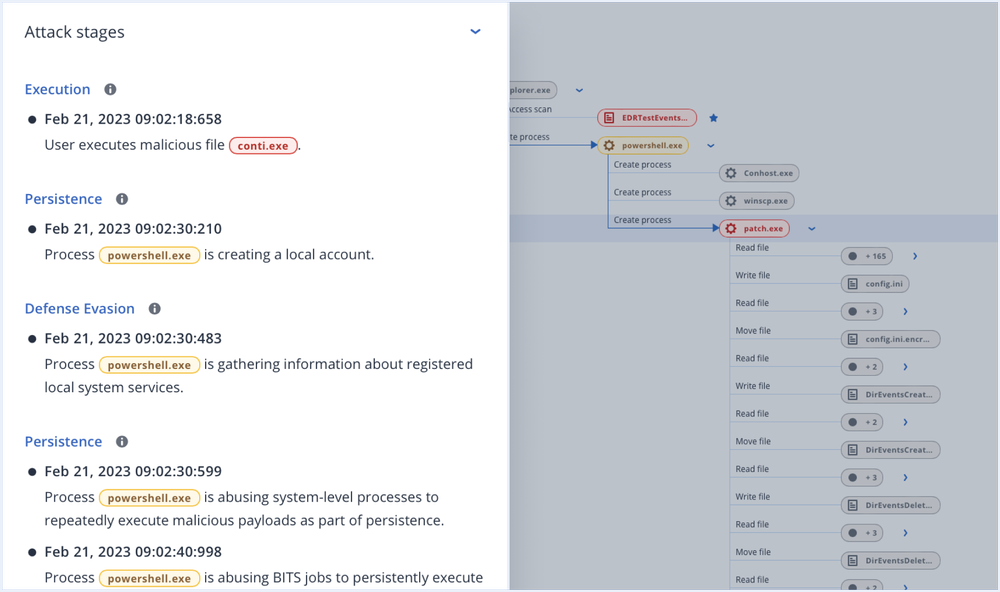
- Easily launch a complete EDR security solution with rapid recovery
- Integrated backup and recovery capabilities, providing robust business continuity where point-security solutions fail.
- Single-click remediation and recovery.
- Complete, integrated protection across the NIST Cybersecurity Framework — Govern, Identify, Protect, Detect, Respond and Recover — all from a single solution.
- Protect against modern threats and comply with cyber insurance requirements
- Get a prioritized view over incidents and unlock minutes-not-hours analysis at scale with AI-based incident summaries and guided attack interpretations.
- Meet multiple cyber insurance requirements with a single platform.
- Protect sensitive data and report on incidents to satisfy compliance.
- Maximize efficiency by minimizing administrative overhead with a single security platform
- Quickly and easily launch new services using a single Acronis agent and console to deploy, manage and scale.
- Scale costs and resources across multiple clients while preserving healthy margins and minimizing OpEx.
- Partner with a vendor focused on your success and enablement.
- GovernRapidly establish cybersecurity and risk management strategies, set roles and policies, and ensure continuous oversight via an integrated platform.
- IdentifyUnderstand your assets and risks with inventory and data classification tools that provide visibility into your attack surfaces.
- ProtectClose security vulnerabilities with forensic insights, a threat intelligence feed and natively integrated tools across the broader Acronis platform, including data protection maps, patch management and policy management.
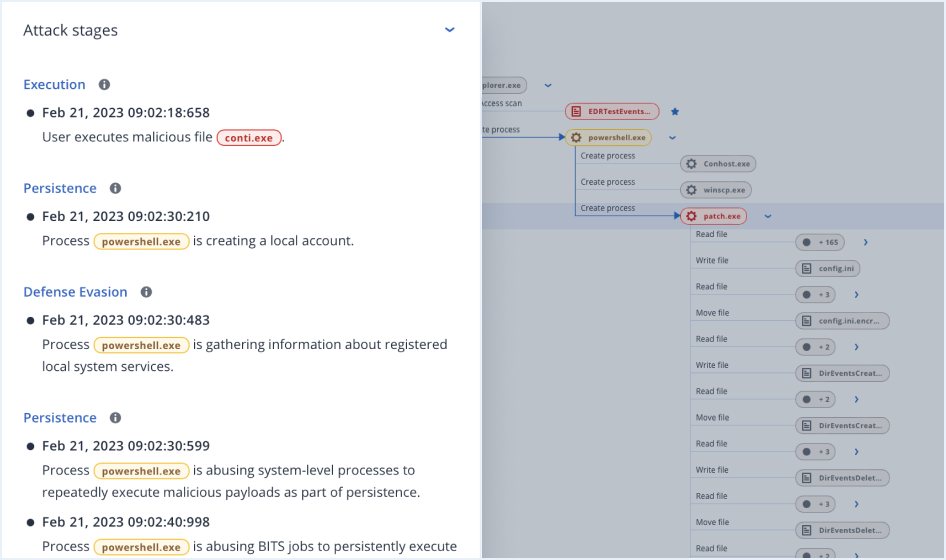
- DetectContinuously monitor for security-related events using automated behavioral- and signature-based engines, URL filtering, an emerging threat intelligence feed, event correlation and MITRE ATT&CK®.
- RespondInvestigate suspicious activities and conduct follow-up audits using a secure, remote connection into workloads or review automatically saved forensic data in backups. Then, remediate via isolation, killing processes, quarantining and performing attack-specific rollbacks.
- RecoverEnsure your clients’ businesses are up and running using our fully integrated, market-leading backup and disaster recovery products and solutions.
Unlock all the benefits of Acronis EDR, including AI-guided attack interpretations and integrated response and recovery, with Acronis XDR and its extended visibility and response beyond the endpoint into most vulnerable attack surfaces.
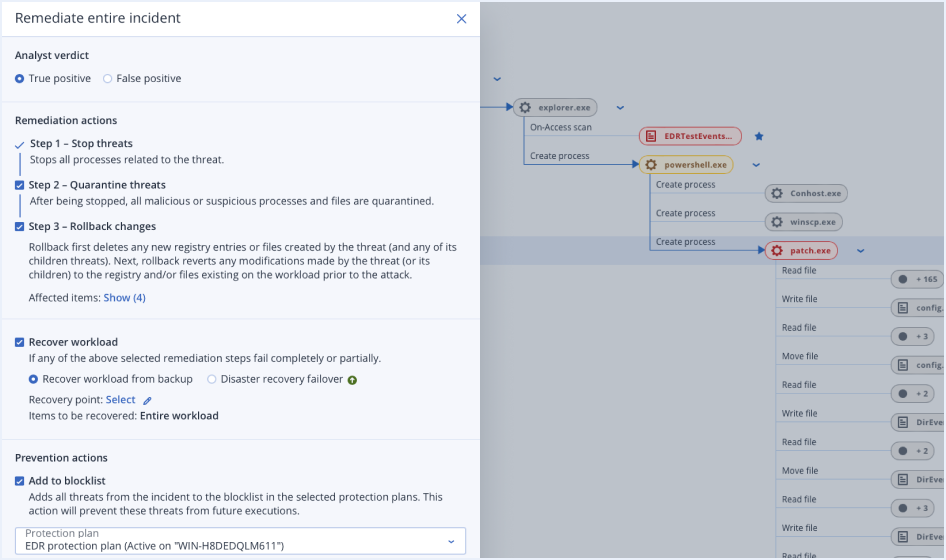
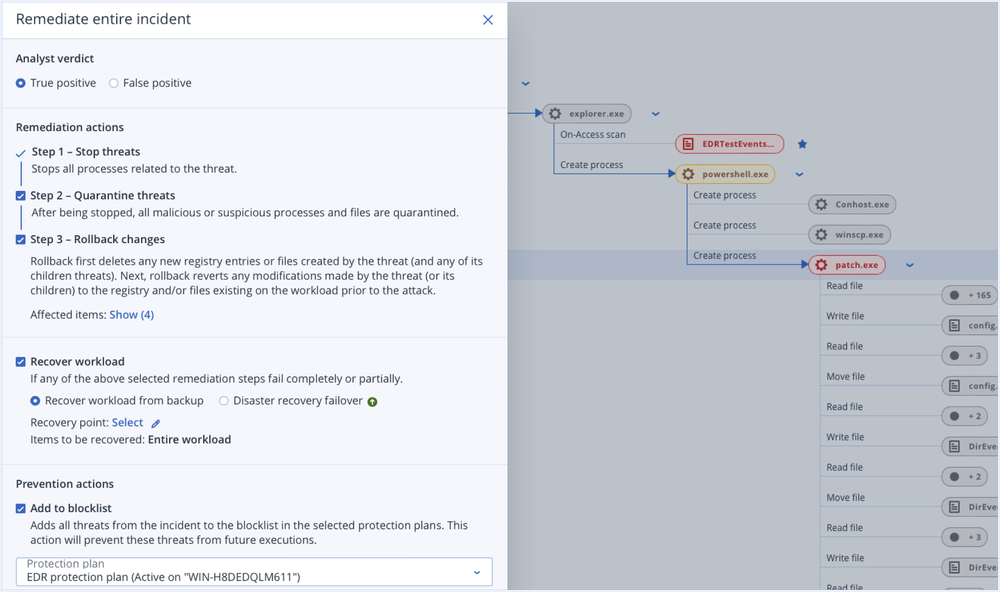
Unmatched business continuity with single-click response
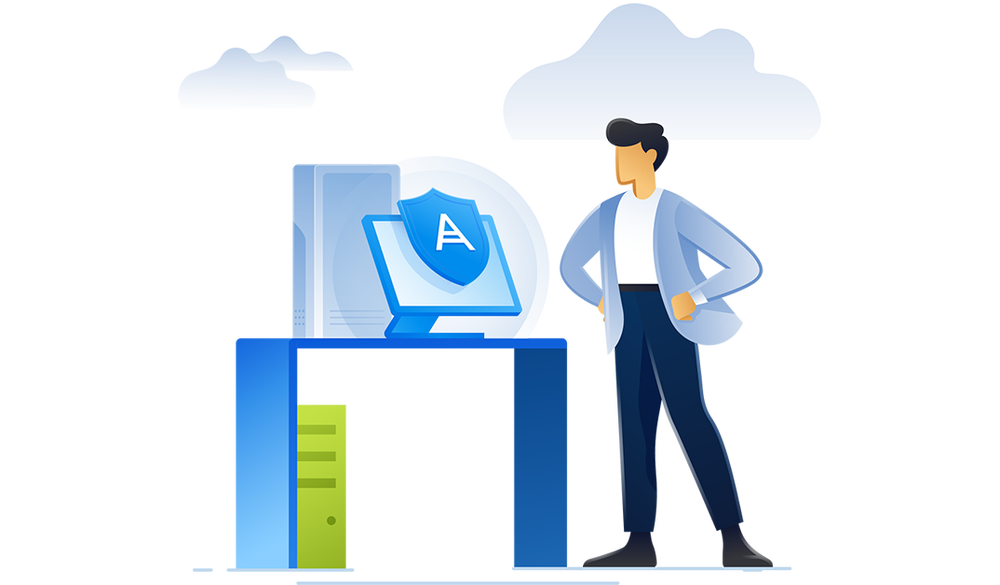
- Remediateby network isolating endpoints, killing malicious processes, quarantining threats and rolling back attack changes.
- Investigate further
using remote connections and forensic backups.
- Prevent future attacksby blocking analyzed threats from execution and closing open vulnerabilities.
- Ensure business continuity with integrated recoveryincluding attack-specific rollback, file- or image-level recovery and disaster recovery.
Acronis MDR is a simplified, fully managed EDR service that is built for MSPs and delivered via a platform that amplifies security effectiveness with minimal resource investment.
Powered by industry-recognized, award-winning endpoint protection











Ensure faster growth with Acronis
All the EDR capabilities you need under one roof
Consolidating tools and centralizing service management is easier and more accessible than ever. Expand your cybersecurity capabilities, offer complete endpoint protection and provide true business resilience for your clients and their data in the face of modern cyberthreats with Acronis EDR.
Acronis EDR
Use Acronis’ cyber protection technologies to detect and respond to advanced threats across endpoints, including leveraging AI-guided analysis and single-click response.Acronis XDR
Expand Acronis’ award-winning endpoint protection technologies with enhanced visibility and response (including integrated recovery) across most vulnerable attack surfaces, including email, identity and Microsoft 365 collaboration applications.
| Behavior-based detection | | | |
| Anti-ransomware protection with automatic rollback | | | |
| Vulnerability assessments | | | |
| Device control | | | |
| File- and system-level backup | | | |
| Inventory collection (with Management) | | | |
| Patch management (with Management) | | | |
| #CyberFit Score (security posture evaluation) | | | |
| Remote connection (with Management) | | | |
| Remediation including full reimaging | | | |
| Business continuity (with Disaster Recovery) | | | |
| URL filtering | | | |
| Exploit prevention | | | |
| Real-time threat intelligence feed | | | |
| Automated, tunable allowlisting based on profiling | | | |
| Forensic data collection | | | |
| Event monitoring | | | |
| Automated event correlation | | | |
| Prioritization of suspicious activities | | | |
| AI-generated incident summaries | | | |
| Automated MITRE ATT&CK® attack chain visualization and interpretation | | | |
| Single-click response to incidents | | | |
| Full threat containment including endpoint quarantine and isolation | | | |
| Intelligent search for IoCs including emerging threats | | | |
| Attack-specific rollback | | | |
| Integration with Email Security (email telemetry) | | | |
| Integration with Entra ID (identity telemetry) | | | |
| Integration with Collaboration App Security (Microsoft 365 apps telemetry) | | | |
| Delete malicious email attachment or URLs | | | |
| Search for malicious attachments across mailboxes | | | |
| Block malicious email address | | | |
| Terminate all user sessions | | | |
| Force user account password reset on next login | | | |
| Suspend user account | | | |
| MDR service | | | |
Upcoming online events
Expand your services with advanced protection packs
Add other powerful components to strengthen your services even further with advanced protection packs and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
- Security + XDRInstead of counting on a costly and complex stack of point solutions, Acronis XDR introduces natively integrated, highly efficient protection built for MSPs:
- Natively integrated cybersecurity, data protection and endpoint management
- Highly efficient security designed to protect the most vulnerable attack surfaces with AI-guided incident analysis and single-click response
- Built for MSPs, including a single agent and console for all services
- Security + EDRInstead of counting on a costly & complex stack of point solutions, Acronis enables MSPs via integration of EDR, endpoint management, and backup & recovery to:
- Easily launch a complete security solution, including rapid recovery
- Protect against modern threats and readily comply with cyber insurance requirements
- Maximize efficiency through a single security platform
- ManagementStreamline and automate your routine tasks via scripting and promptly close security gaps in clients’ infrastructure through patch management. Gain visibility into your clients’ software assets and data protection to ease daily tracking and planning tasks, and improve clients’ uptime by monitoring disk drives health.
- Cyber scripting
- Automated patch management
- Disk drive health monitor
- AutomationStreamline MSP business with a single integrated platform that automates workflows, improves customer interactions, and provides real-time business insights. Enable data-driven decisions and smarter resource utilization, resulting in improved manageability and value-based client relationships.
- High-performance automation
- Precise forecasting
- Next-level profitability
- BackupDefend clients’ data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You can also gain visibility into data-protection statuses across your clients’ infrastructure.
- Continuous data protection
- Data protection map
- Off-host data processing
- Disaster RecoveryGet clients back to business in mere minutes when disaster strikes by spinning up their systems in the Acronis Cloud and restoring them anywhere, ensuring immediate data availability. Make disaster recovery painless and increase efficiency with orchestration, runbooks, and automatic failover.
- Disaster recovery orchestration
- Production failover
- Site-to-site VPN
- Email SecurityBlock any email threat, including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero days in seconds before it reaches end users. Leverage Perception Point’s next-generation technology for lightning-fast detection and easy deployment, configuration, and management.
- Anti-phishing and anti-spoofing engines
- Anti-evasion and account takeover protection
- Next-generation dynamic detection against zero-days
- Data Loss Prevention (DLP)Prevent leakage of sensitive data from endpoints via more than 70 local and network channels and strengthen compliance with minimal effort and speed to value.
- Content-aware data loss prevention
- Automatic client-specific DLP policy creation and extension
- Pre-build data classifiers for common regulatory frameworks
- File Sync and ShareGet a full control over data location, management and privacy with a file sync and share service, including a transaction ledger to enable notarization and eSignature capabilities, across all platforms.
- File notarization
- Embedded eSignatures
- Independent file verification
Acronis Cyber Protect Cloud with Security + EDR
Simplify endpoint security with Acronis Endpoint Detection and Response solution – designed for service providers
Learn More, Earn More with Acronis Academy
Whether you and your team are seeking professional certifications or starting an MSP business, we're here to support you at every stage.

Start learning for Free
New! MSP Academy offers budding and seasoned MSP professionals vendor-neutral training covering the A-Z of managing a successful MSP business.
Train on-demand
Access our most popular sales and technical training courses designed for existing MSPs looking to enhance their cybersecurity skills and knowledge.
Login to Partner Portal
Available exclusively to Acronis Partners. Access our complete Acronis Academy training catalogue and earn your required certifications.
Looking for help?
Frequently Asked Questions
What is Endpoint Detection and Response (EDR)?
EDR (Endpoint Detection and Response) is an active, endpoint security solution that does real-time continuous monitoring correlating different events that happen on an endpoint level to detect malicious activity, compromised processes and suspicious behavior on end-user devices. The purpose is to identify in-progress attacks, potential security incidents, compromises or breaches – and then acting as a response system, providing capabilities to remediate it.
The primary EDR capabilities as defines by Gartner are:- Detect security incidents
- Contain the incident at the endpoint
- Investigate security incidents
- Provide remediation guidance
Who needs endpoint detection and response?
The endpoint protection strategy of any company that is a potential target of cyber threats and/or that stores valuable endpoint data should include advanced endpoint threat detection capabilities and response tools.
SMB and mid-market organizations are under increased risks of advanced cyber threats due to limited internal capabilities and budget constraints, affecting their access to advanced endpoint security solutions, historically targeted at emprises due to costs and complexity.
Moreover, for businesses of all sizes operating in industries with high regulatory requirements and increased cyber risks such as Finance, Healthcare, Legal, Online Retail, Public Sector, EDR is a must for the organization’s cybersecurity strategy to enable compliance and ensure sensitive endpoint data is out of reach of cyber threats.
With Security + EDR you can ensure that organizations of varying size and complexity are protected with high-value services, scalable across multiple clients.How Security + EDR lowers your OpEX compared to other EDR solutions?
Existing, best-of-breed EDR tools and solutions are oriented at enterprises due to costs and complexity and require large security teams to operate. Moreover, security analysts need to manually perform threat hunting activities by scanning hundreds lines of logs with hours of investigating suspicious activities. But even then, a cross-NIST protection, ensuring business continuity, requires additional solutions and software agents to achieve, increasing the complexity and solution sprawl even further.
Security + EDR performs continuous data collection based on security related events, similar as other EDR tools, but then the solution streamlines your analysis capabilities by raising alerts on any potential incidents and aggregating data in guided attack interpretations mapped to MITRE ATT&CK®. This helps security analysts to rapidly investigate suspicious activities across multiple clients, cutting investigation times from hours to minutes to achieve better scalability.
Moreover, Security + EDR is an integrated endpoint security solution in Acronis Cyber Protect Cloud, unlocking unique benefits for administrators such as a single-click response across the NIST, including recovery. This removes solution sprawl and enables you to deliver comprehensive endpoint protection via a single Acronis agent and console.What are some types of threats that EDR protects against?
There’re multiple types of advanced cyber threats, capable of bypassing other endpoint protection layers like existing antivirus software, some of the most common ones include:
- Zero-day malware and ransomware – Malware and/or ransomware that infiltrates the system through a zero-day vulnerability (a vulnerability that is exploitable, but the software vendor has not released a patch for it yet – the vulnerability can be known or unknown). Can bypass some behavior-based detections.
- Advanced persistent threats (APTs) - Attacks that use continuous, sophisticated and highly evasive hacking techniques to gain unauthorized access to system and stay undetected for a prolonged period of time, with potentially destructive consequences. They usually consist of a few phases, including system infiltration, escalation and lateral movement within the system, and exfiltration of sensitive data. Advanced persistent threats commonly depend on “living off the land” techniques that refer to attacker-behavior that uses tools that already exist in the targeted environment – making it harder to detect, on considerably cheaper to carry out.
- Fileless attacks - Fileless malware is a type of malicious software that uses legitimate programs to infect a computer. It does not rely on files and leaves no footprint, making it challenging to detect attacks and remediate them.
- Hacking - Hacking is the act of identifying and then exploiting vulnerabilities in a computer system or network, usually to gain unauthorized access to personal or organizational data. Depending on the used techniques, hacking can be hard to detect, as it might leverage stolen credentials or other techniques that make it look like a perfectly normal process until exfiltration happens and it’s already too late to respond.
Detecting and responding to these and other advanced threats requires more Security controls like EDR.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.