By 2021, security experts project that global damages from ransomware attacks will reach $20 billion. That’s a 57-fold increase in six years, which confirms ransomware as the fastest growing type of cybercrime – targeting consumers and businesses alike.
The growing threat of ransomware
For many people, their knowledge of ransomware began on May 12, 2017 when WannaCry tore across the globe, infecting a quarter million machines in more than 150 countries. The largest ransomware attack ever, it affected a diverse collection of entities, including FedEx, Spain-based Telefonica, Britain's National Health Service, German railway company Deutsche Bahn, and LATAM Airlines.
Since then, countless new strains of ransomware have surfaced and new delivery methods are continually developed by cybercriminals – all in their attempt to extort money from both consumers and businesses.
The good news is that it’s not too late to set up a robust defense against ransomware – and we explain what you can do below.
What is ransomware?
We know that ransomware is one of the fastest growing cybersecurity threats in the world, but what exactly is ransomware?
Ransomware is a type of malware that upon infecting a device, blocks access to it or to some or all of the information stored on it. In order to unlock either the device or the data, the user is required to pay a ransom, usually in widely used e-currency. The term ransomware covers mainly two types of malware: so-called Windows blockers (they block the operating system or browser with a pop-up window) and encryption ransomware. The term also includes some of Trojan-Downloaders, namely those that tend to download encryption ransomware upon infection of machine. Nowadays, encryption ransomware is widely regarded as synonymous with ransomware.
Anti-malware industry, including the FBI and similar organizations, agree that ransomware threats will unfortunately continue to become more and more prevalent, especially for both large and small businesses.
It is always better to stop a ransomware attack as early as possible. Ideally, it should be stopped at the desktop, before the ransomware has a chance to encrypt any files. So, it is important to understand the threat and use data protection solutions that will enable a security team to respond quickly to a ransomware attack, without disrupting the workflow to the desktop and networking teams, as well as users on the network. This is applicable not only to corporate users, but consumer users as well.
Fortunately, Acronis offers a ransomware protection solution that is helping both corporate and consumer users to fight ransomware effectively. Our solution can be used as a part of Acronis consumer (and later on, corporate) products or you can pair these products with the anti-malware solution of your choice.
Acronis Active Protection: an effective answer to ransomware threats
Acronis Active Protection is an advanced technology for Windows operating systems. Acronis has plans to expand it to cover Android and other operation systems, but at this point, most ransomware attacks target Windows systems. Windows systems currently require less research and effort for cybercriminals to create ransom-demanding malware.
Acronis Active Protection’s patent-pending technology is also the foundation of a very solid data protection approach. It can be expanded in a variety of ways. But first, let’s see the basics of how it works, and why Acronis Active Protection should be the first tool in your ransomware protection arsenal.
The heuristic ransomware detection approach
At the heart of Acronis Active Protection lies a heuristic approach that you may have heard of in relation to the anti-malware industry. The heuristic detection approach is much more modern and advanced than the signature one. One signature can detect only one sample, while heuristics can detect a few or even few hundreds of samples of files that belong to one so-called family (usually similar in behavior or patterns of actions). The behavioral heuristics we are talking about are basically a chain of actions (file system events, to be precise) done by a program, which is then compared with a chain of events in a database of malicious behavior patterns.
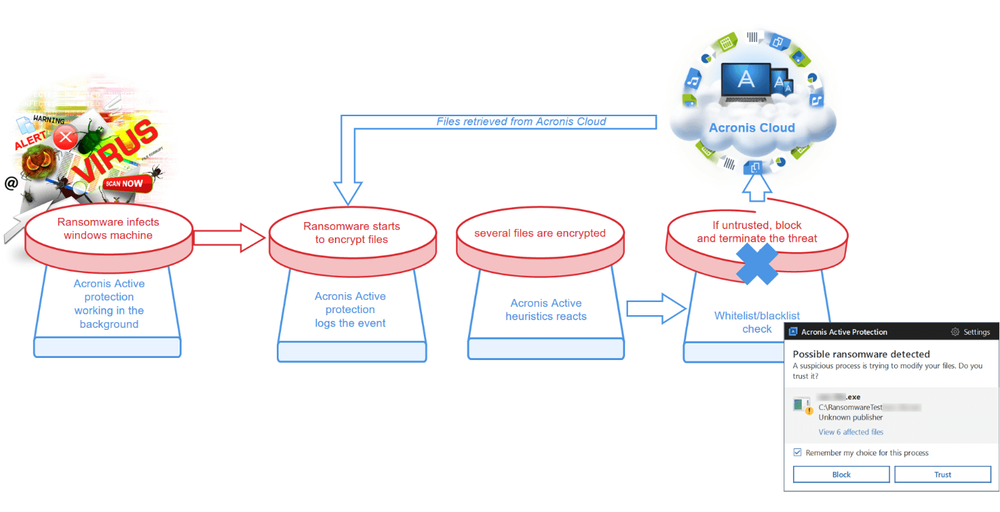
Behavioral heuristics are accompanied by white and blacklists of various programs. Why do we need a whitelist check? Because heuristics are capable of detecting new ransomware threats, yet at the same time, they operate on the basis of experience/behavior results and need to be controlled for false positives. That is why Acronis Active Protection products check any suspicious processes against the whitelist and blacklist. At the same time when user blocks the potential ransomware attack, it goes into the blacklist and this does not let this malicious program to start on next reboot. This is very important because users do not have to repeat the process of blocking a certain type of ransomware again and again.
An obvious way for cybercriminals to compromise the backup would be an attack to the Acronis True Image program. That’s why Acronis Active Protection uses self-protection of the Acronis agent program. No process in the system except Acronis software can modify backup files. We have also implemented a robust self-defense mechanism that will eliminate any typical ransomware attack and will not allow criminals to disrupt the work of the backup software or alter the content of backup files.
More than that, Acronis Active Protection also monitors the Master Boot Record of the user’s Windows-based hard drive and will not allow any changes from non-whitelisted legitimate utilities.
Does Acronis Active Protection work with any ransomware attack?
Yes, it does. However, we must structure this in a way of constant, active data protection from three main ransomware vectors.
1. Stopping a Ransomware attack on any file
A typical ransomware case can usually be solved by using previously backed-up files to restore compromised data. However, this is now easier to handle and most likely will never happen on a wider scale if you have an Acronis Active Protection-enabled product. Restoration of a few encrypted files is done automatically (after user confirmation) and to the latest version-- because the technology works in real-time. Imagine the situation when a backup is scheduled to be done at midnight, but at 11 P.M., ransomware hits the machine. If you simply recover files from an online backup, 11 hours of work are lost. However, with constant monitoring of processes and activity, as described above, no data is lost when a ransomware attack is initiated.
2. When Ransomware attacks a local backup file
In this case, Acronis Active Protection actively monitors any local drives and prevents backup files from being modified by malicious ransomware.
3. Сloud backups are modified by Ransomware
Cloud backup files stored in Acronis Cloud Storage are exceptionally safe from direct modification by malicious code, by using end-to-end strong encryption and restricting access to file modification activities only to signed and authorized Acronis agent software.
How to deal with ransomware attacks
Let’s take a look at the table below, describing techniques and methods used by ransomware to compromise data.
Why is Acronis Active Protection better than antivirus and backup software?
That’s actually simple: two separate products won’t save your data from a ransomware attack, as they do not know how to talk to each other. Any data impacted by a missed detection from an anti-malware solution in a traditional approach is gone, as no anti-malware solution backs up files to the cloud and no backup solution detects malware. However, when Acronis Active Protection is paired with Acronis Cloud via an Acronis endpoint agent, original data can be recovered from local caches, local backups, or cloud backups. This eliminates one of the most dangerous types of ransomware.
Anti-malware software can miss a ransom-demanding malware, and cybercriminals are well aware of this limitation. The bad guys research major, if not all, anti-malware solutions to find weaknesses in detection technologies or program architecture in order to avoid detection. As we already mentioned, traditional signature detection is useless nowadays, because cybercriminals just need to encrypt the malware in order to avoid detection. And many free anti-virus software packages still use this approach, which is why all anti-malware vendors recommend using backups, as we said earlier. At the same time, all cloud backup solutions protect against a simple attack vector – damage of data on a local machine. But no one protects against a targeted attack on a backup solution.
UPDATE April, 10. The independent IT Security Institute AV Test put four new programs onto the test bench and came to conclusion: "The test clearly demonstrates that useful malware protection ought to include the deployment of backup software. "Acronis True Image 2017 New Generation Premium" was the only backup solution in the test that was able to stop ransomware attacks.
Acronis Active Protection protects against future threats
Why would cybercriminals attack backups? Because they will see a threat for their business/money income very soon. Projects like www.nomoreransom.org/prevention-advice.html motivate users to do two simple and very important things:
- Always – backup your data
- Do not pay the ransom!
So, bad guys are already attacking backup files. However, this won’t be enough in almost all cases, as many backup solutions have cloud storage. In order to compromise a cloud-based backup, they need to acquire access credentials — and regular ransomware and malware attackers typically do not have these capabilities.
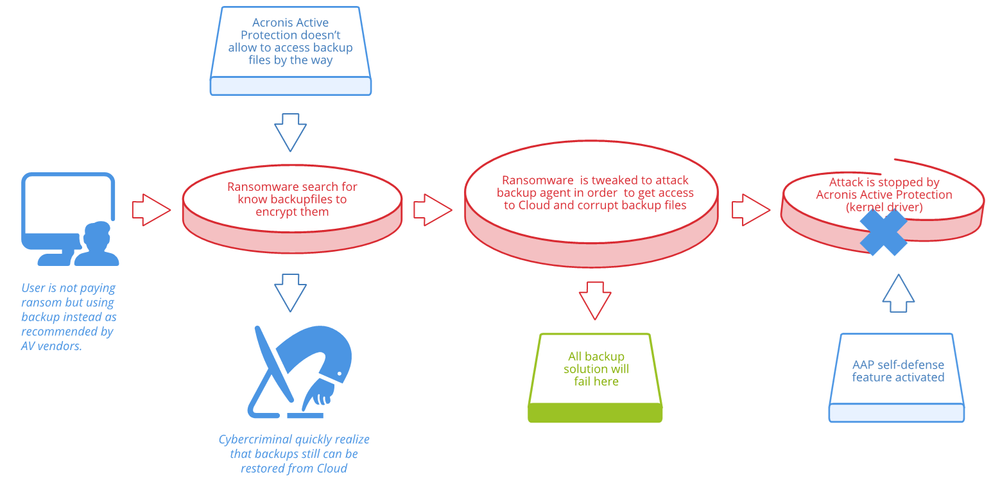
Soon, bad guys will think: “How does data make its way to the cloud?” The answer, obviously, is through an agent on the device. Technically, there are many ways to inject the malicious code in the local agent and compromise backup data in the cloud. The only backup software that can stop this future attack is an Acronis product with Active Protection.
A few things to remember
Acronis Active Protection is the new generation of data protection that provides:
- Real-time backup and protection from ransomware attacks for the Windows platform. There will be no time gap in restored versions of the files, so you do not have to lose any of your progress.
- Future proof protection that can be enhanced even further when new ransomware threats emerge.
- A transparent, user friendly interface that works pretty much automatically.
As you can see, Acronis Active Protection adds an additional, and better, layer of data protection against the ransomware attacks of today and the future.
Products with Active ransomware protection:
- Acronis True Image 2020 for personal backup — Buy now: from $49.99 or Try for free for 30 days
- Acronis Cyber Backup for business data protection — Full functional trial
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



