Unleash the power of industry-proven cyber protection




Upcoming events
What the experts say
Arsenal is at the forefront of using data to improve performance both on and off the pitch. The club knows that data is extremely valuable and needs to be protected, and as an official partner, Acronis provides cyber protection for Arsenal’s data and systems such as OneDrive and SharePoint within Microsoft 365.
Acronis’ business solutions
- Acronis Cyber ProtectComplete cyber resilience for small business, including backup and DR, anti-malware and remote endpoint monitoring.
- Acronis Disk DirectorOptimize, protect and manage your disks and volumes on local and remote machines with the most feature-rich toolkit
- Acronis Cyber FilesEnable employees to securely access, sync, and share content while IT maintains control over security and compliance
- Acronis Snap DeployDeploy a master image of your fully configured operating system to multiple machines at once
- Acronis DeviceLock DLPStop data leaks at the source with complete endpoint data loss prevention (DLP)
Acronis Cyber Protect
Modernize your cybersecurity and backup with integrated cyber protection
From €70.99 per year
Do it all with a single solution
As the only solution that natively integrates cybersecurity, data protection, and endpoint protection management, Acronis Cyber Protect enables you to tackle modern IT challenges with unparalleled ease.
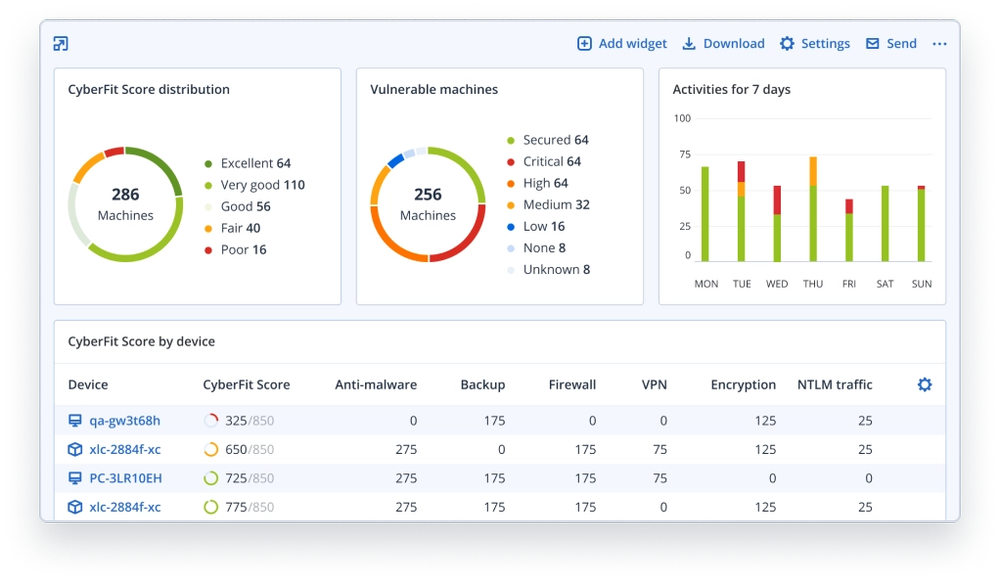
Spot vulnerabilities quickly
Identify gaps in your defenses with automatic vulnerability assessments.Keep systems up-to-date
Integrated patch management ensure that your business-critical applications are running the latest security updates, while automatic backups allow you to quickly roll back systems if necessary.Set custom policies
Create and assign flexible policies by department, user, or device.Ensure privacy compliance
Acronis’ solutions make it easy to identify and meet any applicable data privacy regulations, and to generate compliance reports that serve as proof of protection.Autodiscover devices
Protecting entire workloads has never been easier. Locate and protect multiple machines at once with automatic discovery and agent installation.Gather digital forensics
In the event of a cyberattack — even a failed one — forensic info can help you assess the full extent of what happened and who was responsible.






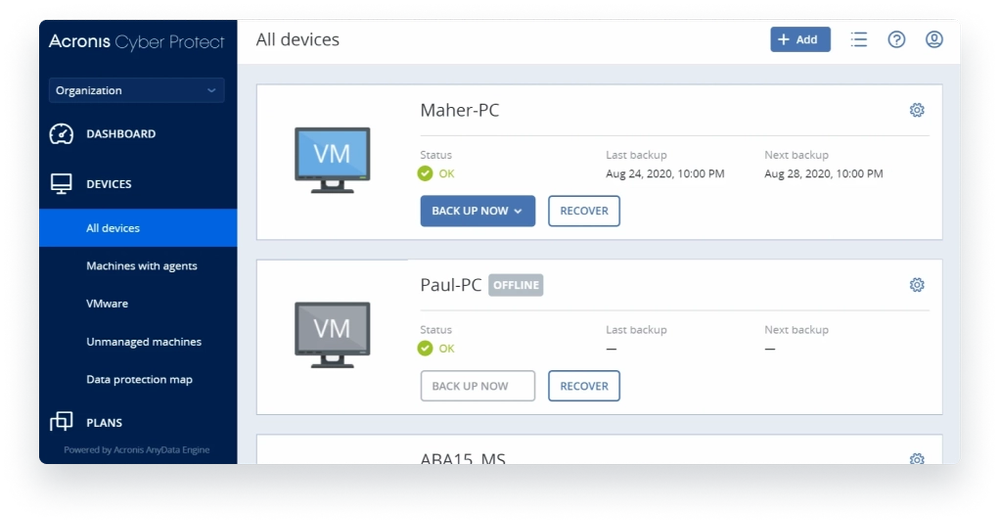
Protect more workloads on more platforms
Physical
Applications
- Microsoft Exchange
- Microsoft SQL Server
- Microsoft SharePoint
- Oracle Database
- Microsoft Active Directory
Virtual
- VMware vSphere
- Microsoft Hyper-V
- Citrix XenServer
- Red Hat Virtualization
- Nutanix AHV
- Linux KVM
- Oracle VM Server
Endpoints
- Windows PC
- Mac

Acronis Cyber Protect
Modernize your cybersecurity and backup with integrated cyber protection
From €70.99 per year
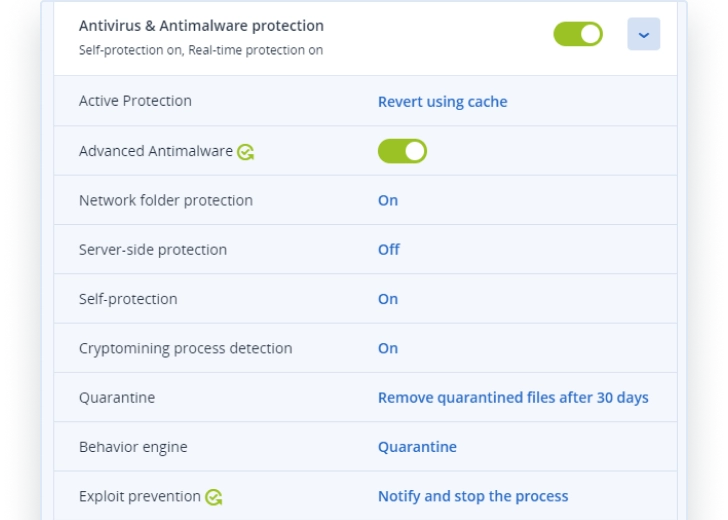
- AI-based anti-malware protection
- Ransomware protection and recovery
- Vulnerability assessments
- Patch management
- URL filtering and categorization
- Windows security solutions management
- Threat feed and smart protection plans
- Forensic data collection
- Anti-malware scanning of backups

- Server backup and recovery
- File backup and recovery
- Application backup and recovery
- Virtual infrastructure backup and data protection
- Server migration P2V, V2C, C2P
- Bare-metal restore
- Cloud backup
- Backup as a service for SMB
- Data storage and retention in cloud
- Back up to public cloud
- Cloud applications backup
- Off-site data protection
- IT disaster recovery
- Cloud disaster recovery
- Disaster recovery as a service
- Secure backup with notarization
- Cloud Storage
- Continuous data protection
- Bare-metal restore
- Mass deployment of PCs
- Mass server deployment
- Mac integration into Windows environments
- Disk partitioning and management
- Disk cloning
- Data protection maps and compliance reporting
- Vulnerability assessment
- Security posture evaluation
- Patch management
- Windows security solutions management
- Drive health monitoring
- BYOD protection and remote wipe
- Remote desktop
- Zoom, Cisco Webex, Microsoft Teams, Citrix Workspace protection
- Anti-malware scanning of backups

Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.