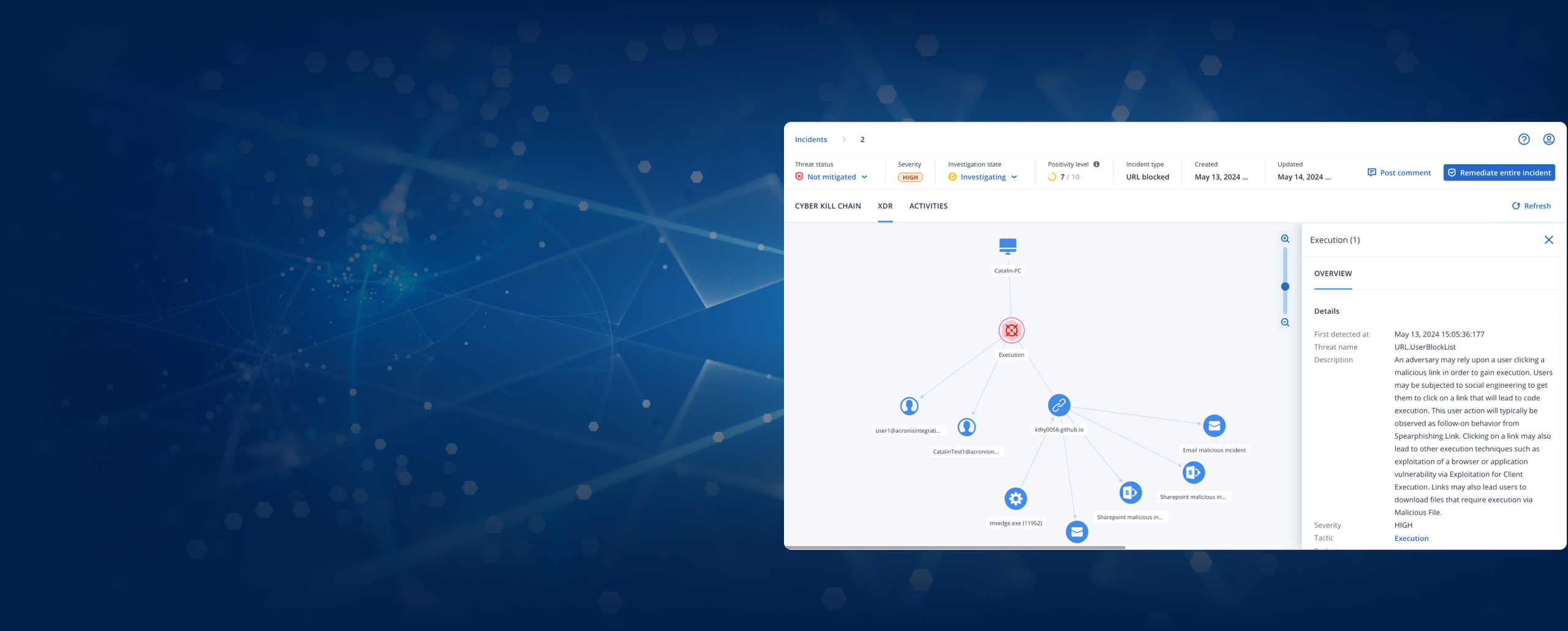
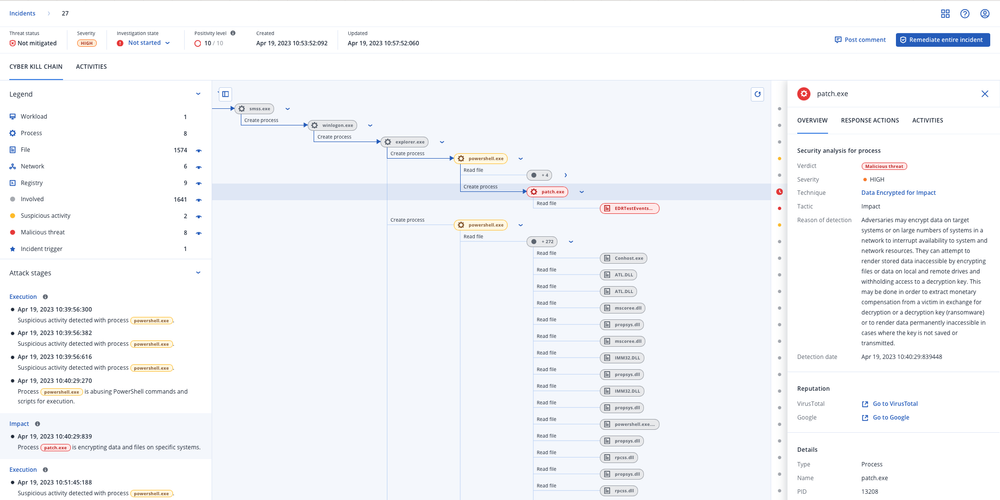
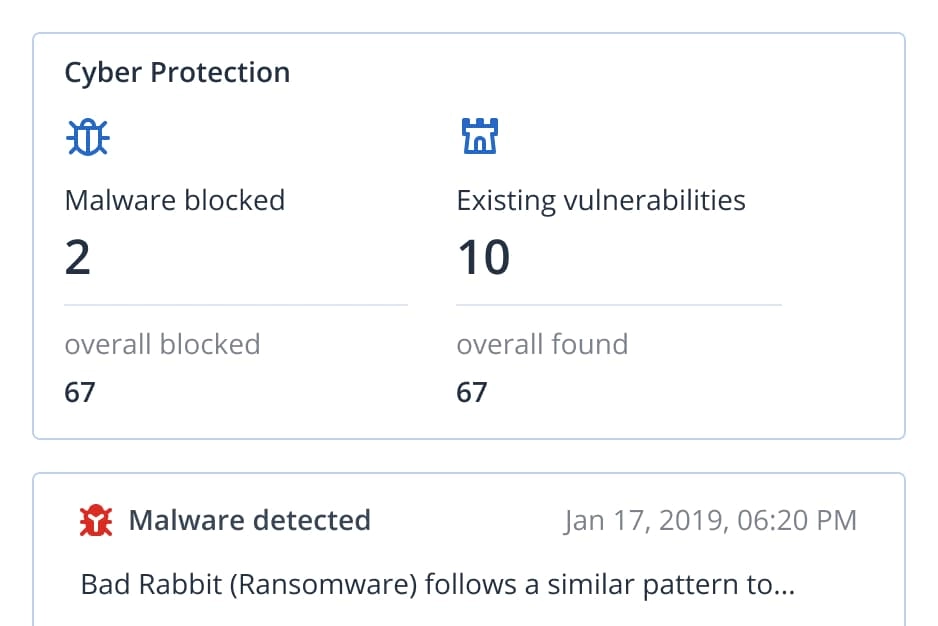
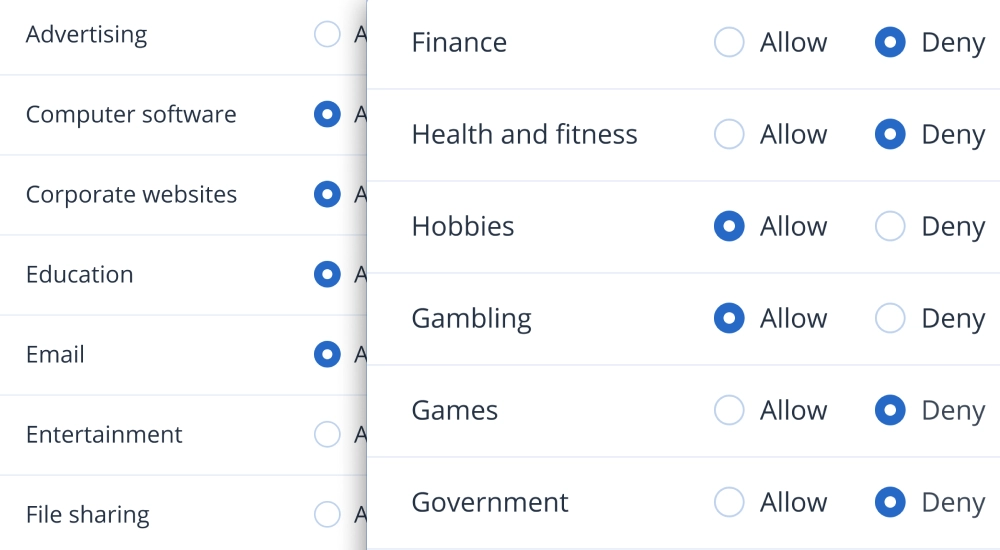
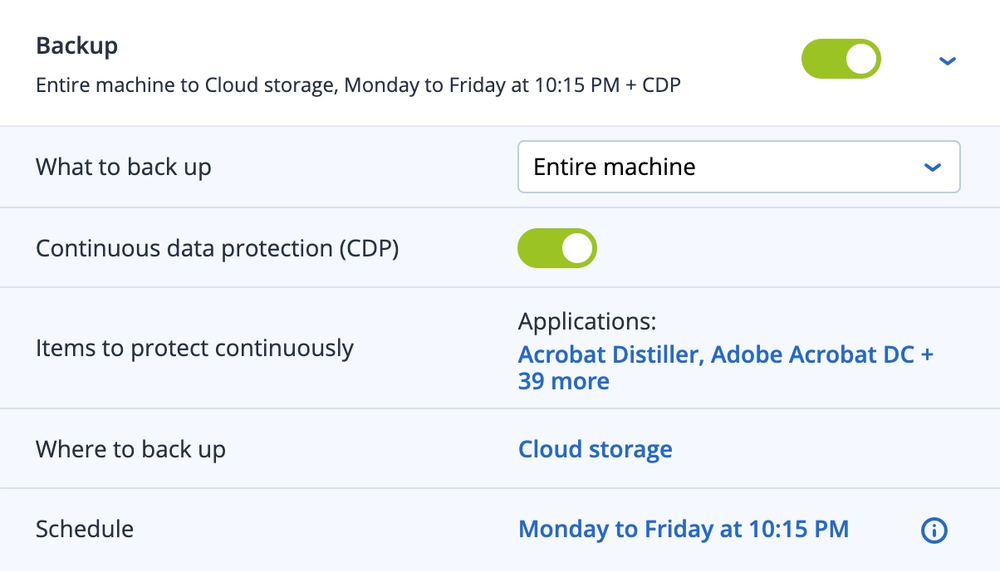
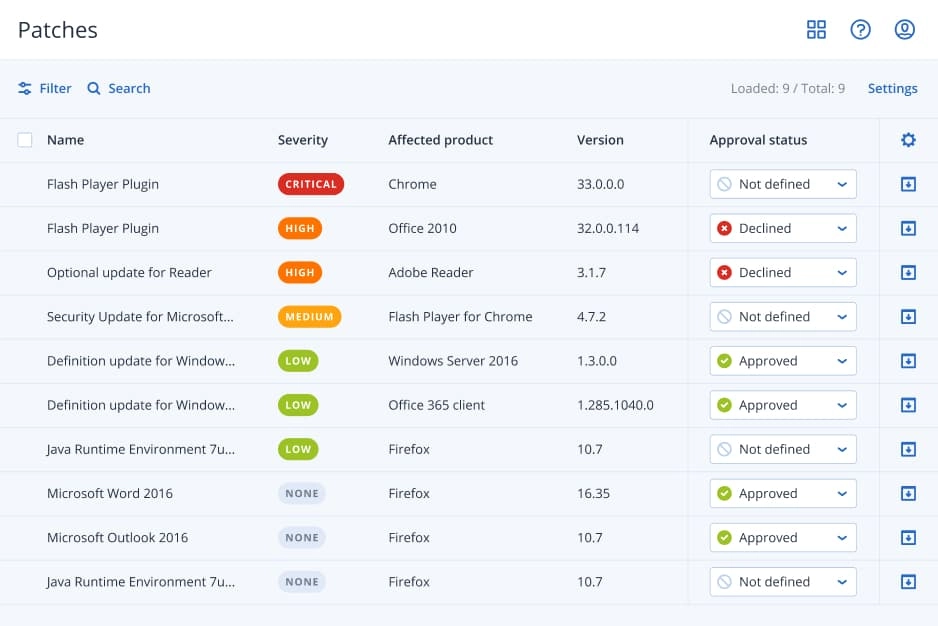
You are on United States + Canada website. Select another region to view location-specific content
United States
English
Select another region