- Natively integrated
- Proactively prevent risks, actively stop threats, and reactively ensure unmatched business continuity across NIST.
- Easily manage and scale with a single platform and agent to deliver all cybersecurity, data protection, and endpoint management services.
- Ensure compliance and protect sensitive data with behavioral-based DLP and best of breed disaster recovery.
- Highly efficient, AI-guided cybersecurity
- Protect endpoints with visibility across the most vulnerable attack surfaces – incl. email, identity, Microsoft 365 apps.
- Streamline analysis and response to just minutes, guided by AI - conduct richer investigations, respond faster and mitigate risks at scale.
- Easily automate response actions for instantaneous remediation to scale security operations and reduce costs.
- Built for MSPs
- Unlock superior ROI via a centralized platform that streamlines daily tasks and reduces costs.
- A SaaS-based, multitenant platform with role-based access that’s easy to manage and scale across disperse client IT environments.
- Extend additionally with 300 integrations, including commonly used by MSPs — SIEM, PSA, RMM tools.
- GovernRapidly establish cybersecurity and risk management strategies, set roles and policies, and ensure continuous oversight via an integrated platform.
- IdentifyIdentify vulnerable assets and data you need to protect across multiple endpoints.
- ProtectProactively protect IT assets, endpoint devices and data with integrated backup, DLP and endpoint management capabilities.
- DetectContinuously monitor via AI- and ML-based threat detection and behavioral analysis to guard against advanced threats and data exfiltration.
- RespondAnalyze and respond to incidents with ease in just minutes, guided by AI. Automate remediation actions for instantaneous mitigation and leverage integrated recovery as part of response.
- RecoverDeliver unmatched data protection and business continuity with no data loss across your clients’ IT stack.
Powered by industry-recognized, award-winning endpoint protection
- Top ProductAV-TEST 02/2025
- 6/6Protection
- 6/6Performance
- 6/6Usability














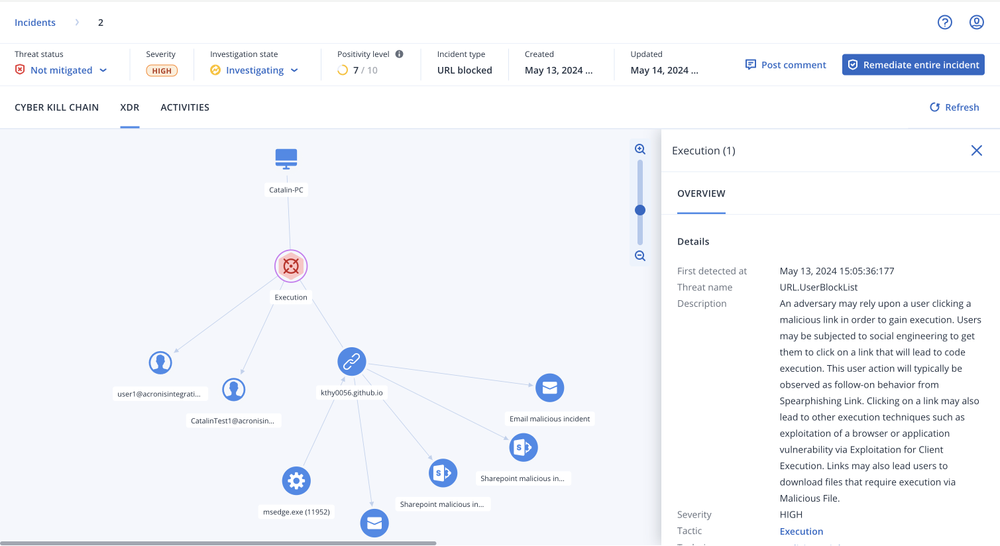
Acronis Cyber Protect Cloud with Security + XDR
Leverage a complete, natively integrated, highly efficient protection built for MSPs
Streamline your services and reduce resource requirements with AI-based innovations
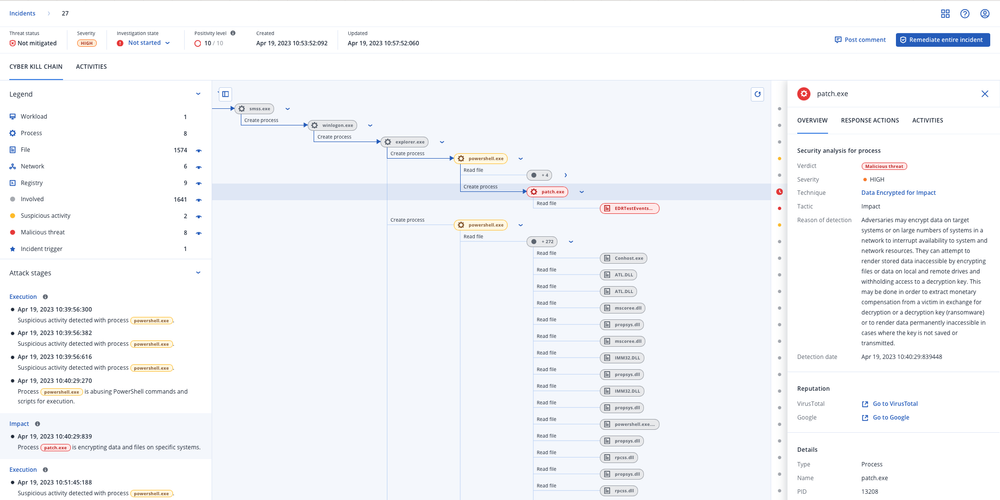
- Acronis CopilotConduct richer investigations, respond faster and mitigate risks at scale in just minutes, using only natural language - via a conversational user experience with a GenAI assistant.
- AI-guided, minutes-not-hours attack analysisLeverage AI-based incident summaries and interpretations aligned with MITRE ATT&CK framework to unlock a swifter response.
- Integrated response, recovery, and patchingEnsure more holistic response to incidents: isolate and remediate the threat, recover from the damage, and close open security gaps.
- AI-prioritization of incidentsEnsure you always stay on top of high-risk activities with a prioritized view of incidents, rather than a flat list of alerts.
- Protect clients’ most vulnerable attack surfaces
- Email Security (Perception Point)
- Entra ID
- Microsoft 365 collaboration apps: SharePoint, OneDrive, Teams
- Benefit from 300 more integrations across your tech stack
- Security information and event management (SIEM)
- Remote monitoring and Acronis RMM
- Professional service automation (PSA)

An MSP-first partner that plays for your success
Our partners are the first to benefit from new product lines and innovations, but also we enable them with technical, marketing and sales support and trainings via the Acronis #CyberFit Partner Program. As a leader on the MSP cybersecurity market, Acronis is focused on your success rather than competing with you for business.
Acronis Professional Services
If your organization has a complex IT infrastructure or limited IT resources, Acronis Professional Services can assist you with the design, integration, implementation and on-going operation of your Acronis solution.
Consulting services
Leverage Acronis’ experience and shorten the time it takes to gain value from your Acronis investment.- Exclusive
Deployment services
With Acronis Deployment Services, you can be the first to market with data protection, infrastructure migration, and disaster recovery services. Audit services
Decrease maintenance costs and enjoy peace of mind knowing your customers’ data is protected in accordance with industry and Acronis best practices.Educational services
Enable your personnel to drive data protection, migration, and disaster recovery services enablement, effectively support your customers.
Resources
- DatasheetAcronis Cyber Protect Cloud
- DatasheetAcronis Cyber Protect Cloud with Security + XDR
- WhitepaperCyber protection across the NIST Framework with Acronis for MSPs
- WhitepaperThe ultimate cyber insurance coverage guide for MSPs
- Solution brief8 real-world MSP use cases with Acronis XDR
- InfographicHow MSPs can propel business growth with Acronis XDR
- Analyst reportAcronis named a Champion in the Canalys Global Cybersecurity Matrix
- Analyst reportFrost & Sullivan names Acronis a Leader in its 2025 Endpoint Security Radar
Compare our protection suites and choose what best fits your needs
Consolidation and service management centralization with Acronis is easier and more approachable than ever. Expand your capabilities to offer holistic protection, defend organizations and provide true business resilience for clients and their data in the face of modern cyberthreats.
Acronis EDR
Use Acronis’ cyber protection technologies to detect & respond to advanced threats across endpoints, including leveraging AI-guided analysis and single-click response, and benefit from modular pricing.
Learn moreAcronis XDR
Expand Acronis’ award-winning endpoint protection technologies with visibility and response (incl. integrated recovery) across most vulnerable attack surfaces – email, identity, Microsoft 365 collaboration applications.
| Behavior-based detection | | | |
| Vulnerability assessments | | | |
| Device control | | | |
| File- and system-level backup | | | |
| Inventory collection (with Advanced Management) | | | |
| Patch management (with Advanced Management) | | | |
| #CyberFit Score (security posture evaluation) | | | |
| Remote connection (with Advanced Management) | | | |
| Remediation including full reimaging | | | |
| Business continuity (with Advanced Disaster Recovery) | | | |
| URL filtering | | | |
| Exploit prevention | | | |
| Real-time threat intelligence feed | | | |
| Threat hunting – Early access | | | |
| Automated, tunable allowlisting based on profiling | | | |
| Forensic data collection | | | |
| Event monitoring | | | |
| Automated event correlation | | | |
| GenAI assistant (Acronis Copilot – Early Access) | | | |
| Prioritization of suspicious activities | | | |
| AI-generated incident summaries | | | |
| Automated MITRE ATT&CK® attack chain visualization and interpretation | | | |
| Single-click response to incidents | | | |
| Full threat containment including endpoint quarantine and isolation | | | |
| Automated response playbooks | | | |
| Intelligent search for IoCs including emerging threats | | | |
| Attack-specific rollback | | | |
| Anti-ransomware protection with automatic rollback | | | |
| Integration with Microsoft 365 apps (SharePoint, OneDrive, Teams, and Outlook, Entra ID) | | | |
| Integration with Advanced Email Security (email telemetry) | | | |
| Integration with Collaboration App Security (Microsoft 365 apps telemetry) | | | |
| Delete malicious email attachment or URLs | | | |
| Search for malicious attachments across mailboxes | | | |
| Block malicious email address | | | |
| Terminate all user sessions | | | |
| Force user account password reset on next login | | | |
| Suspend user account | | | |
| MDR service | | | |
| Public API for EDR | | | |
Upcoming events
Expand your services with advanced protection
Add other powerful components to strengthen your services even further with advanced protection and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
- Security + XDRInstead of counting on a costly and complex stack of point solutions, Acronis XDR introduces natively integrated, highly efficient protection built for MSPs:
- Natively integrated cybersecurity, data protection and endpoint management
- Highly efficient security designed to protect the most vulnerable attack surfaces with AI-guided incident analysis and single-click response
- Built for MSPs, including a single agent and console for all services
- Security + EDRInstead of counting on a costly & complex stack of point solutions, Acronis enables MSPs via integration of EDR, endpoint management, and backup & recovery to:
- Easily launch a complete security solution, including rapid recovery
- Protect against modern threats and readily comply with cyber insurance requirements
- Maximize efficiency through a single security platform
- Acronis RMMAchieve peak MSP performance with a natively integrated, secure, AI-powered RMM. Enhance client satisfaction by delivering superior IT administration and monitoring services while improving security posture for both endpoints and Microsoft 365. Boost technician performance with seamless automation of IT management.
- Automated patch management
- System and hardware monitoring
- AI-assisted scripting and more
- Acronis PSASimplify success with an easy-to-deploy, adopt and use PSA tailored for modern recurring and cloud MSP business models. With Acronis PSA, you take the shortest path to increased profits and streamlined business operations.
- Service desk
- Billing and invoicing
- KPI reports and more
- Advanced BackupDefend clients’ data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You can also gain visibility into data-protection statuses across your clients’ infrastructure.
- Continuous data protection
- Data protection map
- Off-host data processing
- Disaster RecoveryGet clients back to business in mere minutes when disaster strikes by spinning up their systems in the Acronis Cloud and restoring them anywhere, ensuring immediate data availability. Make disaster recovery painless and increase efficiency with orchestration, runbooks, and automatic failover.
- Disaster recovery orchestration
- Production failover
- Site-to-site VPN
- Email SecurityBlock any email threat, including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero days in seconds before it reaches end users. Leverage Perception Point’s next-generation technology for lightning-fast detection and easy deployment, configuration, and management.
- Anti-phishing and anti-spoofing engines
- Anti-evasion and account takeover protection
- Next-generation dynamic detection against zero-days
- Data Loss Prevention (DLP)Prevent leakage of sensitive data from endpoints via more than 70 local and network channels and strengthen compliance with minimal effort and speed to value.
- Content-aware data loss prevention
- Automatic client-specific DLP policy creation and extension
- Pre-build data classifiers for common regulatory frameworks
- File Sync and ShareGet a full control over data location, management and privacy with a file sync and share service, including a transaction ledger to enable notarization and eSignature capabilities, across all platforms.
- File notarization
- Embedded eSignatures
- Independent file verification
Looking for help?
Frequently Asked Questions
What is extended detection and response (XDR)?
XDR, or extended detection and response, refers to cybersecurity solutions that deliver comprehensive protection by integrating and correlating telemetry data and threat intelligence from multiple sources, including endpoints, email, identity, network, etc. This approach enables extended detection and response capabilities more holistically addressing threats beyond the endpoint by integrating data from multiple sources with security analytics to provide context, correlate security alerts, enable fast analysis and swift response — across diverse IT systems.
Why is providing an XDR-based service important?
Nowadays, threats are shifting their focus beyond the endpoint due to the high degree of SaaS-based and IoT infrastructure and remote work practices. This means the security perimeter itself is growing beyond the narrower endpoint focus, which was the standard in last years.
To counter these disperse risks and threats across multiple attack vectors such as endpoints, email, identity, etc., service providers have to deliver XDR-based services to their clients, especially ones working in high-risk industries such as finance, health care, legal, etc. — regardless of their size.
What are the benefits of using an XDR?
Extended detection and response solutions enable you with broader visibility on threats and attacks showing not only what has happened on the endpoint, but also integrating telemetry from other sources such as email, identity, cloud apps and network, to show you in much greater detailed how an attack originated, got in, progressed, and what damage it has done.
This enables faster analysis at scale for incidents without having to manually correlate events between different point cybersecurity solutions.
Moreover, XDR enables you to swiftly perform remediation actions that are not purely focused on isolating the endpoint and removing the threat from it, but also enable further risk mitigation and remediation capabilities such as blocking malicious attachments in emails, blocking malicious email addresses, terminating user account sessions, suspending user accounts, etc.
This comprehensive approach to cybersecurity not only ensures the highest level of protection against advanced threats and targeted attacks, reducing the risks for clients, but can also support compliance and help you streamline incident investigation and remediation efforts that are insurmountable with point security solutions.
What is the difference between EDR and XDR?
Endpoint detection and response, or EDR, is focused on providing event correlation, contextual information and analysis and a response toolkit for threats and attacks that are focused on the endpoint.
Extended detection and response, or XDR, goes the extra mile to ensure a more holistic approach to detection and response which goes beyond the endpoint, integrating data from other attack vectors such as email, identity, cloud applications or network. This approach further reduces risks and ensures a more complete protection that spans beyond the endpoint.
How to choose an XDR?
There’s a great variety of XDR solutions on the market, but the hard truth is that a majority of those have been created with enterprises in mind — introducing insurmountable complexity, costs, resource requirements and time-to-value for service providers.
When MSPs are considering what type of XDR to utilize, they should be thinking of capabilities that enable the MSP to deliver services on top of the solution to disperse and diverse client environments with minimal effort — such as SaaS management console, role-based access, multitenancy and ticketing integrations.
Moreover, as a service provide you need to think of scalability; can you deliver services on top of the XDR solution with your existing resources and would attracting more business also lead to higher resource requirements and costs? Innovations such as AI-guided attack analysis, generative AI experience and single-click response to incidents, along with native solution integrations beyond standard cybersecurity capabilities as well as the support by an MDR service, can help streamline your services, and reduce costs, resource requirements and time to value.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.