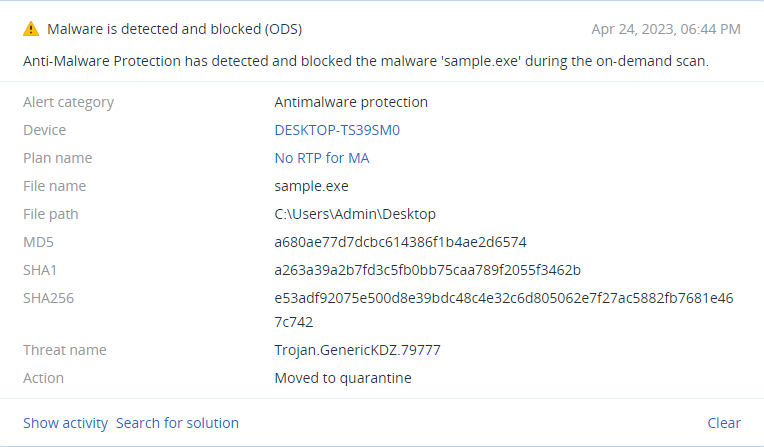
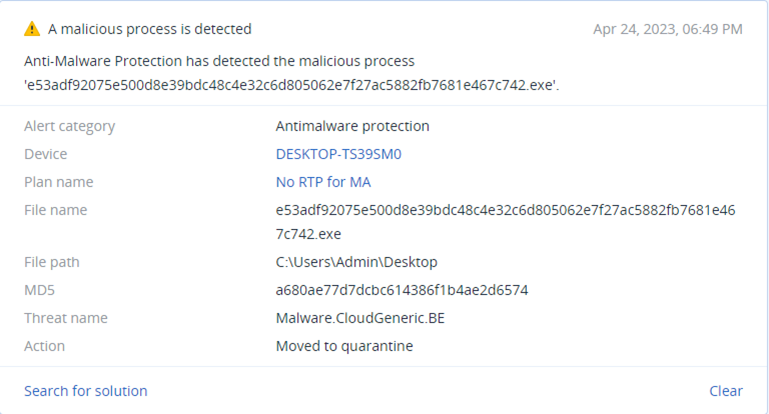
Summary
- Sold as malware-as-a-service on underground forums since 2019
- Sample is PE32 executable, written in C/C++
- Capable of stealing passwords, cookies, and crypto wallet data
- Impersonates the product “ESET Security”
- Packed with custom packer
Introduction
Raccoon Stealer, also known as Mohazo or Racealer, is an info-stealer malware that first appeared in 2019, and is available as malware-as-a-service (MaaS).
It can be obtained from cybercriminal forums; a subscription costs $200 per month. Raccoon Stealer has already infected over 100,000 devices in the wild, across organizations and individuals, and became one of the most-mentioned attacks on underground forums.
The malware is used to steal data like credit card information, nearly all existing desktop cryptocurrencies wallets, cookies, and passwords. Raccoon Stealer performs SQL queries using sqlite3.dll in order to get the user’s auto-login passwords, credit card details, cookies, and browser history. Raccoon Stealer is usually delivered through exploit kits and phishing attacks.
The FBI has identified many credentials stolen by this group. A website was created for any individuals who want to check whether their email address appears in the cache of stolen data.
Technical analysis
Upon performing the static analysis, it is clear that the sample is an x32 architecture portable executable binary written in C/C++ and works on a 32-bit operating system.
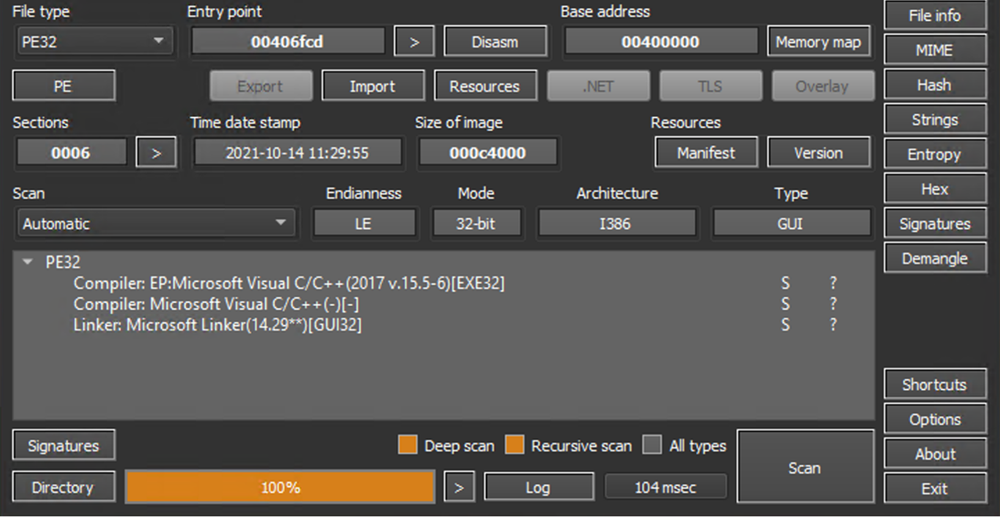
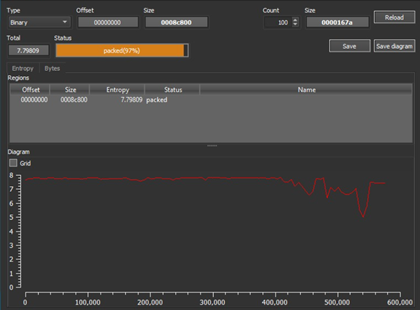
This executable has a high entropy value in total (7.66444), and the section rsrc has an unusual entropy of 7.79713, which can indicate the presence of encrypted, compressed, encoded, and/or obfuscated data in the file. Furthermore, PE section 1 has an unusual name: zqHWbqh.
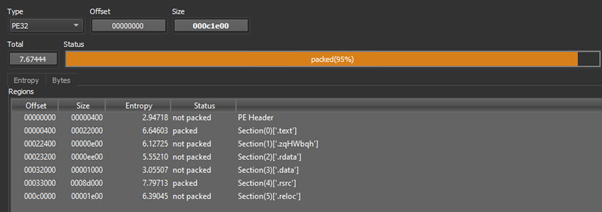
Upon peering further into the executable, the packer that was used is a custom one, appearing as simple numbers to make the research process more difficult.
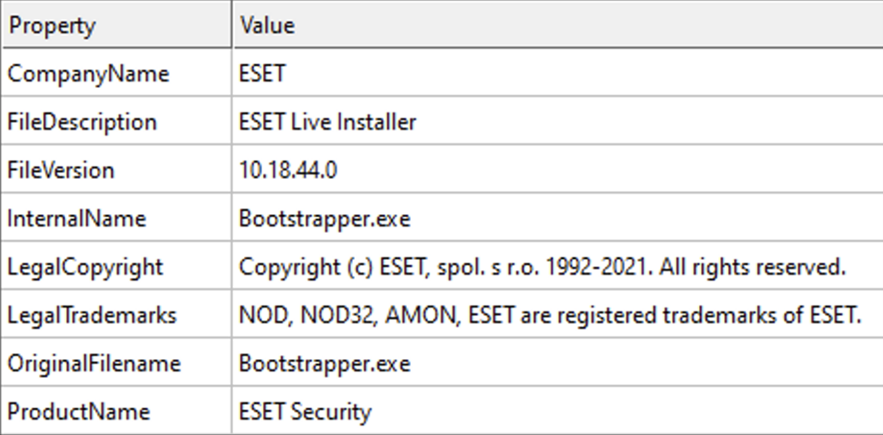
In the malware file description, it says “ESET Live Installer” in order to impersonate the AV engine installer and further fool victims.
When checking the resources, there is a file signature of “rcdata,” which has high entropy, and the language is identified as Russian.

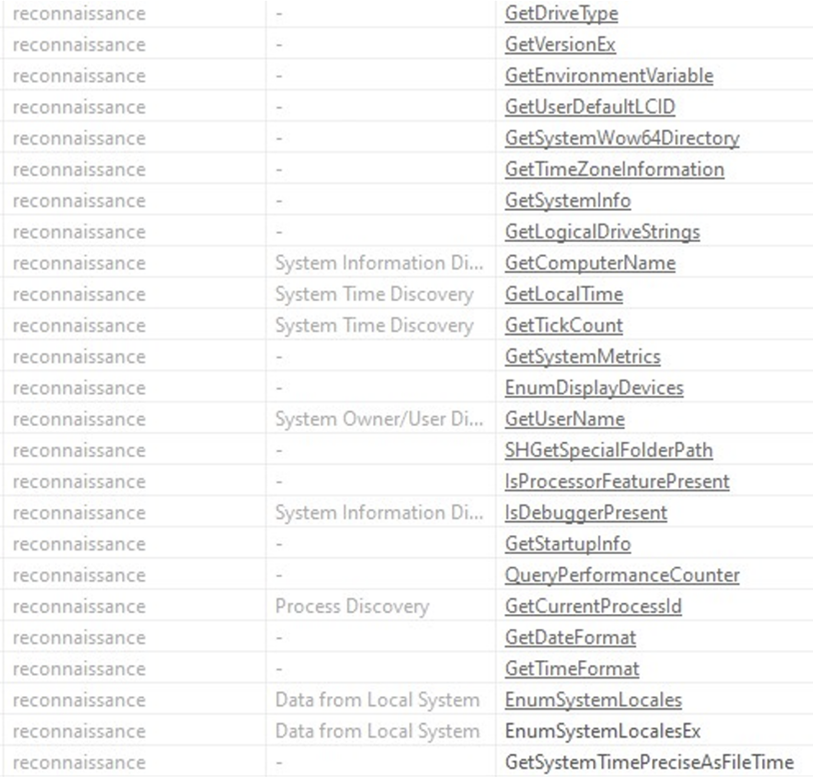
In the sample’s sections, there are two modules noted. It’s immediately clear that the malware has multiple calls to sleep with a high number of seconds. This is an evasion mechanism used by many malware strings to avoid being automatically analyzed inside a free sandbox, as most of the free sandboxes will limit the amount of execution time.
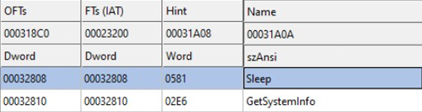
In addition, the sample uses the function GetSystemInfo to check the number of CPU cores, in an attempt to avoid being run in a lab environment.
As an additional layer of protection, Raccoon Stealer invokes the IsDebuggerPresent API to check if it’s being debugged.
Raccoon Stealer begins execution by obtaining the locale identifier for the user language. If the default locale is in Russian, the malware will not execute.
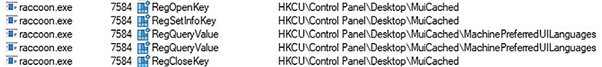
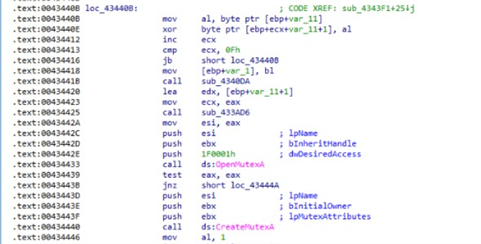
Next, the malware tries to create a mutex with MUTEX_ALL_ACCESS rights. Using this access right increases the possibility that the malware must be run by an administrator.
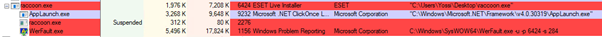
At the same time, the stealer spawns three new processes: AppLaunch.exe, raccoon.exe, and WerFault.exe.
The child processes are terminated almost immediately, only functioning as a pipe for the malware to inject the malicious payload into the memory of a legitimate process — APPLaunch.exe, which is the Microsoft .NET ClickOnce Launch Utility.
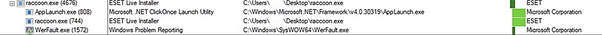
WerFault.exe is the standard Windows error reporting tool used in Windows 10 and 11, allowing the system to track and report errors related to the operating system or applications. Antivirus engines commonly trust WerFault as it's a legitimate Windows executable signed by Microsoft, so launching it on the system won't usually trigger alerts to warn the victim. However, in this case, it uses a known DLL sideloading flaw to load the malicious DLL.
Raccoon Stealer attempts to steal data from the Bitwarden and 1Password password managers, and also from the Atomic cryptocurrency wallet. Attempts to steal Bitwarden data are done by accessing the JSON file under the path %APPDATA%\bitwarden\data.json.
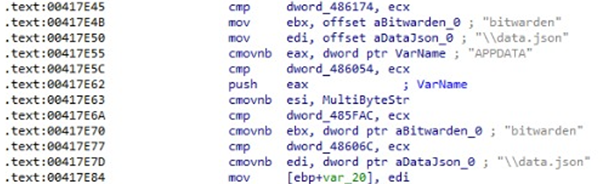
In addition to exfiltrating information, Raccoon Stealer can also take screenshots of the system. The malware creates a snapshot that includes all running process on the system with it.
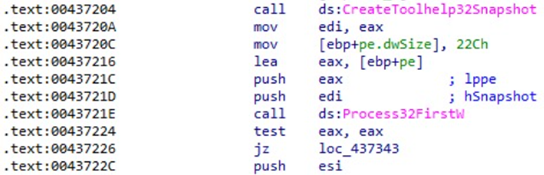
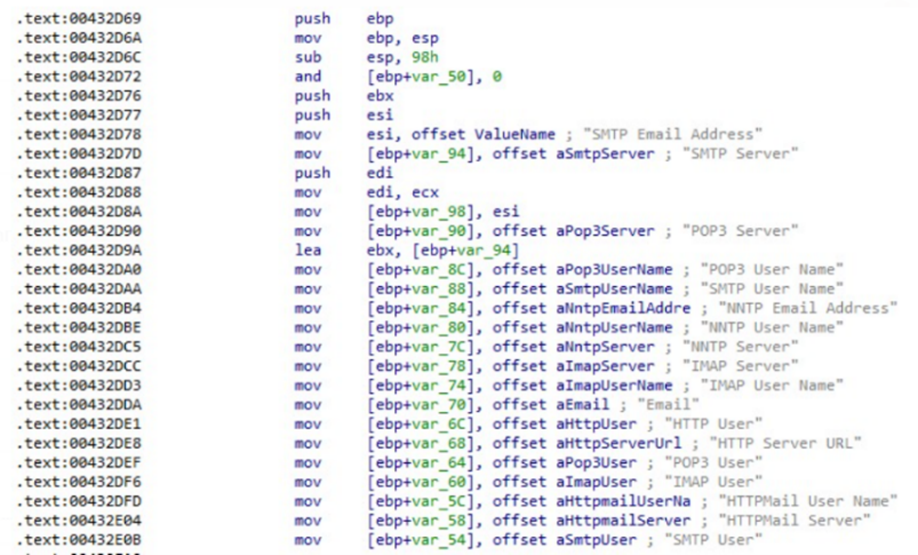
Raccoon Stealer also searches the infected host for email information.
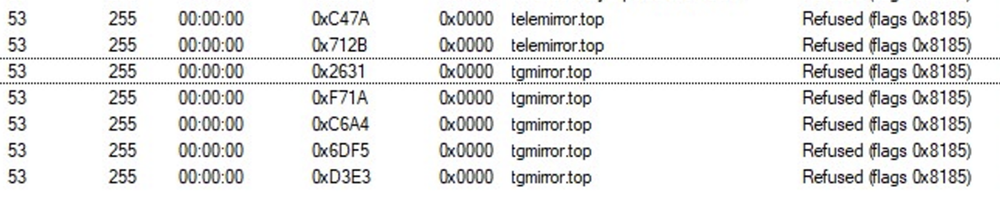
After retrieving the sought information, the stealer performs communication with the Telegram IP 149.143.167.99 in order to update its C2 address list.
The attackers behind Raccoon Stealer have been found using a chat app to store and update C2 addresses to spread within infected machines.
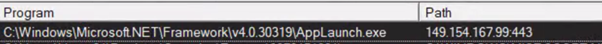
As an additional step in creating communication, one of the child processes of the malware — APPLaunch.exe — attempts DNS queries to the actor-controlled domain.
After being executed, Raccoon Stealer creates a suspended mode process to inject code. Once the process is complete, both the Raccoon and WerFault objects are deleted. AppLaunch continues to run in the background and connects to a remote address when needed.
Conclusion
Raccoon Stealer made a lot of noise in the underground community in 2019 when it was first released. Despite being around for several years, this malware remains popular and has managed to infect a significant number of devices. One reason for this is that the Raccoon Stealer team offers genuine customer service, providing cybercriminals with an easy and low-cost way to engage in cybercrime.
This stealthy/sneaky malware is designed to gather data in small increments as it progresses, storing it until it can be transmitted in a single compressed file using Telegram for data exfiltration and infrastructure updates. With its up-to-date techniques and underground customer service, it is no wonder that Racoon Stealer remains popular to this day.
Detected by Acronis
Acronis Cyber Protect successfully detects and prevents execution of all known versions of Raccoon Stealer, before any harm can befall the system.