If you are interested in cybersecurity, you may remember Stuxnet, an infamous worm which stopped uranium enrichment plants in Iran back in 2010. It’s no longer a secret that it was an Israeli-American cyberweapon. Since that time there were a lot of cases where critical infrastructure was attacked without any political motivation.
One recent case is Industroyer — a sophisticated piece of malware, a dangerous mix of cyber weapon and ransomware-like products. We were contacted by our big OEM partners running process control systems who asked about this threat, wondering if our newest anti-ransomware technology, namely Acronis Active Protection™ could help. And guess what? Acronis Active Protection does help!
What is Industroyer all about?
Ukraine has recently become a kind of a shooting range for new malware. There is strong evidence that the attack on the Ukraine’s power grid in December 2016 was caused by Industroyer, the malware which is capable of harming electric power systems. It is able to control electricity substations and circuit breakers directly. It has a module that erases crucial registry keys and overwrites files with data, making the system unbootable and causing permanent data loss.
This malware was dissected in June 2017 and the analysis showed that it is highly customizable and can be used to attack any industrial system machine, even with a sole purpose to destroy data and make it nonfunctional.
During the attacks that plagued Ukraine recently, a data wiper component was used in the final stage of the attack to hide its tracks and make recovery difficult. This component included a file called haslo.dat or haslo.exe and could be executed by a launcher component or used as a standalone malicious tool.
New age ransomware
This brings us to a future type of attacks. As this component can scramble or randomize file contents, it can be used in a ransomware attack to demand money for unscrambling the corrupted data. The point is that you may never get your data back anyway because this is really a cyberweapon rather than an extortion tool. Same goes for the new Petya-like variant of malware we recently blogged about, as this type was actually never designed to restore the encrypted data. It never generated a valid infection ID, which meant it couldn’t tell one machine from another after the infection. And the Master File Table got overwritten to a non-recoverable state.
Protect your data from cyber weapons
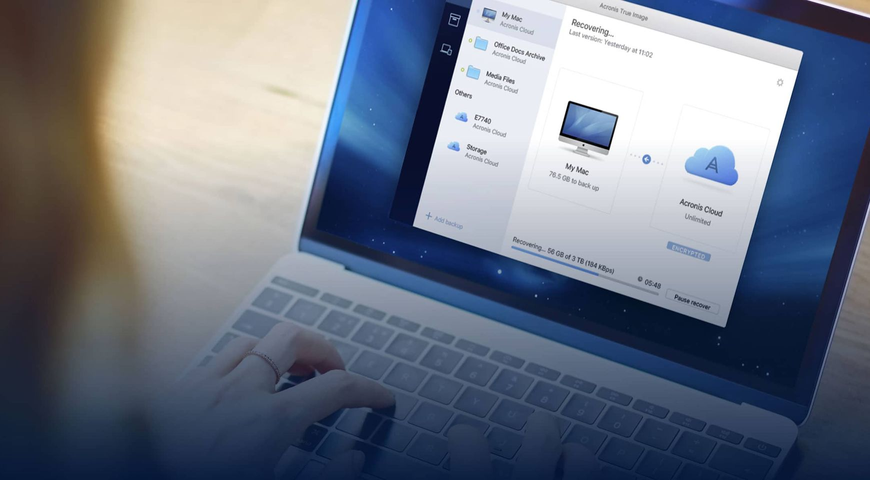
The good news is that if you have corporate and consumer products from Acronis, such as Acronis True Image or Acronis Backup 12.5 with Acronis Active Protection, it will detect Industroyer’s malicious activity, stop it, block it, and restore the affected files as you can see on the screenshot below.
To summarize: no matter what business you’re in — service, manufacturing, or industrial systems, make sure you follow these three simple steps to be on a safe side:
- Use a proper backup solution like Acronis Backup 12.5 with Active anti-ransomware technology to protect your data in real-time;
- Patch your systems regularly and do not use old discontinued operating systems;
- Educate users how to be safe in the current age of cyber threats.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.