
Sensitive data is the primary target of attacks, showing the need for more effective IT controls that protect data. While data protection is primarily considered a BDR (backup and disaster recovery) category, there are other essential technologies, such as data leak prevention (DLP) and encryption, that secure sensitive information against a wider variety of threats, such as data leakage. This is the reason why service providers (SPs) need to understand what data leakage is, what causes it and how to mitigate the risk — all of which are discussed in this article.
What is a data leak?
A data leak is a breach of security in which confidential, sensitive or protected data is accidentally or deliberately released to an untrusted environment or unauthorized users outside or inside the organization. A data leak can happen via any channel, including local channels — removable storage, printers, redirected mapped drives, redirected clipboard — and network communications — email, instant messages, webmail services, file sharing services, social networks, web access and file transfer protocols, etc.
What types of sensitive data usually get leaked?
The four most common types of sensitive data that can leak from an organization and lead to severe financial and reputational risks are:
- Personally identifiable information (PII), including employee or customer names, email, postal address, SSN, passport number, driver’s license, social media account, etc., as per GDPR
- Patient’s protected health information (PHI) as per HIPAA
- Customers’ payment card data with contractors as per PCI-DSS
- Sensitive business documents with “confidential” or other types of sensitive data, including trade secrets, intellectual property (IP), etc.
What is the difference between data leak prevention and data loss prevention?
While “data loss” refers to the data residing in IT systems that are destroyed due to neglect, attacks or disasters, “data leakage” is the transfer of data to unauthorized internal users or external parties. However, data loss prevention and data leak prevention terms are used interchangeably in the DLP industry and refer to the set of controls responsible for detecting, blocking, and auditing data leakage. The main set of technologies that address data loss are backup and disaster recovery (BDR) solutions, while data leaks are addressed by DLP.
What causes data leakage?
Data leaks happen when the organization does not control who has access to its valuable data and what they are allowed to do with it. Data breaches may be caused by internal risks and external activities.
Internal risks. Insider risks can happen for three reasons:
- Unintentional or negligent data exposure by an employee
- System glitches and IT misconfigurations
- Threats caused be a malicious insider
According to Cybersecurity Insiders, 90% of organizations feel vulnerable to insider threats — and with good reason. The major internal reason for data leaks is human nature. Employees, clients, contractors, partners — all legitimate users of the corporate IT system — are humans whose accidental mistakes, negligence, curiosity or misconduct may lead to data leaks. Some users also fall victim to phishing attacks. Others may purposely steal corporate information.
External attacks. In this case, the primary target is sensitive data. In fact, the objective of 80% of data breaches is to exfiltrate sensitive data for financial purposes via malware infiltration through software vulnerabilities, hacking and social engineering (e.g., phishing).
So what happens when data is leaked?
When sensitive data gets leaked, your business and that of your clients can suffer severe financial, reputation and legal risks, including:
- Regulatory fines due to leakage of protected data subject to regulations such as GDPR, CCPA, HIPPA and PCI-DSS
- Embarrassing headlines that can lead to loss of customers, partners and revenue
- Litigation liabilities resulting from your clients’ data leakage or that of your own business
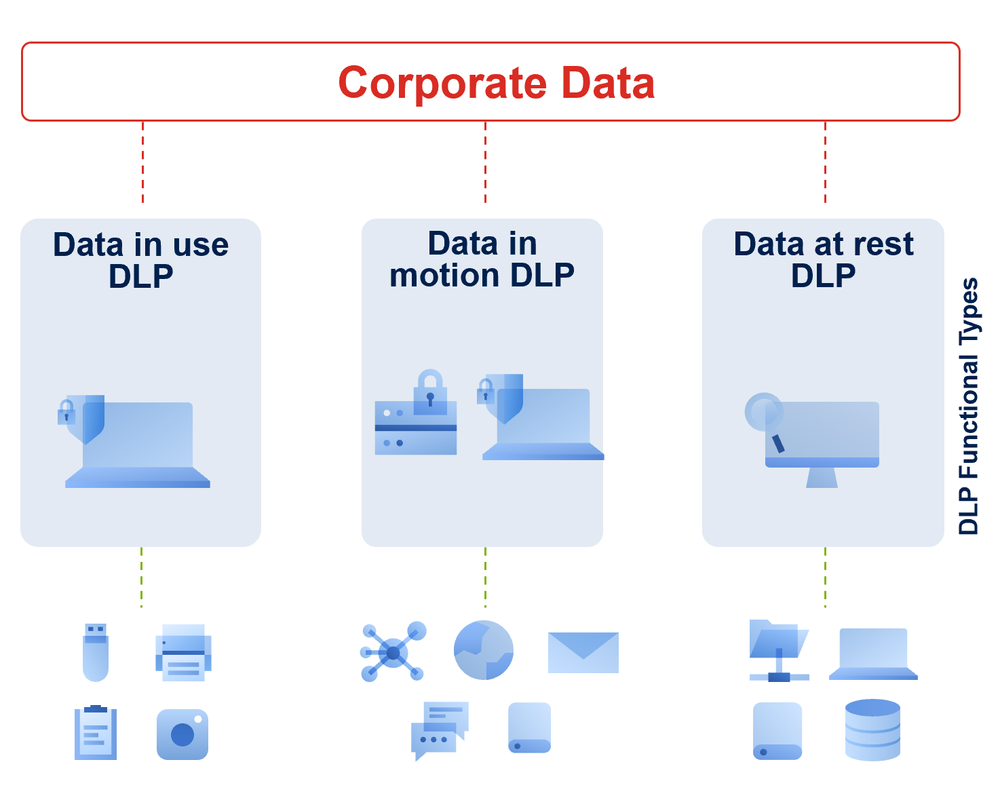
What are the functional types of data loss prevention solutions?
Data Loss Prevention (DLP) solutions can be compared to a “plumbing system” for sensitive business data flows. These solutions detect and prevent unauthorized use (data in use), transmission (data in motion), and storage (data at rest) of sensitive data. More specifically:
Data-at-rest DLP discovers exposed sensitive content in data stored on corporate IT assets (e.g., network file shares, endpoint file systems, databases, document repositories, and cloud-based storage) and remediates data storage policy violations.
Data-in-motion DLP prevents data leakage through network communications (e.g., emails, webmail, IMs, social media, cloud-based file sharing, as well as HTTP(S), FTP(S), and SMB protocols).
Data-in-use DLP prevents data leakage through local channels, peripheral devices, and applications on protected endpoint computers (e.g., removable/redirected storage, Clipboard, printing, screenshot captures)
The DLP solutions do this by applying a combination of contextual controls (based on an operation's context — e.g., sender, recipient, channel used) and content analysis methods to enforce business-acceptable data use and handling policies across the organization that prevent exfiltration of data to unauthorized internal and external recipients.
Here are some data leak statistics
Companies of any size can suffer from data leakage. The most well-known and damaging example of an insider data leak was and still remains WikiLeaks — the one committed by Chelsey/Bradley Manning. She (then he) copied classified and top-secret data to a CD-ROM and published it to WikiLeaks.
In 2021, NASA’s auditors found that users were “sending unencrypted emails containing sensitive but unclassified (SBU) data, personally identifiable information, or International Traffic in Arms Regulations (ITAR) data — any of which could expose the Agency to a risk that can affect national security, incur a loss of intellectual property, or compromise sensitive employee and contractor data."
At the end of 2019, a researcher from Comparitech discovered that 250 million Microsoft customer records were exposed on the open web, including email addresses, IP addresses and locations. This data leak occurred because databases were not properly secured.
In 2020, Tesla experienced an intentional data leak when a software engineer transferred thousands of files with trade secrets to a personal Dropbox account.
What are some tips to protect your clients’ business from data leakage?
Every MSP should encourage their clients to follow these four tips to help mitigate the risk of data leakage:
1. Manage the security levels and risks associated with third parties, including vendors, contractors, consultants. Third parties can be one of the biggest risks, so be sure to evaluate who has access to sensitive information, whether they need access and how you plan to mitigate the risk. You should also continuously evaluate the security posture of your vendors to ensure their security goals are in alignment with your organization.
2. Manage employee permissions to transfer sensitive data. Not all employees should have the same permissions, so be sure to evaluate permissions by employee, groups, etc. Also be sure to immediately stop logon rights and permissions for any employee who leaves the company — regardless of the circumstances.
3. Classify sensitive data. You cannot protect what you don’t know you have. All data, subject to compliance regulations such as GDPR, HIPAA, PC-DSS as well as company-specific confidential data should be classified.
4. Implement a DLP solution to protect all endpoints. This tip is an absolute “must” as no organization can stop data leakage without the right DLP solution in place. A DLP solution blocks risky data by detecting and preventing unauthorized use, transmission and storage of confidential, protected or sensitive data. Without the right DLP solution or service, an organization will have little success protecting their sensitive data from unauthorized access and exfiltration via external attacks or insider risks such as IT misconfigurations, human errors and malicious threats. Data loss prevention is the only technology that can provide visibility and control over the data at rest, in motion and data in use.
What are the challenges for implementing a DLP service?
Historically, traditional DLP systems were developed for enterprise organizations because these solutions are expensive to purchase and laborious to implement. Unfortunately, service providers (SPs) are left out in the cold as these monster solutions have complex, manual processes for policy creation and follow-up adjustments, resulting in long time-to-value and high costs. These solutions cannot be easily tailored to meet the budget and business requirements for small to medium-size businesses (SMBs), nor do they meet the requirements for SPs who want to deliver a multitenant managed service. In addition, DLP experts are harder to find and more expensive than general IT security experts.
DLP service management is also complex and costly. In fact, 69% of technicians spend more time managing tools than defending against threats, and there is a high cost for service delivery and management. Efficient DLP services require business-specific policies, which are unique to each client and are often changing. This is another challenge for SPs that do not have and cannot acquire such deep knowledge of clients’ business specifics.
With traditional DLP systems, the DLP policy creation and configuration process is prone to human error due to the complexity and granularity of the manual processes. These errors in DLP policy can disrupt business continuity and increase client churn.
Acronis provides you with a data loss prevention solution for your business
Acronis Advanced DLP empowers service providers with unmatched provisioning, configuration, and management simplicity to prevent data leakage from client peripheral devices and network communications. Its unique behavior-based, dataflow-profiling technology automatically creates and continuously maintains business-specific policies, without requiring months to deploy, teams to maintain or a Ph.D. in privacy law to understand by baselining and profiling user sensitive data flows. Here is how it works.
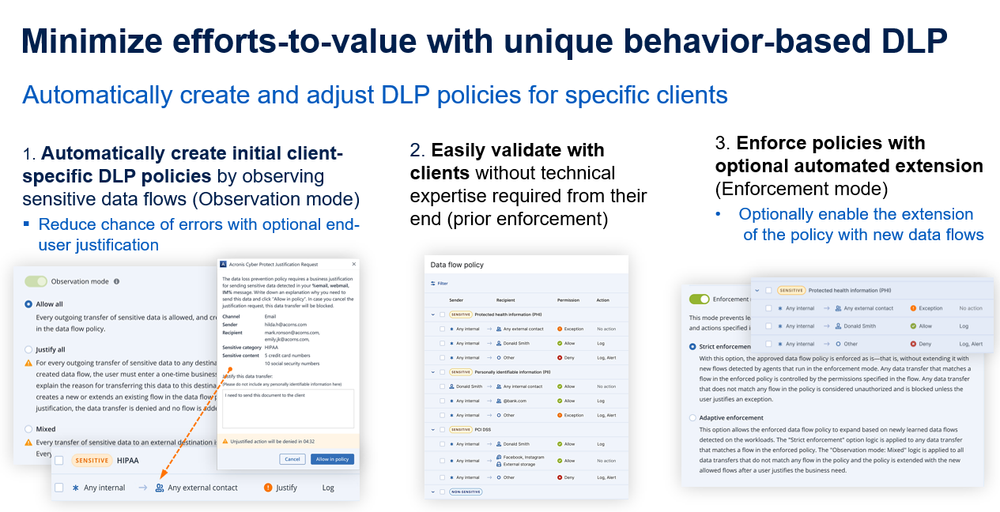
Advanced DLP runs in observation mode and automatically creates the initial DLP policy for each client by monitoring sensitive data flows across their endpoint computers and automatically generating new rules in the DLP policy. This provides business-specific policies without the need to spend a tremendous amount of time learning your client’s business specifics and manually configuring their unique DLP policy — which can cause many mistakes and create uncontrolled data leakage channels or interrupt normal business operations. For increased accuracy, you can enable an optional end user justification for each newly observed sensitive data flow.
Once the baseline policy is created, it’s represented in an easy-to-validate-with-clients graphical form. The validation process requires no technical expertise from the client and is necessary to fine-tune the policy before enforcement.
Once the policy is validated, you can apply it by switching to enforcement mode. In a strict enforcement mode, all rules will be enforced as they are and any new data flows that do not match a rule in the DLP policy will be treated as risky and blocked. Optionally, you can enable automated extension of the enforced policies with new business-related but previously unobserved sensitive data flows by choosing the adaptive enforcement mode. The adaptive enforcement helps minimize the work spent on policy updates and mitigates the risk of potential business disruptions.
Advanced DLP also enables rapid response, post-breach forensic investigations, and policy maintenance with robust auditing and logging capabilities, adjustable alerting based on DLP events, and information-rich widgets.
You will now be able to protect your clients’ data flowing across the 70+ most common channels. This includes local channels — such as removable storage devices and printers — as well as mapped drives and clipboards redirected from remote terminals or BYODs to VDIs or virtual desktop and application sessions on the host computer. You can also protect a wide range of network communications, including the most popular emails and instant messengers, as well as dozens of social networks, webmail and cloud file sharing services.
Advanced DLP also protects your clients’ sensitive data out of the box. Clients can more easily comply with regulations — such as GDPR, HIPAA, PCI DSS — and protect documents marked as confidential with built-in classifiers to detect sensitive data of these categories and block transfers not allowed by the DLP policy. In addition, service providers can also leverage custom classifiers based on file type for more granular control over data flows.
Advanced DLP expands on Acronis Cyber Protect Cloud capabilities by adding powerful components to strengthen your services even further with unique information protection capabilities, integrated with a multitude of other cyber protection technologies.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



