The Best Backup Software for Mac and Windows Computers
Your business deserves proven cyber protection










Comprehensive backup for Windows and Mac endpoints
Protection management made simple
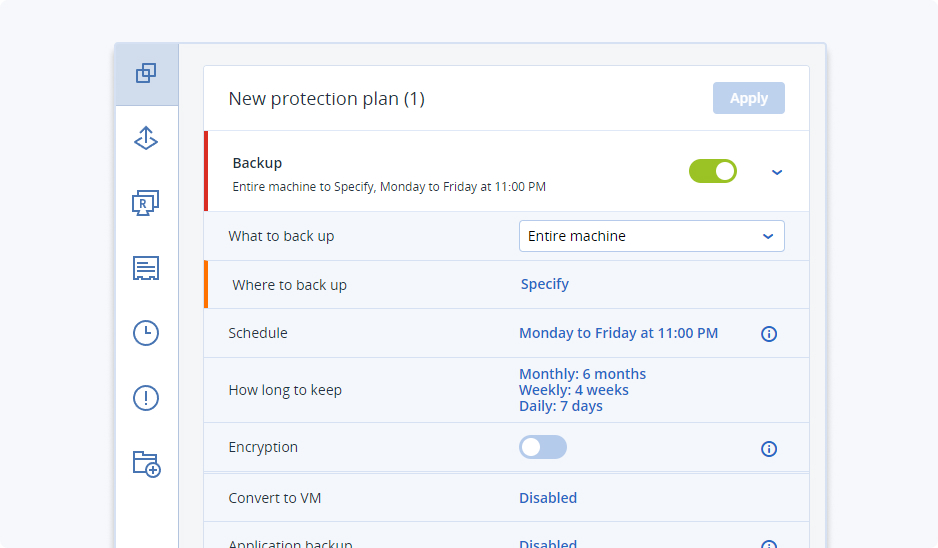
Minimize your resource expenditure with an easy-to-learn, easy-to-implement backup solution. One intuitive web-based interface makes it easier than ever to set up and manage your backups and protection.Flexible reporting and monitoring
All the backup status info you need, right at your fingertips — advanced reporting and status-monitoring capabilities include customizable widgets, reports, notifications, and critical event alerts.Universal restores to any hardware
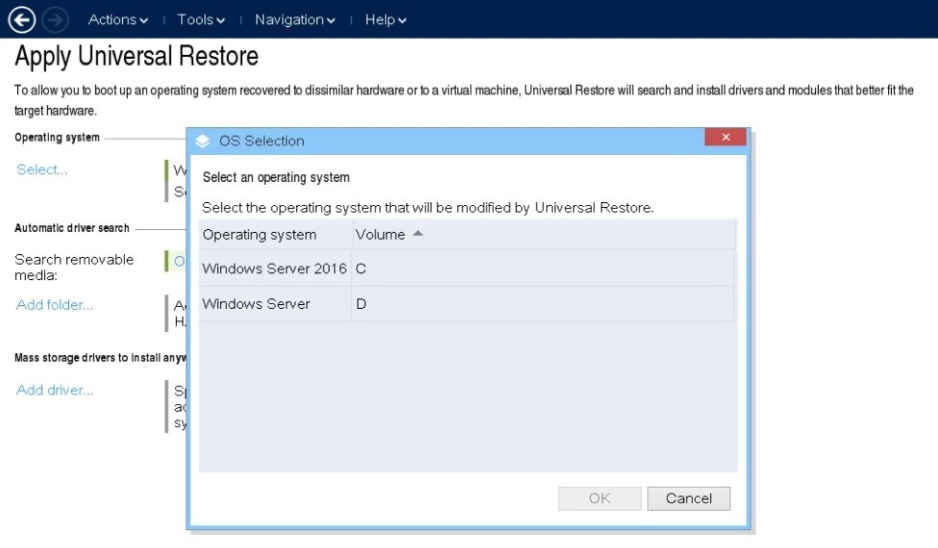
Stop wasting time and money on reinstallation and configuration. Acronis enables system recovery to a variety of physical or virtual platforms — even to new, dissimilar hardware — with just a few clicks.Integrated anti-ransomware
Safeguard your data from unauthorized modification, encryption, and ransomware threats with Acronis’ AI-driven anti-ransomware technology. Add advanced anti-malware and antivirus capabilities with Acronis Cyber Protect.End-to-end encryption
Protect your data from prying eyes with multi-level encryption that includes per-archive AES-256 encryption and high-grade disk-level encryption in Acronis data centers.Remote management of multi-tenants
Manage remote offices, branch offices, and departments easily with the ability to oversee, delegate, and establish separate tenants for multiple administrators.Monitoring of drive health
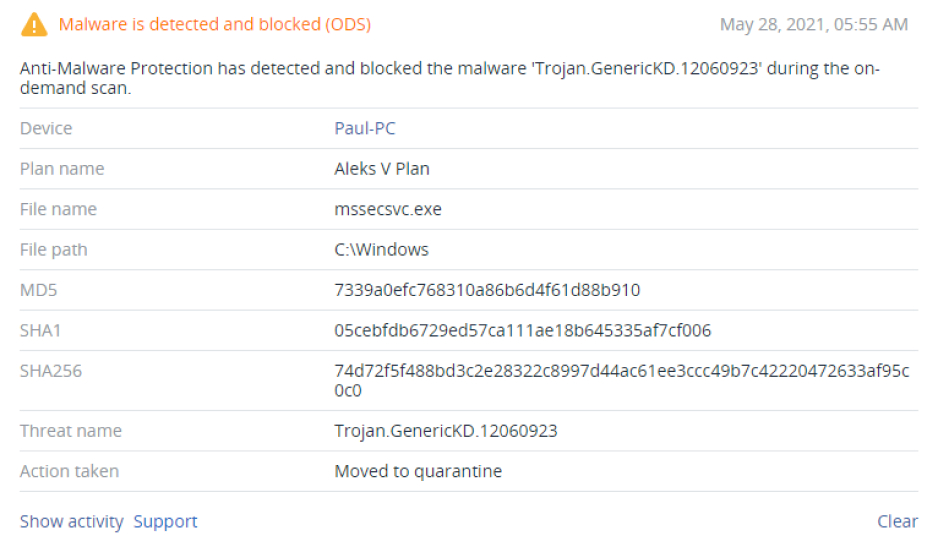
With Acronis Cyber Protect, AI-driven monitoring alerts you to disk issues before they happen, enabling you to proactively protect your data and avert disaster.Malware scans of backup files
Eliminate the risk of restoring infected files from backups with built-in malware scanning. Acronis Cyber Protect finds and removes any lurking threats — ensuring users can restore clean, malware-free data.Efficient data storage
Protect more systems while reducing the impact on disk storage and network capacity by capturing only the data that’s changed since the previous backup. Deduplication minimizes storage usage by detecting data repetition and only storing like data once.Thorough support for all systems
Enable backup for both modern and legacy systems with a single solution, all through one centralized console. Migrate data between different hypervisors, and to/from physical machines or the cloud.Acronis Instant Restore
Avoid downtime caused by time-consuming full recoveries. Simply run any Windows or macOS system directly from backup as a virtual machine, on any of six supported hypervisors.Blockchain-based notarization
Shield your data from tampering with an extra layer of protection. Powered by advanced blockchain-based technology, the Acronis Cyber Notary feature ensures data integrity.
Protect your data from any threat with a single data protection and backup solution
What the experts say
Looking for help?
Frequently Asked Questions
What is PC backup software?
PC backup software refers to all applications that enable users to back up files, folders, documents, software, configuration data, and your PC and server/system. Backup software allows users to create an exact copy of their files and store them in secure storage so they'd always be readily available for data recovery in case of accidental deletion, natural disaster, power outage, or a cyberattack.
PC backup software is primarily used to keep backups of critical data residing on your PC or network drives. You can initiate data backups on local/home computers or back up all PCs on an enterprise-level network. (including servers and networking devices)
Home user backup typically backs up selected files, folders, and critical operating system data. Users can store the backups on the same PC (not recommended), on an external hard drive, USB flash drive, remote server, or on the cloud. Enterprise-level PC backup usually covers each PC on the network to back up selected files and folders regularly on a customizable schedule to minimize downtime. Robust backup software will transmit data copies over a secure internal network or the Internet to a local or remote backup server to ensure the 3-2-1 Rule of Backup.
Moreover, reliable backup software can compress data backups to optimize storage space, allow version control to maintain different file versions, and often comes with enhanced cybersecurity features to safeguard your data at rest and in transit.
Users and companies can initiate full system, incremental, or differential backups, depending on their data creation habits and storage capabilities. Full PC backups duplicate all data on a machine, while incremental and differential backups only backup data that you’ve modified since the last backup, be it full or incremental. Generally, it's best to initiate a full PC backup once a month (for home users) and once a week (for businesses), combined with daily incremental backups to ensure all new data is available for recovery. However, data creation habits differ for home users and companies, so you should create a backup schedule that suits your backup needs optimally.Is Windows backup good enough?
The native backup tool for Windows PCs is called "File History". With File History, users can initiate intuitive partial backups and save local file copies relatively easily. If you don't need to back up extensive amounts of data, File History may be enough to keep important files and folders secure. However, File History backups are stored within the PC, so they won't be any good if your PC is somehow corrupted, stolen, suffers physical damage, or is hit by a ransomware attack.
Microsoft offers another way to go about Windows PC backup, and that is the Backup and Restore feature. The feature serves several purposes similar to File History but has a few crucial limitations.
Firstly, Backup and Restore offers only two backup options: "Let Me Choose" and "Let Windows Choose". If you "let Windows choose" what to back up, it will do so for all default folders unless you interrupt it. The default backup folders for Backup and Restore (as well as for File History) are Documents, Pictures, Music, Videos, Desktop, and any offline OneDrive data stored on the PC. To back up critical files, they must be placed in one of the default folders first.
If you want to initiate a customized backup, you can interrupt the default option, but that comes with another drawback. If you wish to choose backup folders manually, Backup and Restore won't allow the backup of files in the Recycle Bin, data stored on FAT-formatted drives, temp files on small drives (below 1GB), disks and partitions without a drive letter, or files in Windows System folders.
As for data restoration, File History allows single-file recovery, but Backup and Restore does not. If you wish to restore individual files from Backup and Restore storage, you must recover the entire backup. Moreover, Backup and Restore doesn't allow storing multiple system images on the same drive. You'd need multiple backup storage devices to store additional PC system images.
Lastly, File History and Backup and Restore don't support cloud backups. If you want to transfer backups online, you'd need to use a third-party backup solution.Why should I back up my entire pc?
Typically, users would store all sorts of important data on their PC – work-related documents, cherished photos, customized system settings, music and home video files, and more. While you can reinstall your operating system and re-download all programs if your PC is compromised, you can't recreate personal files and documents. Unless you have a reliable backup, those will be lost if, for example, your hard drive fails. However, hard drive failure is just one of the reasons for data loss.
There are numerous ways you can lose data on your PC – hardware or software failure, human error (accidental deletion), natural disaster, cyberattack, and power failure. You can also lose all your data if your PC is stolen or suffers human-inflicted damage. In any of the cases, you can lose valuable data if you don't have a reliable backup to recover it. Full system backups, in essence, work as an insurance policy – they store your readily available data in a secure location so you can recover it reliably following a data-loss event.
If you use a comprehensive backup solution, you can back up personal files, business data, operating systems, programs, and all PC settings on an external hard drive or the cloud. While you can choose which data types to back up, having a full system image in storage can save you time and effort in a recovery scenario. As modern backup solutions allow bare metal restores, you can recover your entire PC as if no data-loss scenario occurred.How to back up my entire PC with Acronis Cyber Protect?
Backing up your entire PC is the surest way to protect your data. The option is beneficial if you're unsure which data to safeguard the most. When you initiate an entire PC backup via Acronis Cyber Protect (formerly Acronis Cyber Protect Home Office), the solution will back up all internal hard drives in disk mode. The entire PC backup will contain all personal data (photos, music, videos, documents), your operating system, installed programs, and personalized system settings.
Here's how to back up your entire PC using Acronis Cyber Protect:
• Start Acronis Cyber Protect -> click "Backup" on the sidebar
• If you have other backups in the list (for example, created by previous Acronis software versions), then choose "Add backup"
•"Entire PC" is the pre-selected option, so leave it as is
• If you wish, choose a custom name for your backup (on the left menu pane)
• Choose "Select destination" –> select a destination for your backup
If you have an Advanced or Premium subscription, you will be able to upload entire PC backups to the Acronis Cloud. If not, you'd be prompted to plug an external drive into your PC to store the backups.
• Once you've chosen the backup destination, click "Options" to set backup specifics – schedule, scheme, archive cleanup, etc.
• We recommend creating regular backups of your entire PC, either scheduled or manual; if you choose the "Do not schedule" option, you'd need to run backup tasks manually via the "Back up now" button
• Next, it's crucial to set up a backup retention rate – if you don't, backups can quickly fill up your storage device; you can set up backup retention rates via the "Backup Scheme" option; for cloud backups, set up cleanup rules in the "Advanced" tab
• Once you're done with customization, click "Back up now" or press the down arrow to choose another start time optionHow do I choose a backup software solution?
There are numerous backup solutions on the market today. Many of them offer extensive features and backup functions. When choosing the most reliable backup software for your PC, we recommend examining seven key elements. Those are as follows:
• Ease of use
You want a user-friendly backup solution. One that's easy to install, run, monitor, and manage and offers intuitive software with customizable dashboards.
• Automation
Automation lets users configure their backup preferences and let the solution take care of the rest. Once the configuration is complete, the software will silently back up data regularly, while you will receive smart alerts to notify you of any data movements, changes, or threats.
• Reliability
Established, proven solutions minimize the risk of data loss. On the other hand, untested, new software can pose bugs and backup issues or even raise security threats.
• Versatility
Business users often rely on complex IT environments to procure company services. Robust backup software should cover all data types and provide flexible storage options – local disks, tape, NAS, SAN, the cloud, and more.
• Speed
Quick backup eliminates bottlenecks that can potentially impact your day-to-day computing operations. Fast recovery times get your systems up and running in a matter of minutes and minimize costly downtime.
• Breadth
You, your family, and your co-workers probably use multiple devices that require backup and protection. As each device may use a different operating system, choosing a backup solution capable of protecting all platforms within your network is recommended.
• Data protection
Nowadays, users can benefit from an integrated solution that combines backup and cybersecurity to protect data, apps, and systems in any scenario. With a combined solution, you will have to monitor and manage only a single dashboard. (with the bonus of having to pay for only a single solution)
Whether you lose data due to human error, hardware or software failure, natural disasters, or a cyberattack, you can quickly and reliably recover data and systems.What is the best backup software for Mac?
Macs are the machines of choice for many home users and businesses. Even if historical data points to more cyberattacks targeting Windows PCs, Macs deserve the same level of protection and backup accessibility as Microsoft devices.
When searching for the best backup software for Mac, you should explore five primary categories to pinpoint the most suitable solution. Those are as follows:
• User-friendliness
Reliable software should be accessible to users of all expertise levels. A user-friendly GUI means less time spent setting up backups and restoring data from storage. A single console to monitor and manage all backup features is best to optimize configuration times and minimize downtime.
• Value for money
Free backup options cost you nothing but rarely provide advanced backup features to ensure your data's integrity and availability. However, purchasing a paid solution doesn't immediately translate to having the most suitable software.
A paid solution should cover all primary elements of robust software, with the addition of customizable options, flexible cloud storage plans, smart alerts, and more.
• Backup features
The bare minimum here is simple – a solution capable of creating Mac backups reliably. However, many users would probably benefit from advanced features like multiple backup types (full, incremental, differential), session management, cloud backup, bare metal restores, and more.
• Performance
Performance is critical for businesses to minimize downtime and ensure day-to-day operations can proceed as quickly as possible following a natural disaster, power outage, or cyberattack. The modern user should expect a lag-free performance from their software of choice. Moreover, reliable software should initiate and complete backups quickly and optimize data recovery times.
• Cybersecurity features
Robust backup solutions provide more than simple data backup. A reliable backup tool will pack advanced cybersecurity features to protect your data at rest and in transit. Moreover, it will be capable of detecting less known threats before they can penetrate your defenses and alert you or your security teams so you can respond to them accordingly.Why Acronis Cyber Protect is the best Mac and Windows PC backup solution?
A lot can threaten your critical data – hardware failure, human error, cyberattacks, and more can lead to data loss, and unless you have reliable backups to restore your data, you may lose it for good.
Acronis Cyber Protect covers the seven key elements of a robust backup solution so you'd never have to worry about your data's safety. Our solution is easy to use – you can monitor and manage all backup and cybersecurity features from a centralized console, even if you have the agent installed on multiple machines. You can automate the entire backup process, so you won't miss an update on your backups. This will also ensure always having your important files and folders readily available for recovery.
Moreover, Acronis Cyber Protect is tested and verified by cybersecurity experts globally for its backup and cybersecurity capabilities. Backups with Acronis Cyber Protect are quick and intuitive, and the same is valid for data recovery, be it incremental, full system, or even bare metal restores.
You can choose a suitable subscription plan to only pay for what you're using, including customizable features and cloud storage space optimization. Cyber Protect is compatible with Windows, Mac, and Linux devices, so you can back up and protect a multi-OS network, as well as safeguard all mobile devices on it.
As for cybersecurity features, Acronis Cyber Protect utilizes threat-agnostic anti-malware defenses and enhanced endpoint protection management to secure your entire system from… well, from end to end. The integrated anti-virus and anti-malware features rely on machine-learning AI algorithms to detect and counter advanced threats, with smart alerts to notify you of any potential attackers.
Even if a data loss event occurs (cybersecurity features won't protect data against natural disasters or accidental deletion), you can quickly restore individual files or full system backups via Acronis Universal Restore. Be it Windows or Mac, you can rest assured your system is protected against all data loss scenarios.What is Backup Software?
Backup software refers to a specialized type of software designed to create copies of data stored on computers, servers, or other digital devices. This process ensures that in the event of data loss due to hardware failure, accidental deletion, or cyberattacks, the data can be recovered from the backup copies. The software can be configured to backup specific files, directories, or entire systems, and it can perform backups at scheduled intervals or in real-time.
Will Windows backup software slow down my computer?
Regarding the impact of Windows backup software on computer performance, it largely depends on various factors. Modern backup solutions are designed to minimize their impact on system resources. However, the performance impact can vary based on the software's efficiency, the size and frequency of backups, and the system's hardware specifications. During the backup process, especially when dealing with large amounts of data or performing a full system backup, you may notice a temporary slowdown in performance. To mitigate this, many backup programs offer options to schedule backups during times of low system use, such as overnight hours.
What are the Benefits of Backup Software?
The benefits of backup software are significant and multifaceted:
- Data Protection: The primary benefit is the protection of data. By regularly backing up important files, you safeguard against data loss due to accidental deletion, hardware failure, or cyber threats like ransomware.
- Easy Recovery: In case of data loss, backup software allows for quick and easy restoration of files, minimizing downtime and ensuring business continuity or personal data accessibility.
- Version Control: Many backup solutions maintain different versions of files, allowing users to revert to previous versions if needed. This is particularly useful in managing documents that undergo frequent changes.
- Peace of Mind: Knowing that your data is regularly backed up provides a sense of security, especially for critical business data or irreplaceable personal files like photos and documents.
- Compliance and Record Keeping: For businesses, backup software helps in complying with legal and regulatory requirements for data retention and protection.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.