As cyberthreats grow in complexity and sophistication, the role of threat hunting has become increasingly crucial, and organizations are turning to advanced solutions to fortify their defenses. Endpoint detection and response (EDR) and extended detection and response (XDR) with threat hunting capabilities are at the forefront of this defense evolution.
Acronis released EDR functionality in May 2023 and has now enhanced it with threat hunting functionality, which is very significant for product maturity and customer satisfaction. With the threat hunting release, Acronis Cyber Protect Cloud with Advanced Security + EDR has become a highly competitive solution on the market, delivering all expected functionality and more, including AI-generated incident summary and best-in-class automated restore.
What is threat hunting?
Threat hunting, within the context of EDR, can be likened to a skilled detective actively searching for clues and anomalies within an organization's network and endpoints. Unlike traditional security measures that rely on predefined signatures and known patterns, threat hunting involves a continuous and iterative process of investigation, analysis and discovery. It aims to uncover hidden threats that might have eluded automated detection mechanisms. To achieve this, proper functionality should be implemented. Let's go through the key components required for threat hunting.
Data collection, search and analysis
Threat hunting begins with the collection and analysis of vast amounts of data generated by endpoints, network logs and other security sources. EDR and XDR products leverage advanced data analytics and machine learning algorithms to sift through this data, identifying patterns, anomalies and potential indicators of compromise. A significant part of data collection, search and analysis is a manual search performed by the malware analyst to find a threat based on their knowledge and experience.
Continuous monitoring
Threat hunting is not a one-time activity; it's an ongoing process. EDR solutions provide real-time monitoring capabilities, allowing security professionals to track changes in endpoint behavior and network activities continuously. This proactive approach enables threat detection at various stages, from initial reconnaissance to lateral movement and data exfiltration.
Integration with threat intelligence
EDR products leverage threat intelligence feeds to enrich the analysis of collected data. By integrating information on known malicious actors, tactics, technique and procedures (TTPs), threat hunters can contextualize their findings and enhance the accuracy of threat detection. This integration helps security teams stay abreast of the latest threats and adapt their defense strategies accordingly.
Automated response and remediation
While threat hunting involves manual investigation and analysis, EDR products also incorporate automated response and remediation capabilities. Once a threat is identified, automated actions can be initiated to contain and neutralize the threat, preventing further damage. This seamless integration of manual and automated processes enhances the efficiency and effectiveness of the overall security posture.
The UI experience: Powerful search
For an admin or analyst who will do threat hunting, the actual experience is to run different search queries that result in some data and insights that will help to understand what is going on. The key here is an ease of use and ability to search for different things using various parameters.
Because Acronis focuses on small and medium MSPs, we included a substantial library of prebuilt search queries to make life easier for admins. When an admin clicks on a query from the repository, the search bar is auto-filled with the corresponding query. Below are a few examples:
· Investigate unusual cmd.exe spawning by other processes.
· Scheduled tasks registered.
· Shell Process creating File.
· svchost.exe running in an unusual user context.
· PowerShell script that has abnormal activity (obfuscating, etc.).
· Check for suspicious Remote Desktop Protocol (RDP) connections.
· Reg Query — last 10 files accessed or executed by explorer.
· Search for obfuscated files or information using ATT&CK ID.
The result of the query answers the question: "What workloads match my query?" The search will return rows for the workloads in which the search query has found a match. These rows will include information that can we narrowed according to the chosen parameters and criteria.
Acronis developed its own query language so customers can easily perform customized queries. It supports several of the most common operations, such as selecting data sources; filtering data based on conditions; specifying which columns to select and return from a query; and sorting, limiting, aggregating and grouping data.
In the next release, Acronis will expand this query language as well as support Kusto Query Language (KQL), which is used by some other vendors in the industry.
Let's look into a few possible attack examples, the queries that can be run and what we will get as a result.
The EDR solution detected credentials dumping, and an admin wants to investigate it further. He or she searches for low fidelity detections for a process to conduct more in-depth investigations.
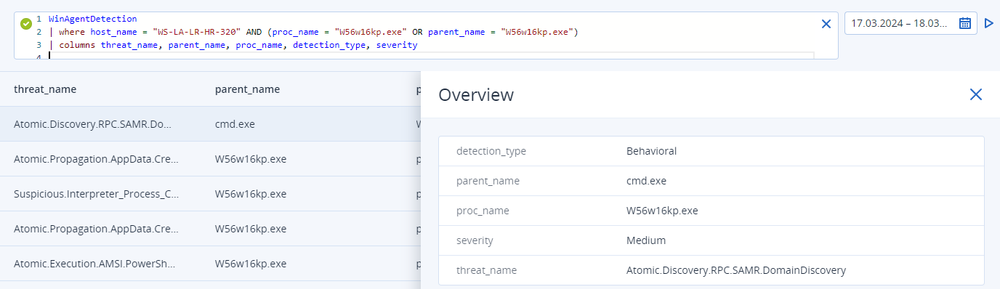
In this first step of threat hunting, the results reveal that low fidelity detection indicates that process "W56w16kp.exe" is conducting domain discovery.
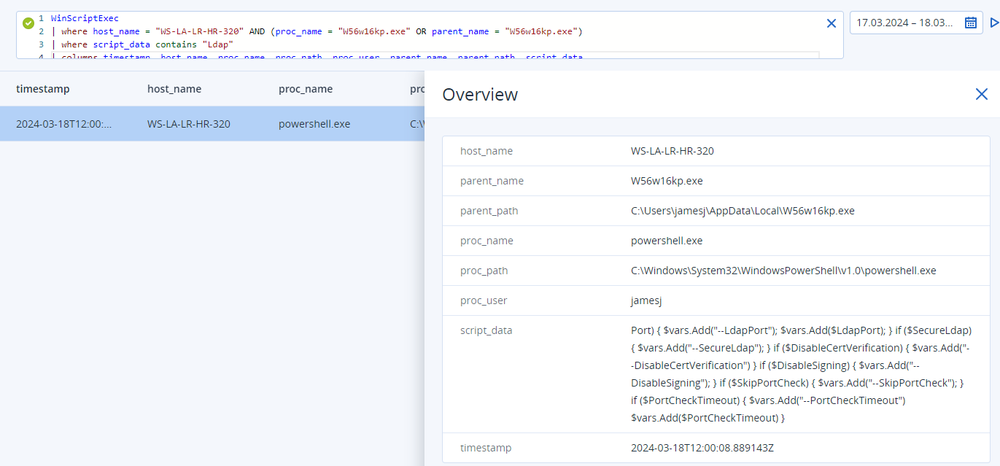
Investigating further, the admin analyzes the connecting events to determine if there are any scripts involved. The admin then runs a query and discovers there was a PowerShell script block with fragments of a modified "SharpHound.ps1" domain discovery script.
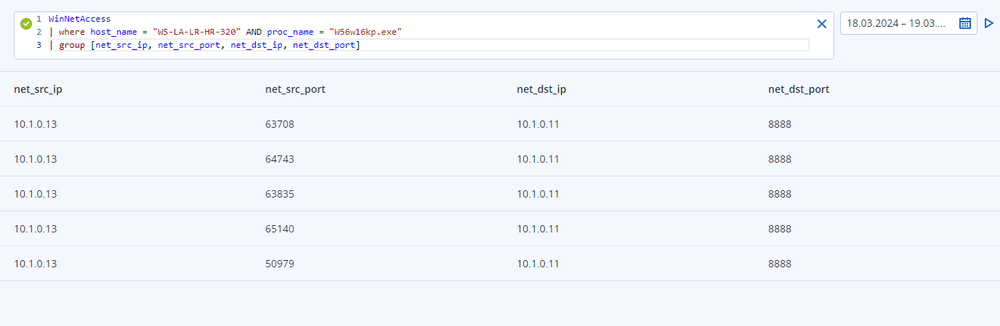
During the next step, network activity can be analyzed to identify possible C2 channels and lateral movement across the network. The results reveal process "W56w16kp.exe" connecting to a command & control server on port 8888/tcp.
This is just one example of threat hunting, but there are countless other cases with different attacks and techniques used.
Why do you need threat hunting as an MSP
MSPs need threat hunting in their security stack for a number of reasons. First, threat hunting allows organizations to identify and neutralize threats at their nascent stages, minimizing the potential impact of cyberattacks. By actively seeking out anomalies and suspicious activities, security teams can thwart adversaries before they can escalate their attacks.
Second, dwell time — the duration a threat remains undetected within a network — is a critical metric in cybersecurity. Threat hunting in EDR products aim to reduce dwell time by swiftly identifying and mitigating threats, limiting the window of opportunity for attackers to move laterally and exfiltrate sensitive data.
Third, insights gained through threat hunting contribute to a more robust incident response strategy. Security teams armed with a deep understanding of their network's normal behavior are better equipped to respond effectively when anomalies are detected.
Finally, threat hunting transforms cybersecurity from a reactive to a proactive stance. Instead of waiting for alerts to trigger, organizations can actively seek out potential threats, ensuring a more resilient and proactive defense posture. The iterative nature of threat hunting encourages a continuous improvement cycle. Insights gained from each hunting expedition can be used to refine and enhance security policies, update baselines, and fortify defenses against emerging threats.
Conclusion
Threat hunting in EDR products represents a paradigm shift in cybersecurity, empowering organizations to take a proactive stance against evolving cyberthreats. By combining advanced analytics, behavioral analysis, and threat intelligence, EDR solutions equipped with robust threat hunting capabilities enable security teams to detect and mitigate threats in real time. As organizations continue to face sophisticated adversaries, the integration of threat hunting within EDR becomes not only a best practice but also a necessity for maintaining a resilient and proactive defense posture in the dynamic world of cybersecurity.
With the threat hunting functionality in Acronis Cyber Protect Cloud with Advanced Security + EDR, it will be possible to retain incident data for up to one year, based on the chosen retention period at the general availability of this feature. During the Early Access Program, Acronis will provide threat hunting on data with seven days’ retention.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




