The Acronis Cyberthreats Report covers current cyberthreat activity and trends, as observed by Acronis analysts and sensors. Figures presented here — including malware, URL and ransomware statistics — were gathered in July of this year and reflect threats that we detected as well as news stories from the public domain.
This report represents a global outlook and is based on over 1 million unique endpoints distributed around the world. Most of the statistics discussed focus on threats for Windows operating systems, but macOS and Linux numbers are included where applicable.
Executive summary
In July, ransomware attacks remained prominent, exemplified by the MOVEit campaign — which impacted over 545 organizations and their customers, and exposed the PII of more than 32.7million individuals. Notably, MOVEit is the third significant case this year involving zero-day vulnerabilities exploited in file-transfer services, with Cl0p being responsible for similar attacks on Fortra's GoAnywhere and IBM Aspera Faspex.
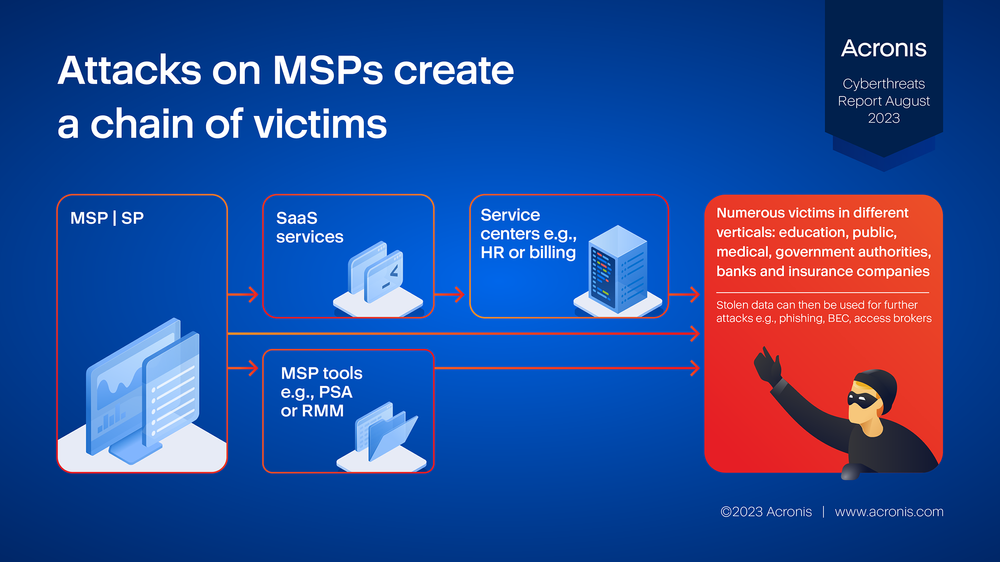
We've noticed an increase in the ongoing pattern of attacks targeting managed service providers (MSPs), where the MSPs’ software and services are used to compromise end users in different verticals, including government, finance, and education.
The top 5 numbers for this report:
- 16.6 million malicious URLs were blocked at the endpoint by Acronis in July 2023. That’s a decrease of 10% compared to June.
- Acronis detected 36,000 malware attacks in July, a 22% increase over June.
- Ransomware detections at the endpoint decreased by 6% from June to July. The most-active ransomware group in July was Cl0p, claiming 205 victims.
- In July, Acronis EDR detected more than 150,000 incidents, 90% of which were automatically remediated.
- We recorded almost 420 data breaches that were reported globally.
Incidents of the month
In July, the exploitation of MOVEit file-transfer vulnerabilities has been far-reaching; some organizations were affected directly, while others were exposed through third-party vendors. It all started when Progress Software disclosed a zero-day vulnerability in May, which was followed by the discovery of five additional vulnerabilities in the service.
It is estimated that the Clop ransomware gang will make between $75–100 million by extorting victims through their extensive MOVEit data theft campaign.
Among the victims thus far are:
- Siemens Energy, a Munich-based energy technology company with a revenue of €32 billion.
- Schneider Electric, the French multinational company, with an annual revenue of over $37 billion.
- The New York City Department of Education (NYC DOE), affecting approximately 45,000 students.
- Radisson Hotels Americas, an international hotel group with more than 1,100 locations.
- TomTom, the Dutch navigation giant, with a revenue of €536 million in 2022.
- First Merchants Bank, an Indiana-based banking giant with more than $18 billion in assets.
Attacks on MSPs can create a chain of victims, perpetuating an ongoing cycle of subsequent threats. We’ve noticed an increase in such attacks. Once an MSP is compromised, the attackers can either go directly after the end customer, abuse PSA/RMM tools to distribute their payloads, or try to compromise SaaS services. This may lead to service centers getting compromised, affecting customers in many different verticals. Stolen data — such as customer names, credentials, emails and invoices — is then subsequently used for further attacks.
Ransomware detections
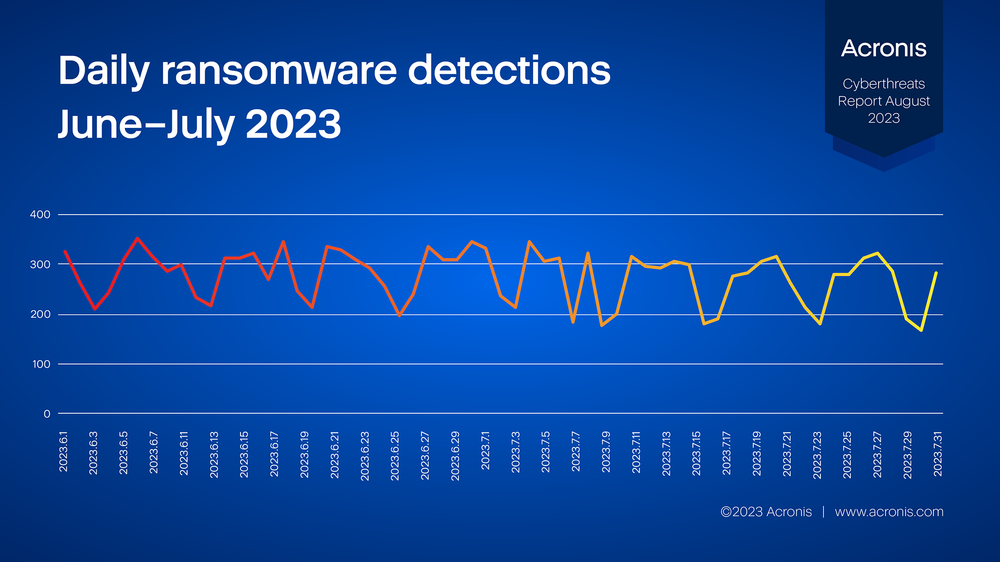
Ransomware detections in July dropped slightly, down 6% compared to June 2023. The day with the most ransomware detections was July 3, when 347 encryption attempts were blocked.
The following statistics are from Acronis anti-ransomware heuristics, which detects encryption attempts on any workload. This represents the last line of defense in the protection layer. Threats that reached this stage were able to penetrate or disable all previous layers of protection, such as email filters and static antivirus detections. The effective number of attempted ransomware attacks will thus be higher.
Ransomware detections by region
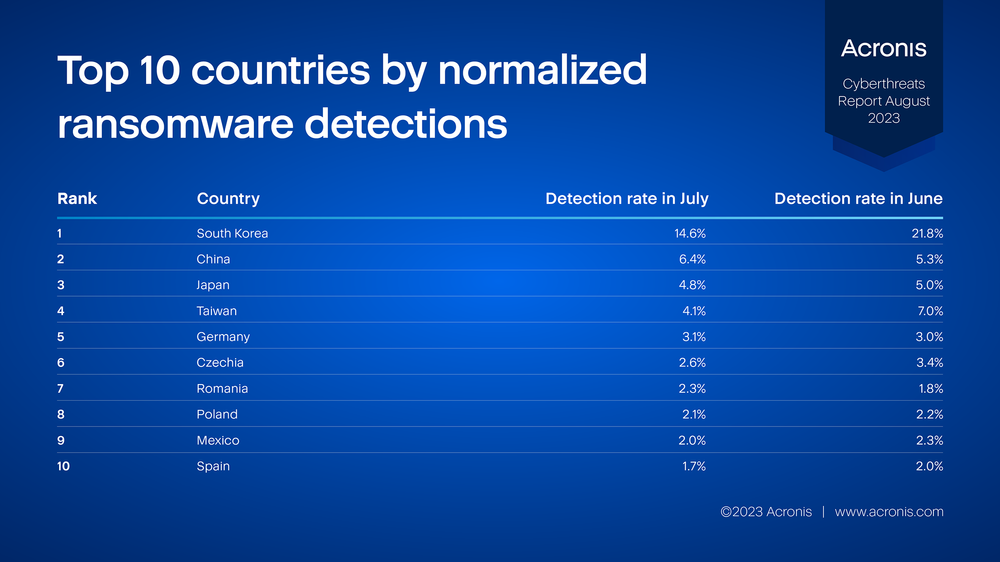
To assess the individual risk level per country, and to make the statistics meaningful and comparable, we use normalized threat detection numbers. This means we use the number of detections per country per month, divided by the number of active clients in that country. This ensures that larger countries are not overrepresented. Countries with fewer than 25 active Acronis product installations are not listed.
The following table shows the normalized percentage of clients with at least one ransomware detection in the given month. The higher the percentage, the higher the risk of a workload in that country being attacked by ransomware.
July ransomware victims
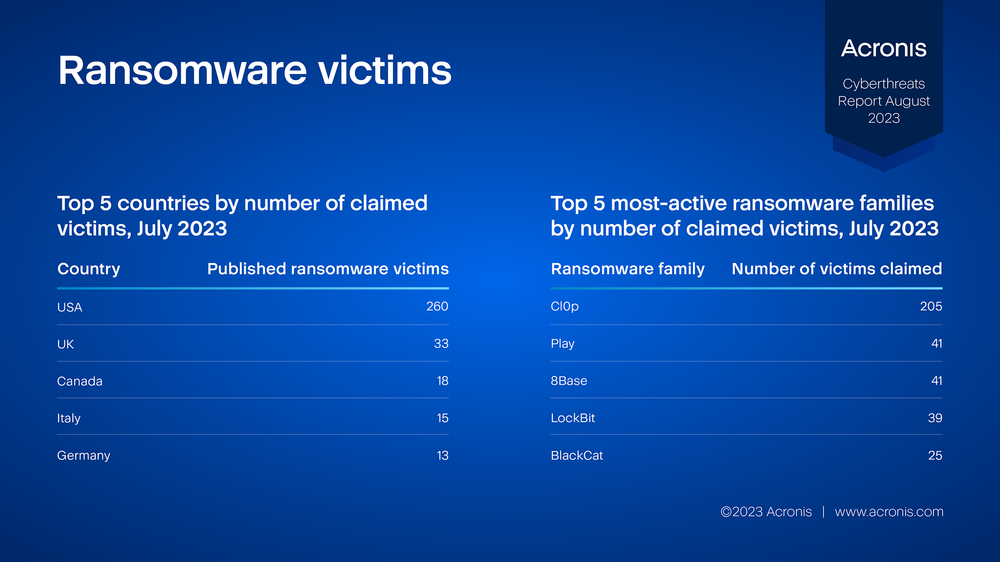
The following statistics are based on data from ransomware groups’ darknet websites, where they publish reports about breached victims and leak stolen files. These numbers may change slightly over time, as not all ransomware groups publish their victims right away, and some keep the names private while negotiating for ransom payments. These figures show the view from the ransomware groups’ side, which differs from the ransomware detection numbers listed earlier in this report.
The published numbers for July (526) dropped by 2% compared to June and show the largest quantitative number of compromises in the United States. The most-active ransomware group in July was Cl0p.
New ransomware groups
Since ransomware is still one of the most profitable types of malware, we do regularly see new variants appearing in the wild. In July, NoEscape and BigHead ransomware entered the stage.
NoEscape ransomware is thought to be a rebrand of Avaddon, known for shutting down and releasing decryption keys in 2021. It now targets enterprises with double-extortion attacks, stealing data and encrypting files on Windows, Linux, and VMware ESXi servers.
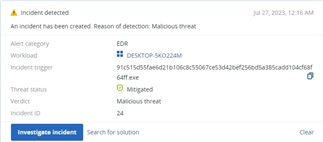
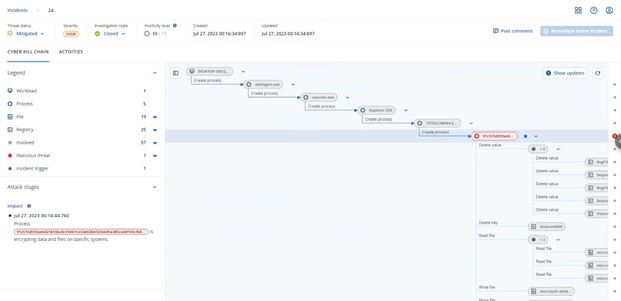
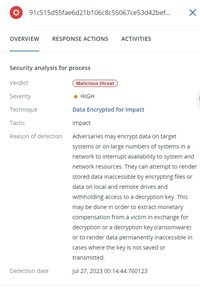
BigHead ransomware is likely spread through malvertising that promotes fake Windows updates and Microsoft Word installers. The malware is a .NET binary that installs three AES-encrypted files on the target system — one for malware propagation, another for Telegram bot communication, and a third for file encryption and displaying a fake Windows update.
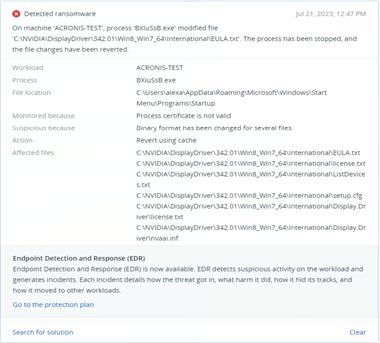
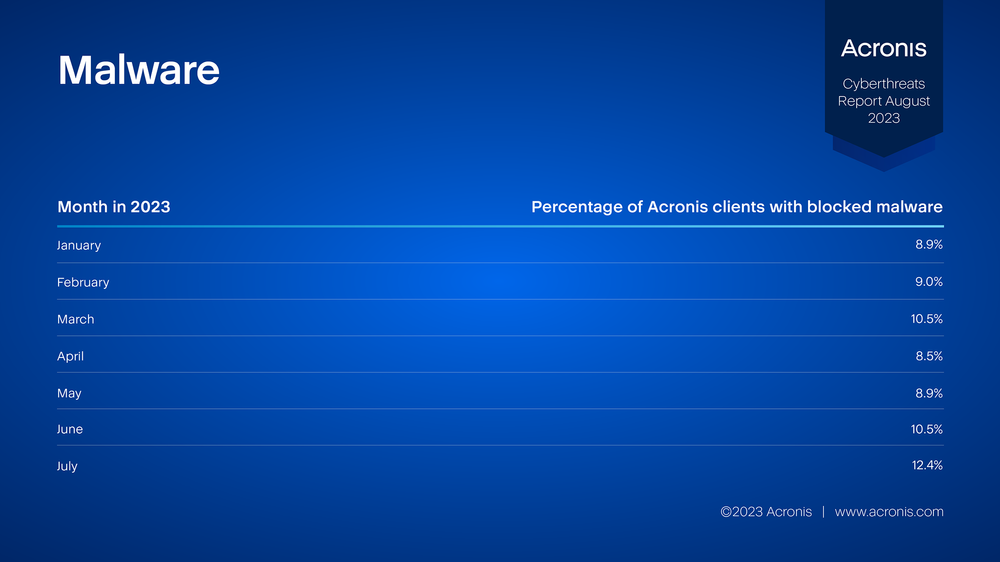
Malware
In July, Acronis Cyber Protect blocked 36,000 malware threats on endpoints, an increase of 22% compared to June. One of the most-active threats this month was the RedLine infostealer, continuing a trend of info-stealing Trojans. Stolen credentials are often sold on the internet and subsequently used for future attacks.
It’s important to stop malware early in the attack chain — for example, by blocking the malicious emails that deliver them. Nevertheless, many threats still do make it to the endpoint.
The following table shows the percentage of Acronis clients that had at least one malware threat blocked this month. This number has been hovering around 9% for the year so far.
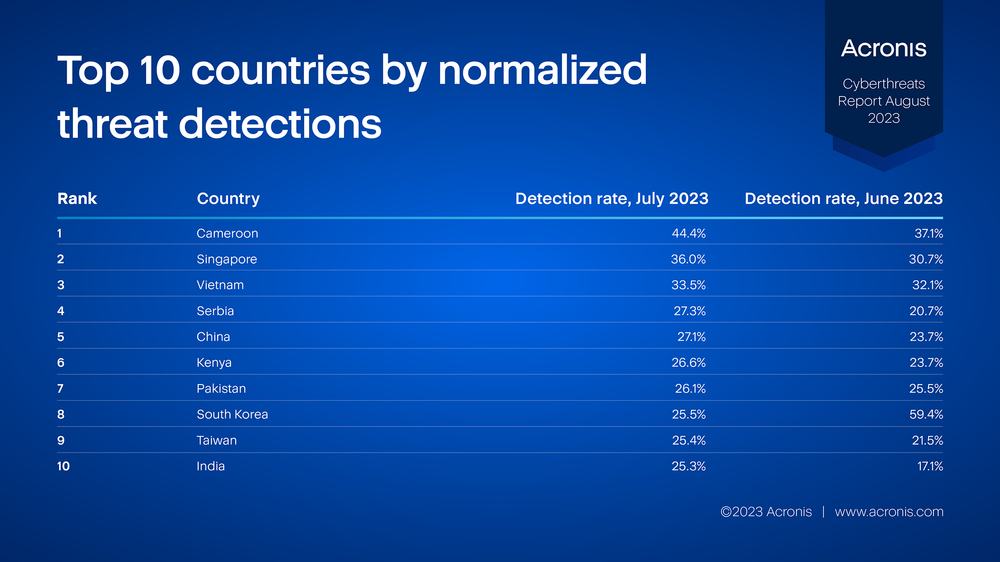
Normalized malware detections by region
The following table shows the normalized percentage of clients with at least one malware detection in the given month. The higher the percentage, the higher the risk of a workload in that country being attacked by malware.
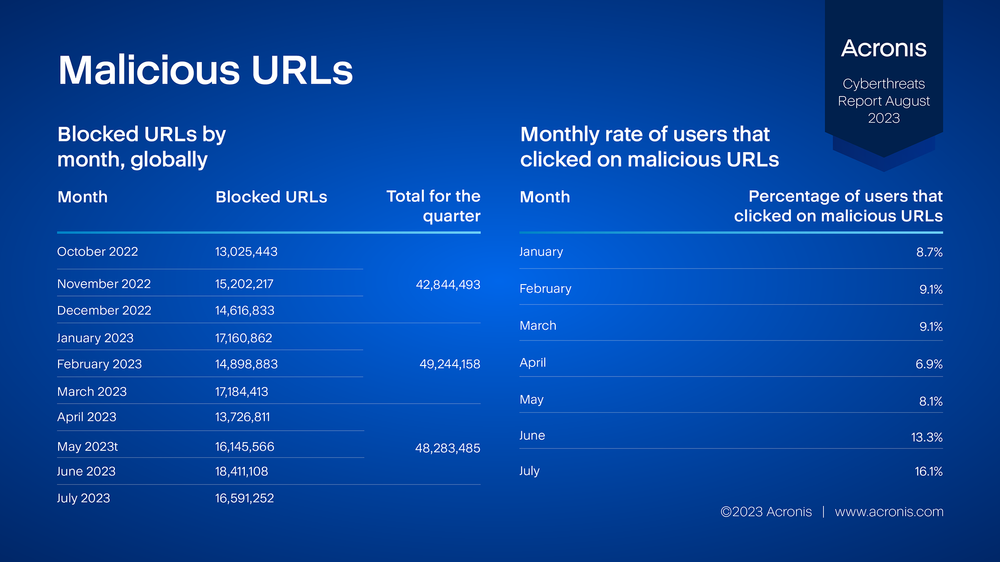
Malicious URLs
The Acronis Cyber Protection Operation Centers (CPOC) blocked 16,591,252 phishing and malicious URLs in July 2023. This constitutes a decrease of 10% compared to June. Malicious URLs continue to be a common tool for cybercriminals to deliver their payloads. Many attackers install a small backdoor application first, and have it connect to a command-and-control (C2) server in order to receive commands or download additional malware.
Normalized URL detections by region
The following table shows the normalized percentage of clients with at least one malicious URL detection in the given month.

Protection
The aforementioned threats can be detected and mitigated with solutions from Acronis.
Acronis Cyber Protect protects against both known and never-before-seen threats through a multi-layered protection approach. This includes behavior-based detection, AI/ML-trained detections, and anti-ransomware heuristics, which can detect and block encryption attempts and roll back any tampered files automatically, without any user interaction.
The Endpoint Detection and Response (EDR) pack for Acronis Cyber Protect Cloud brings the visibility needed to understand attacks, while simplifying the context for administrators and enabling efficient remediation of any threats.
Learn more about Acronis’ approach to cyber protection.



