AV-TEST, the renowned independent evaluator of antivirus and security solutions, has recognized Acronis Cyber Protect for its flawless results in protecting against the latest attack techniques.
The organization’s latest Advanced Threat Protection test took place in March–April, with results published in July, and focused on how cybersecurity products for Windows 11 detect and fend off the new attack technique "Inline Execute Assembly” from data stealers and ransomware.
As you may know from our recent Mid-Year Cyberthreats Report, data stealers and ransomware are the most prominent cyberthreats in today’s landscape. Both operate similarly in the initial phases of attacks. Once present on the system, data stealers gather information and transmit it to the attacker. While ransomware often exfiltrates important files as well, it also encrypts them on the victim’s system.
Test methodology and Acronis results
In this evaluation, AV-TEST specialists were testing resilience against a particular attack technique: the "Inline Execute Assembly."
Here’s how it works: A process is singled out, infected with malware code, then launched. The Anti-malware Scan Interface (AMSI) is circumvented using an AMSI bypass. This is the scan API provided by Microsoft, and is used by antivirus solutions. Furthermore, the event tracing integrated in Windows is disabled so that the process routine cannot be traced any further. Once all of that is successful, the malware has free rein. A good security solution can still prevent further action, such as the siphoning off (or encryption) of data, according to AV-TEST.
The lab sent five samples of data stealers and five samples of ransomware via spear-phishing emails to the test systems. The first stage of an attack is when malware arrives on the system, and the second is when it becomes active. Ideally, the threat should be detected and blocked within these two steps, and this is what Acronis Cyber Protect Cloud with the Advanced Security pack demonstrated.
If a security solution fails to block the threat either before, or at the beginning of, execution, data stealers will be able to gather sensitive information and exfiltrate it to a C2 server. Ransomware also collects information, but with the intention of sending out a file list to the C2 server while the data encryption process is being launched.
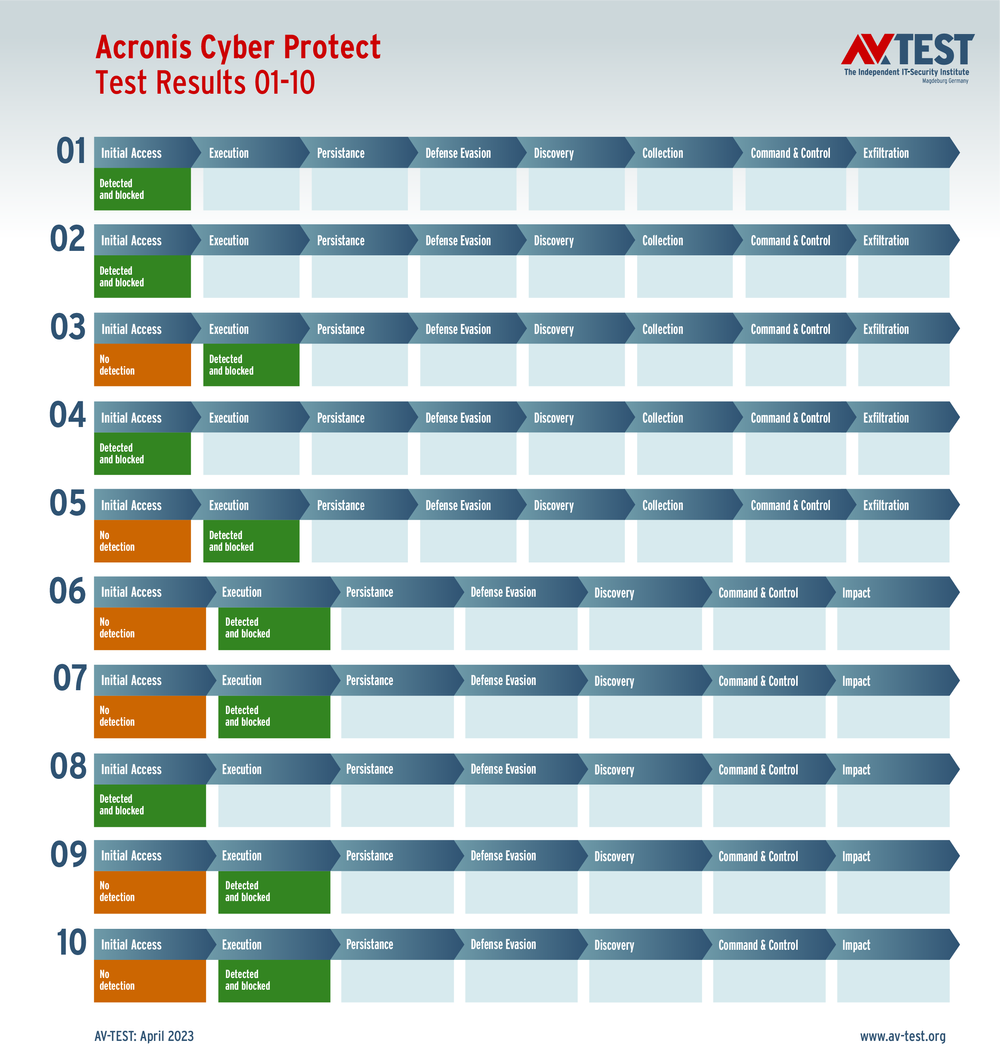
Cases 1–5 show data stealer test attacks and cases 6–10 show ransomware test attacks.
Yet another special feature in this test: the lab awarded points for detecting significant attack steps and taking defensive action. Up to four points were awarded for each tested data stealer, and up to three points for each ransomware variant — thus, the highest possible protection score a solution could earn in this test was 35 points. That’s precisely what Acronis Cyber Protect received: a perfect score of 35 points!
According to AV-TEST, all attack scenarios are documented according to the standard of the MITRE ATT&CK database. The individual sub-techniques are listed in the MITRE “Techniques” database — for example, "T1566.001" is found under "Phishing: Spearphishing Attachment." Each test step is thus defined among experts and can be logically understood. All attack techniques are explained, and the malware’s successfulness is evaluated.
Despite a perfect and error-free score, Acronis Cyber Protect did not receive an official certificate following these results. This is simply because AV-TEST only certifies products that achieve certification in the regular monthly tests, and Acronis is not participating in public tests in this category.
Learn more about Acronis Cyber Protect or start your free trial today.