Summary
- Discovered in the middle of March 2022
- Written in C
- Spreads through Group Policy Objects (GPOs)
- Tempers with Access Control (ACL) entries
- Overwrites all non-system files with zeros, then overwrites driver partitions in the same manner
- Causes the host to crash by wiping the Master Boot Record (MBR)
Introduction
CaddyWiper is an example of data-wiping malware, whose purpose is to corrupt the operating system and leave the targeted device unusable. It was first spotted in Ukraine in mid-March 2022 by the ESET research team.
According to the CERT-UA report, CaddyWiper is being distributed and launched in the network laterally using Group Policy Objects (GPOs). The GPO downloads the malware from an infected-but-unaffected Domain Controller. When run, the malware creates a scheduled task via a separate modular PowerShell script called “POWERGAP.”
After infection, CaddyWiper corrupts all files under the available driver partitions on the host, overriding them with zeroes. It then proceeds to corrupt the disk partition entries by zeroing them as well. Finally, CaddyWiper override with zeroes the MBR and Windows boot loader.
Technical analysis
Examining the malware, it’s easy to establish that CaddyWiper is a 32-bit architecture Portable Executable (PE). It’s designed for systems running Windows XP.
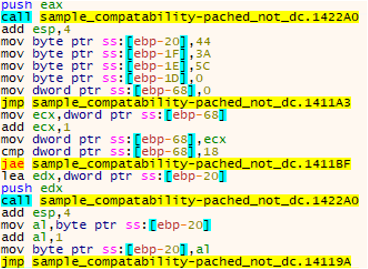
As our research lab was running a newer OS, a compatibility patch was needed. We can then see from the debugger that CaddyWiper is attempting to evade discovery by loading DLL files and calling functions from those DLL files directly.
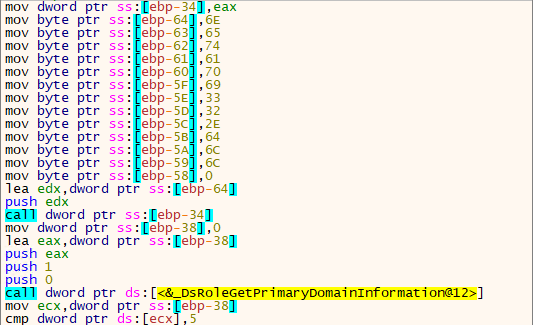
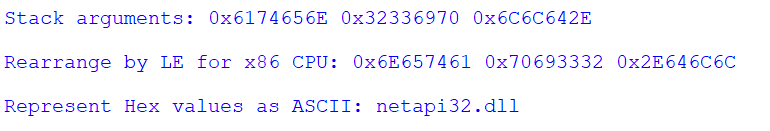
Following these calls, the wiper starts with an attempt to clarify the infected host’s role within a domain. This is achieved by calling the “DsRoleGetPrimaryDomainInformation” function from “netapi32.dll.”

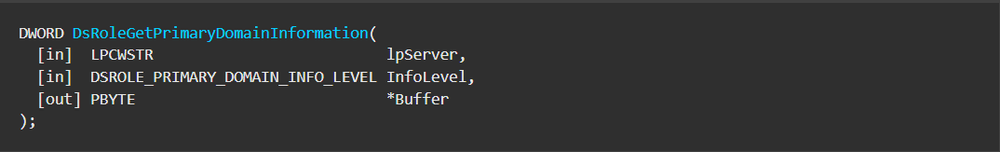
After establishing the role of the host in the domain, CaddyWiper will choose its execution flow accordingly:
- If the host is the domain controller, CaddyWiper will terminate its execution.
- If the host is not the domain controller, the malware will start its main wiping execution flow.
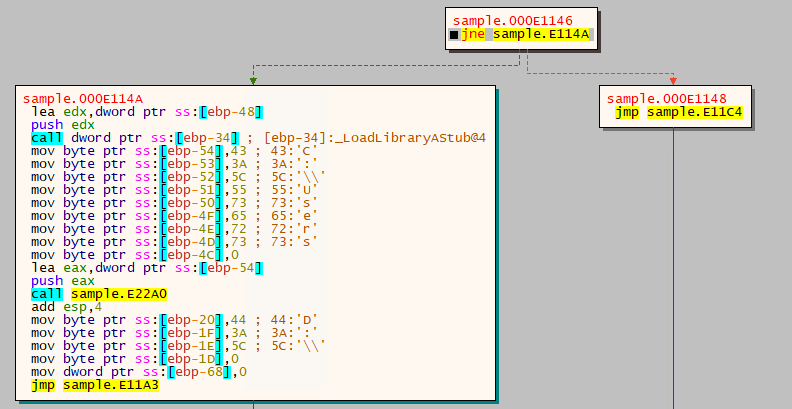
The wiping execution flow starts by accessing “C:\Users” and enumerating all the files within the directory and sub-directories, while simultaneously overwriting the contents of these files with null bytes.
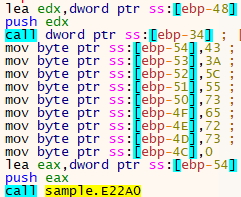
Overwriting is achieved by first changing the ACL entries for the local admin — setting the local admin special permissions, thus denying any permissions from the local admin.
After changing the ACL entries, the malware will attempt to overwrite any file it previously enumerated with null bytes (by zeroing down the content of the files). This is done by using the “WriteFile” Windows API function, and makes the files unusable.
After corrupting all files under the “C:\Users” drive, CaddyWiper attempts to corrupt all files on all other storage drives, starting with “D\:” and going all the way to “Z\:” in a recursive fashion.
After all files are zeroed out, the wiper will attempt to overwrite all logical partitions starting with “//./PHYSICALDRIVE9” and going all the way to “//./PHYSICALDRIVE0.” One by one, if those partitions exist, CaddyWiper overwrites the first 780 bytes of the partition. The original version of this wiper would overwrite the first 1920 bytes.
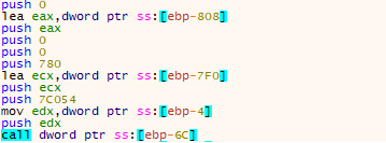
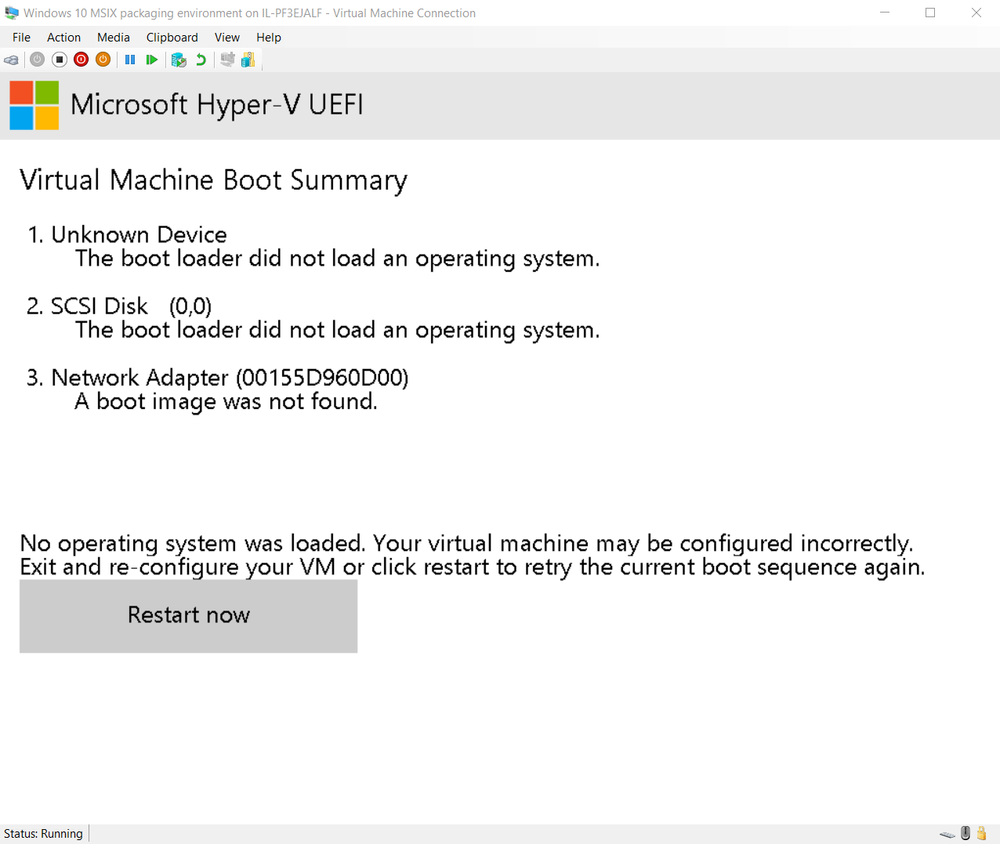
Since “//./PHYSICALDRIVE0” is also the location of the MBR, overwriting results in a crash and inability to load the operating system.
Detected by Acronis Cyber Protect
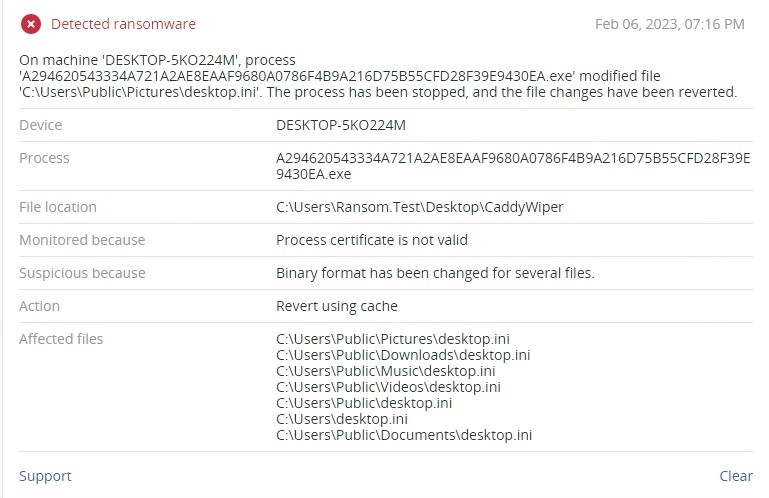
As part of the escalation of the Ukraine–Russian conflict, we note a rise in aggressive threat actors involved in the conflict. These actors have deployed data wipers that target industrial facilities and are distinctive by their ability to spare the domain controller in the infected network. Evidence shows that industrial facilities have already fallen victim, which is why having a security solution that can prevent and protect from wiper attacks is very important.
Acronis Cyber Protect offers full protection against any known destructive malware and unknown operations in the system, ensuring the safety of sensitive documents and information.



