Summary
- Name: HermeticWiper, HermeticRansom
- Discovered in February 2022
- Deployed via Microsoft Active Directory GPO on Ukrainian government machines
- The wiper has four resources, which are compiled and compressed parts of the EaseUS Partition tool for disk management. It abuses legitimate drivers for disk manipulations, obtains necessary privileges and services, control-checks the hard drive file system and corrupts it by swapping bytes
- HermeticRansom encrypts files with AES and RSA algorithms, appending [vote2024forjb@protonmail[.]com].encryptedJB to the file name
- HermeticWiper — PE32 samples, which are very similar and written in Delphi
- HermeticRansom — PE64 sample written in Go
Introduction
On February 23, 2022, a new data wiper and ransomware were deployed on a large number of devices in the Ukraine, as ESET Research reported on Twitter. Just before this, a couple of Ukrainian government sites and services were subjected to DDoS attacks. Cybersecurity specialists discovered that the malware was deployed via Microsoft Active Directory GPO.
In addition to the disk wiper and ransomware, a worm component was deployed to spread malware into the network. They called it HermeticWizard and added that, on the next day, a new IsaacWiper was deployed in Ukraine.
Technical details
Delivery
HermeticWiper was deployed on the victims’ machines by using Microsoft Active Directory GPO. It was installed with another component, called HermeticWizard, which was used to spread HermeticWiper across the local network using SMB protocol and Windows Management Instrumentation. In addition, the ransomware, called Party Ticket or HermeticRansom, was also deployed on government machines.
HermeticWiper
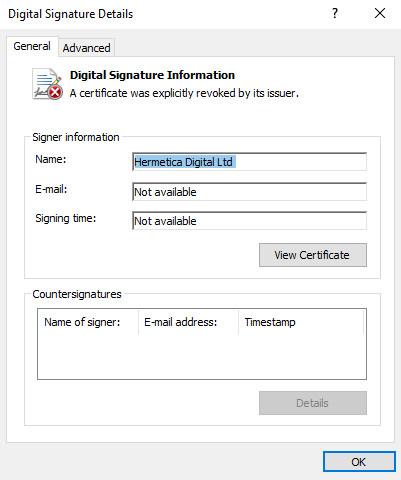
All the samples, which were found in the corrupted systems, appeared to be PE32 files, written in Delphi. All those files were similar: they had a non-valid digital signature ‘Hermetica Digital’ (the reason why it was named as HermeticWiper). The main feature, which distinguished those files, was different hash values.
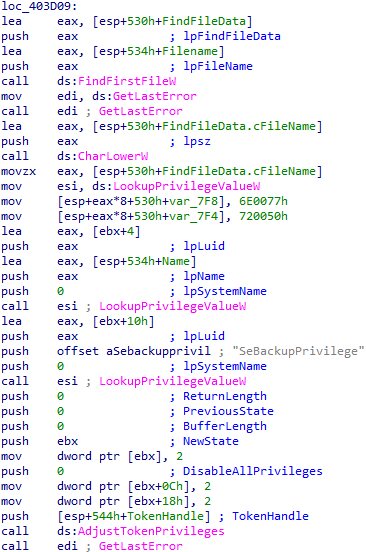
At the start of execution, the wiper tries to obtain the following privileges:
‘SeBackupPrivilege.’This allowed for file
content retrieval even if the security descriptor on the file might not grant
such access;
‘SeLoadDriverPrivilege’ — loads and unloads device
drivers
‘SEShutdownPrivilege’ — required to shut down a local system.
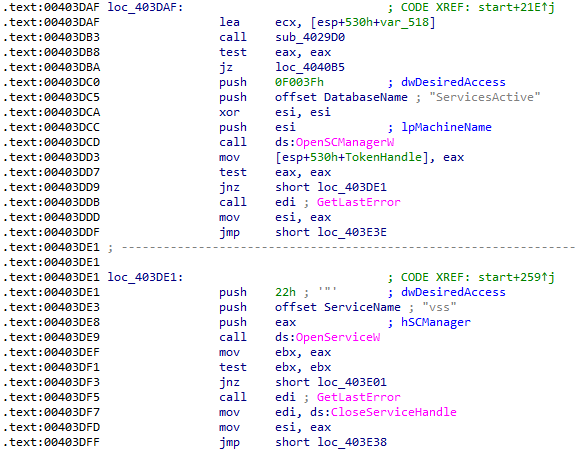
HermeticWiper also tries to obtain the control of the ‘vss’ service, which is responsible for volume shadow copies. Disabling or deleting these shadow copies will make the system recovery through VSS impossible.
If these privileges are obtained successfully, the malware proceeds with the loading of one of its resources.
These resources are considered to be the compiled and compressed drivers, which the wiper abuses for the disk manipulation. These drivers are the essential part of the EaseUS Partition tool for the disk management. The malware samples contain four drivers in the resources:
“DRV_X64” – 64–bit version for
Windows 7+
“DRV_X86” – 32–bit version for
Windows 7+
“DRV_XP_X64” — 64–bit version for Windows XP
“DRV_XP_X86” — 32–bit version for Windows XP
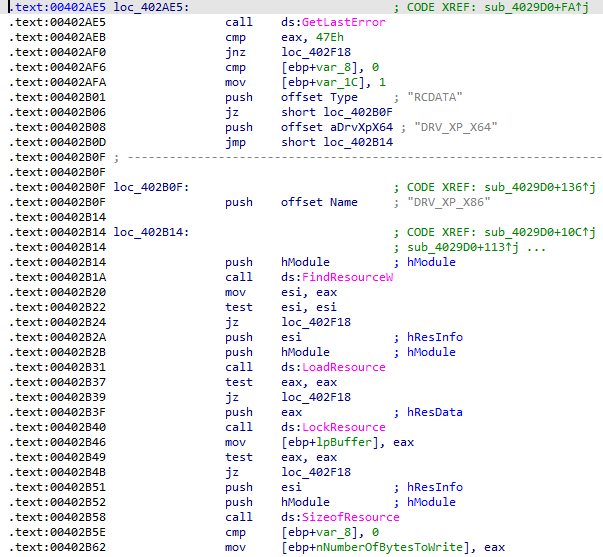
The wiper modifies the registry key “SYSTEM\\CurrentControlSet\\Control\\CrashControl” to disable the dumping process in the event of a crash. The string “\\\\.\\EPMNTDRV\\%u” is an abbreviation from “EaseUS Partition Master NT Driver.”
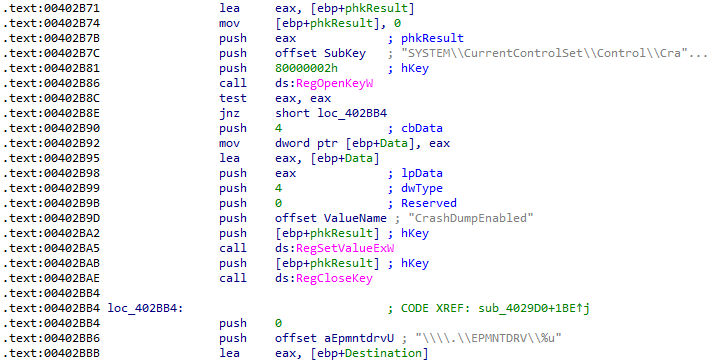
When the necessary driver is loaded, the wiper stores it with the randomly generated name and ‘.sys’ extension in the ‘C:\Windows\System32\drivers\’ folder.
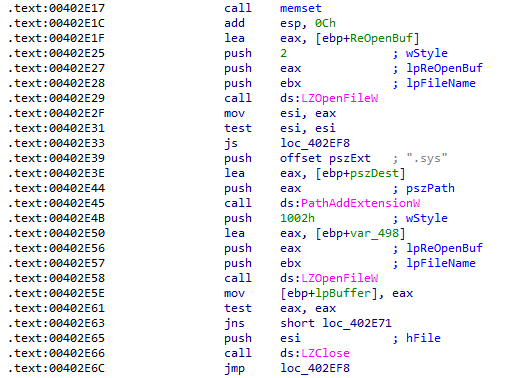
After all preparation steps are done, HermeticWiper begins to create multiple threads to corrupt physical drives. First, the malware will perform 100 iterations on \\\\.\\PhysicalDrive\%u using the DeviceIoControl function.
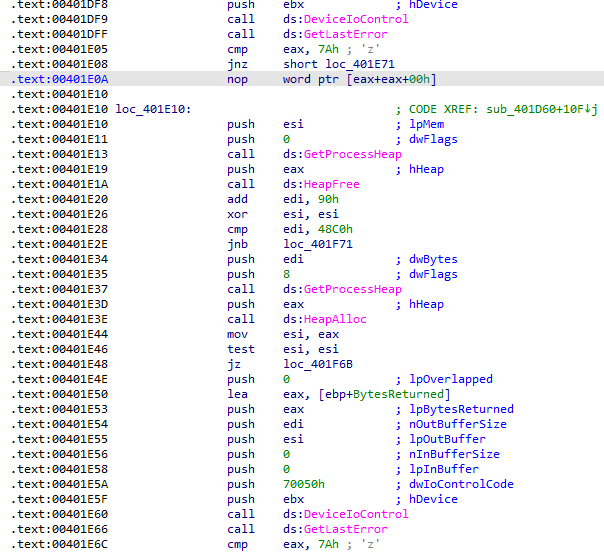
It checks whether the drive uses NTFS or FAT file systems.
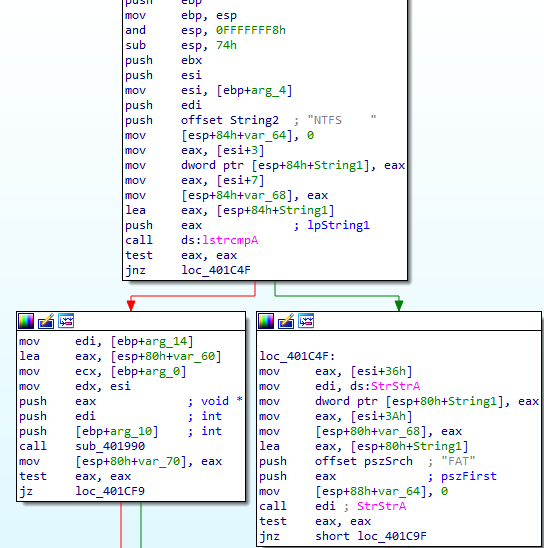
The disk corruption strategy is to perform a loop with the count from 1 to 100 and produce the byte swap operation. For NTFS and FAT systems, these functions have different implementations. It also uses the ‘CryptGenRandom’ and ‘CryptAcquireContextW’ functions to overwrite master boot records (MBR), master file tables (MFT), $Bitmap, $LogFile, ‘ntuser.dat’ and ‘C:\Windows\System32\winevt\Logs’ files with random bytes.
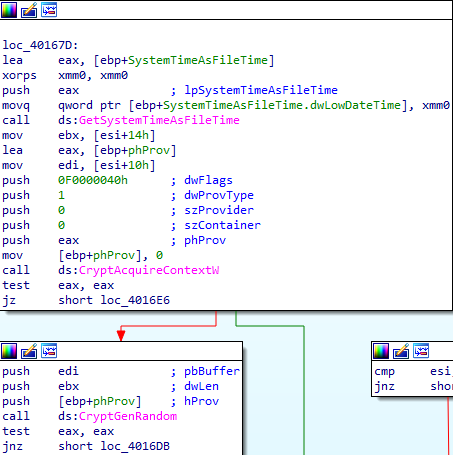
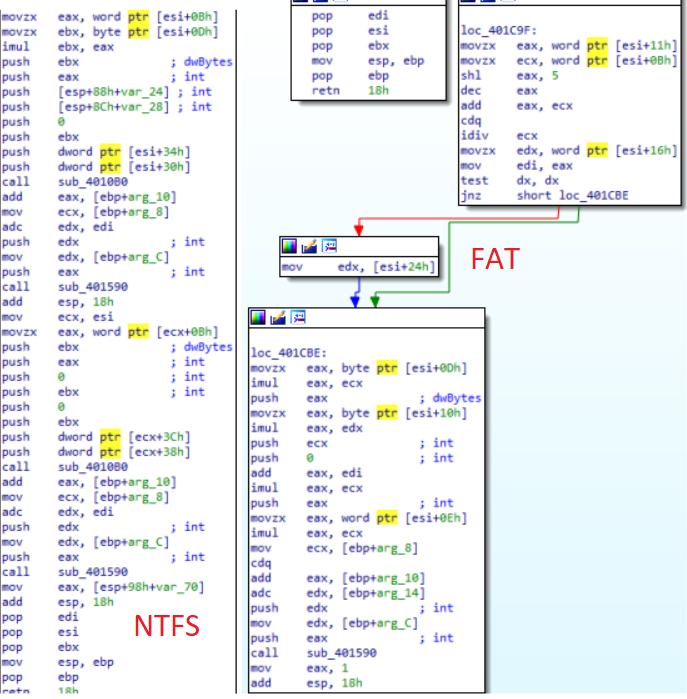
After rebooting the system, the OS won’t start.

The most interesting thing in the found samples is that they all have similar code, but different hashes. Comparing these files in Hex Workshop, we can observe that the only difference is the end of the file or some byte swap.
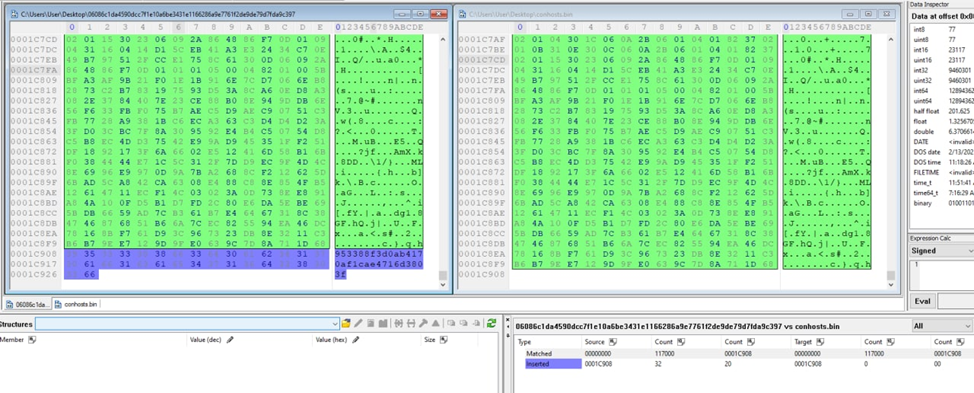
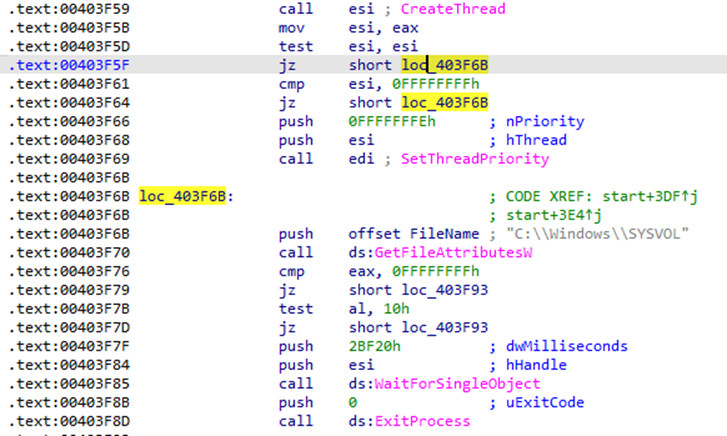
But one sample (1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591) has one more imported function — GetFileAttributesW — that checks “C:\\Windows\\SYSVOL” which is a folder residing on each and every domain controller within the domain. It contains the domain's public files that need to be accessed by clients and kept synchronized between domain controllers.
HermeticRansom
The other malware deployed on the government machines was a form of ransomware, called HermeticRansom or PartyTicket. This file was a PE64 executable, written in Go, which had a fake timestamp and didn’t have any digital signatures.
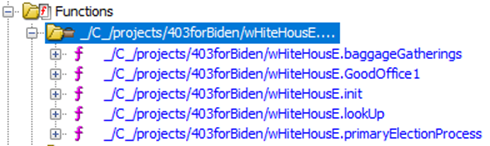
The interesting thing in this executable is names of some functions, which have direct reference to USA President Joe Biden.
To provide file encryption, HermeticRansom contains a lot of crypto functions.
HermeticRansom features a list of extensions that must be encrypted:
.acl.avi.bat.bmp.cab.cfg.chm.cmd.com.crt.css.dat.dip.dll.doc.dot.exe.gif.htm.ico.iso.jpg.mp3.msi.odt.one.ova.pdf.png.ppt.pub.rar.rtf.sfx.sql.txt.url.vdi.vsd.wma.wmv.wtv.xls.xml.xps.zip.docx.epub.html.jpeg.pptx.xlsx
This ransomware uses the AES algorithm to encrypt the victim's files. Before starting the file encryption process, HermeticRansom appends ‘[vote2024forjb@protonmail[.]com].encryptedJB’ to the filename. The extension ‘.encryptedJB’ is another reference to the president of the USA.
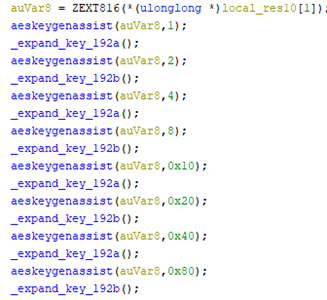
The first key is generated randomly, using the rand() function to choose the offsets in the array ‘1234567890ABCDEFGHIJKLMNOPQRSTUVWXYZ’. To generate round keys, it has a couple of implementations of the expanding keys functions for different sizes, and for 192 and 256 bytes it has two implementations. AES keys will be encrypted with RSA-OAEP.
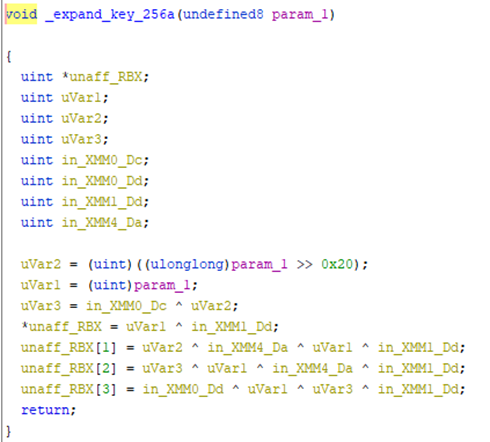
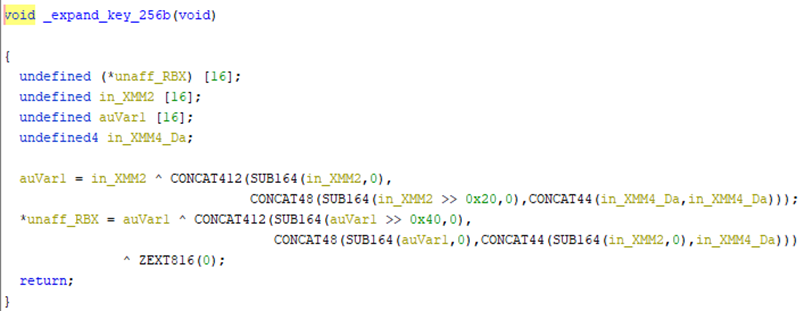
To generate round keys, HermeticRansom uses the previous expansion functions and AESKEYGENASSIST, which is an AES hardware-supported instruction. It has three different implementations for different key sizes.
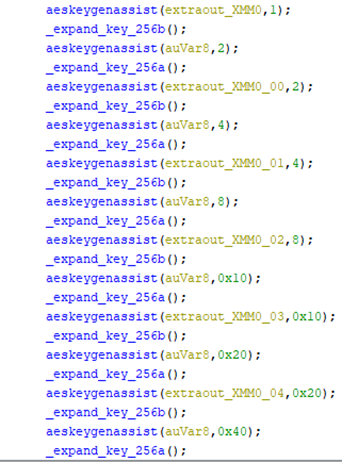
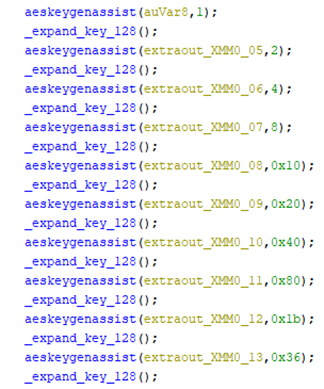
To encrypt a data block, it also uses a hardware-supported instruction (AESENC), which will complete one round of AES encryption flow.
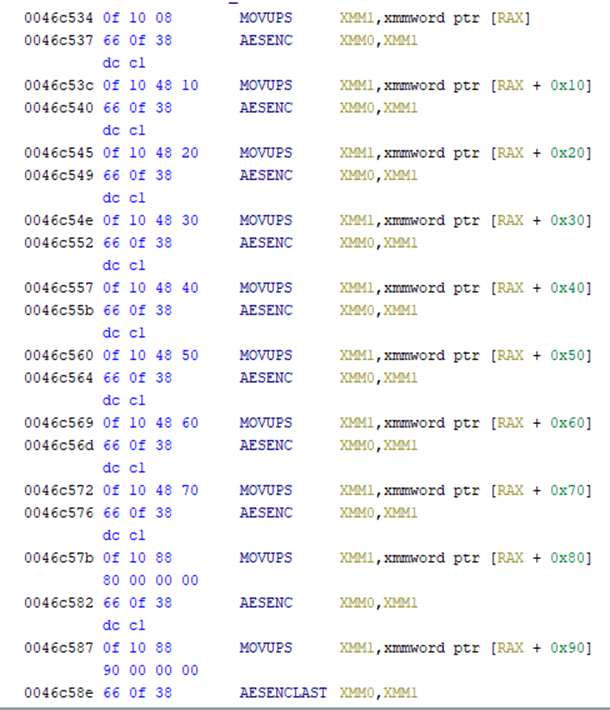
Due to encryption routine implementation errors, it has a breakable and slow encryption. This allowed a research team to write a script that decrypts files.
HermeticRansom uses the ‘cmd.exe’ process to execute a command infinitely. It copies itself in the folder where the sample is executed. The names of the files are assigned a value of the ‘cmd.exe’ process GUID, which copied a certain file.
cmd /c copy C:\Users\user\Desktop\[cmd.exe process GUID].exe
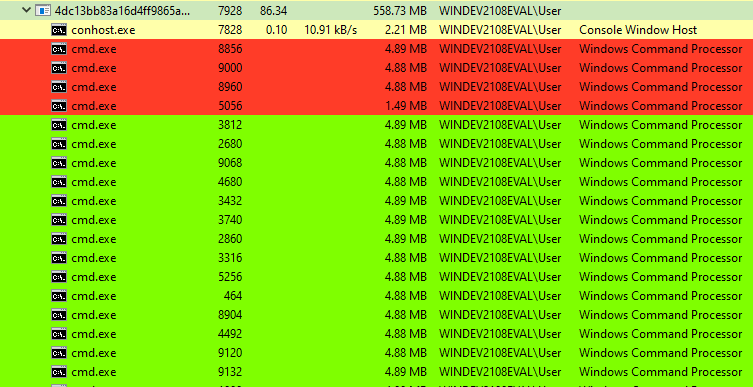
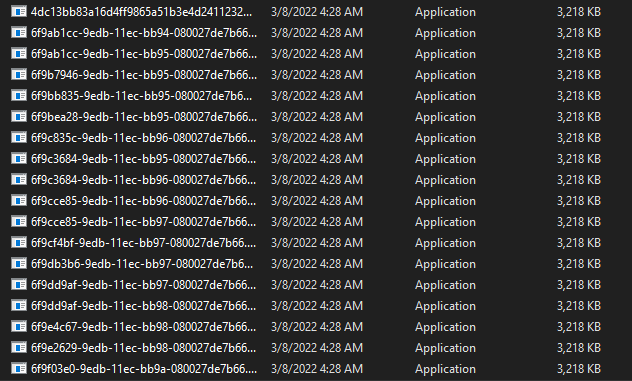
All copied files have the same hash values, as well as a HermeticRansom sample.
During execution it will drop the ransom note, which is stored in the memory and is an HTML file.
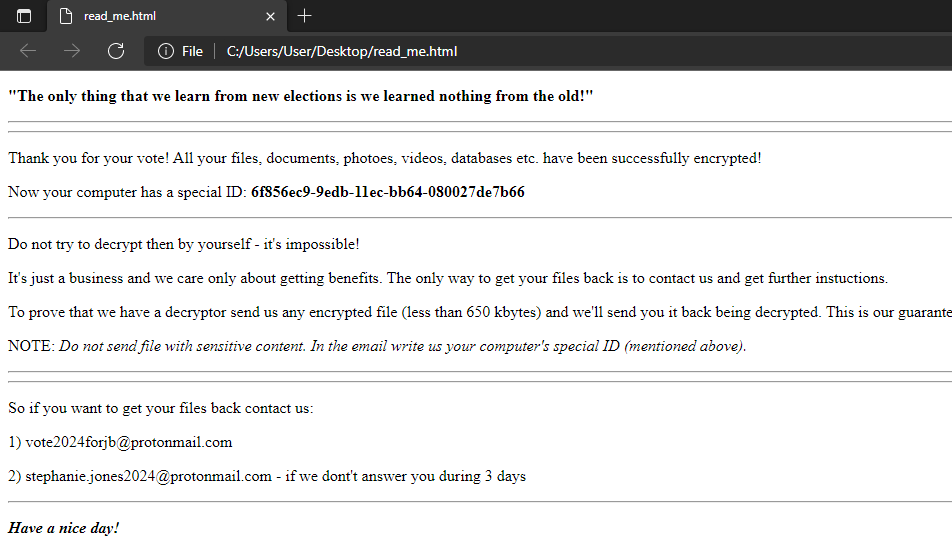
<!DOCTYPE html>\x0a<html lang="en">\x0a<head>\x0a\x09<meta charset="utf-8">\x0a</head>\x0a<body>\x0a<p><b>"The only thing that we learn from new elections is we learned nothing from the old!"</b></p>\x0a\x09<hr>\x0a\x09<hr>\x0a<p>Thank you for your vote! All your files, documents, photoes, videos, databases etc. have been successfully encrypted!</p>\x0a<p>Now your computer has a special ID:<b> </b></p>\x0a<p></p> \x0a<hr>\x0a<p>Do not try to decrypt then by yourself - it's impossible!\x0a</p>\x0a<p>It's just a business and we care only about getting benefits.\x0aThe only way to get your files back is to contact us and get further instuctions.\x0a</p>\x0a<p>To prove that we have a decryptor send us any encrypted file (less than 650 kbytes) and we'll send you it back being decrypted.\x0aThis is our guarantee.\x0a</p>\x0a<p>NOTE: <i>Do not send file with sensitive content. In the email write us your computer's special ID (mentioned above).</i>\x0a</p>\x0a<hr>\x0a<hr>\x0a<p> So if you want to get your files back contact us:\x0a</p>\x0a\x09<p>\x0a\x091)
Ransom note
The ransom note “read_me.html” that was dropped by HermeticRansom:
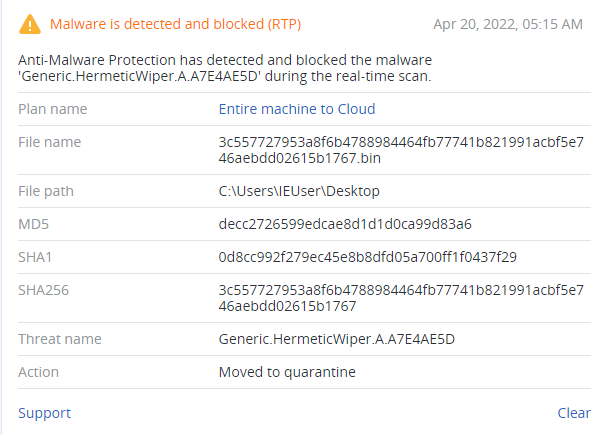
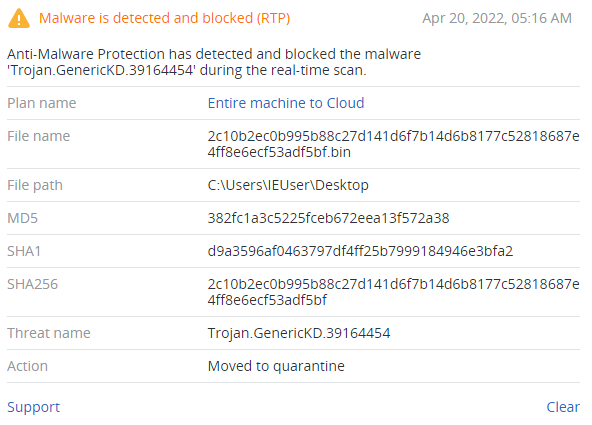
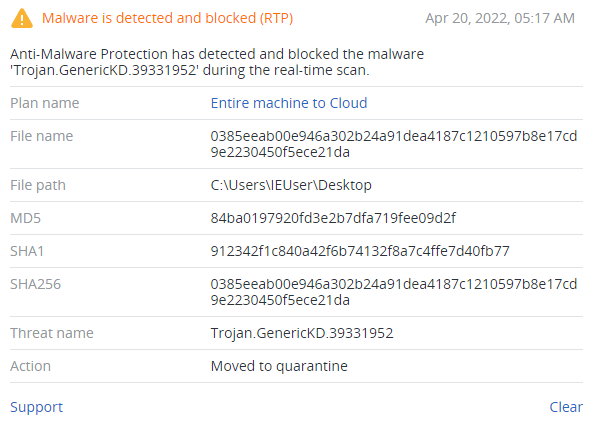
Detection by Acronis
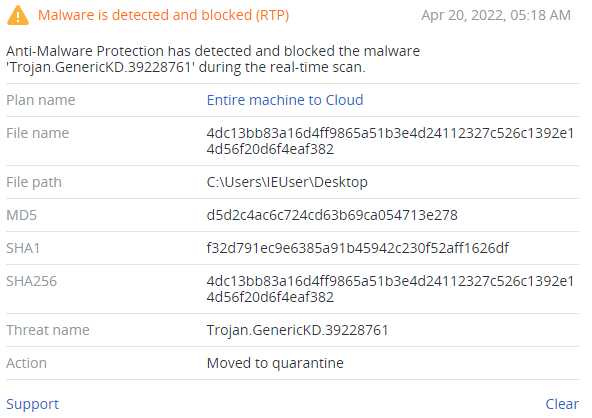
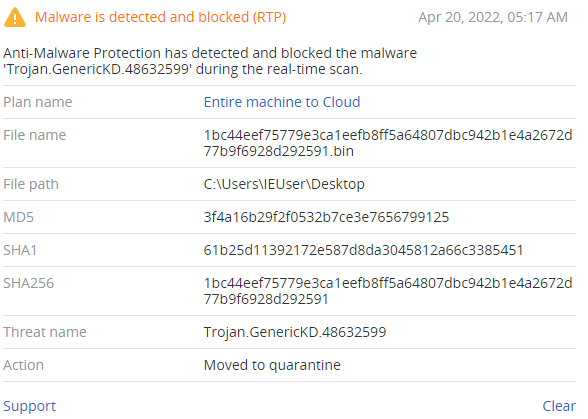
Conclusion
HermeticWiper and HermeticRansom were used in the targeted attack against the Ukrainian government, inheriting the goals of the past massive attack with the malware called WhisperGate.
The goal of the wiper was to corrupt the disks on government machines. HermeticWiper abused legitimate drivers to reach this goal. It had a direct preparation routine, which included obtaining necessary privileges and services controls.
HermeticRansom used AES and RSA algorithms to encrypt files and dropped ransom notes in HTML format. Both forms of malware were deployed through Microsoft Active Directory GPO and another malicious component called HermeticWizard, which spread them throughout the network.
IoCs
Files
All malicious files that were spotted in the targeted systems:



