The new Petya-like ransomware just served a big blow to hundreds of banks, corporations, government organizations, post offices and shopping outlets around the world, spreading like fire, taking advantage of the EternalBlue exploit used by WannaCry ransomware only a few weeks before.
Petya, Petrwrap, EternalPetya — while the world is still deciding what to call this damaging ransomware worm, let’s pull it apart and see what it’s made of. For the purpose of this article, we’ll call it EternalPetya.
Propagation
It is believed that the attack started by executing an infected software update for the M.E.Doc program (the e-document management tool widely used by accountants in Ukraine to submit tax reports). However, at the moment of writing, we cannot confirm this information.
Once EternalPetya infects a computer within an organization, the ransomware can easily spread with EternalBlue/EternalRomance exploit and WMIC and PSExec tools. On the contrary to WannaCry, the propagation functionality is embedded to the ransomware main module represented as DLL.
Similar to WannaCry, it scans IP addresses on a local network, looking for open ports 139 and 445 of the NETBIOS Session Service (netbios-ssn) and Microsoft Directory Services (microsoft-ds) to run the EternalBlue and EternalRomance (for versions from Windows XP to Windows 2008) exploits respectively.
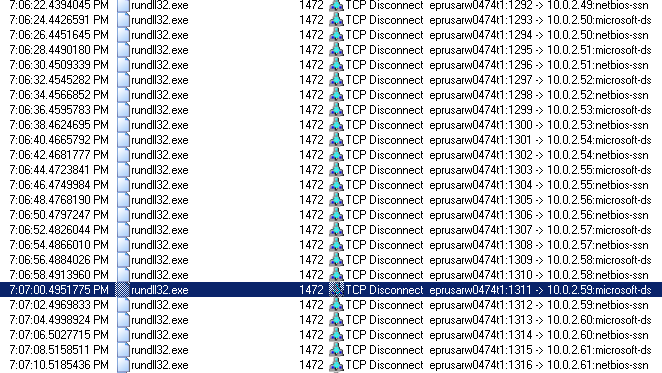
Once a connection is established, the cryptolocker drops its DLL to the following folders to be executed by the vulnerable service:
Once the EternalBlue exploit (CVE-2017-0144) succeeded, the ransomware runs DoublePulsar exploit to inject the uploaded DLL into ‘lssas.exe’ starting it on the kernel level that allows EternalPetya to steal user logins and passwords, which can be used to propagate over the local network using the WMIC (or PsExec in some versions) tool.
Another way of propagation is by using WMIC or PsExec to connect to a remote computer using stolen user’s login and password and remotely execute the ransomware DLL:
The logins and passwords are harvested using specialty tools executed from the resource section and transferred through a specially created pipe back to ransomware main module:
File information
EternalPetya is a DLL with the exported function named ‘perfc_1’ that can be called by the ordinal number ‘1’.
EternalPetya is signed using an expired Microsoft certificate:
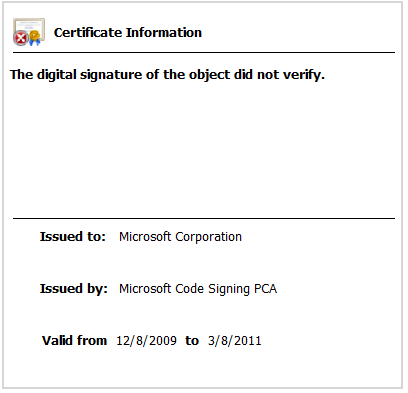
This might confuse some antivirus solutions and let the cryptolocker stay undetected.
Encryption
Unlike Petya, EternalPetya encrypts the files with the following extensions before system shutdown:
For the encryption, the cryptolocker utilizes Microsoft Cryptographic Provider. EternalPetya generates one AES-128 key for all files and export it using a hardcoded X509 certificate (public RSA-2048 key) imported having X509_ASN_ENCODING | PKCS_7_ASN_ENCODING type.
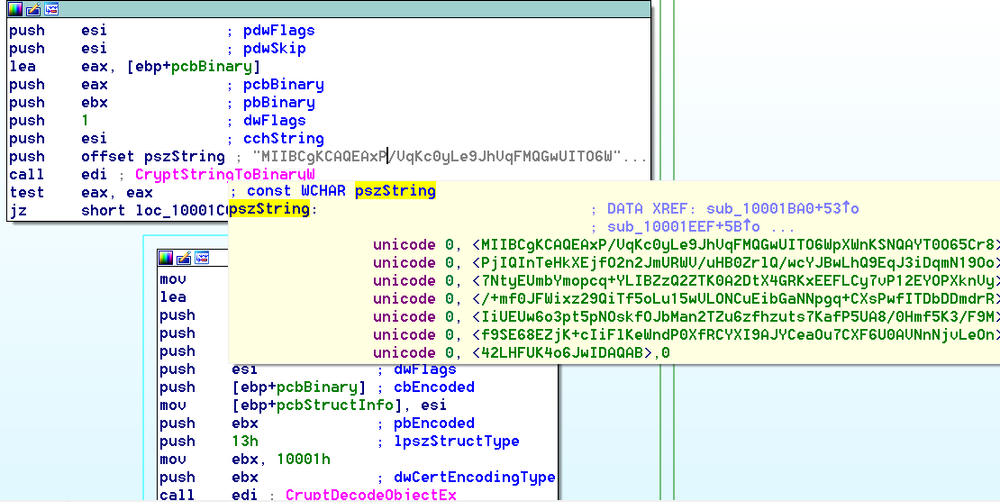
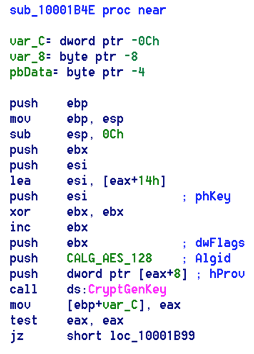
The encrypted AES session key is exported as SIMPLEBLOB and stored in a README file.
To avoid overloading the CPU, the ransomware waits for one minute before starting a new thread to perform encryption and spreading. It waits for another minute before creating a README file.
Shutting down the system
To shut down the system EternalPetya creates a task to start the command ‘shutdown,exe /r /f’ in 10-60 min:
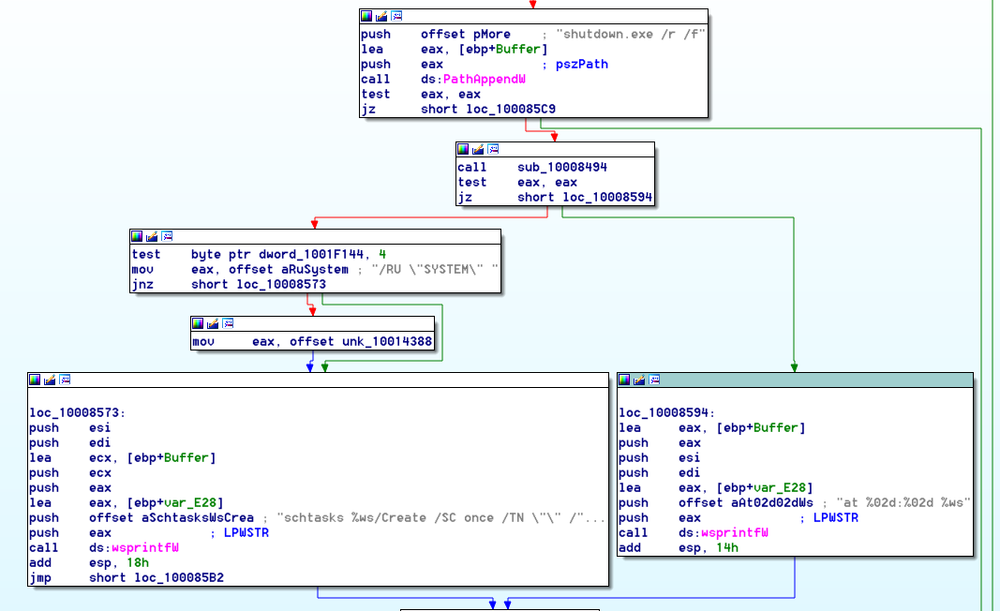
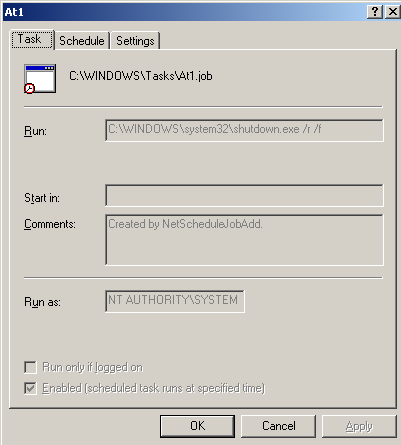
Hiding its traces
To hide its own traces from the Event Log, EternalPetya runs the following command:
BootLoader
The EternalPetya ransomware overwrites 22 sectors in the beginning of the primary hard disk \Device\Harddisk\DR0 putting its boot loader and own kernel like all previous modifications of Petya to prevent Windows from starting up.
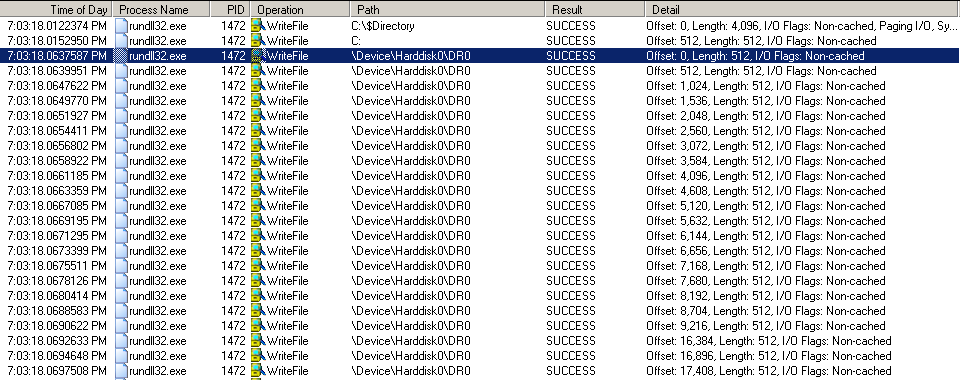
The EternalPetya code written into the boot sector:

After the reboot it starts encrypting the MFT showing a fake CHKDSK progress:
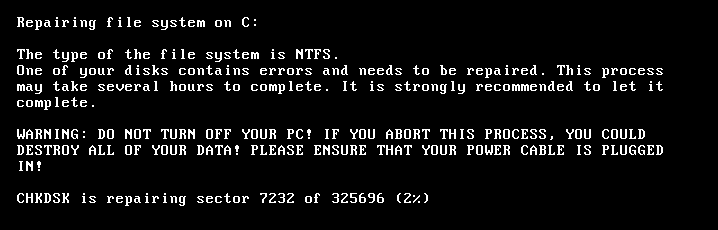
Once the encryption is completed, it displays the following message:
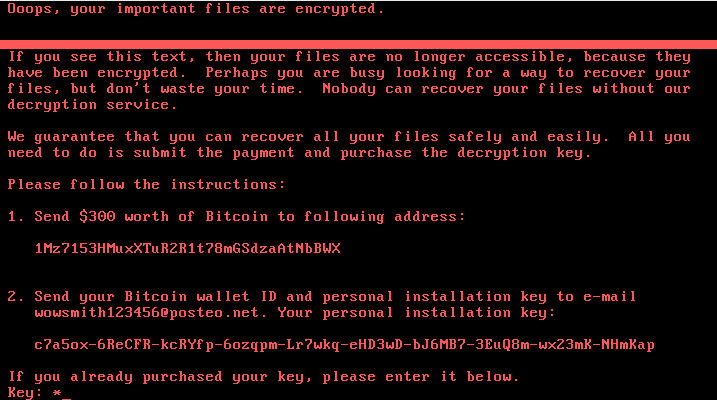
Bitcoin payment
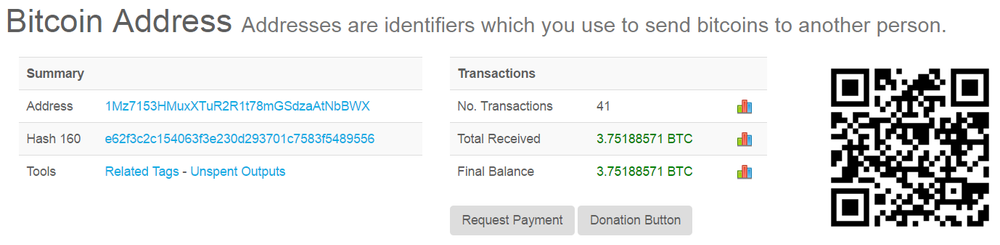
So far, we see 45 payments totalling 3.75 BTC, which is over $10 000. Keep in mind that the payment does not guarantee the decryption of files.
At the moment of writing this article, the attacker’s email is blocked by the service provider. There is no way to decrypt files and unlock your computer.
How to protect your computer
Performing secure backup is the only way to protect your computer without paying the ransom. However, to avoid prolonged downtime and the need to manually restore the affected data, a full image backup with Acronis Active Protection™ is highly recommended.
Acronis Active Protection, which is part of Acronis True Image 2017 and Acronis Backup 12.5, uses sophisticated analysis and artificial intelligence to monitor your system. If it spots any errant behavior or suspicious processes, it stops the activity and blacklists the program responsible for it, ensuring that it can’t restart on the next reboot.
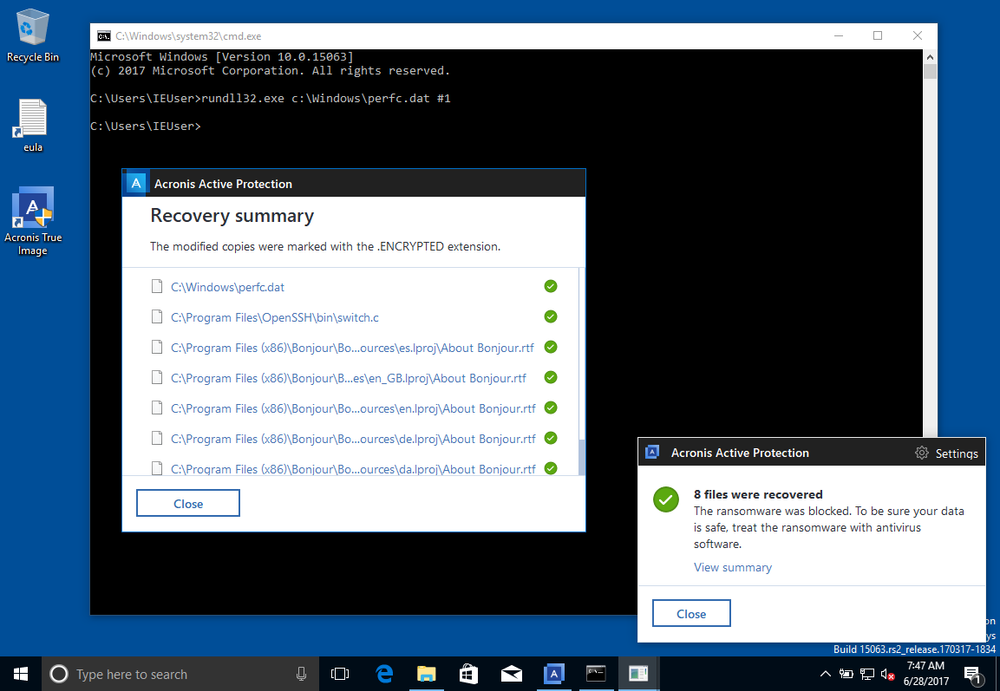
If ransomware somehow does manage to sneak through and start encrypting files, Acronis Active Protection will quickly detect the encryption that’s going on and halt it – automatically restoring the files to the most recently backed up version.
Here is what it looks like when Acronis Active Protection blocks EternalPetya on a Windows computer.
Would you like to find out more? Try Acronis True Image 2017 for home or Acronis Backup 12.5 for business and enjoy protection from ransomware.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.