AV so that organizations do not need to acquire and deploy third-party antivirus solutions separately. Active Protection™ looks for threats on the VMs as they are written to the disk. When a vulnerability is discovered, Acronis Cloud Security immediately notifies you before it has a chance to spread throughout the network.
- The platform includes licenses and AV signatures from Bitdefender.
- Acronis Cloud Security protects VMs at the networking layer through a virtual router, and does not require an antivirus agent to be installed
- There is no dependency on the end-user to install a security solution or run antivirus
- The system prevents malicious tenants from uninstalling security components running in the VM
- Meet compliance objectives that mandate admins cannot have VM access to install agents
- Protect all guest operating systems supported by Azure, including Windows and Linux
- Prevent antivirus storms that slow down VMs and cause noticeable performance impact
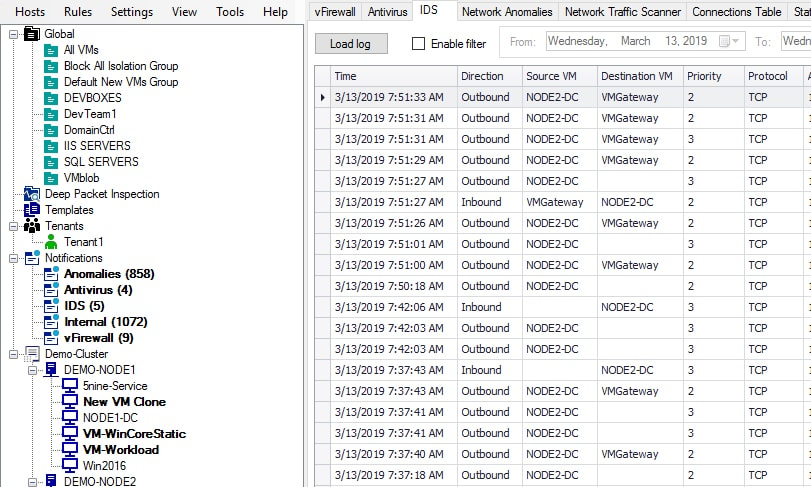
Intrusion Detection System (IDS)
Cisco Snort IDS rules are integrated into Acronis Cloud Security to identify different types of network attacks, including DoS/DDoS, direct access attacks, cross-site scripting, brute force, buffer overflows, CGI attacks, stealth port scans, and much more.
- If an issue is discovered the admin is alerted, and a detailed description of the threat is provided with recommended remediation actions.
- Cisco Snort licenses and support is provided by Acronis to ensure you only have one point of contact for your security needs.
- IDS updates can be scheduled and downloaded through a proxy server, which protects the security management server from being connected to the public internet
Automatic Protection
Assign VMs to groups and apply security settings to them automatically.
- The system ensures security policies are updated and applied in dynamic environments where VMs are rapidly deployed and destroyed
- Acronis Cloud Security applies security to virtual machines as soon as they are created and placed into a security group
- Newly created VMs can also have the virtual firewall, antivirus or intrusion detection system (IDS) automatically enabled
- Group multiple VMs and push settings to that collection to streamline bulk security or compliance changes

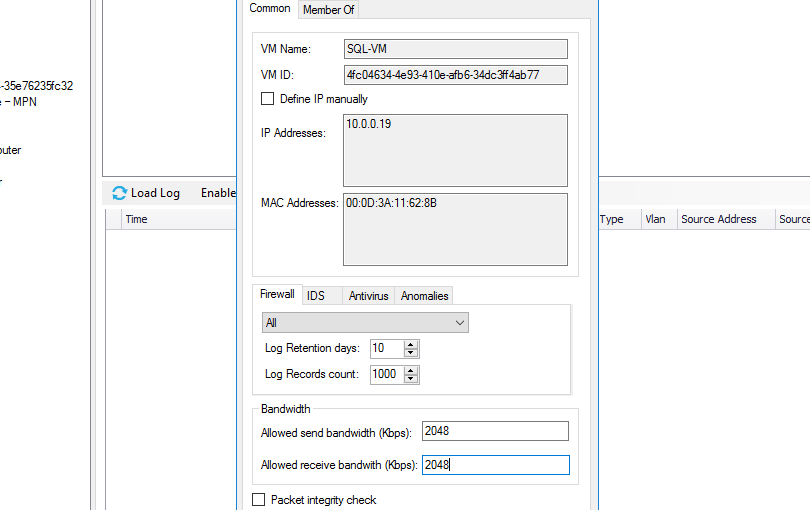
Quality of Service (QoS)
Manage network bandwidth configurations for each VM
- The system automatically enforces a policy that prevents any VM from consuming too many network resources
- Acronis Cloud Security mitigates the risk of impacting the performance of other VMs, services or users
- Configure a maximum amount of bandwidth for both inbound and outbound traffic
Network Statistics & Analytics
Get complete visibility into your virtual network’s usage.
- View all inbound and outbound network traffic statistics and connections
- Traffic is presented in both table and graph formats
- Filter information by direction, protocol, state, port, IP address and more
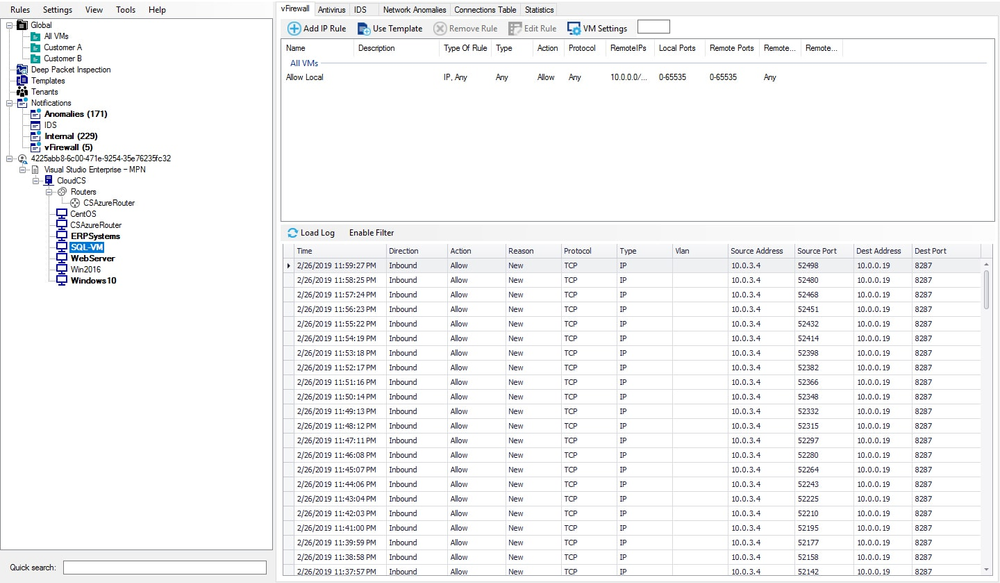
Network Logging
Log all the network traffic within your Azure Resource Groups.
- Each inbound and outbound packet which passes through the virtual router is logged with a timestamp, action, protocol, type, VLAN, source and destination information
- The system retains information for a configurable number of records or days
- Filter data or perform advanced analytics for testing, optimization or incident triage
- Acronis logs are extensible and written in the Syslog format (optionally with RFC5424 headers), to be forwarded to other SIEM systems for analysis, such as Splunk or Microsoft OMS
Events Logging
Any change made to the security management system, services or virtual infrastructure component is logged. Administrator actions are also logged to ensure compliance.
- The platform provides visibility into health and change status for compliance purposes
- Each audited event includes details like categories, objects, operations, targets, servers, and the results of the operation
- The system logs all user actions, tracks changes and is immutable to prevent tampering.
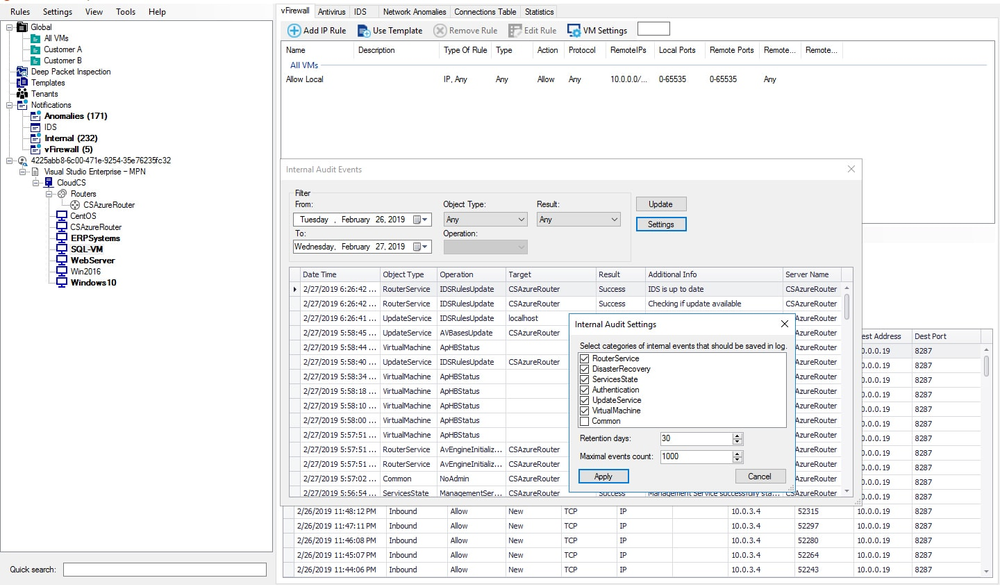
Granular User and Tenant Management
Role-based access control for each admin and tenant provides isolation across virtual resources.
- Access Acronis Cloud Security as an administrator or with read-only access using Windows security credentials or a custom account
- Apply tenant-level permissions to grant administrators access to specific security features
- By separating users and their resources, Acronis reduces the risk of threats passed between them
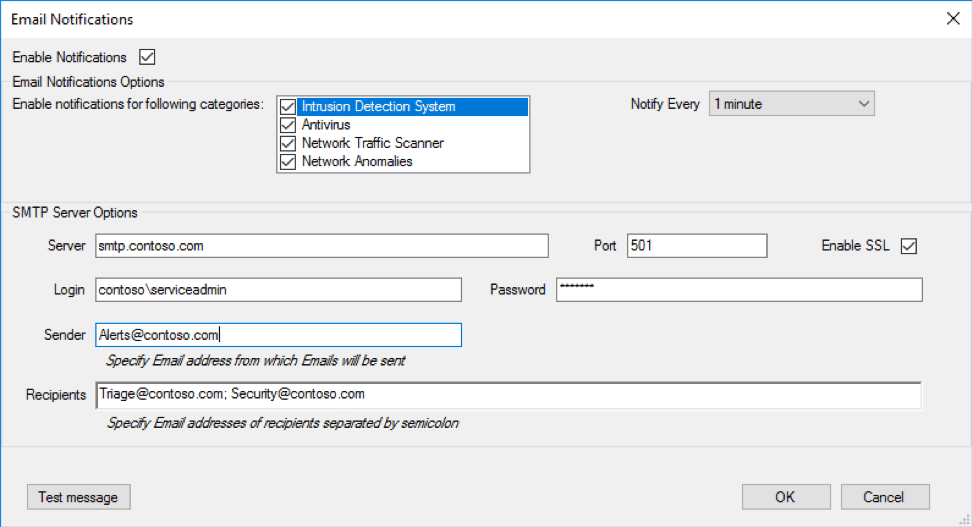
Alerts and Email Notifications
Acronis Cloud Security provides a variety of email alerting options so that admins receive notifications as soon as an issue is detected.
- Easily customize the frequency of communications
- Select from different threat categories
- Configure email alerts using an SMTP mail server
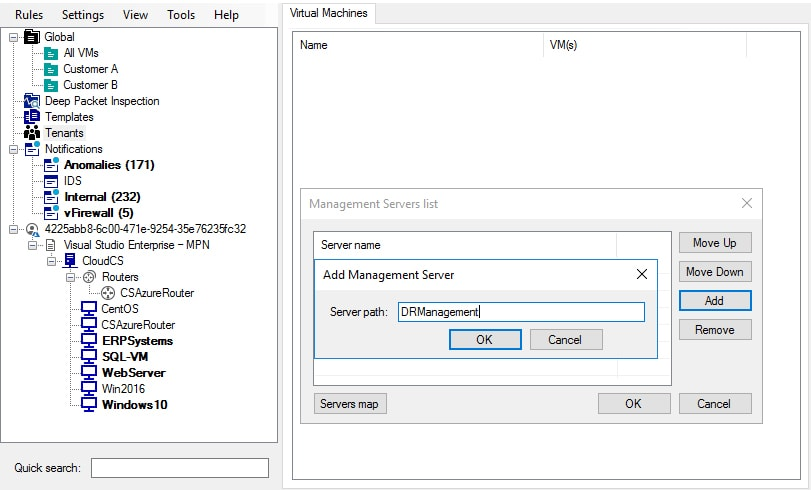
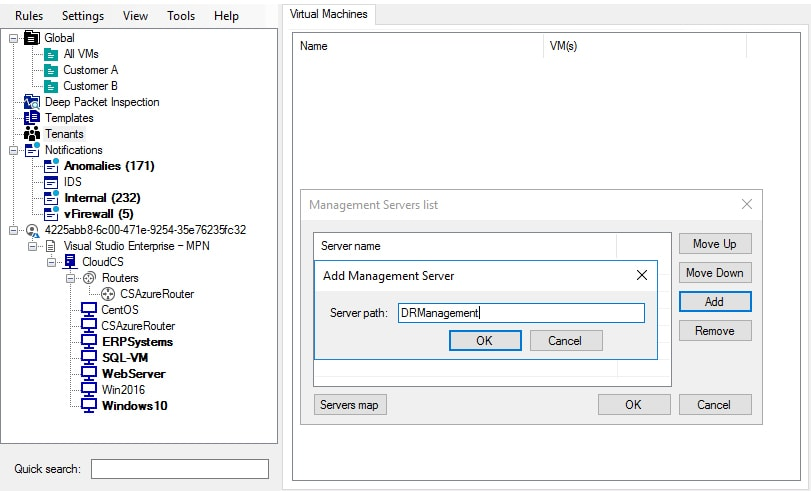
Highly-Available Security Management Infrastructure
Acronis Cloud Security for Azure is managed from a centralized GUI console running from a Windows computer, removing the need for admins to log into the Azure Portal to manage their security.
- The system supports an architecture where the management servers are redundant and can be run on physical servers or in clustered VMs
- The SQL database can be clustered and replicated to a backup location
- The management portal can be made redundant by having multiple consoles
- Different management servers can be mapped to individual Azure Resource Groups to distribute the processing overhead
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



