
Small and medium-sized businesses (SMBs) are facing new, more sophisticated attacks on business continuity and critical data as ransomware continues to surge. The frequency of ransomware attacks is increasing at an alarming rate — every 11 seconds a business is attacked. The situation is dire as 80% of businesses have already experienced an attack in the past few years. The severity of the situation is heightened by the fact that 25% of all cyber breaches now involve ransomware payloads. As such, SMBs are facing a major challenge in trying to protect their systems against this type of attack.
To make matters worse, no one can hire enough quality cybersecurity and IT operations talent and the age of AI is here, with services like ChatGPT enabling cybercriminals to write perfect phishing emails and continually improve their sinister effectiveness with machine learning (ML).
But managed service providers (MSPs) can help by creating anti-ransomware services using an MSP-optimized cyber protection platform. Read on and discover how.
Stop relying on inadequate legacy approaches
Traditional anti-malware and anti-ransomware solutions are inadequate in addressing modern cyberthreats due to their reliance on signature matching — which cannot identify previously unknown zero-day threats — to detect known malware threats during the initial intrusion. Moreover, traditional solutions are unable to block ransomware in time to prevent the corruption or deletion of volume shadow copies, making recovery from an attack nearly impossible.
Additionally, with new types of ransomware emerging every day and evolving to evade traditional security defenses by moving laterally, exfiltrating data and encrypting critical data, it is challenging for behavioral anti-malware processes to detect them. This renders traditional solutions ineffective against new and sophisticated ransomware attacks, particularly when attackers withhold the decryption key and threaten to leak sensitive data, leaving businesses struggling to recover lost data.
Industry experts recommend that MSPs and their clients stop relying on traditional anti-malware and anti-ransomware solutions. Modern threats require a more comprehensive and layered approach to cybersecurity. By adopting more advanced solutions that leverage artificial intelligence, machine learning, and behavioral analytics, businesses can ensure that they are better protected against these sophisticated and evolving cyberthreats.
But how can we define what set of solutions is sufficient for modern ransomware protection? First, we map the essential components to the ransomware attack stages to demonstrate comprehensive protection and second, we utilize the NIST framework as a guideline to showcase compliance.
Ensuring comprehensive ransomware protection by addressing all stages of an attack
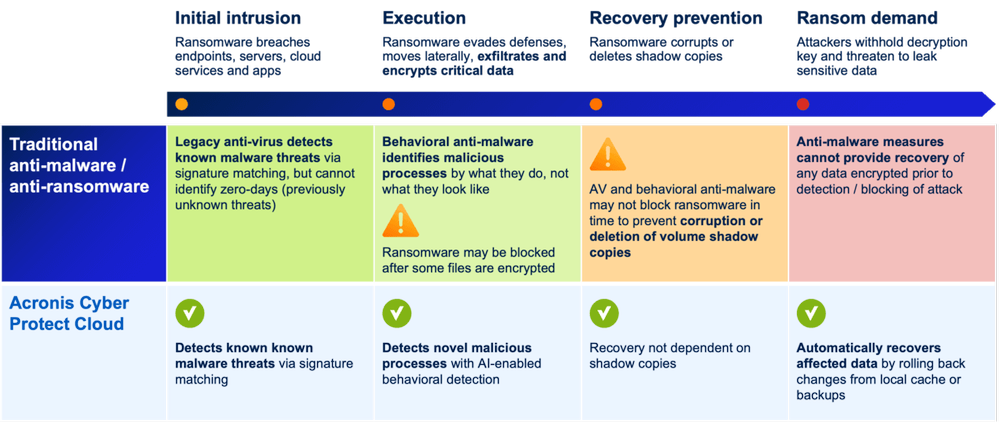
A robust and modern ransomware protection / cybersecurity solution should offer comprehensive protection against ransomware attacks. It should go beyond traditional anti-malware and anti-ransomware solutions by utilizing a combination of advanced techniques to deliver complete protection.
First, it will detect known malware threats via signature matching, which is a standard method in the cybersecurity industry. Secondly, it will use AI-enabled behavior detection to identify new and unknown malicious processes that may have slipped through traditional security defenses. This feature is especially useful in detecting zero-day attacks, which are increasingly prevalent in the current cybersecurity landscape.
In addition, a modern solution is designed to provide quick and easy recovery from ransomware attacks. Unlike traditional solutions that rely on shadow copies, this software will use a local cache or backups to automatically recover affected data by rolling back changes. This feature ensures that businesses can recover from an attack quickly and with minimal data loss.
Modern cybersecurity solutions offer a more comprehensive and effective approach to protecting businesses against ransomware. By combining signature matching, AI-enabled behavior detection, and innovative recovery mechanisms, it will provide complete protection against the evolving threat of ransomware. MSPs can benefit from this advanced solution to ensure that their clients’ data is secure and their operations run smoothly.
Delivering business continuity and data protection that spans the NIST Cyber Security Framework
The NIST (National Institute of Standards and Technology) Cyber Security Framework is a set of guidelines and best practices designed to help organizations manage and reduce cybersecurity risks. The framework provides a flexible and comprehensive approach to managing cybersecurity risks by organizing information, identifying vulnerabilities, and implementing controls to mitigate those risks. The NIST framework is widely recognized and adopted by organizations of all sizes and industries as a valuable tool to strengthen their cybersecurity posture and protect against threats.
An MSP-optimized cyber protection platform delivers business continuity and data protection that spans the NIST framework. Here is an overview of the features and the value each feature offers based on the five stages of the framework.
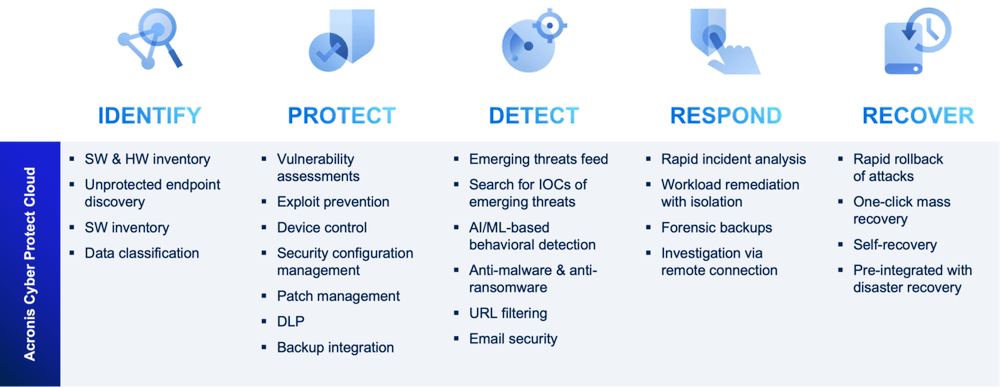
Identify
Identifying the software and hardware inventory is the first step in ensuring that all devices are up to date and secure and running the latest updates, patches and security features to protect against potential vulnerabilities.
Data classification involves identifying and categorizing data based on its level of sensitivity, importance, and regulatory requirements to ensure that only authorized personnel have access to sensitive information and that it is properly encrypted and secured.
Unprotected endpoint discovery involves identifying all devices that are connected to an organization's network that may not have the necessary security measures in place so that they can be properly secured and not pose a risk to the network.
Protect
Vulnerability assessments involve identifying potential weaknesses in an organization's systems and applications to proactively identify and address potential vulnerabilities before they can be exploited.
Patch management involves keeping all software and applications up to date with the latest security patches and updates to ensure that they are protected against known vulnerabilities and threats.
Exploit prevention involves using various tools and techniques — such as intrusion detection and prevention systems and anti-malware software — to prevent potential vulnerabilities from being exploited and prevent potential attacks before they can cause damage.
Backup integration involves regularly backing up all data and applications to ensure that they can be restored in the event of a data loss or cyberattack.
DLP (Data loss prevention) involves implementing various techniques and technologies to prevent data leakage from client workloads and strengthen regulatory compliance.
Security configuration management involves ensuring that all devices and systems are configured according to security best practices and that all devices and systems are properly secured and protected against potential vulnerabilities and attacks.
Detect
Subscribing to an emerging threats feed is one of the first steps in detecting emerging threats. This feed provides real-time information on the latest threats and vulnerabilities.
Another critical step in detecting emerging threats is to search for indicators of compromise (IOCs) of emerging threats, which are pieces of information that indicate a system has been compromised or is vulnerable to attack.
Anti-malware and anti-ransomware software are software programs designed to identify and block potential threats before they can cause harm.
URL filtering involves blocking access to potentially dangerous websites and URLs to prevent employees from inadvertently visiting malicious websites that could compromise the organization's security.
Email security is another critical aspect of detecting emerging threats as 94% of cyberattacks use email. By implementing robust email security measures, such as email filtering and encryption, organizations can protect themselves against potential threats.
Respond
Rapid incident analysis involves quickly analyzing the incident to determine the scope and severity of the incident to determine the appropriate response and minimize the potential impact of the incident.
Workload remediation involves isolating any affected systems or applications to prevent further damage and help contain the incident and prevent it from spreading to other parts of the organization's network.
Investigation via forensic backups allow organizations to analyze the incident and identify the cause of the incident.
Investigation via remote connections is used to access affected systems and applications to investigate the incident without further compromising the organization's network.
Recover
One important step in recovering from a cybersecurity incident is to ensure that disaster recovery is preintegrated into the organization's cybersecurity solution to quickly restore data and systems to their pre-incident state.
Rapid rollback involves quickly reversing any changes made by the attacker to minimize the potential impact of the attack and restore systems to a safe state.
One-click mass recovery by end users empowers end users to recover their own systems quickly and easily and minimize the potential downtime caused by the incident.
Next steps
In this article, we outlined the key components of a modern ransomware protection solution. However, the crucial question remains — are SMB clients able to invest in such robust defenses? Join us in our next article, accessible here, where we delve into the affordability of these defenses and cost-effective solutions.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



