A new ecosystem of ransomware delivery and profit-making is coming into being. It’s no longer one individual who is solely responsible for manufacturing, distribution and profiting from a ransomware. It’s now an open business for anyone and everyone who is willing to be a part of this illicit money-making scheme.
Written by Ravikant Tiwari
Within a very short span, we have seen an explosion of the number of Ransomware as a Service (RaaS) offerings made on dark web. Data Keeper is the latest addition, joining recently offered RaaS strains like GandCrab and Saturn. If you’re willing to distribute Data Keeper, it’s offered for free by the members of this service. The ransom demanded from victims is currently a minimum of 0.03 BTC.
Data Keeper spread quickly, reportedly being seen in the wild just two days after the service was live in the underground market. Infections from Data Keeper were reported from many different parts of the world, generating plenty of media attention.
Data Keeper’s RaaS Model
The Data Keeper RaaS is available on the dark web and requires one-time registration to become a member of the service. Each member is assigned a globally unique identifier, or GUID, which is used to recognize members for each ransomware infection and to award them accordingly.
Half of the overall profit made by all ransomware infections generated by a particular GUID is awarded to the owner of that GUID.
Member Panel
The Member Panel has options to manage passwords, generate GUID-specific ransomware binaries, customize binary functionalities, specify the payment amounts for victims, and show the current statistics on the total number of infection and total number of payments made.
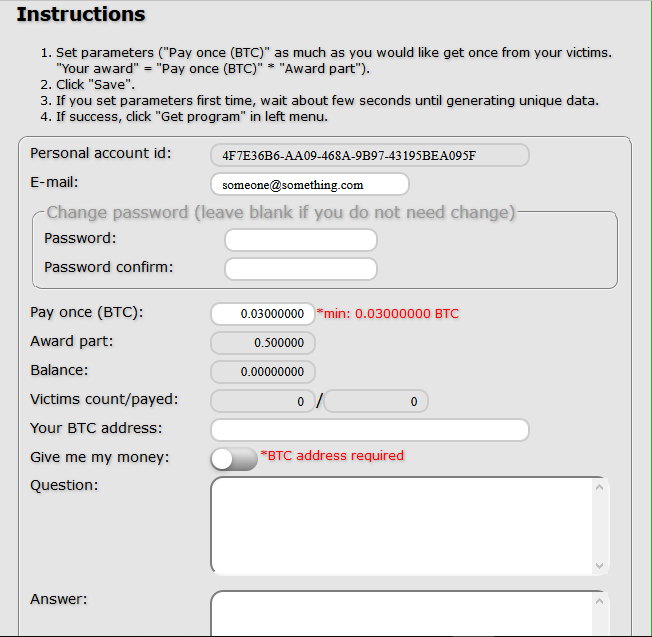
Figure 1: Member's panel - Instructions page
On the Compile page, users can specify the list of extensions that the ransomware will encrypt, enable or disable network share encryption, choose to enable or disable run-as-administrator options, and control the ability to encrypt remote shares.
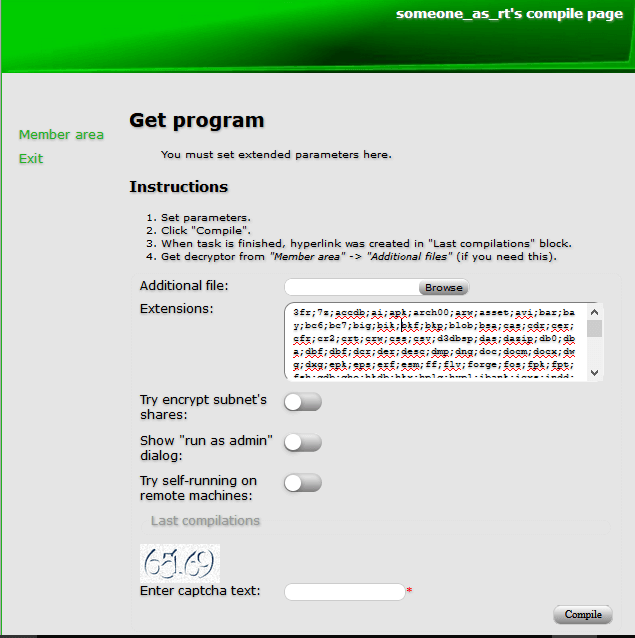
Figure 2: Compile page
Once the user hits the Compile button, a task is created and the process of generating a member-specific ransomware binary begins. As soon as the ransomware-building process finishes, a hyperlink to download the binary is created on the same page. Users can build multiple binaries for distribution, and all builds will be listed with the last compile time as its label.
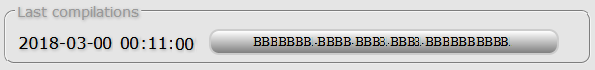
Figure 3: Link to download ransomware encryptor
The ransomware decrypter is also available to download in the Member Area section of this panel.
Figure 4: Ransomware decryptor download page
Technical Analysis
In this article we will take a look at a Data Keeper sample with MD5 0x75DD2CDF1A2D2CAFCD90F34214F5F037, which was found in the wild. The file has following version information and was first submitted to Virustotal on 2018-03-01 13:33:10.
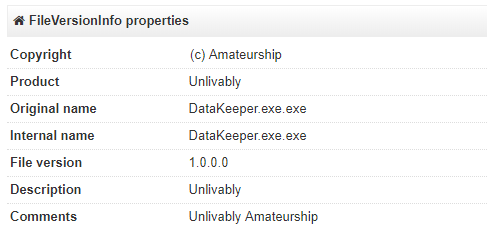
Figure 5: File Version Info
Installation
Data Keeper ransomware is built in dotnet and has multiple layers of executables compressed and stored in the resource section, which has .resx format. Each layer is also obscured using ConfuserEx. The subsequent first two layers are executables and the next two are DLLs.
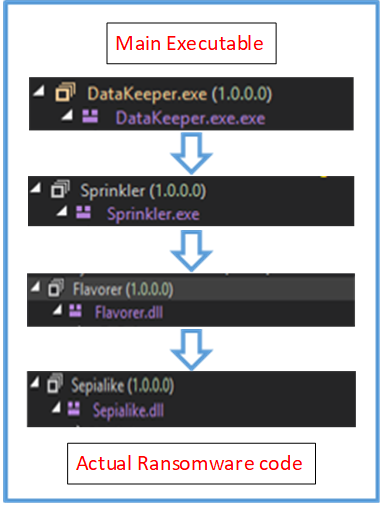
Figure 6: Flow diagram of Data Keeper executables
The main executable decompresses the next layer of the dotnet executable, copies it with a random name and .bin extension to the %LocalAPPDATA%/ directory, and executes it. The main executable then terminates and the newly created binary takes over. The new executable also decompresses and loads a DLL named Flavorer.dll in memory from its resource section. Flavorer.dll similarly loads the actual ransomware DLL named Sepialike.dll which has functionalities for encryption and lateral movement. At no point are these two DLLs are written onto the disk.
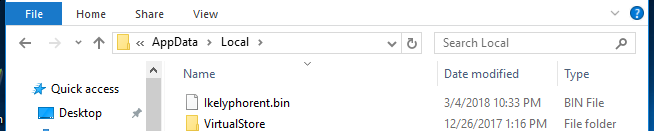
Figure 7: Executable with random name copied in APPDATA/Local
No entry for persistence is found for this ransomware, and there are also no checks implemented to prevent reinfection of the same machine, which means it can infect the same user’s machine multiple times. For every encryption, a new link is added to the ransomware’s “Help” file. If there are multiple infections, the victim needs to pay for each infection separately.
Data Keeper don’t use any named mutex. Instead it scans all of the processes running on the system and if a process with a similar name as of the current ransomware process is found, it terminates itself.
Key Generation
Data Keeper uses an AES symmetric cipher to encrypt user files. For AES encryption, it uses the non-FIPS compliant RijndaelManaged class of dotnet framework instead of the standard AesCryptoServiceProvider class generally preferred by other ransomware authors.
The AES algorithm is used with the following configuration.
The AES key and Initialization Vector (IV) are generated by calling on the GenerateKey() and GenerateIV() functions. For each key, a unique Key ID is also generated using Guid.NewGuid() method.
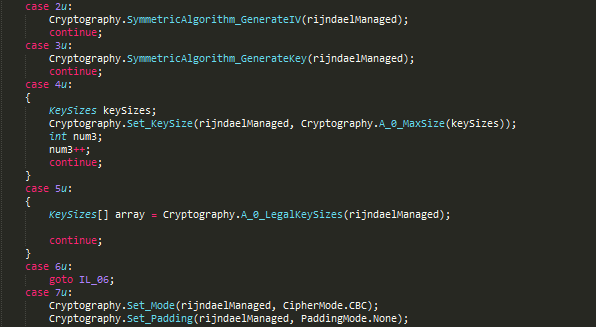
Figure 8: Key Generation
Next it decompresses and decodes the hardcoded master public key stored in the resource .resx file, and imports it to encrypt the AES key, IV and other encryption related contents mentioned below.
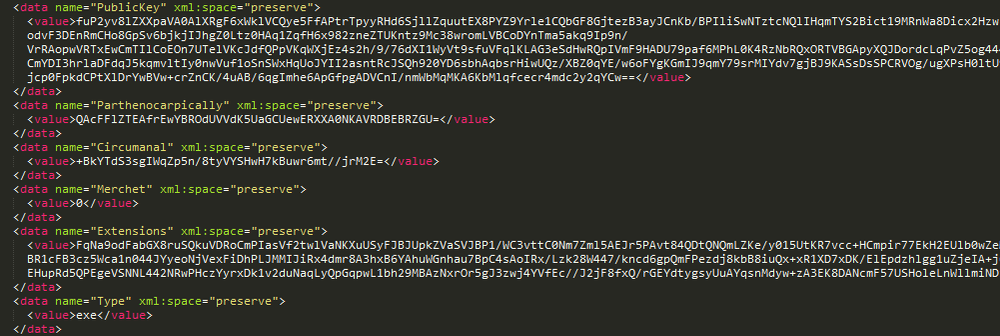
Figure 9: Master RSA public key and extensions list in resource.
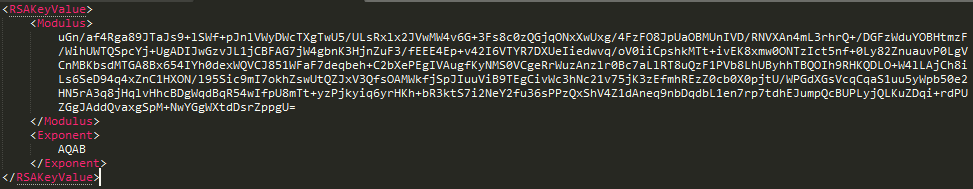
Figure 10: Decompressed and decoded Master RSA public key
The encrypted key, IV, and length of encryption is then converted to base64 before writing it to the user data URL in the ransom note, along with key ID and token (the identifier of the ransomware distributor). This URL redirects to a personalized decrypter service page where victims can make payment and receive a decrypter.
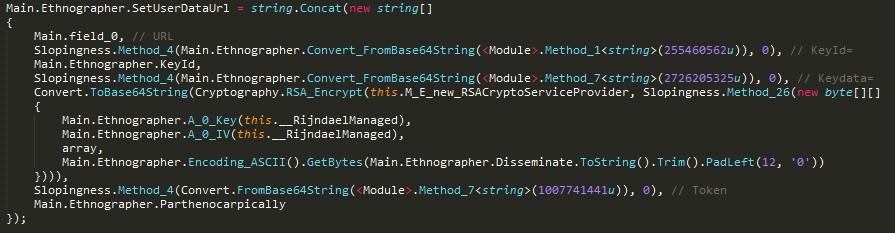
Figure 11: Setting user data URL
The Key Data structure has the following format:
- First 20 bytes is key
- Next 10 bytes of IV
- Followed by four bytes of a constant value from resource and
- 12 bytes of randomly generated length for encryption (encryptDataLength) which is in multiple of 256-bit block size.
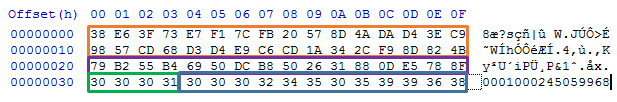
Figure 12: Key Data Structure
The user URL included in the ransom note appears as seen in below image. Different components of the URL are marked with different color.
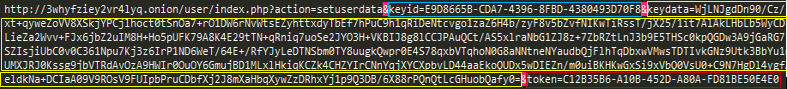
Figure 13: User data URL example
Encryption Process
Data Keeper only encrypts files on fixed drives. However, it can itemize all connected network shares and use PsExec to launch itself and encrypt files on these devices. It maintains a list of names that can be used to launch a dictionary attack to gain access to shared network devices.
It excludes the files inside the “Program files” folder from encryption.
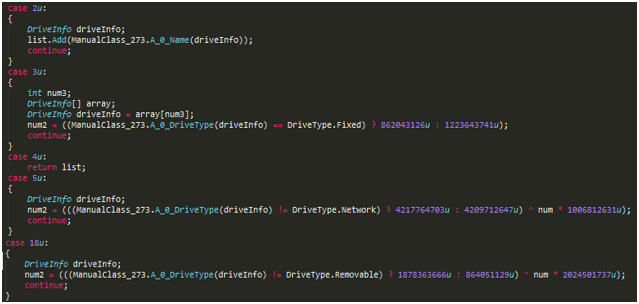
Figure 14: Drive Enumeration
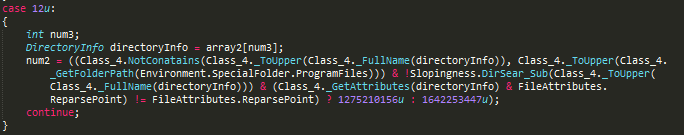
Figure 15: Excludes program files
It begins the file and directory enumeration and encryption process in a multi-threaded mode. The maximum number of threads are decided based on the number of processors on the machine. Before encryption, it reads the last 36 bytes and matches it with regex to find a string like GUID in order to verify whether the file was already encrypted. If the file was previously encrypted, the file will not be encrypted again.
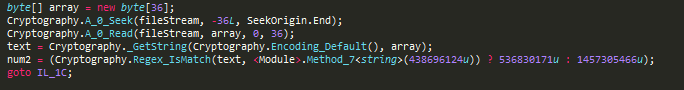
Figure 16: Checking the last 36 byte
To encrypt user files, Data Keeper begins by saving the last write time of the file. It then compares the file size against a value “n” (where “n” is length of encryption), which is randomly decided by ransomware for the current session. It then tries to read “n” number of bytes in memory from the file on disk. If the file size is smaller than “n”, then the file size is divided by the square of the maximum block size possible in RijndaelManaged class (that is 322 bytes), and the resulted number of bytes are only read into the memory from the file for encryption.
A crypto stream is then created using a crypto transform object instantiated by the CreateEncryptor() function and the session’s AES configuration. The memory array is then written to this crypto stream to encrypt the content. The encrypted content is then written back at the “offset 0” of the file, replacing a number of original bytes that is equal to the length of the encrypted data. The file is reopened in the append mode and the current key GUID is added to the end. Finally, the newly encrypted file is restored to original last write time, which was there before encryption.
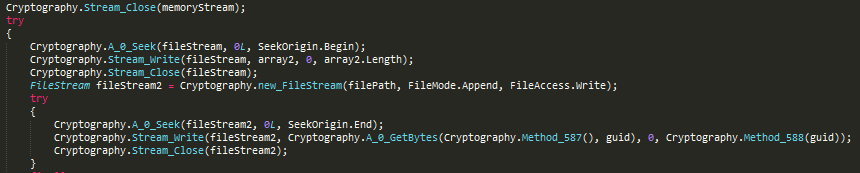
Figure 17: Writing encrypted content and key ID to file

Figure 18: Restore last file write time

Figure 19: Extension names that data keeper sample found in wild encrypts
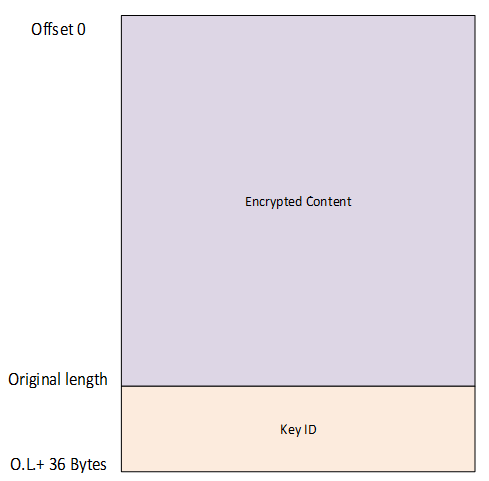
Figure 20: File structure after encryption
Network Enumeration and Encryption
Data Keeper uses the same multi-threaded routine to enumerate and encrypt files on network share. To enumerate network shares, it implements its own NetShares class which uses the NetShareEnum API from Netapi32.dll of the Windows operating system.
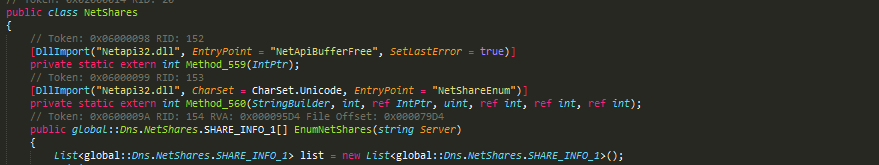
Figure 21: NetShare class implementation
The code snippet below shows Data Keeper calling method_48() in thread functions.
Figure 22: Calling method_48() in multi-threading
The called method_48 implements the NetShares class to enumerate all network resources and creates a list of files that will be then passed to the encryption routine.
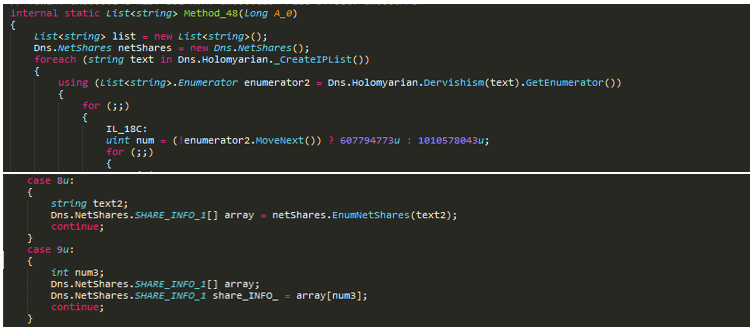
Figure 23: Snippet of method_48()
Ransom Notes
Data Keeper creates a ransom note as an HTML file with name “!!! ##### === ReadMe === ##### !!!.htm” in the parent directory of the encrypted files directory. The ransom note contains instruction on how to download a TOR browser and links to the site for downloading the decrypter.
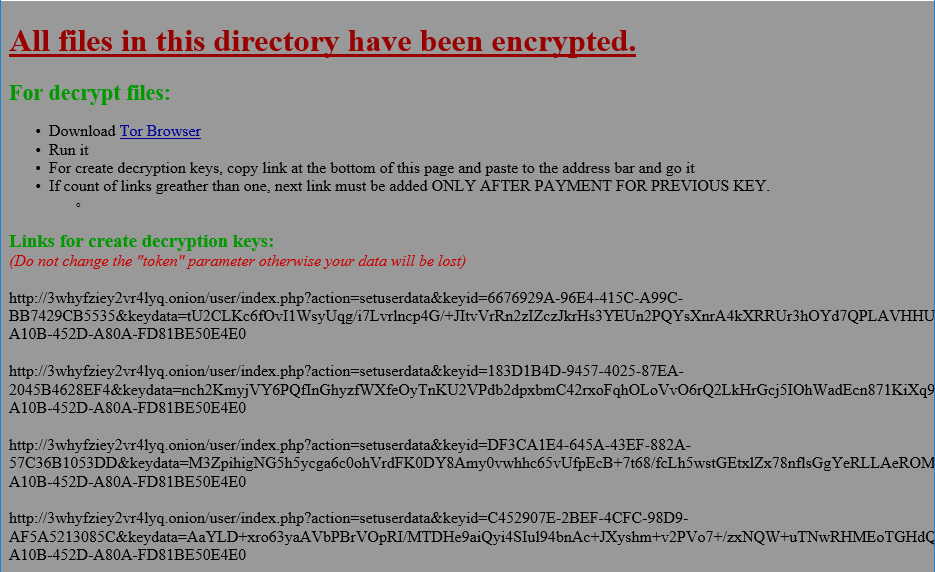
Figure 24: Ransom Note
Decryption
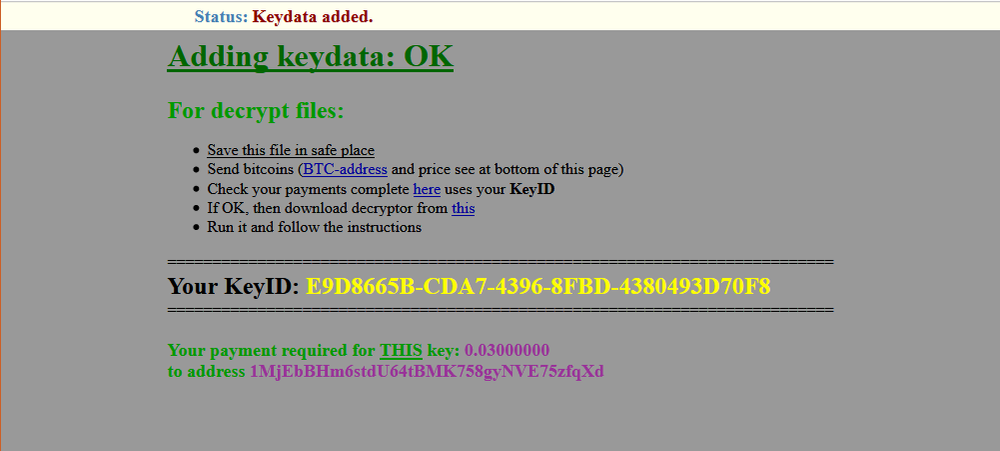
No free decryption tool is available for this ransomware yet. To decrypt their files, users must visit the link in the ransom note, which will redirect them to Data Keeper’s decrypter service page. It instructs victim to pay 0.03 bitcoin to the attacker’s wallet address. Once the payment is successfully validated, the decrypter can be downloaded from a link on the same page.
Conclusion
With rise of the Ransomware as a Service model, it has become very easy for any attacker to acquire a binary for free, spread it, and get paid for their successful infections. The promise of “free money” will lure many people to become attackers, which is why a steep rise in ransomware activity is expected.
To protect against complicated ransomware attacks like Data Keeper, users need next gen cybersecurity solutions based on machine learning and behavioral heuristic. Products with Acronis Active Protection enabled, like Acronis True Image 2020, include these next gen technologies and are able to protect users against sophisticated ransomware attacks like Data Keeper.
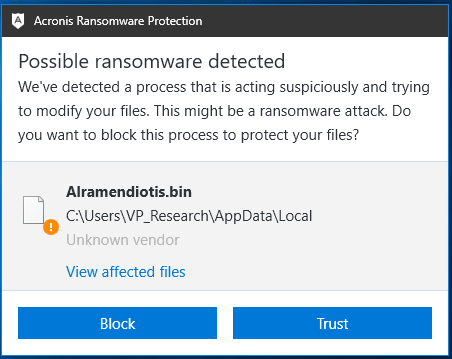
Figure 25: Acronis detects Data Keeper ransomware
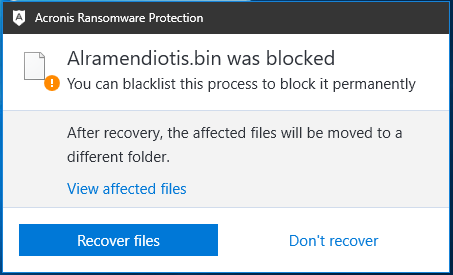
Figure 26: Acronis blocks Data Keeper
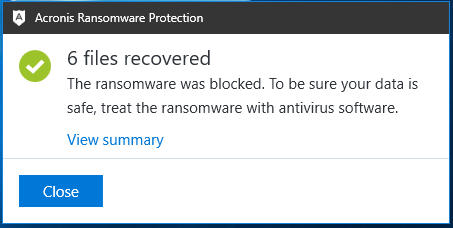
Figure 27: Acronis recovers affected files by Data Keeper
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



